Outlook Security Profile Configuration
This section describes Outlook security profile management through the following ActivClient Outlook Usability enhancements settings:
-
Turn Off Setup Email Certificates in Microsoft Outlook on Card Insertion.
-
Turn On Automatic Publication of Certificates to the Global Address List.
Outlook Security Profile Settings
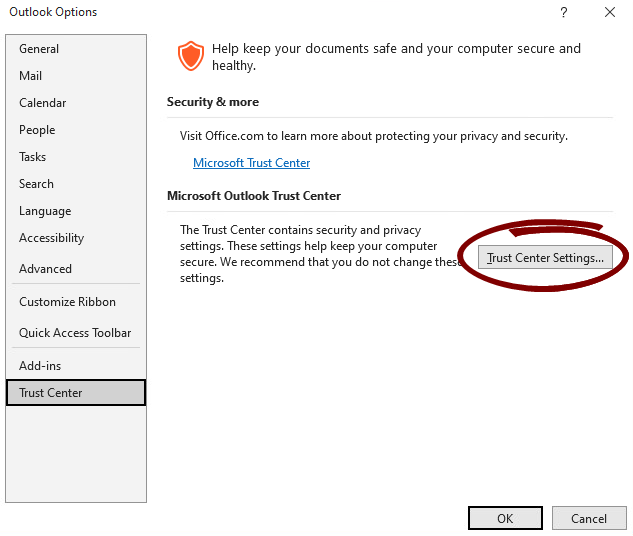
To view the security settings for Outlook 2019:
-
Go to File >> Options.
-
In the Outlook Options window, select Trust Center from the menu.
-
Click Trust Center Settings.
-
In the left pane, click Email Security.
-
In the Encrypted e-mail section, click Settings...
The Change Security Settings window is displayed.
The Outlook security profile created by ActivClient defines the following parameters:
-
Security Settings Name
-
Cryptography Format
-
Signing Certificate
-
Hash Algorithm
-
Encryption Certificate
-
Encryption Algorithm
Other parameters can be defined using Microsoft policies (e.g., Add digital signature to outgoing messages).
These settings are configured automatically at smart card insertion depending on:
-
The content of the inserted smart card
-
ActivClient Microsoft Outlook Usability Enhancements settings
-
Environment conditions as described in following section.
Outlook Security Profile Update
In default settings (i.e., when the Turn off setup email certificates in Microsoft Outlook on card insertion setting hasn't been enabled), ActivClient automatically updates the Outlook Security Profile upon card insertion provided certain conditions are met.
Conditions for Security Profile Update
General Prerequisites:
-
Certificate propagation: Microsoft Certificate propagation must be enabled.
-
A default Microsoft Outlook security profile is defined, and an Exchange account is set for this profile (for example POP accounts are ignored).
Conditions for Signature Certificate:
ActivClient selects the most recent signature certificate (based on the ‘Valid From’ date) that meets the following criteria:
-
Validity:
The current date must fall between the certificate's ‘Valid From’ and ‘Valid To’ dates.
-
Key Usage:
Must include 'Digital Signature' in the Key Usage extension.
-
Intended Key Usage:
-
Must include CERT_KEY_DIGITAL_SIGNATURE_USAGE, or
-
Must be identified as a CAC Signature Certificate or the PIV Digital Signature Key.
-
Conditions for Encryption Certificate:
ActivClient selects the most recent encryption certificate (based on the ‘Valid From’ date) that meets the following criteria:
-
Validity:
The current date must fall between the certificate’s ‘Valid From’ and ‘Valid To’ dates.
-
Key Usage:
Must include 'Key Encipherment' or 'Data Encipherment' in the Key Usage extension.
-
Intended Key Usage:
-
Must include CERT_KEY_ENCIPHERMENT_KEY_USAGE, or
-
Must be identified as a CAC Encryption Certificate or a PIV Key Management Key.
-
Additional Certificate Validation Checks:
Depending on the configuration settings, ActivClient performs additional checks on the selected signature and encryption certificates before updating the Microsoft Outlook Security profile and publishing to the Global Address List (GAL).
Email Address Consistency
The email address in the smart card certificate must match the email address configured in the Microsoft Exchange account, unless this prerequisite is disabled using the Allow Different Email Addresses in Smart Card Certificate and Microsoft Exchange Account setting.
If the Allow Different Email Addresses in Smart Card Certificate and Microsoft Exchange Account setting is enabled:
-
The email address is retrieved from the certificate RFC822 Subject alternate name.
If the attribute is missing, the email address is retrieved from the "E=" field in the certificate's subject.
-
If online, ActivClient validates the email address against Active Directory.
-
If offline, this check is automatically bypassed.
-
If the email addresses match, ActivClient updates the Outlook profile/publishes to GAL.
-
If the email addresses do not match, then ActivClient continues to check if Outlook/the GAL needs to be updated.
-
If no update is needed (that is, the card certificates are already used to configure Outlook/publish to the GAL), then no action is performed.
-
If an update is needed, then ActivClient prompts the user by presenting the email address configured in Microsoft Exchange and the email address used in the smart card certificate. The user then makes an informed decision on whether to proceed with updating the Outlook profile/publishing to GAL.
-
If the Allow Different Email Addresses in Smart Card Certificate and Microsoft Exchange Account setting is disabled:
-
The email address is retrieved from the certificate RFC822 Subject alternate name.
If the attribute is missing, the email address is retrieved from the "E=" field in the certificate's subject.
-
If online, ActivClient validates the email address against Active Directory.
-
If offline, this check is automatically bypassed.
-
If the email addresses match, ActivClient updates the Outlook profile/publishes to GAL.
-
If the email addresses do not match, these actions are not performed.
This last configuration is only applicable to customers who configure Microsoft Outlook with SuppressNameChecks.
Certificate Revocation List Check
If the Check CRL for Microsoft Outlook Security Profile Creation and Publish to GAL setting is enabled:
-
If CRL check is enabled and enforced, and if CRL check is not OK (certificate is revoked or on hold, or CRL times out), the certificate is ignored and the operation (automatically configure email certificates in Microsoft Outlook and/or automatically publish certificates to the GAL) is not performed.
-
If CRL check is enabled and not enforced, and if CRL check is not OK certificate is revoked or on hold, or CRL times out), the certificate is accepted and the operation (automatically configure email certificates in Microsoft Outlook and/or automatically publish certificates to the GAL) is performed but the certificate is marked as not CRL valid and an event warning is added in the Microsoft Windows event log.
-
If CRL check is enabled (and enforced or non-enforced) and if CRL check is OK, the certificate is marked as CRL valid.
If the Check CRL for Microsoft Outlook Security Profile Creation and Publish to GAL setting is disabled:
-
The operation (automatically configure email certificates in Outlook and/or automatically publish certificates to the GAL) is performed regardless of the CRL check status.
-
The CRL check timeout is also configurable.
-
The whole certificate chain is checked.
-
For performance reasons, the CRL check is performed only if the security profile needs to be updated (that is, after comparing with the current configuration).
-
If an OCSP provider is installed and configured on the Windows client, ActivClient will check the certificate status with OCSP instead of CRL.
The description above applies if the workstation is connected to the corporate network (Active Directory is accessible). If it is not and the Active Directory is not accessible, then the automatic configuration is still performed but with two differences:
-
No user account check is performed.
-
No CRL check is performed (whatever the configuration for the CRL check).
Once the conditions above are met, the security profile and the encryption/signature options are always updated:
-
If a security profile named ActivClient Certificates already exists, it is overwritten. The default profile setting remains unchanged:
-
If it was the default profile, it remains the default profile.
-
If it was not the default profile; it is not set as the default profile.
-
-
If no security profile named ActivClient Certificates exists, the profile is created and set as default.
-
All other security profiles (not named ActivClient Certificates) remain unaltered.
The profile creation or update is executed whether Microsoft Outlook is running or not, yet Microsoft Outlook needs to be restarted to see the updates in effect.
The Outlook security profile may be updated if new policies are configured (for example, changing the hashing algorithm from SHA-1 to SHA-256), even if certificates are not updated.
The created profile might be altered if the ActivClient setting Remove certificate from Microsoft Windows on smart card removal is enabled or if the user certificates are deleted from the Internet Explorer (CAPI) store.
In this case, the user needs to insert the smart card prior to sending signed emails in order to restore the security profile; otherwise, no 'insert smart card' window will be displayed when sending a signed email.
Security Profile Updated Values
The values updated by the ActivClient configuration are retrieved either from the smart card (certificates) or from the configured policies (ActivClient policies or Microsoft policies).
The following table lists the configured value for each setting when the profile is created or updated.
| Setting | Value |
|---|---|
| Security settings name Default Setting field |
ActivClient Certificates (always – not configurable) |
| Encrypt contents and attachment for outgoing message |
Same value as configured in Microsoft Outlook Cryptography Options Encrypt all e-mail messages. |
| Add digital signature to outgoing message |
Same value as configured in Microsoft Outlook Cryptography Options Sign all e-mail messages. |
| Send clear text signed message when sending signed message |
Same value as configured in Microsoft Outlook Cryptography Options Send all signed messages as clear signed messages. |
| Request S/MIME receipt for all S/MIME signed message | Same value as configured in Microsoft Outlook Cryptography Options Request an S/MIME receipt for all S/MIME signed messages. |
| Cryptography format | S/MIME (always – not configurable through ActivClient) |
| ‘Default security settings for this cryptographic message format’ check box | Checked (always – not configurable through ActivClient) |
| ‘Default security settings for all cryptographic message messages’ check box | Checked (always – not configurable through ActivClient) |
| Signing certificate selected |
The selected certificate is the most recent certificate (the most recent Valid From date) on the smart card that meets the following conditions:
|
| Signing certificate displayed name | Certificate friendly name. |
| Hash algorithm |
Same value as configured in ActivClient Outlook Enhancements setting Hash algorithm configured in Security Profile on card insertion. The selected algorithm cannot be updated in the Microsoft Outlook profile. It can only be updated through GPO settings. Default is SHA-256. |
| Encryption certificate selected |
The selected certificate is the most recent certificate (the most recent Valid From date) on the smart card that meets the following conditions:
|
| Encryption certificate displayed name | Certificate friendly name. |
| Encryption algorithm |
Same value as configured in the ActivClient Outlook Enhancements setting Encryption algorithm configured in Security Profile on card insertion. The selected algorithm cannot be updated in the Microsoft Outlook profile. It can only be updated through GPO settings. Default AES-256. |
| ‘Send these certificates with signed message’ check box | Checked (always – not configurable) |
For further information about the Microsoft policies that control these settings, see section Microsoft Policies Relevant to ActivID ActivClient.
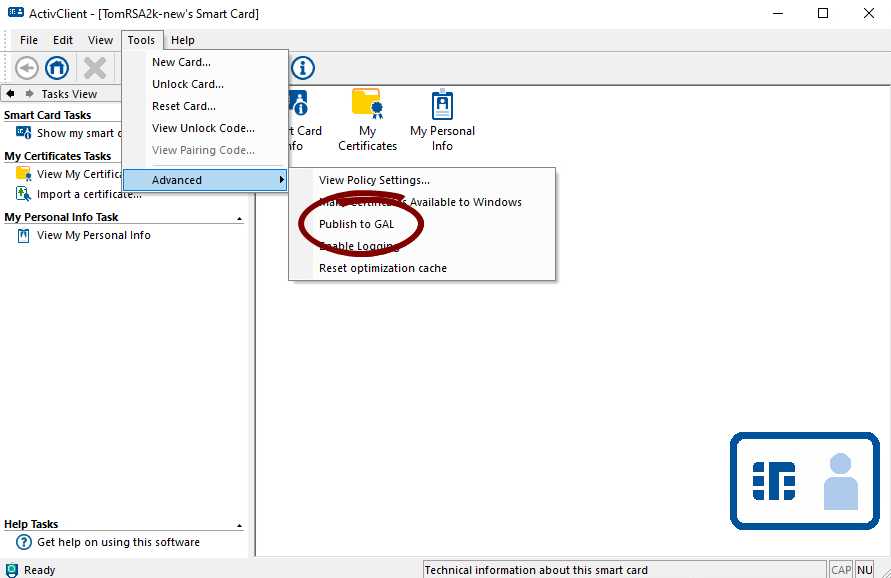
Publish Certificate to GAL
The ActivClient Publish Certificate to GAL feature consists of publishing the user's encryption certificate used for secure e-mail to the user's object in the Active Directory. This allows other Microsoft Exchange users using Microsoft Outlook or Outlook Web Access to automatically access the encryption certificate to send the user encrypted emails.
The feature is the equivalent of the Publish to GAL option that can be found in the Trust Center (Outlook 2007).
In full Microsoft environments (that is, using Windows-based CA), the Active Directory attributes are automatically updated when the certificates are created.
In this case, the ActivClient Publish to GAL and the Outlook Publish to GAL features are not necessary. On the contrary, they could lead to mismatched certificates. This is why the ActivClient Publish to GAL feature is disabled by default.
Profile Selection and Email Account
The email account selection is the same as for the security profile update: applicable to Exchange accounts (that is, not applicable for Outlook accounts configured for a third-party server or using a POP3 configuration).
Configuration
The setting Turn on automatic publication of certificates to the Global Address List is applicable only if the setting Turn off setup email certificates in Outlook on card insertion is disabled or not configured (the setting is disabled by default).
Workflow
When a smart card is inserted, certificate publication to the GAL is executed after the automatic update of the Microsoft Outlook security profile.
Workflow Steps:
-
Outlook Security Profile Update:
-
If the smart card content is valid, the Microsoft Outlook security profile is updated. For details, see Security Profile Updated Values.
-
-
Certificate Publication to GAL:
-
If the Publish to GAL feature is enabled, ActivClient publishes the user's encryption certificate that has been set in the Outlook security profile to the GAL by updating the following attributes:
-
The userSMIMECertificate attribute of the user's object in Active Directory (certificate in PKCS #7 format):
-
This attribute (defined in RFC 2798) contains the user’s S/MIME configuration.
It is multi-valued and includes the user’s encryption certificate and the user’s signature certificate (all certificate chains).
-
The ActivClient Publish to GAL feature erases the existing content of this attribute and publishes the current user’s encryption and signature certificates.
-
The ActivClient Publish to GAL feature produces the same result as the native Outlook Publish to GAL feature.
-
-
The userCertificate attribute of the user's object in Active Directory (certificate in DER-encoded format):
-
This attribute is multi-valued.
It may contain all user certificates (signature, encryption, logon, EFS, etc) if certificates are issued by Microsoft CA.
-
The native Outlook Publish to GAL feature:
-
Adds new encryption certificates without deleting earlier ones, which may lead to multiple encryption certificates and cause conflicts in some configurations.
-
-
The ActivClient Publish to GAL feature:
-
Erases the existing content of this attribute and publishes the user’s encryption certificate.
This behavior differs from the native Outlook behavior and ensures that the Active Directory configuration matches the local Outlook configuration, enabling secure email exchanges with the most up-to-date certificates.
-
-
-
-
Once the certificate is published, other Exchange users can send encrypted emails without manually configuring the recipient's encryption certificate.
Pin Prompt Cancellation:
If the user cancels the PIN code prompt (when required for updating the userSMIMECertificate attribute), no certificates are published to either the userSMIMECertificate or userCertificate attributes.
Error Handling:
Any errors during the Publish to GAL process are logged in the Windows Event Viewer of the user workstation. No error messages are displayed to the user directly. For further information, see Audit.
-
To limit write operations to Active Directory, ActivClient first reads the existing attributes to check if an update is needed. This verification ensures that the certificate(s) match those configured in the local Outlook security profile.
-
PIN Prompt Behavior:
The smart card is used to sign the certificates in a PKCS#7 format when updating the userSMIMECertificate attribute.
Depending on the PIN caching policy, the user might be prompted to enter their PIN when certificates are published to Active Directory. This happens only if there is a change in the certificate. If the existing certificates in Active Directory are already up to date, no PIN prompt will appear. -
Avoiding Conflicting Updates:
If the ActivClient Publish to GAL feature is enabled, consider disabling the native Outlook Publish to GAL feature to prevent conflicting updates of Active Directory for the userCertificate attribute. You can do so using an Outlook policy; refer to the Microsoft documentation for details.
Environment Considerations
Users must have the necessary permissions to update their Active Directory object. This implies the following:
-
Scenarios where the email account is configured for a different user name than the Windows account user are not supported.
-
If the user is not authenticated to Active Directory, the Publish to GAL will fail.
-
If the Exchange server is configured in cached mode, there might be a delay up to 24 hours before Outlook Web Access (OWA) users can access the updated GAL.
Interactive Publish to GAL Process in the User Console
In addition to the automatic Publish to GAL operations (performed in the background on card insertion), users can manually trigger the process through the ![]() ActivClient User Console.
ActivClient User Console.
This option provides a similar functionality which:
-
Performs both the Microsoft Outlook profile configuration and the Publish to GAL operations as described above.
This occurs regardless of whether the following policies (which control automatic execution) are enabled or disabled:
-
Displays success and error messages via dialog boxes, in addition to logging events in the Windows Event Viewer.
-
Prompts the user to authenticate to Active Directory if required for the operation.
-
Follows the same Certificate Revocation List (CRL) check configurations as used in the automatic mode.
Audit
ActivClient enables the auditing of the two operations described earlier – Outlook security profile configuration and Publish certificate to GAL.
ActivClient audits the successes and failures of these operations and logs them in the Windows Event Viewer.
To be notified of unexpected events, it is recommended that you filter the audited information using the Event Viewer filters.
By default, the ActivClient auditing function is enabled. To disable the option, see Disable audit for Microsoft Outlook security profile creation and Publish to GAL.
The ActivClient events are formatted following Microsoft logging guidelines and are:
-
Logged in the HID Global section of the Applications and Services Logs of the Windows Event Viewer.
-
Labeled with ActivClient as the Source.
Each event contains the following elements:
-
Event Type
-
Information
-
Warning
-
Error
-
Event ID
For the complete list of ID codes, see the below table of Audited Event ID codes List.
-
Event Description:
Specifies the username and domain; and reason of failure when applicable.
To do so, on the domain controller, go to the Default Domain Controller Security Settings, Security Settings, Local Policies, Audit Policy, and enable Audit directory service access.
Then, for each user, specify the attributes that should be audited: open the Advanced Security Settings for the user, Auditing tab, and select Write userSMIMECertificate and Write userCertificate.
For further information, refer to the Microsoft documentation.
Audited Event ID codes List:
| Event ID | Event Type | Category | Description |
|---|---|---|---|
|
257 |
Information |
Outlook Profile Update |
Outlook security profile updated |
|
258 |
Information |
Publish to GAL |
Publish to GAL completed |
|
513 |
Warning |
Outlook Profile Update |
No applicable update |
|
514 |
Warning |
Publish to GAL |
No applicable update |
|
515 |
Warning |
Outlook Profile Update |
CRL check failed for signing certificate for the following reason: Revoked, Offline, or Other |
|
516 |
Warning |
Outlook Profile Update |
CRL check failed for encryption certificate for the following reason: Revoked, Offline, or Other |
|
517 |
Warning |
Publish to GAL |
CRL check failed for signing certificate for the following reason: Revoked, Offline, or Other |
|
518 |
Warning |
Publish to GAL |
CRL check failed for encryption certificate for the following reason: Revoked, Offline, or Other |
|
519 |
Warning |
Outlook Profile Update |
Impossible to reach Active Directory |
|
520 |
Warning |
Publish to GAL |
Impossible to reach Active Directory |
|
521 |
Warning |
Publish to GAL |
Your certificates were not published to the Global Address List.To publish successfully, start the Publish to GAL operation again, and enter the PIN when prompted to do so. |
|
769 |
Error |
Outlook Profile Update |
No Exchange account |
|
770 |
Error |
Outlook Profile Update |
No valid certificate found |
|
771 |
Error |
Outlook Profile Update |
No valid email address in signing certificate |
|
772 |
Error |
Outlook Profile Update |
No valid email address in encryption certificate |
|
773 |
Error |
Publish to GAL |
Access Denied |
|
774 |
Error |
Outlook Profile Update |
CRL check failed for signing certificate for the following reason: Revoked, Offline, or Other |
|
775 |
Error |
Outlook Profile Update |
CRL check failed for encryption certificate for the following reason: Revoked, Offline, or Other |
|
776 |
Error |
Publish to GAL |
CRL check failed for signing certificate for the following reason: Revoked, Offline, or Other |
|
777 |
Error |
Publish to GAL |
CRL check failed for encryption certificate for the following reason: Revoked, Offline, or Other |
|
778 |
Error |
Publish to GAL |
Your certificates were not published to the Global Address List. MAPI error code CAPI error code |