Approve Logons or Actions
The HID Approve application offers the convenience and security of:
-
Logon validation – push-based authentication using notifications
-
Action validation – push-based transaction signing using notifications
The logon or action parameters are passed to the application through a notification, allowing the user to sign this data with their private key.
The look and feel of the notifications can be customized to meet your branding/deployment requirements.
To use biometric authentication as the key protection method, the option must be enabled.
Approve a Logon Request
-
The user logs on to your bank’s web portal using their credentials.
- The banking application calls ActivID Appliance to submit the Logon validation data and deliver a challenge to the user’s mobile device via push notification. This call contains the:
- User ID
- Device ID
- Logon message to be displayed
- Possible approval status
- ActivID Appliance generates an OOB message and sends it to the selected device via a push notification. The OOB message is encrypted with the device transport key and contains the:
- Challenge (Logon request) Identifier
- One-time password (OTP)
- Security domain, channel and authentication details
- Device ID
-
The HID Approve application receives the push notification:
-
It decrypts the OOB message using its transport key and recovers the:
- One-time password (OTP)
- Security domain, channel
- Device serial number
-
It calls the HID Approve SDK to retrieve the Logon validation data.
-
The HID Approve SDK generates the Logon validation data retrieval request encrypted using the transport key and submits it to ActivID Appliance. It contains the:
- Challenge Identifier
- One-time password (OTP)
- ActivID Appliance verifies the one-time password and retrieves the stored Logon validation data and the Status options.
- The Logon validation data (encrypted with the device transport key) and the Status options (plaintext) are sent back to HID Approve via ActivID Appliance and the HID Approve SDK.
If the one-time password has expired, due to a delayed notification, then the authentication will fail.
-
-
The user accesses the notification content:
- If the application is already open:
- The notification content is displayed immediately if the service is not protected by a password or biometric.
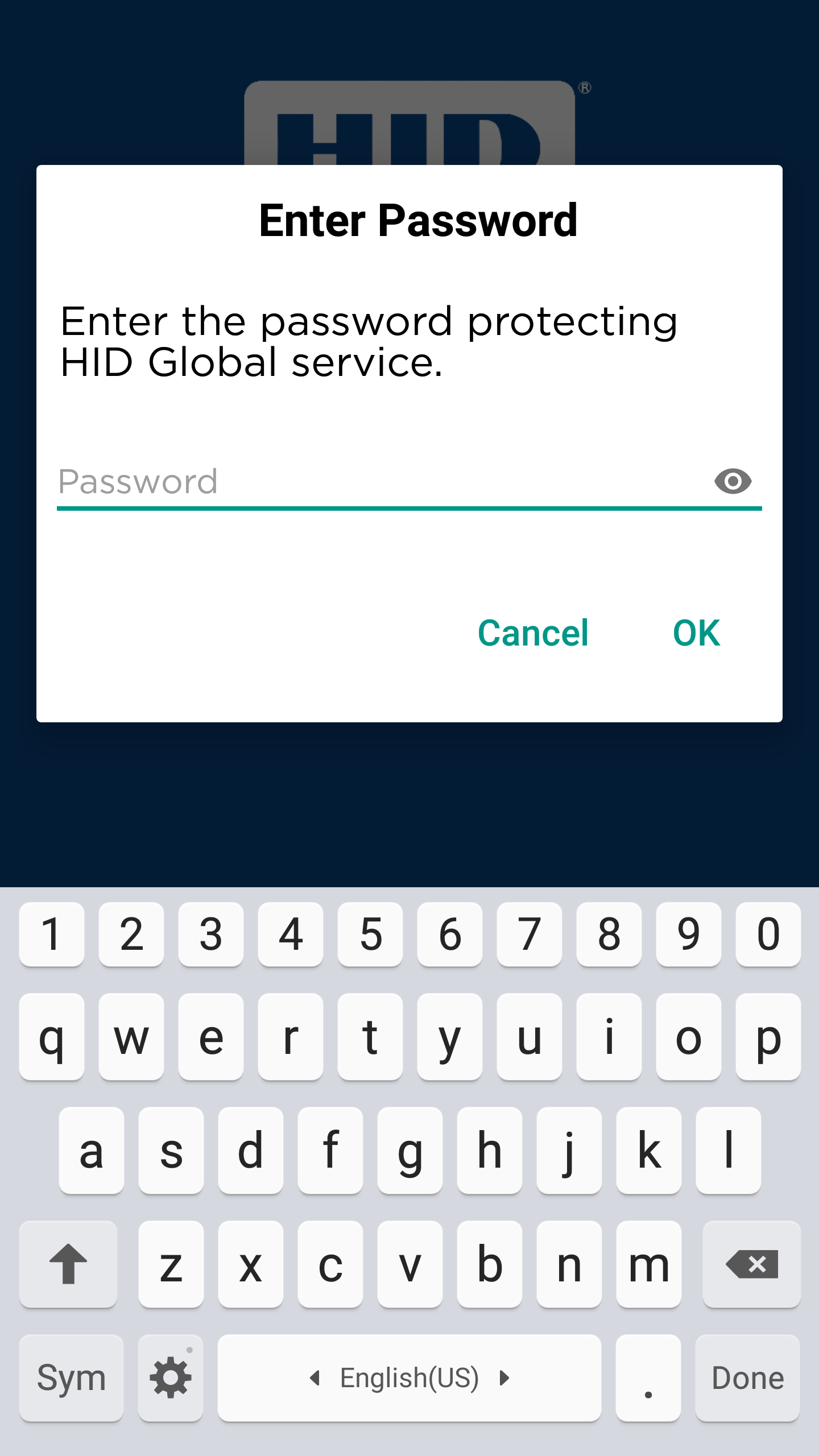
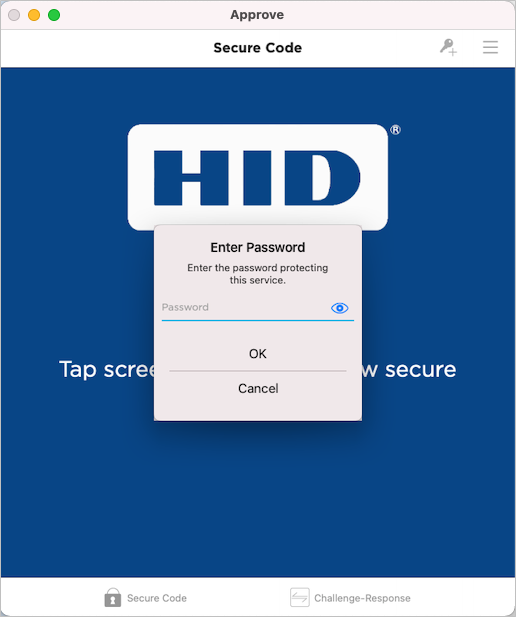
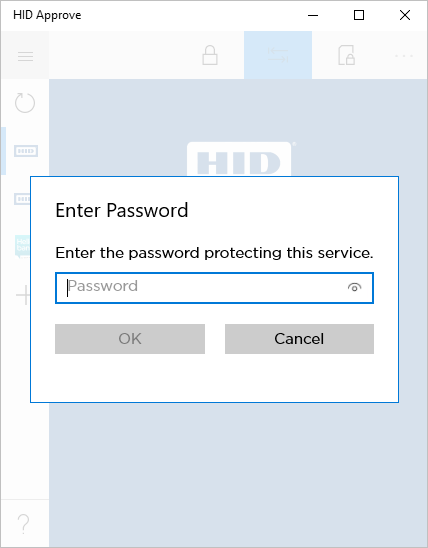
- Otherwise, the user is prompted to enter his password or biometric.
- If the application is closed:
- The user selects the notification.
- The application starts and the notification content is displayed immediately if the service is not protected by a password or biometric.
- Otherwise, the user is prompted to enter his password or biometric after the application starts.
Password prompt:
iOS/Android
macOS
Windows 10
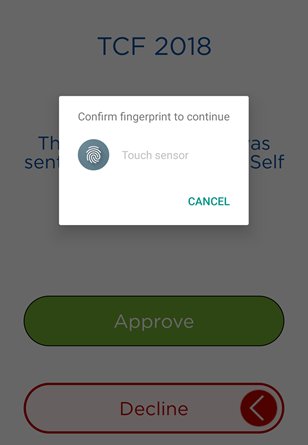
Biometric prompt (Android, iOS and macOS only):
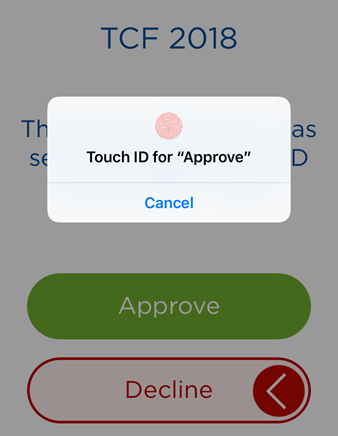
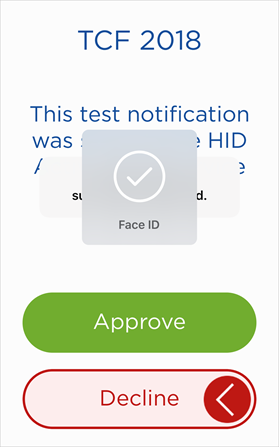
- If the application is already open:
-
The user enters the password and taps OK, or provides their biometric credential (fingerprint/face).
-
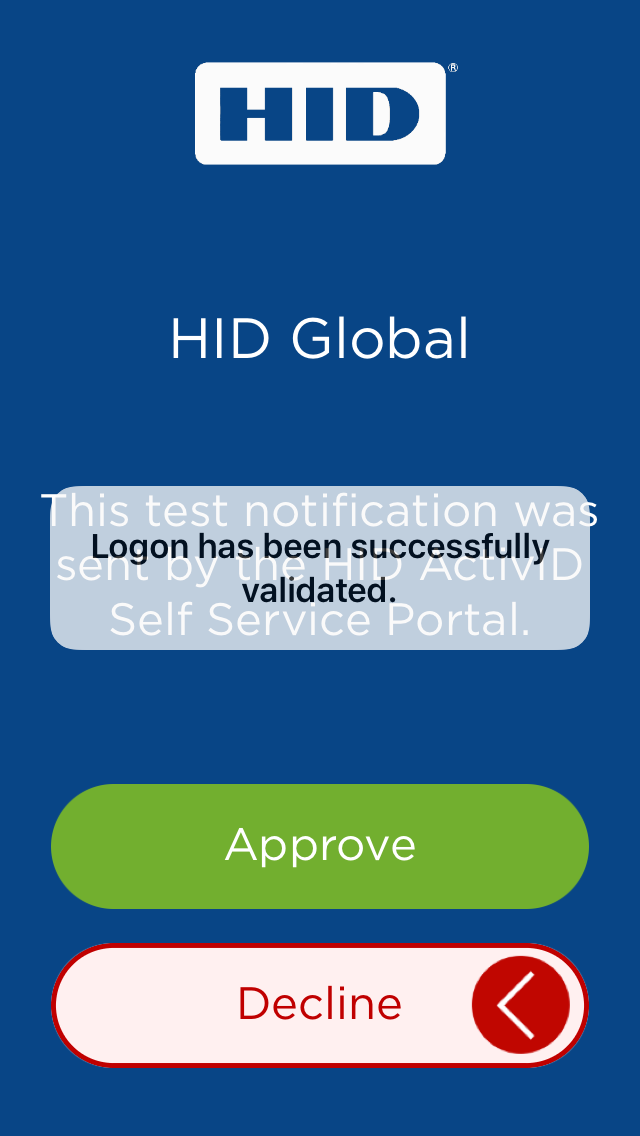
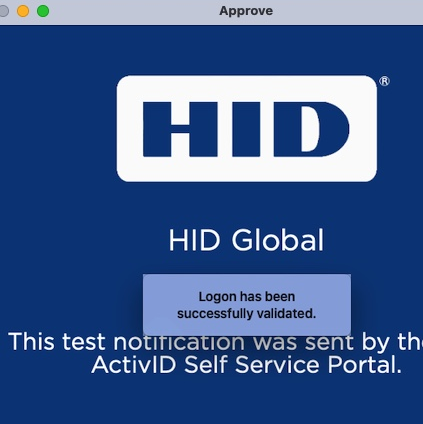
The HID Approve application displays the Logon validation data to the user and asks the user to select one of the Status options (that is, Approve or Decline).
-
The user reviews the notification content.
iOS/Android
macOS
Windows 10
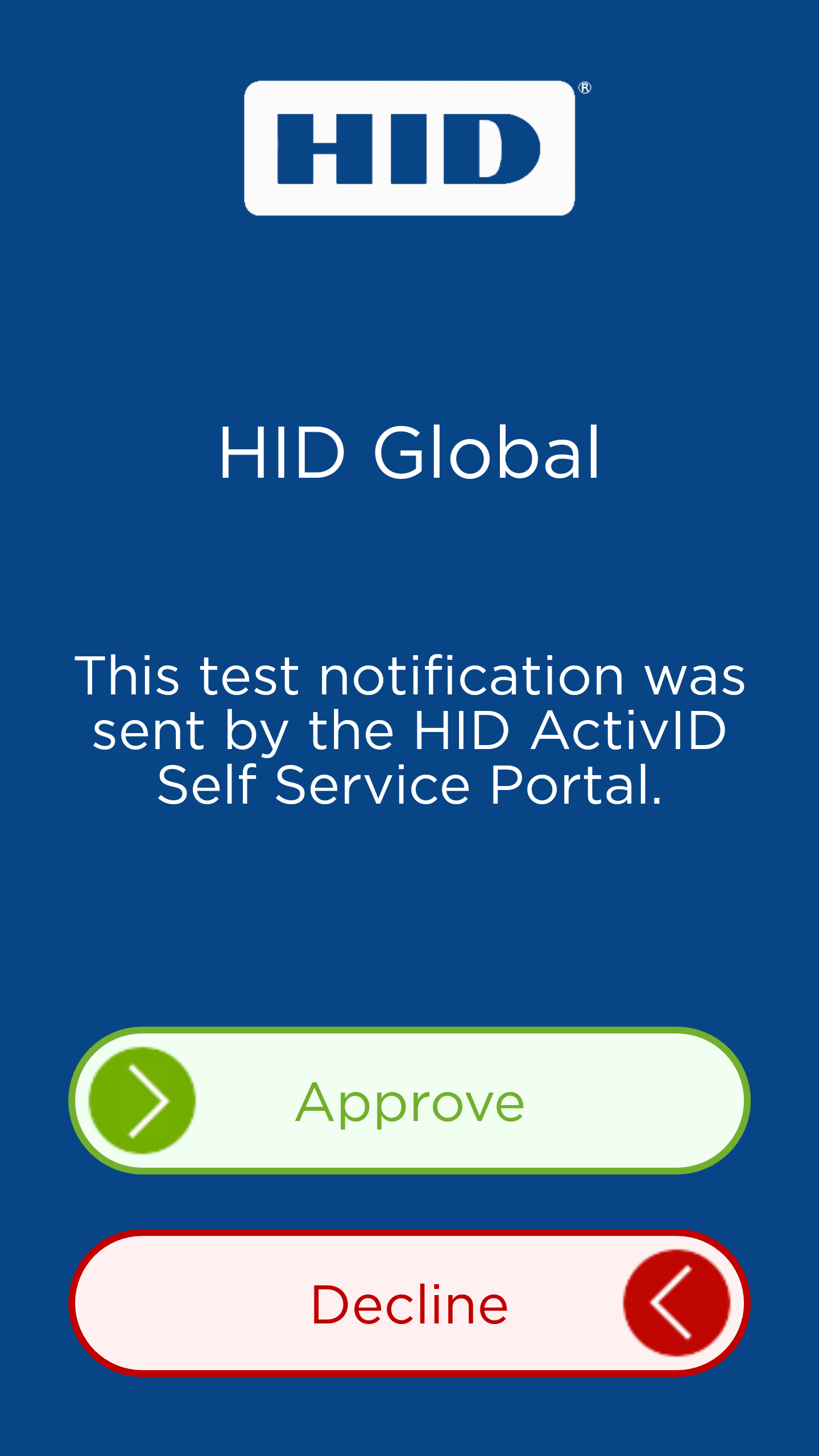
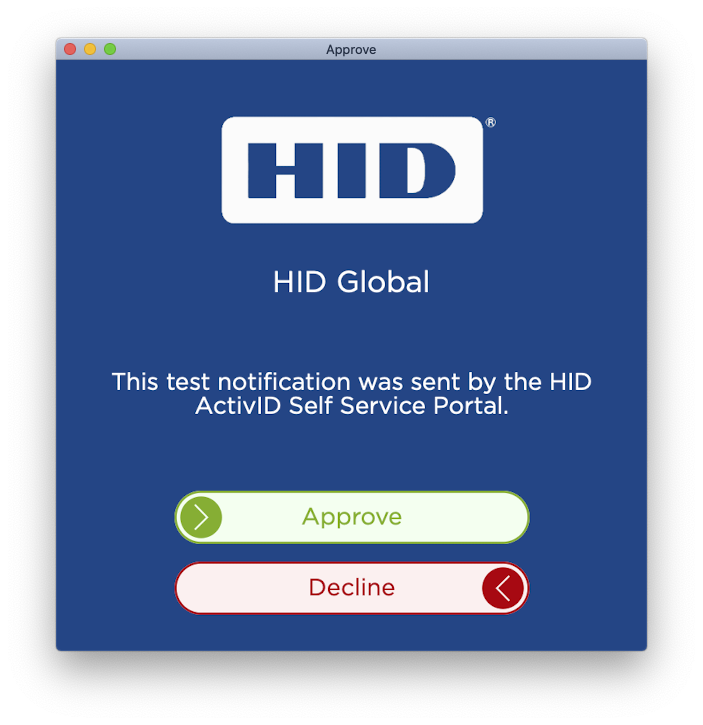
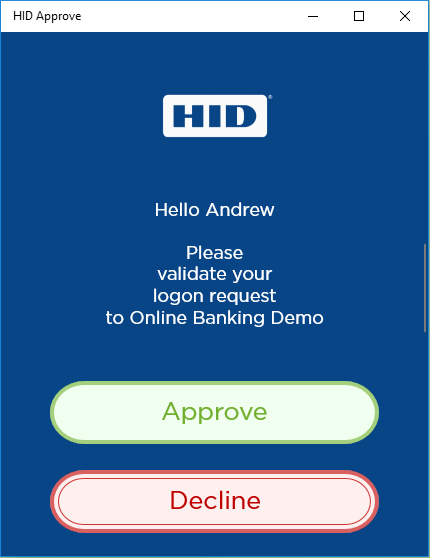
-
The user swipes the Approve button from left to right.
-
If the application was open before the notification, the previous screen is displayed.
- The HID Approve application calls the HID Approve SDK to sign the Logon validation data and set the Status for the transaction (that is, Approve or Decline).
- The HID Approve SDK signs the Logon validation data and Status with the user’s private key.
- This data, encrypted with transport keys, is submitted to ActivID Appliance for validation.
- ActivID Appliance validates the signed Logon validation data.
- Upon completion of the signature validation, an ActivID Appliance audit entry is created and a notification is raised.
The following data is audited in ActivID Appliance:
- Logon validation data
- Signature value
- Public key component of the private key used to sign the Logon validation data
- User ID and device ID
- Correlation ID (that is, external transaction ID)
The Logon validation data is deleted even if the authentication has failed for some reason.
Other Logon validation data pending for that user is not deleted.
- The result of the signature validation is sent back to HID Approve via ActivID Appliance and then to the HID Approve SDK.
- ActivID Appliance notifies the bank web portal application of the outcome of the push-enabled authorization process. (The portal will have been waiting for either this notification or a timeout.)
- The portal informs the user of the outcome of the push-enabled authorization (for example, by displaying the home page for the user).
-
The user can then access the banking application.
-
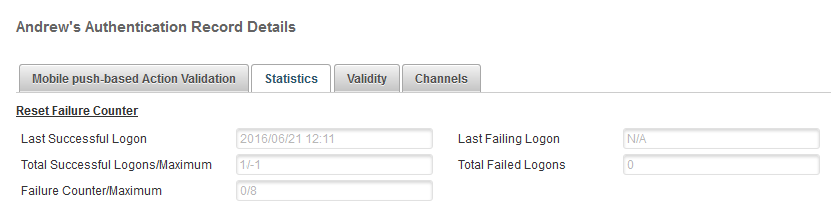
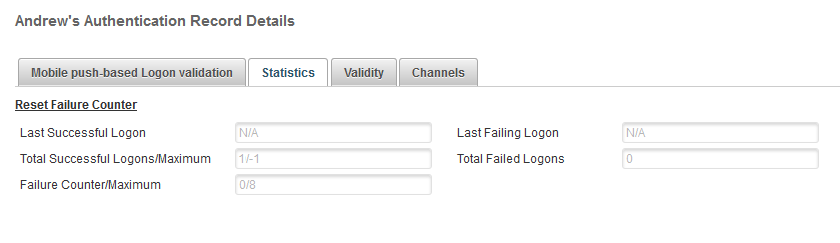
Log on to the ActivID Management Console to check the user’s statistics.
The push notification is then sent to the mobile device.
The success message is displayed.
|
iOS/Android |
macOS |
Windows 10 |
|
|
|
|
Optionally, the Password Caching option can be disabled to allow the user to view the notification content immediately. In this case, the password or biometrics are entered after the user has swiped Approve or Decline. For further information, see Key Protection Policy Parameters.
If the application was closed/in background before the notification, the application fades back into the background.
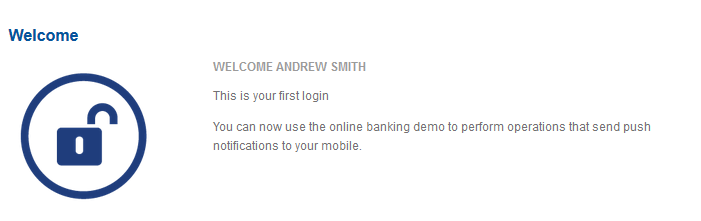
The user is automatically logged in to the web application.
Approve an Action
-
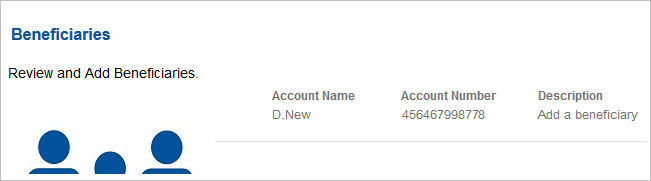
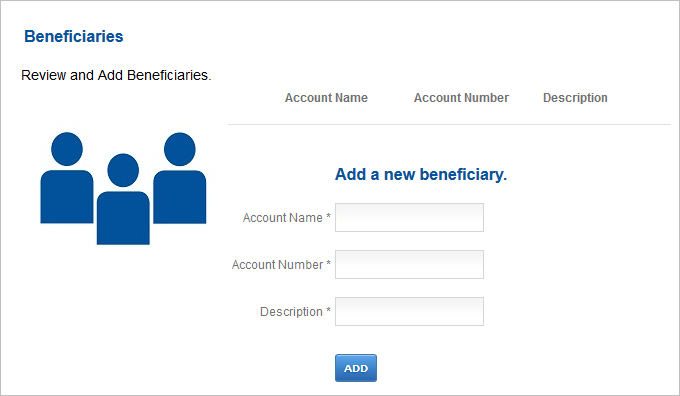
The user logs on to your bank’s web portal and requests an action (for example, to add a beneficiary).
-
The action approval workflow is the same as that for the logon request approval as described in Approve a Logon Request.
-
When the action has been approved, the user returns to the banking application and verifies that the beneficiary has been added.
-
Log on to the ActivID Management Console to check the user’s statistics.
A notification is sent to the user’s device.