Manage the Keystores and Certificates
The location of the ActivID Appliance keystore (containing the certificates and keys) depends on the cryptographic type:
| Cryptographic Type | ||
|---|---|---|
| Credentials |
Software |
External HSM |
|
SSL server keys/certificates |
Soft Key Store |
Soft Key Store |
|
IdP keys/certificates |
Soft Key Store |
HSM |
|
ActivID portals direct users keys/certificates |
Soft Key Store |
Soft Key Store |
|
ActivID database keys |
Soft Key Store |
HSM |
From the ActivID Console Key Stores configuration page, you can:
- View and manage CA certificates required for SSL Client authentication, Trusted IdP interaction, and Service Providers interaction.
- View and manage your private certificates and eventually update them with certificates issued by a CA.
This includes updating the certificates before they expire to avoid an interruption of service.
As a best practice, it is strongly recommended that you implement policies and procedures to:
-
Monitor the certificates (expired, revoked or compromised) with automated notifications
-
Regularly maintain and update certificates with a defined renewal strategy
-
Identify a role (either an individual or team) who is responsible for certificate management according to your organization’s security policies and compliance requirements
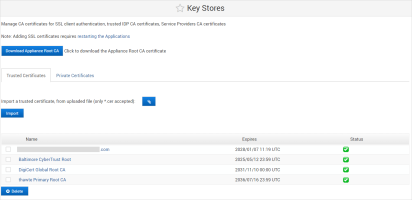
Manage the Trusted CA Certificates
A list of Trusted CA certificates for SSL authentication is available by default in the Trusted certificates key store. You can add or delete certificates as needed.
-
Log on to the ActivID Console and, under Configuration in the left menu, select Key Stores.
-
To download the appliance’s self-signed root CA key store certificate, click Download Appliance Root CA.
-
To add Trusted CA certificates, browse to the certificate file and then click Import.
-
To delete CA certificates, select the certificate, click Delete, and then confirm the action (not illustrated).
This certificate can be imported into the key store on other appliances in order to create a trusted relationship. For example, to trust a back-end appliance on a front-end appliance, and vice versa.
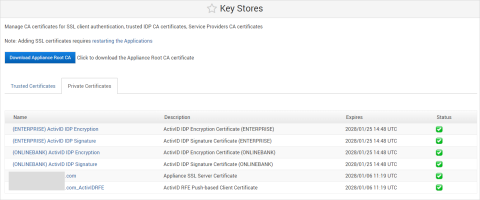
Manage the ActivID Appliance SSL Server Certificate
The ActivID Appliance SSL server certificate is used to identify the server in SSL client authentications.
The default certificate is signed by the appliance root CA certificate and valid 10 years. You can download it from the ActivID Console key store and also update it with a CA signed certificate of your choice.
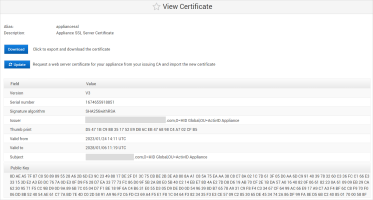
Download the Default Self-signed Certificate
-
Log on to the ActivID Console and, under Configuration in the left menu, select Key Stores.
-
Select Private Certificates.
-
Select the Appliance SSL Server Certificate for your server.
-
Click Download and then import the root CA certificate of this certificate into the trusted CA store of your client browser.
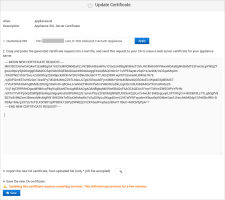
Update the Appliance SSL Certificate
To update the appliance server SSL certificate, request a certificate from your issuing CA, and add it to the truststore.
-
Log on to the ActivID Console and, under Configuration in the left menu, select Key Stores.
-
Select the SSL certificate name from the list of certificates.
-
Click Update.
-
Copy and paste this request into a text file, and send this request to your CA to issue a web server certificate for your appliance server.
- When copying the certificate request, highlight all the text including the ---BEGIN and End --- headers.
- The certificate must be in the P7b format using base-64 encoding, and include the full certification chain.
-
In the Key Stores page, select the Trusted certificates tab and click Import to add the new issuing CA certificate to the trusted certificates key store.
-
Click Save to update the key store.
-
If you have deployed the ActivID RADIUS Front End, click Restart RADIUS Front End in the ActivID Applications page.
-
After successfully importing the certificate, restart the appliance.
Alternatively, follow your organization's procedure to obtain a CA-signed web server certificate for use.
Manage ActivID IdP Signature and Encryption Certificates
ActivID IdP signature and encryption certificates are used for SAML exchanges between the ActivID IdP and Service Providers.
Sample certificates are signed by the appliance root CA.
If the appliance is deployed with an external HSM, you must update the certificates manually in your HSM. Refer to the technical documentation provided with your HSM for details.
If the appliance is deployed with software cryptography, you can use the ActivID Console menu to update these certificates.
You can download the signature and encryption certificate using the ActivID Management Console.
The Import option will not be available. After you have added them to your external HSM, restart the ActivID Console to view them in the key store.