Preparing an Entrust HSM for the ActivID Appliance
Install and configure your Entrust nShield Connect HSM (refer to the technical documentation provided with your HSM):
The recommended firmware version is 12.60.11
This version is part of Entrust Security World Software for nShield distribution
You have the CD containing the Entrust Security World Software for nShield (recommended version is 12.60.11) that needs to be installed on the RFS
You have the following client licenses for Entrust nShield Connect HSM:
One license for the RFS (HSM Remote File System)
One license per ActivID Appliance in your deployment
For example, in a High Availability deployment, you need three licensees – one for the RFS and one for each of the two appliances.
Configure the HSM and the RFS
This section describes the basic configuration steps to configure the HSM and RFS.
For complete instructions, refer to the technical documentation provided with your HSM.
-
On the HSM:
-
On the RFS:
-
Install the Security World Software.
The following is an example of a shell script to automate the installation if the Security World Software payload (for example, folder “linux/libc6_11”) is copied into the <NSHIELD_DISTRIB> folder defined in the script.
Copy#!/bin/sh
NSHIELD_DISTRIB=/WORK/nShieldConnect
NFAST_HOME=/opt/nfast
# Create nfast and ncsnmpd system users
useradd -r -m -d $NFAST_HOME -s /bin/bash -c "nFast" nfast
useradd -r -m -d $NFAST_HOME -s /bin/bash -c "nFast" ncsnmpd
# untar distribution
cd /
find $NSHIELD_DISTRIB -name '*.tar' -exec /bin/tar xf '{}' \;
# install
$NFAST_HOME/sbin/install || {
echo "fail to install nShield Connect Security World Software"
}
chown -R nfast:nfast $NFAST_HOME -
Add a firewall rule to open 9004 inbound TCP port.
-
Switch to the nfast user account.
Copysu - nfast -
Check that the HSM is operational using the following command (output of the command should show “mode operational” for the “Server” section):
Copy./enquiry -
Retrieve the ESN and keyhash of the HSM using the following command:
Copyanonkneti <HSM-IP> -
Create the RFS directory structure using the following command:
Copyrfs-setup --force <HSM-IP> <HSM-ESN> <HSM-KNETI-hash>CopyFor example:
$> rfs-setup --force 10.16.96.149 FFDF-E4F6-9787 b4cdac0cb25c2326c3de1886b8fb205d119529f0
Adding read-only remote_file_system entries
Ensuring the directory /opt/nfast/kmdata/local exists
Adding new writable remote_file_system entries
Ensuring the directory /opt/nfast/kmdata/hsm-FFDF-E4F6-9787 exists
Ensuring the directory /opt/nfast/femcerts exists
Ensuring the directory /opt/nfast/kmdata/hsm-FFDF-E4F6-9787/features exists
Ensuring the directory /opt/nfast/kmdata/hsm-FFDF-E4F6-9787/config exists
Ensuring the directory /opt/nfast/log/hsm-FFDF-E4F6-9787 exists
Saving the new config file and configuring the hardserver
Done
-
-
On the HSM:
-
Configure the HSM to use the RFS by entering the IP address of the RFS machine and leaving the port number as the default (9004) (HSM menu 1-1-3).
-
(Optional) Allow HSM configuration files on the RFS to be modified and then loaded to the module by turning on the auto push (HSM menu 1-1-6-2).
-
Configure the HSM log file storage and append the option to allow storing the log files on the RFS and HSM (HSM menu 1-1-7).
-
Set the time and date as UTC (HSM menu 1-1-8).
-
Add the RFS and the ActivID Appliance(s) as HSM clients by entering the remote client IP address and setting the client permission to unprivileged (HSM menu 1-1-4-1).
-
Create a new security world FIPS 140-2 level 3 and Cipher suite AES (HSM menu 3-2-1).
At this point, the Administrator Card Set (ACS) is created:
-
Each card set consists of a number of smart cards, N, of which a smaller number, K, is required to authorize an action. The required number K is known as the quorum.
-
For the ACS, the value for K should be less than N and not equal to 1.
-
-
-
On the RFS:
-
Verify that the security world data is present locally using the following command:
Copyls –l /opt/nfast/kmdata/localFor example, the output with a security world present is:
Copy-rw-r--r-- 1 nfast nfast 128 Jul 23 09:38 card_849a96545928fa28759273fad3272961c42a4657_1
-rw-r--r-- 1 nfast nfast 808 Jul 23 09:38 cards_849a96545928fa28759273fad3272961c42a4657
-rw-r--r-- 1 nfast nfast 856 Jul 22 14:22 module_FFDF-E4F6-9787
drwxrwsr-x 2 nfast nfast 4096 Jul 22 16:38 sync-store
-rw-r--r-- 1 nfast nfast 17964 Jul 22 14:22 world -
As the nfast user account, use the following commands to:
-
Configure the TCP socket for Entrust KeySafe™ utility usage:
Copyconfig-serverstartup --enable-tcp --enable-privileged-tcp
-
Configure RFS to use the HSM as unprivileged client:
Copynethsmenroll -V <HSM-IP> <HSM-ESN> <HSM-KNETI-hash>
-
-
As the root user account, restart the HSM local agent (hardserver) using the following command:
Copy/opt/nfast/sbin/init.d-ncipher restart
-
Generate the ActivID Appliance Keys in the HSM
BEFORE you can migrate to an external HSM and add ActivID security domains, you must generate the HSM encryption keys that protect the sensitive information in the ActivID databases and assure database integrity.
These keys are used for all security domains defined in the ActivID Appliance.
ActivID Appliance supports the following levels of key protection:
-
Module-protected keys
-
OCS-protected keys (using Operator Card Sets)
The keys are managed in consistent set of five AES-256 symmetric keys with specific roles and naming convention for the key aliases:
<PREFIX>.<Key Role Type>.<version>
Where:
-
<PREFIX> – to make sure that the names remain unique, a specific prefix 'HID-IA-4T’ is used for all the ActivID Appliance key aliases
This prefix is not configurable.
-
<Key Role Type> – is mandatory and is part of the key set
-
<Version> – number version of the key (increment with renewal)
Based on this convention, the default key set (shared by all domains) that you need to generate using the HSM tools is:
| Key Role | Key Type | Alias – shared | Key Usage | Key Role |
|---|---|---|---|---|
|
AUDIT |
AES 256 |
HID-IA-4T.AUDIT.1 |
Signature | Audit signature |
|
CREDS |
AES 256 |
HID-IA-4T.CREDS.1 |
Encryption | User credentials encryption (replaces the des and DeviceSecretsKey keys of previous versions of the ActivID Appliance) |
|
DSIGN |
AES 256 |
HID-IA-4T.DSIGN.1 |
Signature | Database row integrity signature |
|
SESSION |
AES 256 |
HID-IA-4T.SESSION.1 |
Encryption | ALSI sessions encryption/decryption |
|
SYS |
AES 256 |
HID-IA-4T.SYS.1 |
Encryption | System credentials encryption/decryption (adapter parameters, replaces the ParameterValueKey key of previous versions of the ActivID Appliance) |
Therefore, when the HSM keys are created or renewed using a manual process (using HSM dependent tools), it is recommended that you always use the uppercase key aliases.
Generate the ActivID Database keys using the Entrust KeySafe utility or command line utility (for further information, refer to the technical documentation provided with your HSM):
The following are examples to create module-protected keys.
Using the KeySafe utility:
-
As the nfast user account, launch the KeySafe utility (<NFAST_HOME>/bin/ksafe).
-
Click Keys in the left panel, and then click Create.
-
Select PKCS#11 in the applications list and then click Next.
-
Enter the following properties:
-
Protected by – module
-
Key recovery: yes
-
Key type – AES
-
Key size – 256
-
Key name: <keyname>
-
Blob in NVRAM – No
-
-
Click Commit.
Using the command line utility:
As the nfast user account, create the keys using the following command:
<NFAST_HOME>/bin/generatekey pkcs11 type=AES size=256 protect=module nvram=no plainname=<keyname>Create the Operator Card Sets
The Operator Card Set is required to recover ActivID Appliance domain administrator users (ftadmin and ftinit).
Optionally, create and Operator Card set (or re-use an existing set) to protect the ActivID Appliance keys.
For instructions, refer to the technical documentation provided with your HSM.
Generate the ActivID Appliance IDP Keys/Certificates in the HSM
For each ActivID security domain, the following RSA-2048 key/certificate pairs should be generated in the HSM for SAML support:
| Key Type | Key Size | PKCS#11 Certificate Label (aliases) | Certificate Key Usage | Certificate Purpose |
|---|---|---|---|---|
| RSA | 2048 | IDP_CERT_SIGNATURE_<domain> | Digital Signature | ActivID Appliance IDP signature |
| RSA | 2048 | IDP_CERT_ENCRYPTION_<domain> |
Key Encipherment and Data Encipherment |
ActivID Appliance IDP encryption |
Each key should be generated with the following properties:
-
Protected by – module
-
Blob in NVRAM – No
If they are incorrect, the appliance will not be able to use the HSM and it will not function properly.
However, during the ActivID IDP Keys/Certificates generation process, a temporary key in lowercase is created (key_hwcrhk_rsa-idpcertencryptionmydomain). This key will not be used as such and is deleted at the end of the process.
Generate a Self-Signed IDP Certificate
The procedure below is illustrated using module-protected keys and with an IDP encryption certificate for a domain called MyDomain
If you are using OCS-protected keys, in the commands detailed in the following sections, you must replace
-nby-c <OCS name>(where <OCS name> is the label defined for the OCS card set)Commands should be launched as the nfast user account
-
To configure OpenSSL for IDP certificates key usage, edit the <NFAST_HOME>/lib/ssleay/openssl.cnf file by adding the following sections:
Copy[ idp_encryption ]
keyUsage = dataEncipherment, keyEncipherment
[ idp_signature ]
keyUsage = digitalSignatureNote: From this point on, the OpenSSL utility is used with either the -extensions idp_encryption or -extensions idp_signature option depending on the IDP certificate type (encryption or signature).
-
Generate an RSA key pair for the Crypto Hardware Interface Library (CHIL) application.
The hwcrhk parameter value is the application name for the CHIL applications.
Copy<NFAST_HOME>/bin/generatekey hwcrhk type=RSA size=2048 protect=module nvram=no ident=idpcertencryptionMyDomain
OPTIONAL: pubexp: Public exponent for RSA key (hex)? []
>
key generation parameters:
operation Operation to perform generate
application Application hwcrhk
protect Protected by module
verify Verify security of key yes
type Key type RSA
size Key size 2048
pubexp Public exponent for RSA key (hex)
ident Key identifier idpcertencryptionmydomain
nvram Blob in NVRAM (needs ACS) no
Key successfully generated.
Path to key: /opt/nfast/kmdata/local/key_hwcrhk_rsa-idpcertencryptionmydomainThis temporary key is generated with lowercase domain name, and not the original case.
-
Generate the self-signed certificate using OpenSSL:
Copyexport LD_LIBRARY_PATH=<NFAST_HOME>/toolkits/hwcrhk
<NFAST_HOME>/bin/openssl req -new -days 1825 –sha256 -engine chil \
-config <NFAST_HOME>/lib/ssleay/openssl.cnf \
-extensions idp_encryption \
-key rsa-idpcertencryptionmydomain -keyform engine -x509 \
-out /tmp/IDP_CERT_ENCRYPTION_MyDomain.pem \
-subj "/OU=MyDomain/O=HID/CN=ACTIVID IDP Encryption"
engine "chil" set.Note:In the example, the IDP encryption certificate duration is set to 5 years (1825 days)
The “key” corresponds to temporary key created in previous step (lowercase)
However, for the output, you must specify your <domain> name with correct case.
-
Duplicate the RSA key pair for PKCS#11 application:
Copy<NFAST_HOME>/bin/generatekey --retarget pkcs11 from-application=hwcrhk plainname=IDP_CERT_ENCRYPTION_MyDomain
from-ident: Source key identifier? (rsa-idpcertencryptionmydomain)
[default rsa-idpcertencryptionmydomain] >
key generation parameters:
operation Operation to perform retarget
application Application pkcs11
verify Verify security of key yes
from-application Source application hwcrhk
from-ident Source key identifier rsa-idpcertencryptionmydomain
plainname Key name IDP_CERT_ENCRYPTION_MyDomain
Key successfully retargetted.
Path to key: /opt/nfast/kmdata/local/key_pkcs11_ua59677affe039c8ab700772b93c99a812da690357This generates a PKCS#11 key pair identifier that is the value following the key_pkcs11_” value in the “Path to key displayed by the above command. In this example,
ua59677affe039c8ab700772b93c99a812da690357
-
Retrieve the key pair identifier (for sanity checks):
Copy<NFAST_HOME>/bin/cklist -n --cka-label=IDP_CERT_ENCRYPTION_MyDomain | grep CKA_NFKM_ID
CKA_NFKM_ID "ua59677affe039c8ab700772b93c99a812da690357"
CKA_NFKM_ID "ua59677affe039c8ab700772b93c99a812da690357"The key pair identifier corresponding to the value of the “CKA_NFKM_ID” should match the value obtained in the previous step.
-
Import and bind the certificate to the key pair:
Copy<NFAST_HOME>/bin/ckcerttool -n -f /tmp/IDP_CERT_ENCRYPTION_MyDomain.pem -k ua59677affe039c8ab700772b93c99a812da690357 –L IDP_CERT_ENCRYPTION_MyDomain
Certificate found, processing...
Certificate successfully imported.
Run cklist to view your certificate object.
OK
-
Using the Entrust KeySafe utility, remove the RSA key pair (identified by idpcertencryptionmydomain) created above as it is no longer needed.
-
Repeat the steps above to create the IDP signature certificate (IDP_CERT_SIGNATURE_MyDomain).
Generate a CA Trusted IDP Certificate
-
The procedure below is illustrated using module-protected keys
If you are using OCS-protected keys, in the commands detailed in the following sections, you must replace
-nby-c <OCS name>(where <OCS name> is the label defined for the OCS card set) -
Commands should be launched as the nfast user account
-
From the RFS, generate key pair and certificate request:
 Using the KeySafe utility
Using the KeySafe utility
-
Launch the KeySafe utility (<NFAST_HOME>/bin/ksafe).
-
Click Keys in the left panel, and then click Create.
-
Select PKCS#11 with certificate request (RSA only) in the applications list and click Next.
-
Enter the following properties:
-
Protected by – module
-
Key recovery: yes
-
Key size – 2048
-
Public exponent for RSA key (hex):
-
Filename to write key to: <path>/<IDP_CERT_XXX_YYY>
-
Key name: <IDP_CERT_XXX_YYY>
-
Country code: <your value>
-
State or province: <your value>
-
City or locality: <your value>
-
Organisation: <your value>
-
Organisation unit: <your value>
-
Domain name: <your value>
-
Email address: <your value>
-
Blob in NVRAM – No
-
-
Click Commit.
-
In the Load FIPS Authorization page, click OK and, if required, insert your operator or administrator card into the HSM.
-
Click OK and then click Commit.
-
Click OK.
The following certificate request file is created in the <path> folder:
<IDP_CERT_XXX_YYY>_req
-
In the Keys page, select the <IDP_CERT_XXX_YYY> key in the Key List and identify the Key Instance/Copy id information (for example, <IDP_CERT_XXX_YYY_KEYID> as in the subsequent steps).
 Using command line utilities
Using command line utilities
-
Generate the key pair and the certificate request.
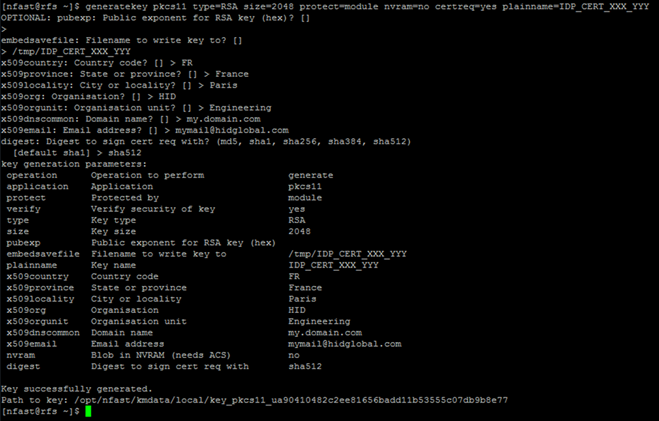
Copy<NFAST_HOME>/bin/generatekey pkcs11 type=RSA size=2048 protect=module nvram=no certreq=yes plainname=<IDP_CERT_XXX_YYY> -
Provide the parameters as illustrated below.
The following certificate request file is created in the <path> folder of the Filename to write key to parameter (“/tmp” in the example above):
<IDP_CERT_XXX_YYY>_req
-
In the “Path to key” displayed in the console, identify the value displayed after the key_pkcs11_ pattern (in the following steps, this is <IDP_CERT_XXX_YYY_KEYID>).
-
-
Obtain the certificate from the CA and upload it in PEM format:
-
Submit the certificate request (<IDP_CERT_XXX_YYY>_req) to the CA.
Important: Make sure that you request the IDP certificate with the correct key usage. -
Upload the PEM format of the certificate into the <path> folder on the RFS.
For example, if a “.CER” format has to be obtained from a Microsoft Windows CA, then:
-
Copy the <filename>.cer file into the <path> folder on the RFS.
-
Use the following OpenSSL command to convert it to a PEM format:
Copyopenssl x509 -inform der -in <path>/<filename>.cer -outform pem -out <path>/<IDP_CERT_XXX_YYY>.pem
-
-
-
From the RFS, import and bind the certificate to the key pair:
-
Import and bind the certificate to the key pair:
Copy<NFAST_HOME>/bin/ckcerttool -n -f /<path>/<IDP_CERT_XXX_YYY>.pem -k <IDP_CERT_XXX_YYY_KEYID> -L <IDP_CERT_XXX_YYY>
Certificate found, processing...
Certificate successfully imported.
Run cklist to view your certificate object.
OK -
Check the HSM content:
Copy<NFAST_HOME>/bin/cklist -n --cka-label=IDP_CERT_XXX_YYY | grep CKA_CLASS
CKA_CLASS CKO_PUBLIC_KEY
CKA_CLASS CKO_PRIVATE_KEY
CKA_CLASS CKO_CERTIFICATE
-
Renewing an IDP Certificate
To renew an IDP certificate, the data related to this certificate (key pair and certificate) should be removed from the HSM before creating the new data.
Next step: