Integration Samples
The solution is delivered with the following Java samples for easy configuration/usage purposes. They demonstrate different aspects of the solution integration.
The samples are available in the SDK\Samples\Push_Authentication_Sample\ folder on the ActivID Appliance Companion delivery disk.
-
Request device registration sample – demonstrates how to request a device registration for a user. It includes the option to specify the HTTP callback for notification.
-
Request operation validation sample – demonstrates how to send an approval validation message to a user’s mobile device (smartphone or tablet).
- OpenID API request samples for offline validation - demonstrates OpenID Connect REST API requests to authenticate the end user or perform offline transaction signing when the HID Approve device is offline.
-
jmslistener sample – demonstrates how to retrieve the result of device registrations or operation approval message through JMS notifications.
-
Registration Listener sample – a sample web application that demonstrates how messages are posted to the HTTP callback URL when a device registration succeeds.
-
CIBA Demo Portal sample – a sample web application that demonstrates how to send an approval request using CIBA and waits/listens for the mobile device approval result on its CIBA HTTP callback (endpoint/servlet).
These samples include:
-
Full source implementation
-
All of the required 3rd party libraries binaries
The samples are designed to enable developers and integrators to test the entire solution, as well as the HID Approve application.
Source code can be re-used to develop a Web Bank Portal application that makes use of the ActivID Appliance push-based validation feature.
The samples code uses ActivID OAuth/OpenID Connect API and ActivID SCIM API to interact with ActivID Appliance server:
ActivID Appliance configured as described in Configuring the Solution.
The Microsoft Azure Notification Hub is configured with Information from HID Global.
ActivID Appliance server must be accessible from the mobile device.
The HID Approve application is installed on the mobile device (smartphone or tablet).
You have the:
- Certificate of your ActivID Appliance server.
- Hostname and port number of your ActivID Appliance server.
A direct user is configured with a valid login authenticator and the required permissions (for example, the spl-api predefined user can be used).
The direct user must be defined as the OpenID Client:
The ActivID OAuth/OpenID Connect API requires that client applications are registered on the ActivID Appliance.
This registration process includes a configuration that defines the ActivID Appliance channels and authentication policies to be used for this client application.
Client application definitions are added by configuring Adapters using the ActivID Management Console.
The default data set includes a pre-defined user (spl-api) as the OpenID client application (direct user authenticating though CH_DIRECT channel and AT_SYSLOG authentication policy).
The following image illustrates the default configuration.
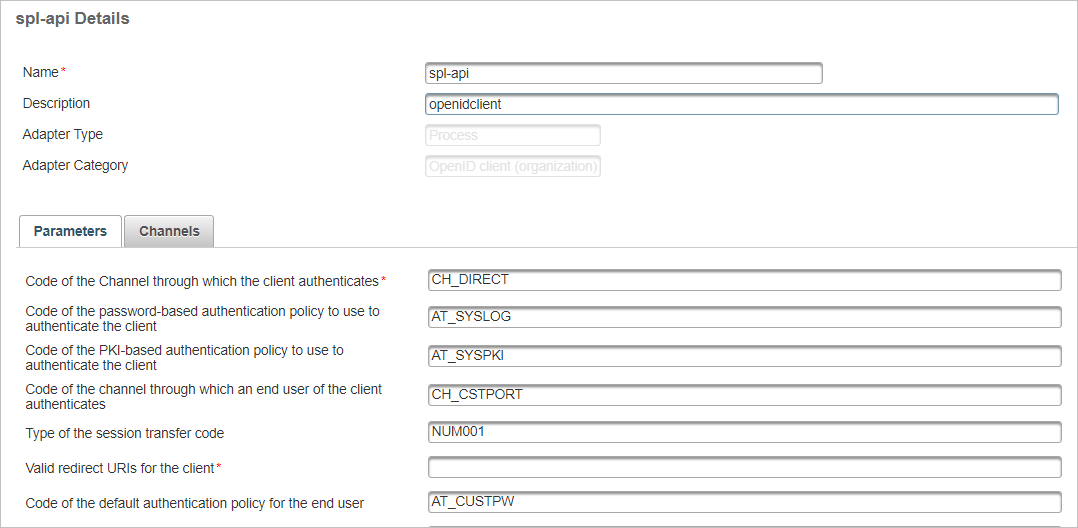
You can use a sample client definition to implement the request registration workflow and the request Action or Logon workflow.
Note:Customize the expected channel and authentication policy for end users (instead of CH_CSTPORT and AT_CUSTPW) according to users group configuration used by your application.
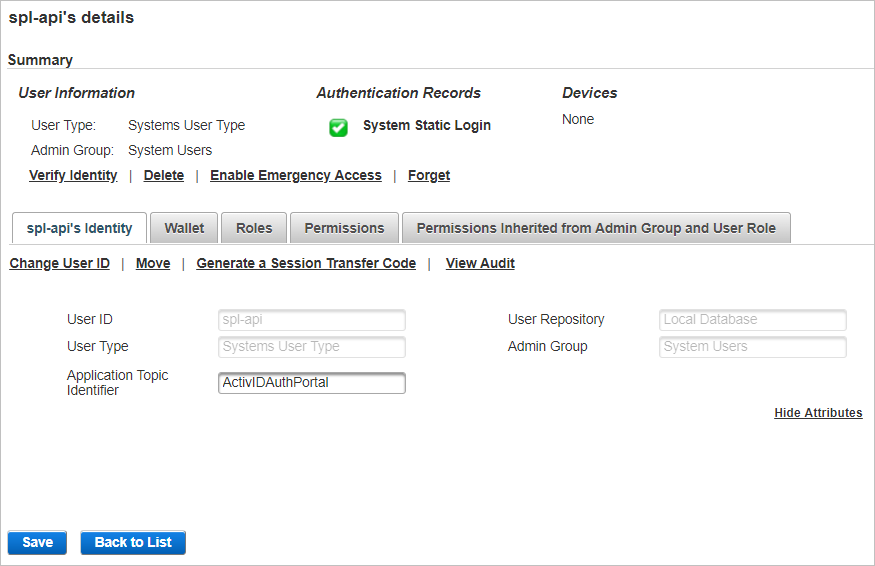
If your application uses a specific direct user (instead of the default spl-api user), register (add) a configuration for this user in the ActivID Management Console.
The direct user should have JMS topic Identifier configured in their user attributes (see example below when using spl-api direct user).
Topics in this section:





