Configure the Web Help Desk Settings for Soft Tokens
You must define the token init strings and configure the Web Self Help Desk portal authentication policy. Perform this configuration in the AAA Web Help Desk portal.
- Start the ActivID AAA SKI Connector service.
-
To connect to the Web Help Desk either:
-
Open your browser and enter the Web Help Desk server URL:
https://<IP address or hostname>:<port number>/4tress-aaa/helpdesk/login
The IP address or hostname, and port number were configured during installation.
- Click Start, and point to All Programs, ActivID, AAA, and then click Connect to AAA Web Help Desk.
-
Go to the Web Help Desk installation directory (by default, C:\Program Files\ActivIdentity\AAA\WebHelpDesk), and double-click the Connect to AAA Web Help Desk shortcut.
You can also copy the Web Help Desk and Self Help Desk shortcuts to a more convenient location (for example, the desktop):
-
-
Log on to the Web Help Desk with the static or dynamic credentials for an Administration Console Administrator.
-
Select the Configuration tab.
-
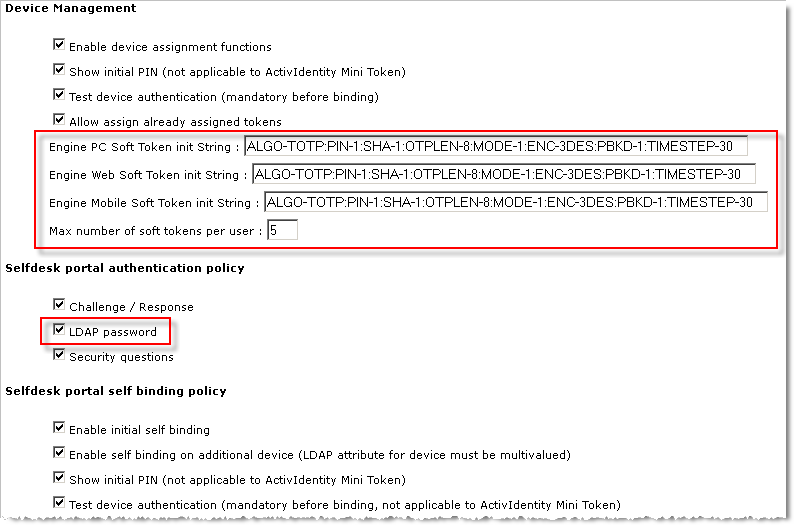
Scroll down to the Device Management section.
HID Approve initializations can be configured with the following options, which are broken into sections for easier reading below.
When used in the configuration, the init string should be configured as a single unbroken string.
Each Entity / Value pair is formatted as, “ENTITY-Value”, and each pair is separated by a colon (:).
As an example, the init string is initially set to the following default value:
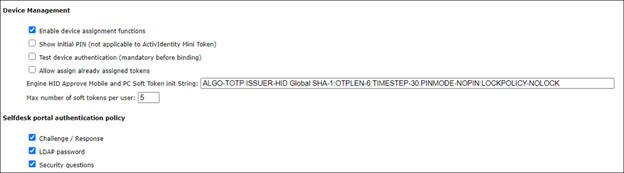
ALGO-TOTP:ISSUER-HID Global:SHA-1:OTPLEN-6:TIMESTEP-30:PINMODE-NOPIN:LOCKPOLICY-NOLOCKNote:
- “{ }” symbols denote where there is a configurable option
- “[ ]” symbols denote additional important information about that Entity / Value pair and should not be included in the string
- the “|” symbol denotes where the options are one of only two options
- “to” between two values denotes that the value chosen can include the values listed as well as any whole value in between
For HOTP:
ALGO-HOTP:
ISSUER-{HID Global}:
[Default – use any desired string up to 40 alphanumeric characters or spaces]
SHA-1:
OTPLEN-{6|8}:
PINMODE-{PIN|NOPIN}:
LOCKPOLICY-{DELAY| NOLOCK}:
INITIALDELAY-{0 to 99}:
[INITIALDELAY should only configured if LOCKPOLICY is set to -DELAY; default value is 2]
MAXCOUNTERVALUE-{0 to 99}:
[MAXCOUNTERVALUE should only configured if LOCKPOLICY is set to -DELAY; default value is 6]For TOTP:
ALGO-TOTP:
ISSUER-{HID Global}:
[Default – use any desired string up to 40 alphanumeric characters or spaces]
SHA-1:
OTPLEN-{6|8}:
TIMESTEP-{30|60}:
PINMODE-{PIN|NOPIN}:
LOCKPOLICY-{DELAY|NOLOCK}:
INITIALDELAY-{0 to 99}:
[INITIALDELAY should only configured if LOCKPOLICY is set to -DELAY; default value is 2]
MAXCOUNTERVALUE-{0 to 99}
[MAXCOUNTERVALUE should only configured if LOCKPOLICY is set to -DELAY; default value is 6]The following table describes each entity in the string and the values available.
Note: The grayed-out cells indicate values that are unavailable in this version.
Entity Entity Description Value options Description ALGO
One-Time Password (OTP) Algorithm
HOTP
Event-based token OATH HOTP
TOTP
Time-based token OATH TOTP
ISSUER
Name of the Issuer of the HID Approve Service – this is the name that appears before the username when a user activates an HID Approve device.
It is set to “HID Global” by default, but can be any string that:
- Contains a maximum of 40 characters
- Can contain upper and lower case letters and numbers
- Can contain spaces (but no other special characters)
For example, if the ISSUER value is set to “ABC Company”, when a user registers an HID Approve device using the AAA Self Help Desk, the name of the HID Approve service is registered in the app as, “ABC Company – user@abccompany.xyz”
SHA
The hashing algorithm to be used.
Note: In this version, only SHA1 is supported. It is only used to hash the value used to generate the OTP, which is secure by its temporary nature and is not stored for later use (see rationale in https://tools.ietf.org/html/rfc4226#appendix-B)
1
SHA1
OTPLEN
The number of digits in the OTP.
6
6-digit OTP
8
8-digit OTP
PINMODE
Whether the OTP is protected by a second factor (Default: NOPIN)
PIN
Protected by a user PIN
NOPIN
Not protected by a user PIN
LOCKPOLICY
Whether PIN entry is further protected by an exponential delay between each failed authentication attempt (Default: NOLOCK)
DELAY
An exponential delay is inserted between each failed authentication attempt.
NOLOCK
The PIN never locks.
INITIALDELAY
The initial value in seconds of the exponential delay referred to in LOCKPOLICY (only valid when LOCKPOLICY=DELAY) (Default: 2)
{number value in seconds, from zero to 99}
For the initial failed attempt, an ‘n’-second delay is introduced before another attempt can be made (‘n’ is 2 seconds by default).
On the second failed attempt, the delay is ‘n’^2, the third attempt is ‘n’^3 and so on, until the MAXCOUNTERVALUE number is reached, at which point the delay does not increase.
MAXCOUNTERVALUE
The maximum counter value after which exponential delays are fixed and do not keep increasing (only valid when LOCKPOLICY=DELAY) (Default: 6)
Number of failed attempts allowed
Once this number of PIN failures are reached, the time delay between attempts does not exponentially increase further.
TIMESTEP
The time step for TOTP algorithm.
Important: This is a required parameter and exclusively for use with ALGO-TOTP, which means it MUST appear in the suite string for ALGO-TOTP, but MUST NOT be used in the init string for ALGO-HOTP.
30 or 60 seconds are valid supported values for TIMESTEP.
30
30 seconds time step
60
60 seconds time step
Note: Using the HID Approve Engine init string, you can define the following PIN policies:
- PIN Enforcement policy – see the PINMODE entity
- PIN Protection policy – see the LOCKPOLICY entity
(The PBKD option is no longer available.)
Other PIN policies cannot be edited:
- PIN codes are always checked for weakness (for example, PINs such as 123456, 111111, 654321, and 987654 are not accepted)
- Minimum PIN length is 6 digits, and the maximum PIN length is 8 digits
- No other PIN rules are enforced
Important: For manual offline HID Approve activation, the required init string configuration is:
- ALGO - TOTP
- ISSUER - HID Global
- SHA - 1
- OTPLEN - 6 digits
- TIMESTEP - 30 seconds
ALGO-TOTP:ISSUER-HID Global:SHA-1:OTPLEN-6:TIMESTEP-30
In this mode, the following settings will not be taken into account by the HID Approve Token:
- PINMODE
- LOCKPOLICY
HID Approve will automatically apply a 6-digit PIN policy with a delay policy.
-
Set the Maximum number of soft tokens per user.
-
Under Selfdesk portal authentication policy, select LDAP password.
-
Click Apply changes.