Mutual Transport Layer Security (mTLS) authentication is supported for:
- OpenID clients
- PKI certificate import
- Other OpenID client PKI authentication methods (JWT)
Using the certificate extracted from the TLS connection, the ActivID Appliance mTLS validation flow is as follows:
- Validate the certificate trust path.
- Validate the certificate status (using CRL or other mechanisms such as OCSP).
- Validate the certificate binding:
- OpenID client JWT authentication - verify of the JWT signature
- OpenID or end-user PKI certificate matching - validate the rules with user information
- OpenID or end-user PKI certificate check - verify the TLS certificate matches the registered user certificate
- The OpenID client should have a valid PKI credential (type certificate check).
- The root certificate of client credential should be trusted by ActivID Appliance server as the certificate path and revocation status will be validated by server.
- The token request should be sent via a TLS connection with mutual authentication.
- The root certificate should be imported into the ActivID Appliance server truststore.
- When creating PKI credential, the PKI certificate to be imported should contain certificate chains (PEM or P7b) to be validated until the root certificate.
The first certificate in the chain must be the end user certificate.
The certificate path and revocation status are now checked when importing the certificate and at authentication (CRL check can be deactivated by the ActivID Appliance server’s configuration file). This certificate chain will also be persisted in the database to allow certificate path validation at authentication.
-
Create an OpenID client with a valid PKI credential:
-
Log on to the ActivID Management Console as an ActivID Administrator (for example, ftadmin).
-
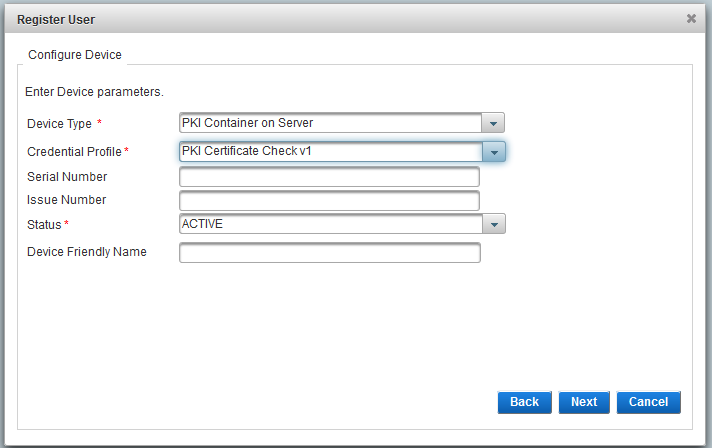
Click Register User and then proceed through the wizard to create a user with a PKI credential.
-
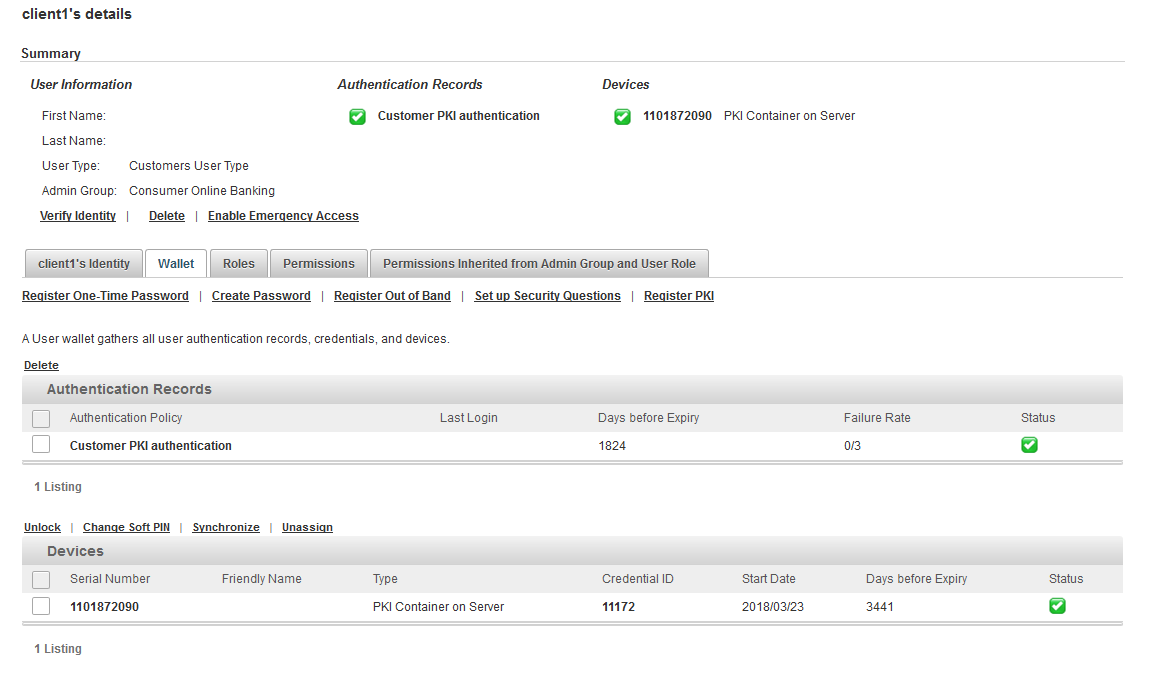
In the client’s details page, select the Wallet tab and verify that the PKI authenticator is configured correctly.
-
In the Configuration tab, under Environment, select Adapters and click Add.
-
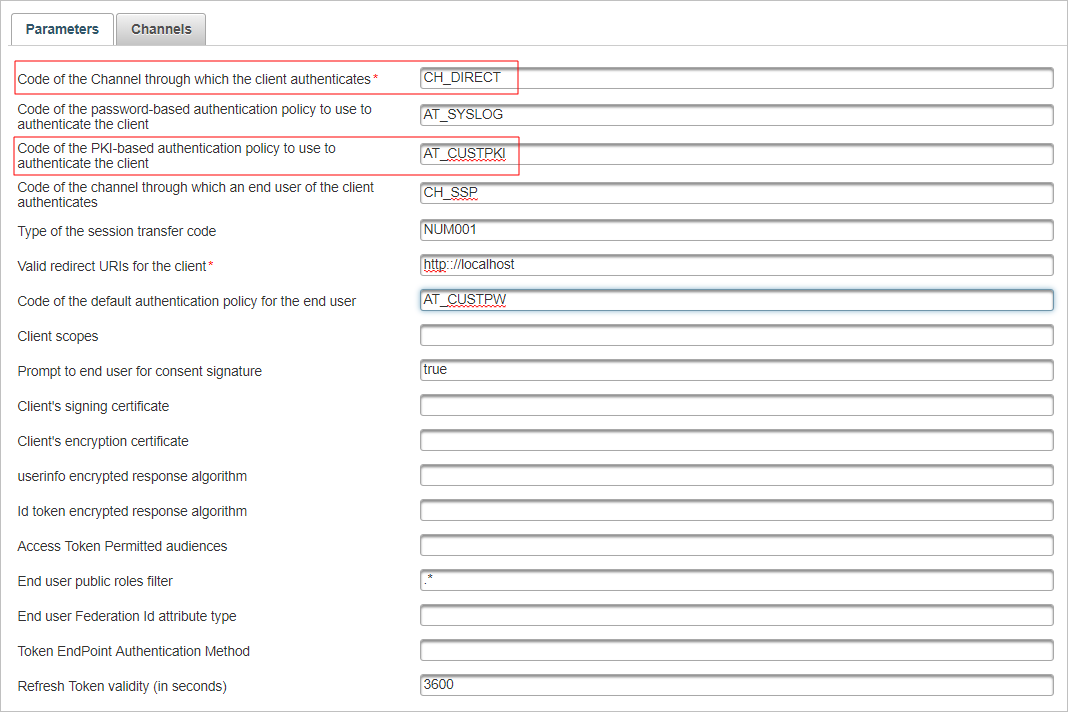
Create an OpenID client adapter with corresponding parameters (see Create an OpenID adapter – with same name as the "OpenID administrator":).
-
In the Configuration tab, under Environment, select Authentication Policies and select the policy configured for the OpenID client PKI authenticator (in this example, Customer PKI authentication).
-
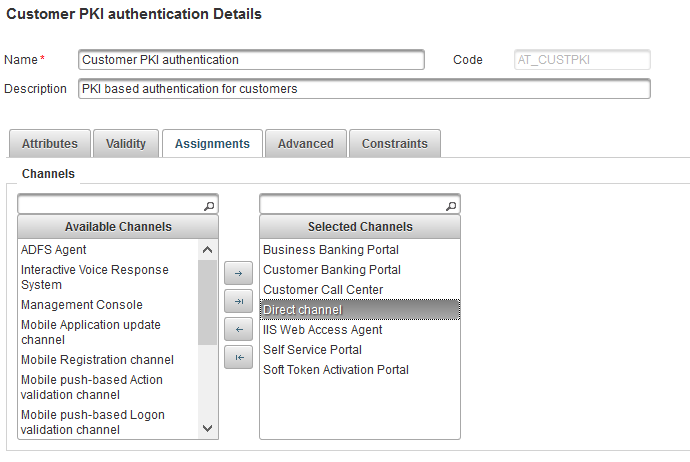
Select the Assignments tab and verify that OpenID client can authenticate via the configured channel.
-
Select the Constrains tab and verify that OpenID client can authenticate with the registered credential.
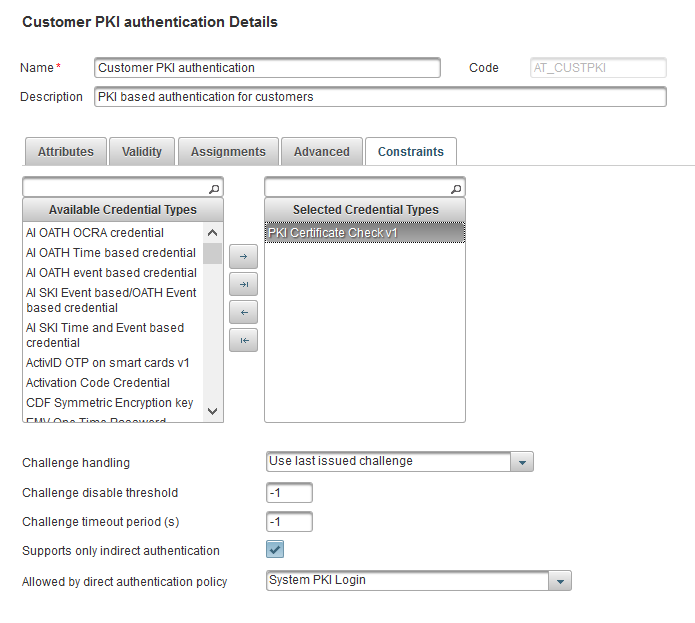
-
-
Send a token request to the token endpoint via an TLS connection with mutual authentication.
The ActivID Appliance server’s token endpoint which supports TLS mutual authentication listens on different TCP ports (such as 443, or 8443) depending on your deployment.
For example:
https://<host name>:443/idp/<Domain>/authn/token
CopySample token request using OpenID’s ‘self_signed_tls_client_auth’ authentication method with client_credentials grant with client PKI authentication using a mTLS authentication connection to the token endpoint
POST https://[base-server-url]/{tenant}/authn/token HTTP/1.1
Content-Type: application/x-www-form-urlencoded
grant_type=client_credentials&client_id=client1&scope=openidNote: The token endpoint accepting mTLS authentication connection might be using another port, such as 8443, and the root CA certificate of client’s certificate should be stored in the ActivID Appliance truststore.CopySample token request with a HID custom grant type client_secret_pki with client authentication certificate used in a mTLS authentication connection to the token endpoint
POST https://[base-server-url]/{tenant}/authn/token HTTP/1.1
Content-Type: application/x-www-form-urlencoded
grant_type=urn:hid:oauth:grant-type:client-secret-pki&client_id=client1See Mutual TLS Profiles for OAuth Clients
CopySample response
HTTP/1.1 200 OK
Cache-Control: no-store
Content-Type: application/json;charset=UTF-8
{
"access_token": "m8kwawAAAWWLVMh0jZ1DXLwiTag2nsC6iWdH5wcb",
"context": {"LEVEL_OF_ASSURANCE": "2"},
"token_type": "Bearer",
"expires_in": 84600
}





