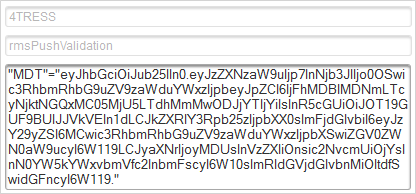
HID RMS Auditing
The information related to the HID RMS authentication process is audited during the end-user authentication.
The following table describes the auditing data retrieved:
| Code | Name | Description |
|---|---|---|
|
MDT |
malware_detection_type |
Detailed Information on the risk detection |
Example
eyJhbGciOiJub25lIn0.eyJzZXNzaW9uIjp7InNjb3JlIjo0OSwic3RhbmRhbG9uZV9zaWduYWxzIjpbeyJpZCI6IjdlMDQ4NDZlLTFmNTAtNDAxNS05YTViLTNjYzYxYjFhMjA1MCIsInR5cGUiOiJOT19GUF9BUlJJVkVEIn1dLCJkZXRlY3Rpb25zIjpbXX0sImFjdGlvbiI6eyJzY29yZSI6MCwic3RhbmRhbG9uZV9zaWduYWxzIjpbXSwiZGV0ZWN0aW9ucyI6W119LCJyaXNrIjoyMDYsInVzZXIiOnsic2NvcmUiOjcsInN0YW5kYWxvbmVfc2lnbmFscyI6W10sImRldGVjdGlvbnMiOltdfSwidGFncyI6W119This data is visible in the Reporting > Audit Report details, in the indirectPrimaryAuthenticationUP parameter:
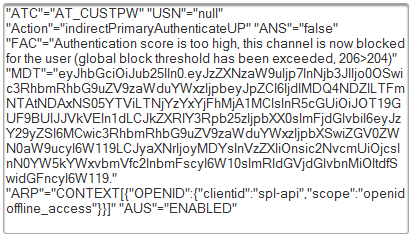
To read the MDT information, paste the JWT into a JWT decoder and view the result
{
"session": {
"score": 49,
"standalone_signals": [
{
"id": "7e04846e-1f50-4015-9a5b-3cc61b1a2050",
"type": "NO_FP_ARRIVED"
}
],
"detections": []
},
"action": {
"score": 0,
"standalone_signals": [],
"detections": []
},
"risk": 206,
"user": {
"score": 7,
"standalone_signals": [],
"detections": []
},
"tags": []
}This data is also visible in the Reporting > Audit Report details, in the rmsPushValidation parameters, (for example, when Mobile Push logon is used as a step-up authentication):