Managing the Network Configuration
ActivID AS Ports and Protocols
The following table outlines the network communications that are required to and from ActivID AS for the following configurations.
| Protocol | Direction | Type | Port | Encryption | Authentication |
|---|---|---|---|---|---|
| HTTPS | Inbound | TCP | Configurable | SSL/TLS | Mutual PKI |
| HTTPS | Inbound | TCP | Configurable | SSL/TLS | Server-based PKI and one additional form factor |
ActivID AS requires an HTTPS port and, if a client application (for example, a RADIUS front end) or end users need to authenticate with PKI, you must also configure an HTTPS port with mutual authentication.
Reverse Proxy/Web Application Firewall Configuration
The following REST endpoints are used by the HID Approve™ mobile application and SDK to communicate to the authentication server:
GET https://<host>[:<port>]/idp/<DOMAIN>/authn/.well-known/openid-configuration
POST https://<host>[:<port>]/idp/<DOMAIN>/authn/token
POST https://<host>[:<port>]/idp/<DOMAIN>/authn/revoke
POST https://<host>[:<port>]/scim/<DOMAIN>/v2/Device/Provision/.search
GET https://<host>[:<port>]/scim/<DOMAIN>/v2/Device/Provision/<id>
PUT https://<host>[:<port>]/scim/<DOMAIN>/v2/Device/Provision/<id>(where <id> represents a number)
These are endpoints that are likely to be accessed from the internet (as the clients are the end-user devices). Other endpoints are likely to be accessed only from specific sub-networks, with the possible exception of the ActivID Authentication Portal, depending on your deployment architecture.
Therefore, it is a good security practice, when applicable, to use a reverse proxy or web application firewall to filter and limit access from the internet to the aforementioned endpoints only. Other endpoints should only be reachable from specific sub-networks.
Set the System Date and Time
ActivID AS requires the synchronization of all application server clocks. You can achieve this manually or with any external time protocol. The recommended external time protocol is Network Time Protocol (NTP).
Set the time zone on the application server for ActivID AS to Coordinated Universal Time (UTC). This ensures no regional changes, such as daylight savings time, can occur to the server system clock.
Update the HTTPS Ports or Proxy Hostname/Ports
After installing the ActivID AS applications, you might need to update the ActivID Authentication Portal host/port configuration (for example, because of load balancer usage in front of several instances of the ActivID Authentication Portal).
To do so, edit the <ACTIVID_HOME>/ActivID_AS/applications/resources/common/activid.properties file to update the following properties:
Update the reverse proxy hostname and port
IDP_HOSTNAME=<new proxy hostname>
IDP_HTTPS_PORT=<new port>- Reverse proxy forwards the <public hostname:8443> requests to <AS-hostname:8443>.
- Reverse proxy 8443 port is configured for mutual authentications (request a certificate, trust the client certificates).
- End-user certificate is propagated to the ActivID IdP via a configurable HTTP header.
Configure Forward Proxy Support
In deployments with an outgoing/forward proxy (such outgoing HTTPS connections for push-based authentication), you need to configure the proxy in ActivID AS.
To configure a forward proxy:
- Edit the <ACTIVID_HOME>/ActivID_AS/applications/resources/common/activid.properties file to update the following properties:
- F_PROXY_HOSTNAME - proxy address Host name or address of your proxy
- F_PROXY_PORT - proxy port Listening port on your proxy
- F_PROXY_USERNAME - proxy username If proxy authentication is required, enter the username
- F_PROXY_USERPWD - proxy password If proxy authentication is required, enter the password
- To obfuscate the Proxy password, run the changePasswords.sh script as ftadmin using the following command:
Copysu - ftadmin
/usr/local/activid/ActivID_AS/bin/changePasswords.sh
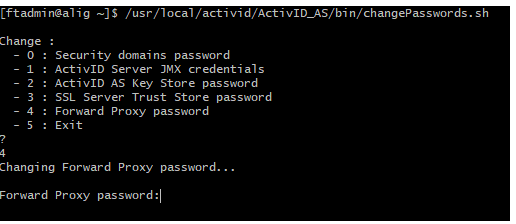
- At the prompt, enter 4 to obfuscate the Forward Proxy password.
- Restart the applications.





