Configure Syslog Monitoring
The ActivID Appliance Syslog function can be configured to send audit events and system notifications to an external Syslog server:
- Audit events – events to log can be filtered using a regular expression on audit EventID (for example, ^.*Authenticate.*$ can be used to send the authentication audit events).
- System events – same events as sent as SNMP notifications.
Each type of event is managed separately so only one type can be sent to the Syslog server (for example, system events (Enabled) but not the audit events (Disabled)).
<EVENTDATE> <HOSTNAME> <DOMAIN>||<CHANNEL>|<MESSAGE>|<USERID>|<ALSI>|<STATUS>|<TARGETUSERID>|< RESPONSE>|<PALSI>|<AUTHTYPECODE>|<CORRELATIONID>|<EVENTTYPE>|< CORRELATIONTYPE>|<EVENTID>|<ENTITYID>|< ENTITYTYPE>|<HOSTADDRESS>|<TEXT1>|< TEXT2>|<TEXT3>|<TEXT4>|<TEXT5>|<TEXT6>|<TEXT7>|<TEXT8>|<TEXT9>|<TEXT10>|<DIRECTEXTREF>|< INDIRECTEXTREF><PARAMETERS>
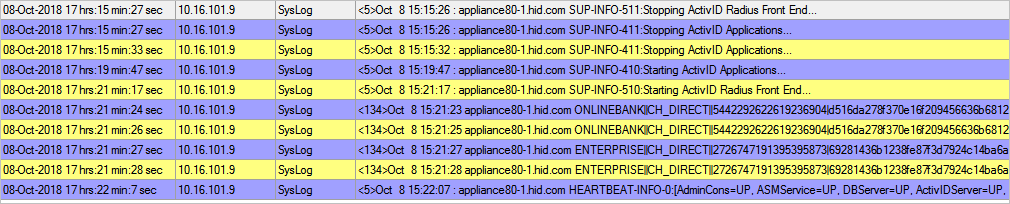
For example, an audit event for an authentication:
May 30 10:21:42 cbl.hidps.xyz MYDOMAIN||CH_WEB||8270620930151440364|f470360389015eea377ba254c19ad8da893dd35ef6d4dd65b4dfea1c3842916c|RESPONSE_SUCCESS|8270620930151440364|SUCCESS||AT_CUSTPW||||primaryAuthenticateUP|||e58fc828-c0ba-4450-8ddd-1156f6229a10|||||||||||5048f1a7-cda5-42d2-bffb-b672a6cec47b|5048f1a7-cda5-42d2-bffb-b672a6cec47b|{"ATC":"AT_CUSTPW ","USN":"null","Action":"primaryAuthenticateUP","ANS":"false","ARP":"","AUS":"ENABLED"}
| Name | Data type (Max length) | Description |
|---|---|---|
|
EVENTDATE |
Char(19) |
Date and time of event |
|
HOSTNAME |
Char(255) |
Hostname FQDN that generated the Syslog event |
|
DOMAIN |
Char(20) |
Security domain on which the action was performed |
|
EVENTID |
Char(50) |
Identifier of the event that is audited |
|
EVENTTYPE |
Char (10) |
Type of event that is audited |
|
USERID |
NUMBER (28) |
Identifier of the direct user who executed the action |
|
DIRECTEXTREF |
Char (255) |
External Reference ID of the direct user who executed the action |
|
CHANNEL |
Char (30) |
Channel over which the action was requested. |
|
AUTHTYPECODE |
Char (10) |
Authentication Type code for authentication and administrative activities that relate directly to a specific authentication type |
|
STATUS |
Char (30) |
Indicates if the call successfully completed. Note that a failed authentication is still considered to be a successfully completed call. |
|
RESPONSE |
Char (50) |
Indicates if the authentication request succeeded or failed (this field is only populated for authentication requests). |
|
MESSAGE |
Char (100) |
Free text field used to store additional information in exceptions |
|
ALSI |
Char (100) |
Session ID of the direct user who executed the action |
|
HOSTADDRESS |
Char (512) |
Hostname or IP address of the remote system that performed the action being audited |
|
TARGETUSERID |
Num (28) |
Id of the user on whom the action was executed (obfuscated) |
|
INDIRECTEXTREF |
Char (255) |
External Reference ID of the indirect user on whom the action is being executed (obfuscated) |
|
PALSI |
Char (100) |
Session ID of the indirect user. This field is only populated for indirect user authentications and logouts |
|
PARAMETERS |
Char (3000) |
Contains additional parameter values specific to the action (some parts are obfuscated) |
|
CORRELATIONID |
Char (200) |
Identifier of the process from which the action was performed from a remote system |
|
CORRELATIONTYPE |
Char (10) |
Type of process from which the action was performed from a remote system |
|
ENTITYTYPE |
Char (10) |
Type of object that is audited from the remote system |
|
ENTITYID |
Char (20) |
Identifier of the object that is audited from the remote system |
|
TEXT1/TEXT2 …/TEXT10 |
Char (100) |
Additional fields containing information provided from the remote system that is audited. |
- The appliance uses Syslog user-level messages (Syslog facility user). You must make sure the Syslog messages traffic is correctly secured.
- You can only define one Syslog server for the appliance. If required, you must configure a relay Syslog server if you need to send log events to multiple Syslog servers.
- The Syslog function is disabled by default.
- The appliance does not check if the CA root certificate of your Syslog server (required for TLS/mTLS connections) has been imported into the appliance truststore.
- Enabling Syslog might generate significant logging data (especially with audit events) and could impact the performance of the appliance.
-
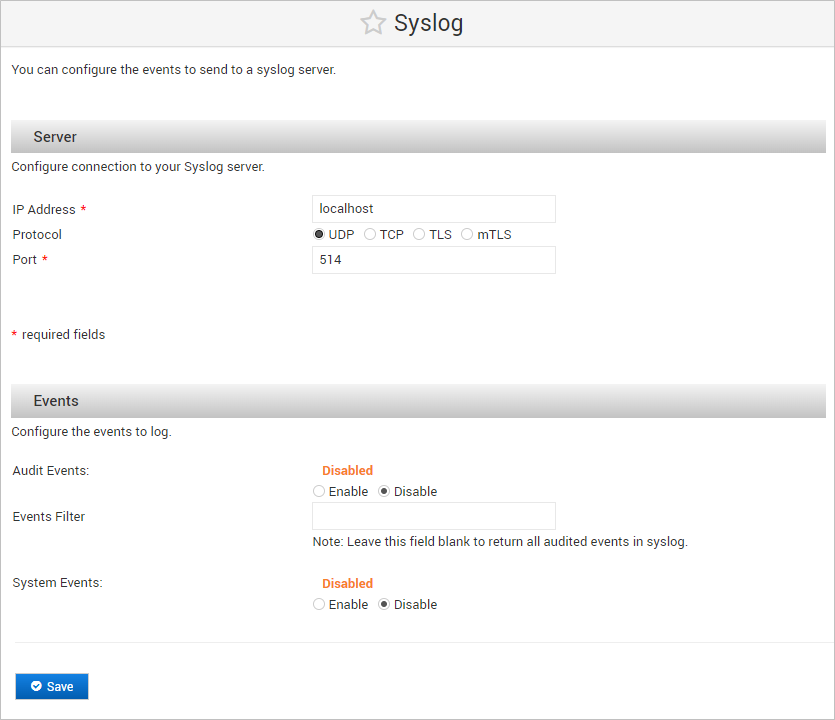
Log on to the ActivID Console and, under Monitoring in the left menu, select Syslog.
-
In the Server section, configure the connection to your Syslog server:
- Enter the IP Address.
- Select the required Protocol.
- Enter the Port number.
The default protocol ports are:
- UDP - 514
- TCP - 601
- TLS/mTLS - 6514
- If you are using the mTLS protocol:

Upload the client certificate (.p12) and enter the corresponding password.
Note: If there is an existing certificate configured for the connection, you can View the certificate's details or Change the certificate by uploading a new one.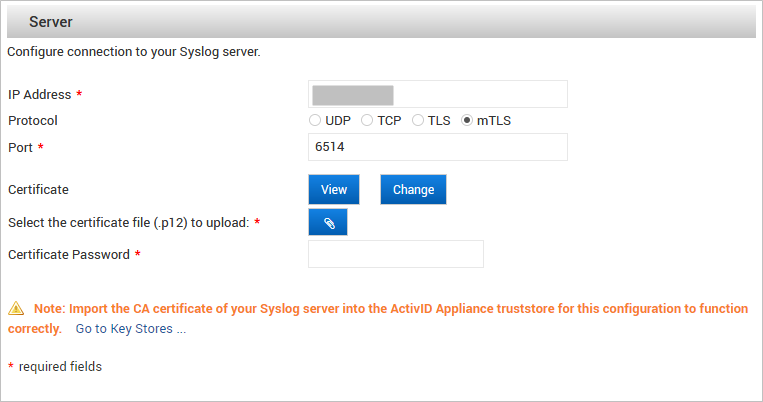
- In the Events section, select the type of appliance event data you want to send to your Syslog server by selecting Enable for Audit Events and/or System Events.
-
Click Save to apply the configuration.
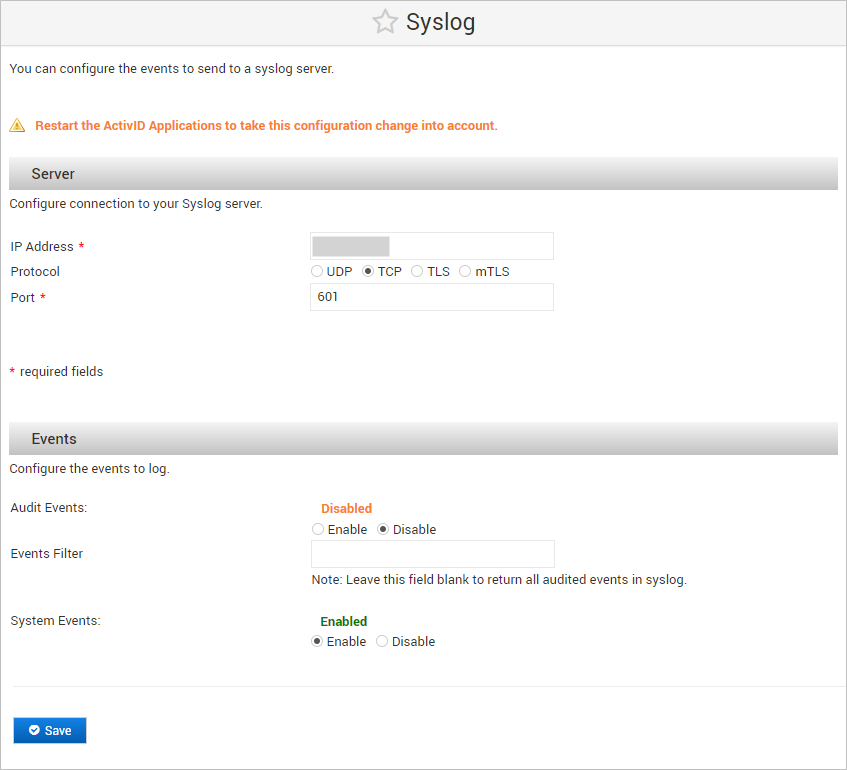
In addition, for Audit Events, you can filter the type of audited event.
For example, to send only authentication events, add the ^.*Authenticate.*$ filter.
The following illustration is an example of notifications: