AAA Wireless
AAA Wireless LAN (802.1x) Deployment
The AAA Server supports wireless LAN authentication using the Extensible Authentication Protocol (EAP) to define the communication with the wireless client.
Three EAP methods are supported:
- EAP-TLS - mutual authentication using server and client certificates.
- PEAP-MSCHAP (v2) - mutual authentication using server certificates and client passwords.
- PEAP-GTC (v0 and v1) - mutual authentication using server certificates and client passwords.
All methods provide high levels of security for authentication across a wireless network, as well as dynamic Wired Equivalent Privacy (WEP) key generation.
The EAP methods available depend on the wireless clients installed:
With Microsoft WiFi Clients but NOT Cisco Wireless Clients installed:
- EAP-TLS
- PEAP-MSCHAP (v2)
With Microsoft WiFi Clients AND Cisco Wireless Clients installed:
- EAP-TLS
- PEAP-GTC (v0 and v1)
Network Overview
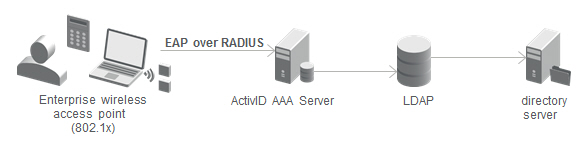
EAP-TLS Authentication Flow
- The client sends an authentication request to the wireless access point.
- The access point requests the client’s identity and blocks all requests until authentication completes.
- The client returns its identity and the access point forwards it to the AAA Server.
- The AAA Server sends its server certificate to the client via the access point.
- The client checks the authenticity of the server certificate and returns its own client certificate to the AAA Server.
- Random session keys are generated and transferred between the client and the AAA Server (via the access point) in an encrypted exchange.
- The client authenticates successfully.
EAP-PEAP (MSCHAP and GTC) Authentication Flow
- The client sends an authentication request to the wireless access point.
- The access point requests the client’s identity and blocks all requests until authentication completes.
- The client sends its identity and the access point forwards it to the AAA Server.
- The AAA Server sends its server certificate to the client via the access point.
- The client checks the authenticity of the server certificate and an encrypted tunnel is established.
- Client-side authentication is performed using the client password.
- The client authenticates successfully.
For illustration purposes, this section uses the Cisco Aironet 1100 as the wireless access point and Microsoft Windows XP on the workstation.





