Using ActivID ActivClient Auto-Update
This section describes how to update and configure ActivClient using Auto-Update in order to access your company’s internal web site.
Because configuration is site dependent, HID Global cannot pre-configure the ActivClient package with your auto-update settings. However, you can create a custom setup including configuration settings that are specific to your deployment.
In order to update ActivClient, the Auto-Update service runs with elevated privileges. Always use the Auto-Update service with an SSL protected AutoUpdate server.
Using the Auto-Update service without SSL protection could lead to malicious software being installed on the client workstation.
Use the Auto-Update service without SSL protection only for testing and troubleshooting purposes.
ActivClient Auto-Update Overview
The Auto-Update system uses a standard web server to publish ActivClient software updates. The Auto-Update client uses the HTTP and HTTPS protocols to communicate with the web server, although it is highly recommended that you use HTTPS for security reasons.
The web server can reside on your company intranet, the DMZ, or on the Internet. You can use any standard web server.
ActivClient periodically checks your company’s web site for new versions and acts as follows:
-
If ActivClient is already upgraded, nothing is done.
-
If a new version is available, the new version (or patch) is downloaded, and then automatically installed.
The Auto-Update client runs with elevated privileges as a service. Therefore, even if the end user does not have enough privileges to run the installer, the client software is updated successfully.
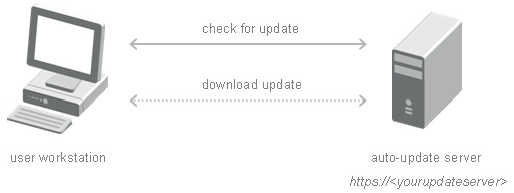
On the user workstation, the following tasks are performed by the Auto-Update tool:
-
Starts the update wizard at regular times (set up in registry)
-
Checks to confirm that communication is secure and that the server trusted
-
Reads the Auto-Update configuration file on the host
-
Checks the local version number against that of the server
-
Downloads a new version of the installer
-
Runs the new installer
-
Updates the local version number
The Auto-update Server:
-
Contains Auto-Update configuration file
-
Stores the new version number
-
Stores the URL to the new installer
The Auto-Update server can be configured to apply:
-
Major updates – new ActivClient versions (MSI files)
-
Maintenance updates – ActivClient hot fixes and service packs (MSP files)
To configure the Auto-Update Server, you must obtain:
-
Web certificates from your web server (Server Authentication certificate)
-
A Root Certificate (Certification Path)
For further information, see Configure ActivClient Auto-Update.
Prerequisites
Confirm that the ActivClient Auto-Update component is installed on the client machines.
The ActivClient Auto-Update component is not installed during a typical setup. Install the ActivClient Auto-Update component on the user workstation using the Custom setup option. For further information, see Customize the Installation.
If you are using HTTPS (recommended), make sure that the Auto-Update server SSL certificate is trusted by the client.
-
Download the trusted certificate in .cer format (for example, activclient.cer).
-
Trust the certificate for the client machine by using acregcrt.exe (installed in ActivClient install path):
acregcrt.exe-regcrt activclient.cer.
ACREGCRT.EXE
This executable is installed in the ActivClient installation directory.
This tool does not accept path for the certificate file and does not return any feedback. Use Internet Explorer to check if the certificate is correctly trusted (from the Tools menu, go to Internet Options, Content, Certificates, and then Trusted Root Certification Authorities).
Configure ActivClient Auto-Update
To configure auto-updates for 64-bit edition of ActivClient on the same server, you must create two different configuration files.
-
On the web server you want to use for the updates, create a virtual directory for x64 and an autoupdate.ini file in the AutoUpdate\ActivClient\Updatex64 directory.
-
In autoupdate.ini, replace AC_XX.msX with the filename of the .msi or .msp that must be installed.
For example:
[AUTOUPDATE]
BuildNumber=7.4.1.XX
FileName=ActivID ActivClient x64 7.4.1.msi
CmdLine=/qrWhere:
-
BuildNumber is required and indicates the build number (refer to ActivClient_ReleaseNotes.html for the correct BuildNumber) to be installed.
-
FileName is required and indicates the update file to be installed.
-
CmdLine is optional and indicates optional options to use with msiexec during installation. For example:
It is highly recommended that you:
-
Set REINSTALLMODE=vomus in the command line in order to make sure that a Windows Installer repair operation does not reinstall an older version of ActivClient that does not contain the latest patches. Because v requires access to the original setup (v forces updates of msi cached locally on the machine), the installation using that option must have easy access to the original installation package.
-
If the Auto-Update service does not have sufficient rights to access the original installation directory on the network, you can achieve the same result without the v switch in the MSI command line.
-
Place the .msX file (Microsoft Patch file) in the same virtual directories as the autoupdate.ini file.
Configure ActivClient Auto-Update on the Client Machines
You then must configure ActivClient as follows.
(See Smart Card Auto-Update for details on product customization.)
-
Enable software auto-update – defines if ActivClient will automatically check if software update is made available:
-
URL (text, empty by default)
This is the web address of the server where the new version is stored.
The URL can be a http or https URL. If the URL is SSL, the validity of the certificate must be checked (that is, the certificate must be trusted on the machine).
Example: http://194.168.2.221/Autoupdate/ActivClient
-
DownloadPath (text, empty by default)
This file must have restricted access rights (administrator and system) to avoid security issues.
Example: C:\DownloadedUpdate
-
Frequency of update – defines the interval (in days) between checks for software updates:
-
CheckDays (numerical, '1' by default)
Interval when the check must be done (in days).
-
Maximum number of update retries – defines the number of times the AC autoupdate service will attempt to update the software.
-
NumberOfRetries (numerical, '3' by default)
In case of problem when downloading the patch, numbers of tries before aborting download. If the download is aborted, the next check has a chance to download the patch.
-
Delay between update retries – defines the waiting period (in minutes) before AC autoupdate service retires to update the software.
-
TimeBetweenRetry (numerical, '15' by default)
Time in minutes before retrying the download.





