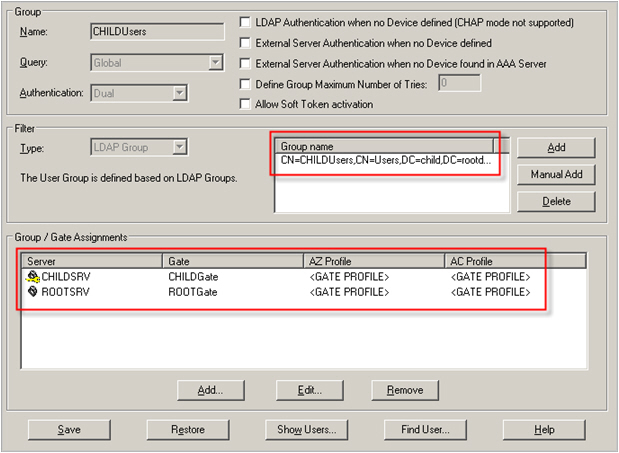
Scenario 1: Domain Tree
Description of the Scenario Environment
For this scenario, visualize an enterprise with two sites. The domain of the second site is a child domain of the root domain of the main site, as shown in the following image:
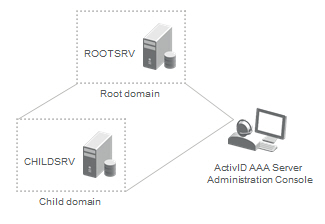
Assumptions
- Each site has its own Active Directory domain.
- The domains are in the same tree.
- There is an AAA Server on each site.
Goals
The goal is to fully manage all users and devices from a single AAA Server Administration Console. This means that operators using the Administration Console should be able to:
- Assign a device to any user in any of the Active Directory domains.
- Handle help desk tasks for any user in any of the Active Directory domains.
Each of the Administration Consoles connect to the forest root domain through LDAP, and each AAA Server is configured to connect to its local Active Directory domain.
AAA Server Configuration
See the Installing the AAA Server for Remote Access for information concerning the installation and standard configuration of the AAA Server. Only the configuration parameters related to the integration with Active Directory is detailed in this section.
We describe the configuration of the AAA Server for the following two sites:
-
Site A:
- Active Directory Domain - rootdom.com.
First domain created in the forest. - Active Directory Users Group - ROOTUsers
- Active Directory Users - ROOTUser1 and ROOTUser2
- AAA Server - ROOTSRV
- Active Directory Domain - rootdom.com.
-
Site B:
- Active Directory Domain - child.rootdom.com
- Active Directory Users Group - CHILDUsers
- Active Directory Users - CHILDUser1 and CHILDUser2
- AAA Server - CHILDSRV
-
Both sites:
The AAA Server Administration Console registry DWORD key HKEY_LOCAL_MACHINE/SOFTWARE/ActivCard/ActivPack/ActivPackAdmin/LDAPReferralDomainOrForestMode must either be set to 0 or must not exist.
The following image shows the AAA Server LDAP options for this scenario:
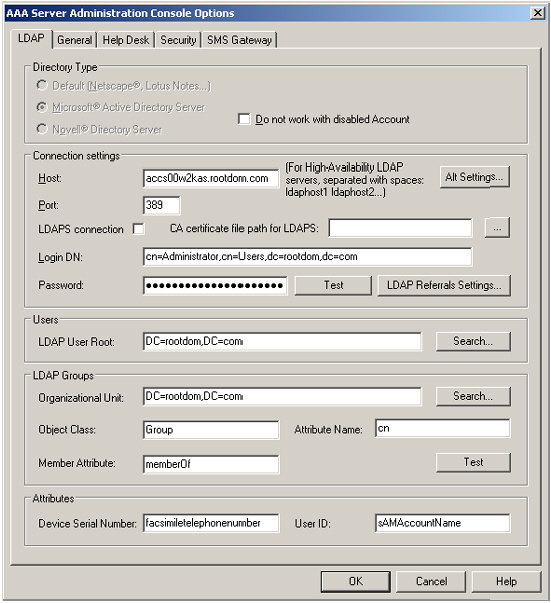
The AAA Server is configured to connect to rootdom.com through LDAP. This scenario provides more flexibility than Scenario 2 because the Administration Console is able to browse both the rootdom.com and child.rootdom.com domains, as shown in the following image:
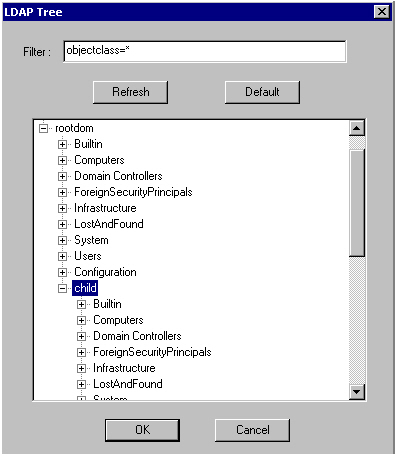
This simplifies the management of LDAP queries and the creation of groups later in the configuration.
LDAP Settings
Both servers (ROOTSRV and CHILDSRV) must be created in the server tree of Administration Console.
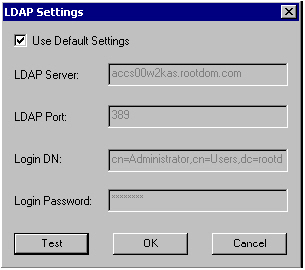
ROOTSRV inherits the default LDAP options that have been previously defined, as shown in the following image:
CHILDSRV must use specific LDAP settings to be able to connect to child.rootdom.com. The following image shows the required LDAP configuration for CHILDSRV:
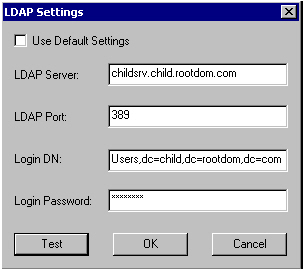
For performance reasons, CHILDSRV is connected to its local LDAP server.
LDAP Queries
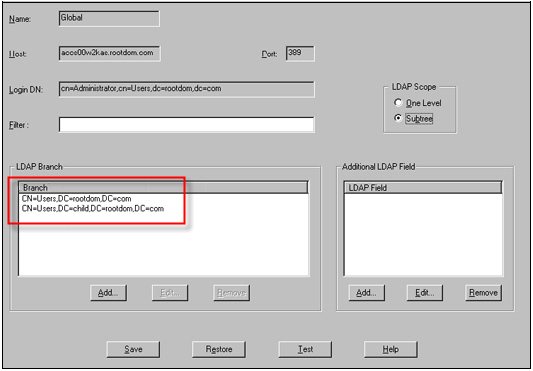
As shown in the following image, you can create a Global LDAP query to retrieve users from both rootdom.com and child.rootdom.com:
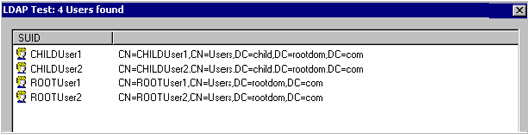
You can use the Test button to verify that this query correctly retrieves users from both domains, as shown in the following image:
It then is possible to assign devices to the displayed users, using only the query that has been previously configured. This outcome is shown in the following image:
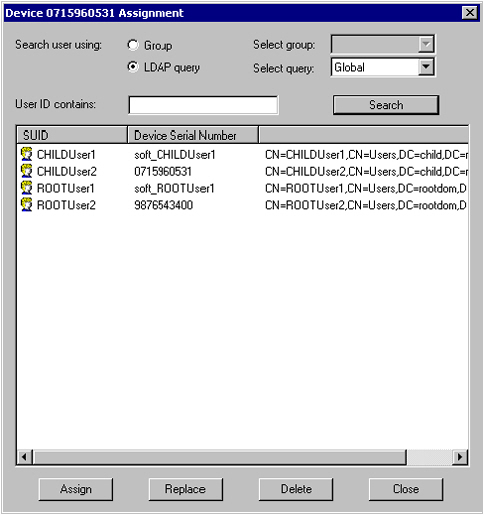
Roaming with Challenge/Response Authentication
You might want any user from any domain to authenticate from any site.
The above configuration natively enables such a roaming support for challenge/response authentication. Make sure that all relevant user groups are added to all the necessary gates on the different servers, as shown in the following image:
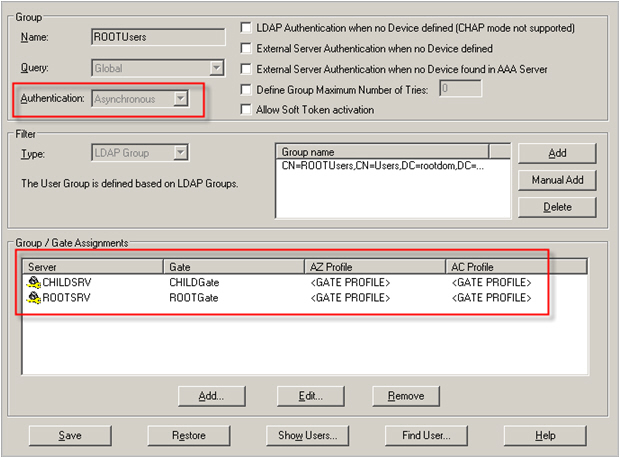
If ROOTUsers refers to the members of rootdom.com, this configuration allows the users from Site A to successfully authenticate with challenge/response from the AAA Server located on Site B, the authentication being directly validated by CHILDSRV.
Roaming with Synchronous Authentication
In order to enable roaming for synchronous authentication, ROOTSRV must contact CHILDSRV to validate the password sent by a user from Site B who connects through Site A.
In the following image, the yellow key is present only for ROOTSRV, showing that the keys and counters required to validate the passwords of the members of ROOTUsers are present only on ROOTSRV.
The process is similar when a user from Site A authenticates from a AAA Server located on Site B.