Deployment Modes
High Availability helps to facilitate network-wide resilience to increase network availability. It provides continuous access to applications, data, and content anywhere, anytime by addressing potential causes of downtime with functionality, design, and best practices.
The following list describes the main benefits of running in a Dual Mode deployment (resulting in High Availability):
- Software Updates – one appliance stays active while the other appliance is being updated (for both hot fixes and new versions). This minimizes the impact on the High Availability system.
- Multiple Nodes – in this release, two nodes (appliances) work in a synchronized manner. Additional appliances can also be deployed to run the front ends (for example, RADIUS or portals).
- Multiple sites/geography – supports the option of being deployed in different geographic locations for better tolerance against disasters. The DNS can be configured to use one external system instance (for example, LDAP) in one location and a different instance in another location. DNS configuration is done outside of the appliance.
- Latency requirements – RTT (round-trip time) latency exceeding 200 milliseconds is not supported in a Dual Mode deployment. The service and synchronization status for a remote appliance is displayed as unreachable if the latency is high. It is recommended that you maintain RTT below 100 milliseconds.
- Bandwidth requirements – approximately 50 kb is required per authentication. Configure a bandwidth compatible with the number of authentications per second in your deployment. For example, you need a 1 Mbit/second bandwidth for 20 authentications per second.
- Security – the communication between each appliance is secure to prevent a third party from attacking the system (that is, intercepting the communication or attempting a man-in-the-middle attack between the appliances).
- Monitoring – this feature makes it possible to notify administrators who are using supported mechanisms (for example, audit or SNMP) of any event related to HA.
High Availability requires two appliances configured in Dual mode. Both appliances are synchronized on real-time.
This configuration allows high availability, load balancing and automatic failover. For the content of its database and its configuration, the two nodes are symmetric regarding all available services, components and supervision.
- Symmetric Services – all services are available from both nodes.
- Authentication and authorization, including API, RADIUS Front End and Authentication Portal
- Self-Service Portal
- Administration
- Audit review
- Symmetric Components – all physical and software components are installed and configured on both nodes identically.
- Both nodes have their own authentication server and their own active database
- All data updates are replicated from A to B and from B to A in real-time
- Audit logs from both nodes are available on both nodes
- Security domains are identical
- Front Ends are configured identically
- Compatibility digests are identical
- Symmetric supervisor – statuses are visible from both nodes. The High Availability View shows the options and status of the services and the status of the synchronization on both nodes that are available depending on the context.
Among the services offered on both appliances, there is no exclusive operation.
However, if two background operations are triggered simultaneously (such as backup, archive audit and purge, or large SDS import), the system serializes the operation execution. Therefore, operation execution can be delayed until the previous one is completed.
The following sections describe the deployment models (standalone appliance or use of two appliances running in either Single or Dual Mode). It also describes the different roles appliances own when they are running in Dual Mode to achieve High Availability.
The following sections describe the possible deployment configurations that involve the ActivID Appliance components and portals.
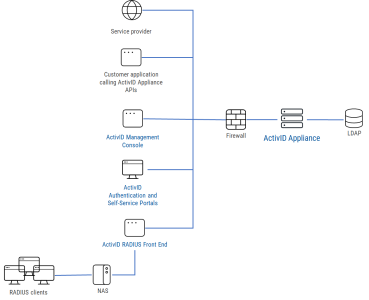
Standalone Deployment
This deployment does not require high availability, so it requires only a single ActivID Appliance with the ActivID Authentication Services installed. Front ends and other clients can be installed separately from the appliance.
The main purpose of a standalone deployment is to demonstrate how to configure the appliance and to demonstrate different authentication methods. It should be used for proof-of-concept (POC) or non-business critical deployments where failover does not need to be immediate.
Reminder: Standalone configuration is not recommended for production. It does not provide high availability. The recommended production deployment requires running in dual mode using two appliances.
- If the ActivID Authentication Services are installed, then the appliance offers authentication and administration services.
- If the ActivID Authentication Services are not installed, then the appliance behaves as a front end. In this case, it must be connected to another appliance on which the ActivID Authentication Services are installed.
Running in single mode, you can choose to configure how to install the ActivID Appliance. Components that can be deployed outside of the appliance must be installed on ActivID Appliances dedicated to the Front End and portals. They are:
- ActivID RADIUS Front End (installing the RFE as an ActivID Appliance Front End offers better security so that the server cannot be exposed),
- ActivID Management Console, and
- ActivID Self-Service Portal.
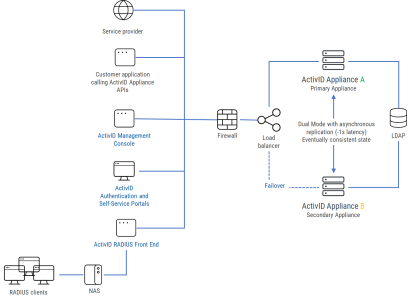
Deployment with Two Appliances
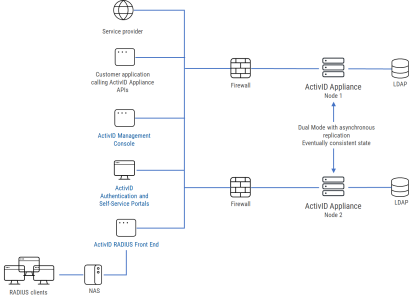
The above configuration and the distant dual node deployment (illustrated below) are for medium to large-sized deployments. High availability is required – with two nodes installed behind the load balancer and externally monitored (via alarms raised).
The front ends and other clients can be installed on one or more appliances.
This deployment requires two appliances, with at a minimum, the ActivID Authentication Services installed on both.
The two nodes share the same ActivID Appliance applications, database data, and cryptographic data (HSM or Soft cryptography).
High Availability highlights:
- Each node has its own ActivID Authentication Services and an active database
The databases are synchronized using Oracle Golden Gate (GG) replication.
- Running in dual mode, appliances have the same security domains
- Both appliances must have compatible versions of ActivID software (same major version)
- Service pack versions must be identical
- Appliances are time-synchronized
Deployment for Running with Two-Appliances (Distant Dual Nodes)
Appliance Backup
An ActivID Appliance backup is an archive containing the following:
- Metadata (describes the payload content and some context information)
- Database data (includes data related to all security domains defined)
- SSH configuration
- Cryptography module content
- ActivID Console data (configuration, certificate, keystore and truststore)
- ActivID Appliance data (configuration, certificate, keystore, and truststore)
This backup is used for the following purposes:
- Recovery of the appliances (in case of disaster where all appliances are lost)
- Auditing and history (to retrieve/check full information about any event from audit data)
Audit archiving is a separate process/function on the appliance.
This backup can be created through a scheduled backup or manually using the ActivID Console. A standard backup is encrypted and stored in an external SFTP/FTP server.
See also:
Managing a High Availability Deployment
About High Availability Synchronization and Data Replication