Activate the HID Approve Application
Users can activate HID Approve (registering the banking service) using the following methods:
-
Scanning a QR code with the application
-
Entering an Invite Code manually (for example, if the device does not have an activated camera)
-
Using an activation URL (for HID Approve Microsoft Windows 10 only)
The HID Approve application obtains its Push ID from the mobile OS Push Service.
User's HID Approve application is registered into the ActivID AS database as well as in the Azure hub portal.
All of the keys needed for future logon or actions (that is, banking operations) are provisioned on the mobile during service registration.
The workflow is illustrated using JMS notifications to web application. Alternatively, you can deploy a CIBA-based workflow as described in Configure Feedback for External Applications.
By default, the Mobile provisioning URL used during registration is computed with local information (server name and port in the HTTP request).
Using the manual Invite Code registration method implies that some of the registration information is predefined (for further information, see Add a Service by Entering an Invite Code.
If you are using a proxy in front the ActivID AS, or the registration portal is installed on a front-end server, you must define the required URL (proxy server or back-end server). For example, in the banking demo, configure the application.config.mobile.activation.provisioningurl property.
Install HID Approve
ActivID AS and the banking web portal are deployed and configured for push-based validation.
The HID Approve application is configured according to deployment needs.
To use biometric authentication:
- The device must be biometric-capable (that is has a fingerprint sensor and supports biometric authentication).
- The user must enroll a fingerprint/face on the device.
The Root CA of the ActivID AS server SSL certificate is imported into your browser’s Trusted Root Certification Authorities Store.
If you are installing on a mobile device and the Root CA is not a part of your device system Trusted Root CAs, make sure that you install your authentication server SSL Root CA certificate in your mobile device (and restart the HID Approve application if necessary) before registering the service.
-
The user downloads and installs the HID Approve
 application:
application:- For Android, download the app from Google Play®
- For iOS and macOS, download the app from the Apple Store
- For Windows, download the app from the Microsoft Store
Note: Alternatively, you can provide the user with a deep link that checks if the application is already installed on the device. If it is not, the user is directed to the application on the relevant store, prompting them to install it. -
The user taps Open to launch the app on the device.
-
Depending on the device’s operating system, the user then allows HID Approve to send notifications and/or access to the device’s camera.
-
The user must make sure that the device has internet access (via WiFi or a mobile network).
Add a Service by Scanning a QR Code
-
The user launches the HID Approve application and the Welcome page is displayed, explaining how to register a new service.
iOS/Android macOS
Windows 10 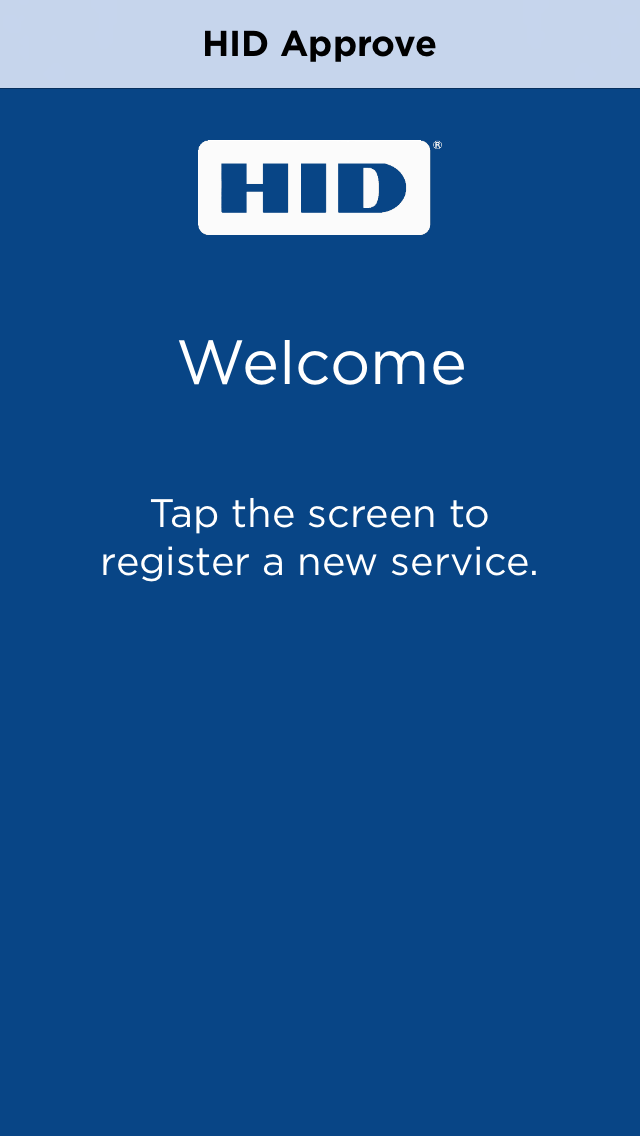
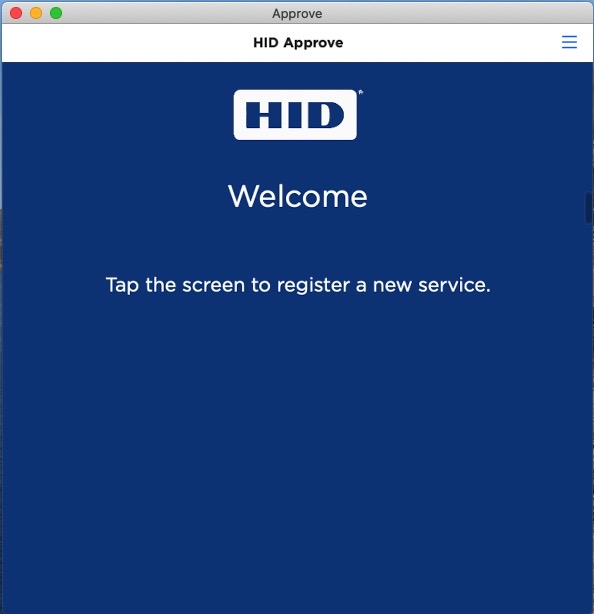
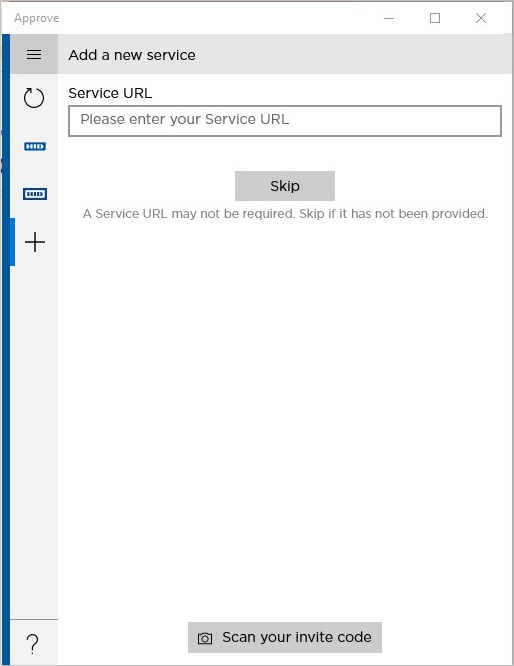
The user taps the screen.
The user clicks Scan your invite code.
-
The user accesses your bank’s web portal to register as a new banking customer (or connects to the ActivID Self-Service Portal) and clicks Register New User.
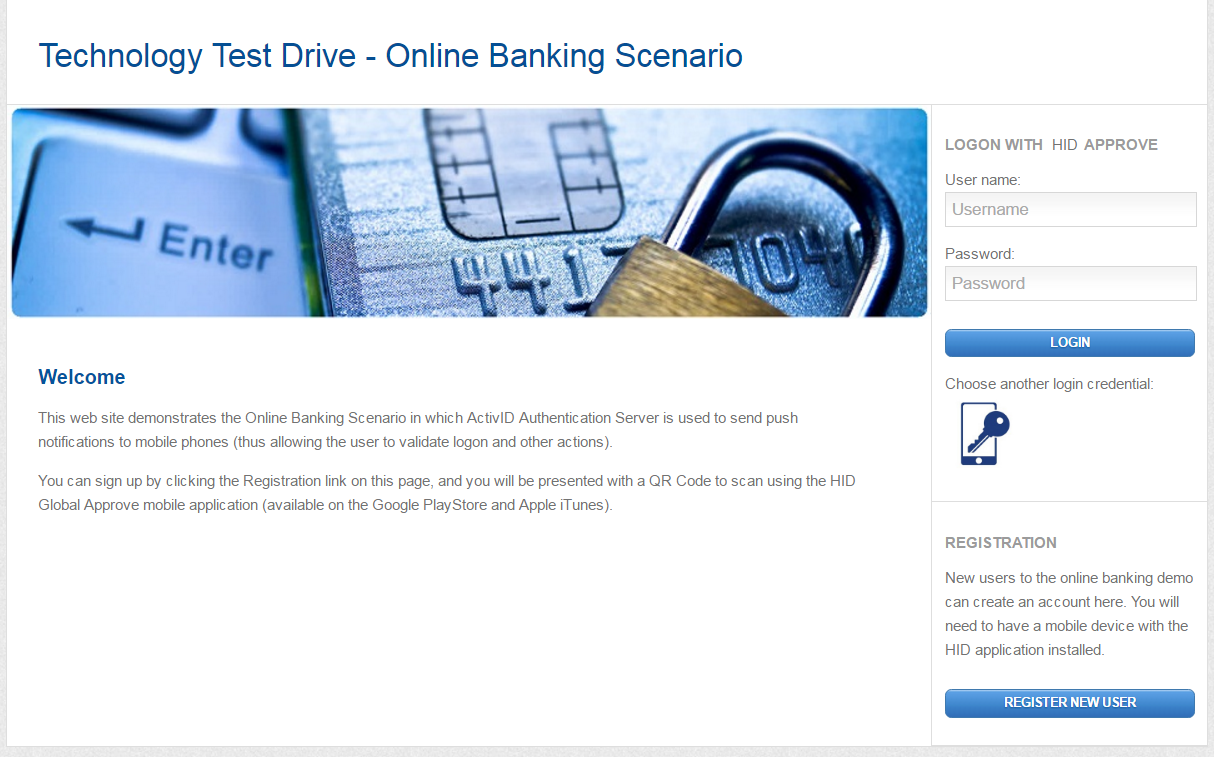
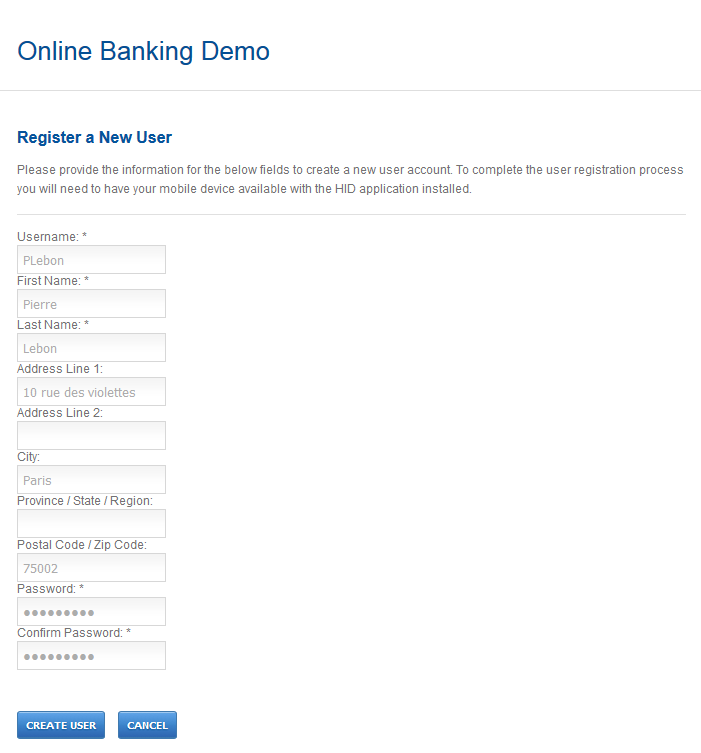
-
The user enters their details and clicks Create User.
- Creates the user in ActivID AS.
- Creates a Mobile push-based Validation device for the user.
- Submits a device request to ActivID AS for the user.
- A Mobile push-based validation device, with the PENDING status (a device issuance request exists for this device).
- A Mobile Registration Authentication record.
- A Mobile Registration Virtual Device assigned with a Mobile registration credential.
- A Customer Static Password (created in previous step).
The Mobile push-based validation authentication record is not created yet.
The keys are not generated yet.
User and device issuance request creation are audited within ActivID AS.
-
The user scans the QR code using the device’s camera.
iOS/Android Windows 10 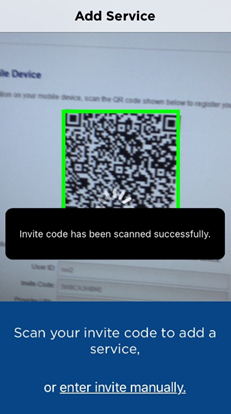
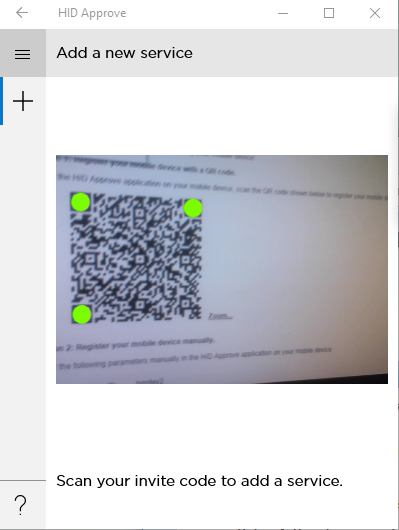
- Registration protocol version
- Service Provider server URL
- Customer ID for the user
- Device ID
- Device Type code (mobile push-based Validation)
- Channel code for Mobile Registration channel
- Authentication policy code for Mobile Registration Authentication
- Secret to initiate mobile registration (by default this is empty, the secret is computed using a hash of shared secret below)
- Shared secret for mobile registration protocol
HID Approve calls the HID Approve SDK to authenticate to ActivID AS, passing on the provisioning server URL and one-time password.
The one-time password is validated by ActivID AS.
A valid one-time password establishes a session between the HID Approve SDK instance and ActivID AS.
ActivID AS retrieves the device issuance request that was created during registration for the user.
The HID Approve SDK calls ActivID AS to retrieve pending operations, to define the session transport keys used to establish a secure channel.
These session keys are established via an Elliptic Curve Cryptography Diffie-Hellman (ECC-DH) key agreement protocol.
The HID Approve SDK calls ActivID AS to retrieve pending operations to generate the user private/public key pair for logon validation credential.
The Public key is sent to ActivID AS and a Logon validation credential is created and linked to the Mobile push-based Validation device on ActivID AS. Corresponding Mobile push-based Logon Validation authenticator record is created.
The HID Approve SDK calls ActivID AS to retrieve pending operations to generate the user private/public key pair for Action validation credential.
The Public key is sent to ActivID AS and the Action validation credential is created and linked to the Mobile push-based Validation device on ActivID AS. The corresponding Mobile push-based Action Validation authenticator record is created.
The HID Approve SDK calls ActivID AS to retrieve pending operations to generate the user Mobile OATH event-based Credential.
ActivID AS generates a key for the OATH credential and sends the value to the HID Approve SDK. The corresponding authenticator record is created (for example, Customer One Time Password authentication record).
The HID Approve SDK calls ActivID AS to retrieve the customization for the registered service (label, color, and bitmap).
The HID Approve SDK closes the session with ActivID AS when there are no more pending operations.
To complete the service registration, the user might be required to set a new key protection password (see Customize the Key Protection Methods).
QR code has a JSON format.
If the QR code scan is rejected, an error message will be displayed “This invite code is invalid. Please scan a correct QR code” and the user can start again.
If the Network is not accessible, the service registration will fail with the "The internet connection appears to be offline” error.
-
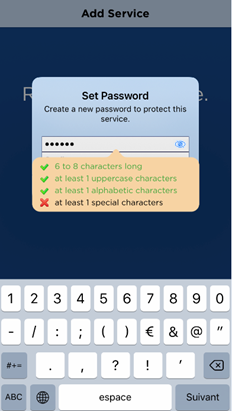
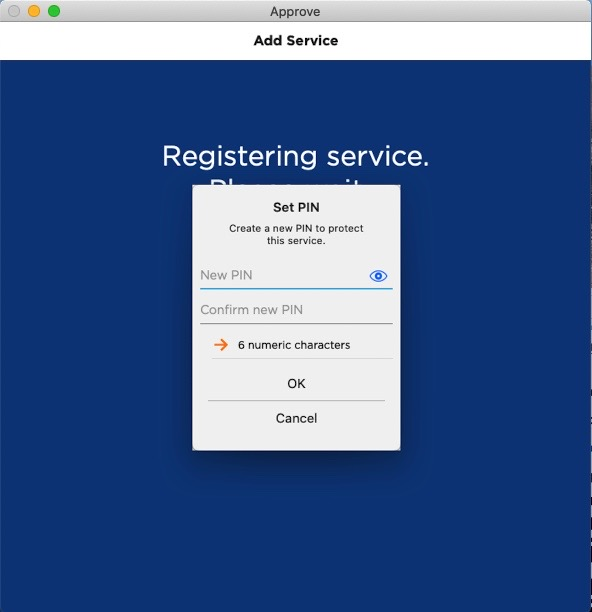
The user enters and confirms a Password and then taps OK.
A QR code is generated by the portal.
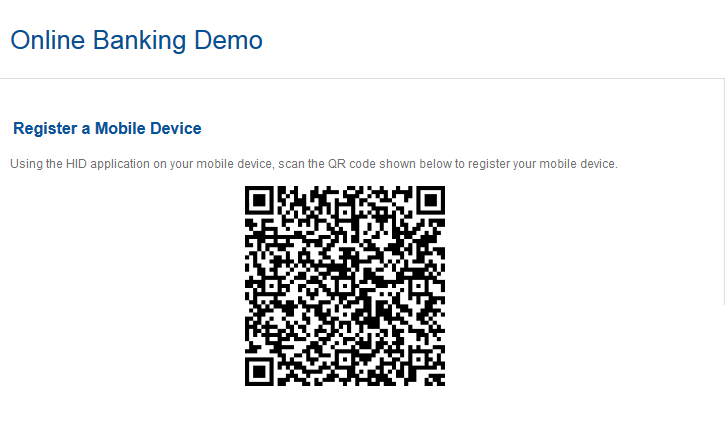
The portal:
In ActivID AS, the user is registered with the following information:
This initiates the registration process on the device.
The QR code contains:
{
"ver":"v7",
"url": "<hostname>:<port>/<DOMAIN>",
"uid": "CustomerID",
"did": "11532",
"dty": "DT_TDSV4",
"pch": "CH_TDSPROV",
"pth": "AT_TDSOOB",
"sec": "",
"pss": "NTBJQ0ROTDgwWQ=="
}Transparently to the user:
If the security policy requires that the service be protected by a password or biometric, the user is prompted to set a password.
The password protection conditions depend on the key protection policy configured for the Device type (or individual Credential Type). For further information, see Customize the Key Protection Methods.
|
iOS/Android |
macOS |
Windows 10 |
|
|
|
|
As the user types, the app displays the password rules (such as the number of upper or lower case characters).
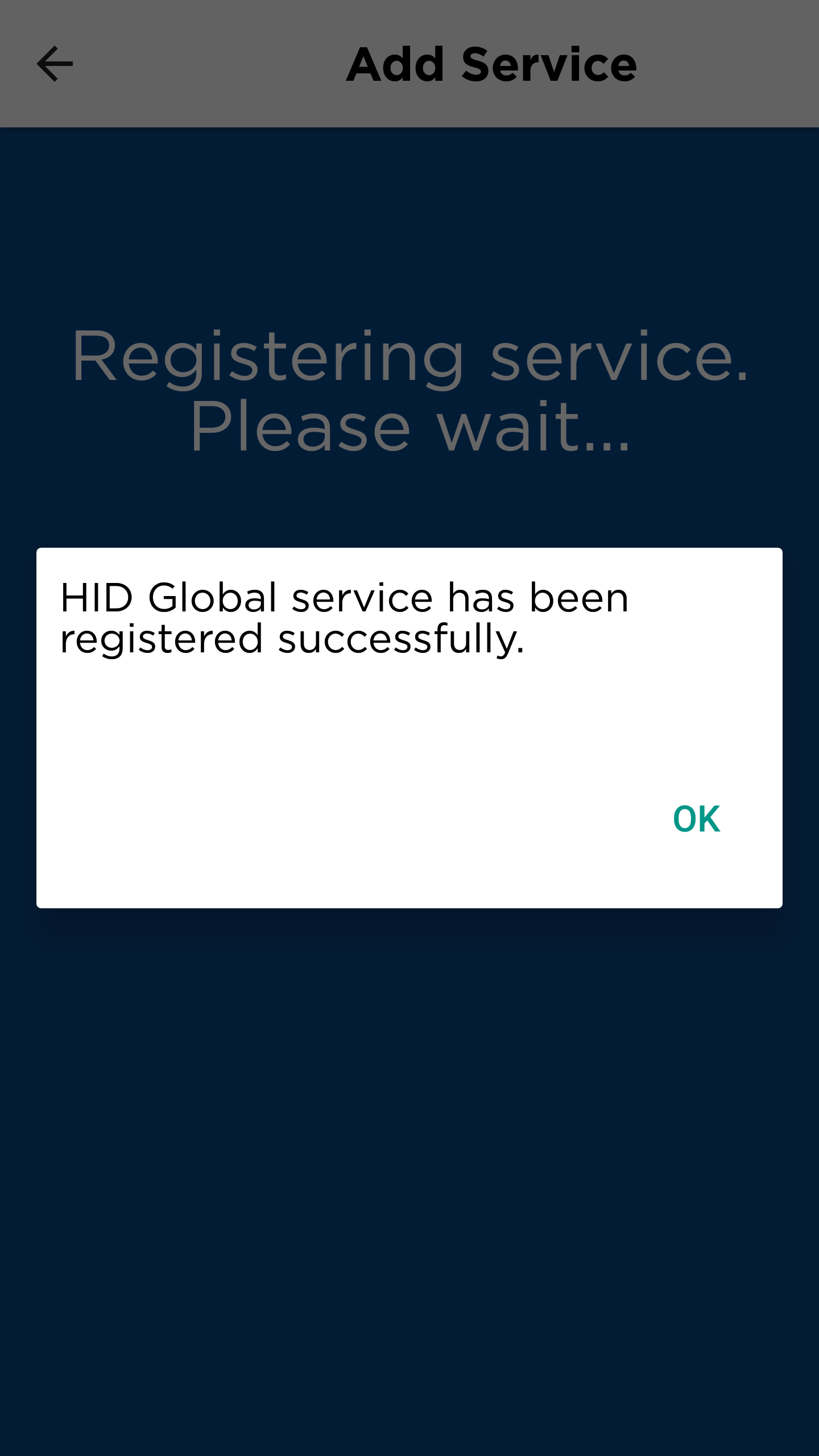
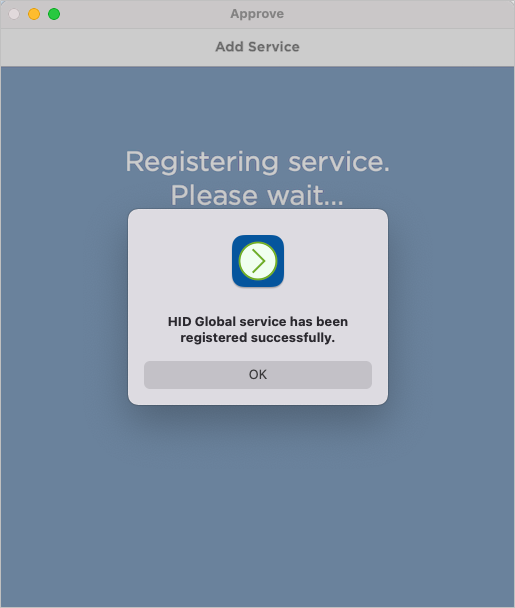
The success message is displayed.
|
iOS/Android |
macOS |
Windows 10 |
|
|
|
|
At the end of the registration process:
-
On the device (when using the default configuration), there is:
- One session transport key (made up of 2 AES keys - ENC/MAC) used for application updates and to secure validation operations.
- One RSA private key for Logon Validation.
- One RSA private key for Action Validation.
- One OATH key for Secure Code generation.
- One OATH OCRA key for Secure Code generation using Challenge/Response
- One OATH OCRA key for Secure Code generation using Signature
-
If the key password is protected, the password protecting the signing keys has been updated by the device’s user.
-
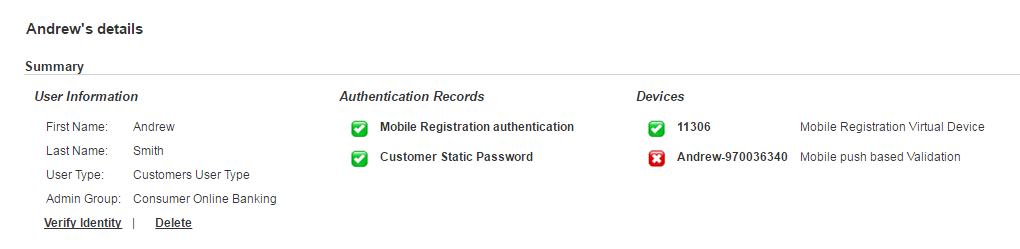
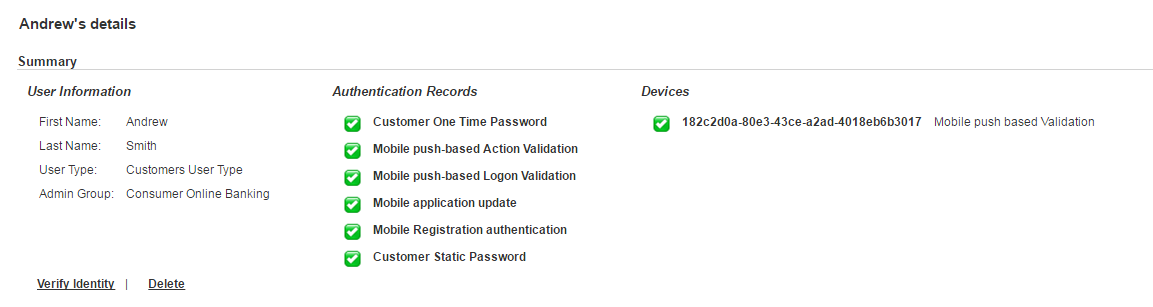
In ActivID AS, the user is now fully registered and has:
- A Mobile push-based Logon Validation authentication record (to validate Logon).
- A Mobile push-based Action Validation authentication record (to validate Actions).
- A Customer One-Time Password authentication record (to authenticate with Secure Code).
- A Mobile application update authentication record (used for mobile Service communications).
- A Mobile push-based Validation device, with the ACTIVE status, and four associated Credentials for Logon, Action, OTP (OATH), and Session Transport.
Add a Service by Entering an Invite Code
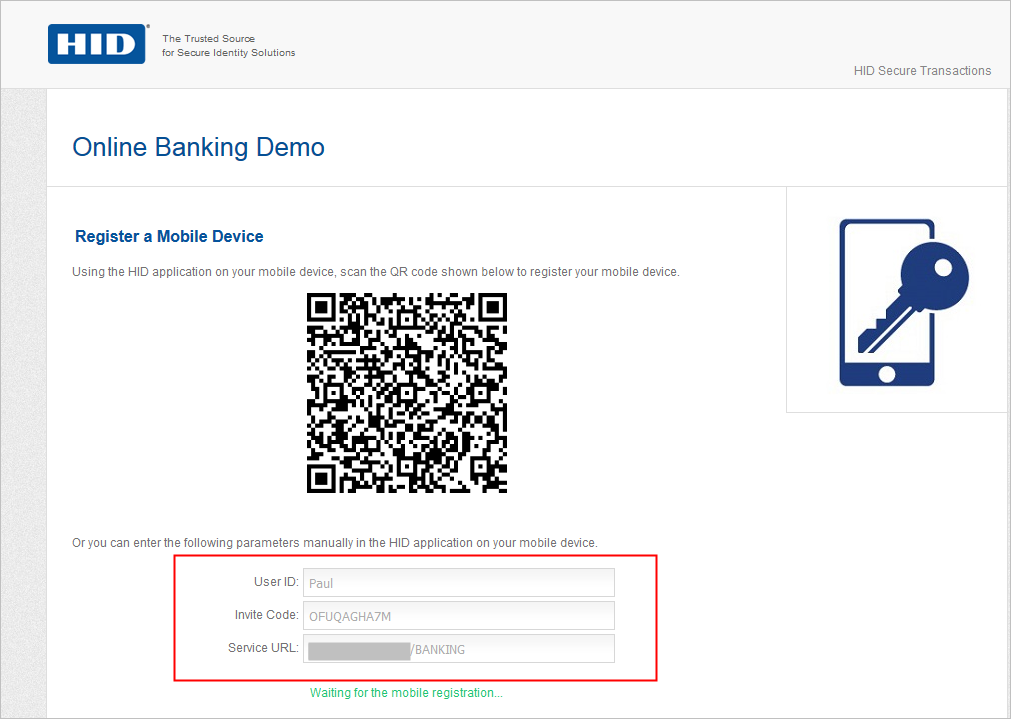
When a camera is not available on the device, the user can manually register a Service using the Invite Code.
The Invite Code is displayed below the QR code generated by the web portal.
The transparent exchanges between the application, HID Approve SDK and ActivID AS are the same as those during the QR code registration.
However, when using manual Invite Code method, only a subset of the registration information is sent to the mobile. This includes the following mandatory values:
-
User ID "uid"
-
Service URL "url"
-
Pre-shared-secret "pss"
For the optional parameters, the application uses its own default values as follows (they are not configurable):
-
Device Type "dty" =DT_TDSV4
-
Channel "pch" =CH_TDSPROV
-
Mobile registration Authentication Policy "pth"=AT_TDSOOB
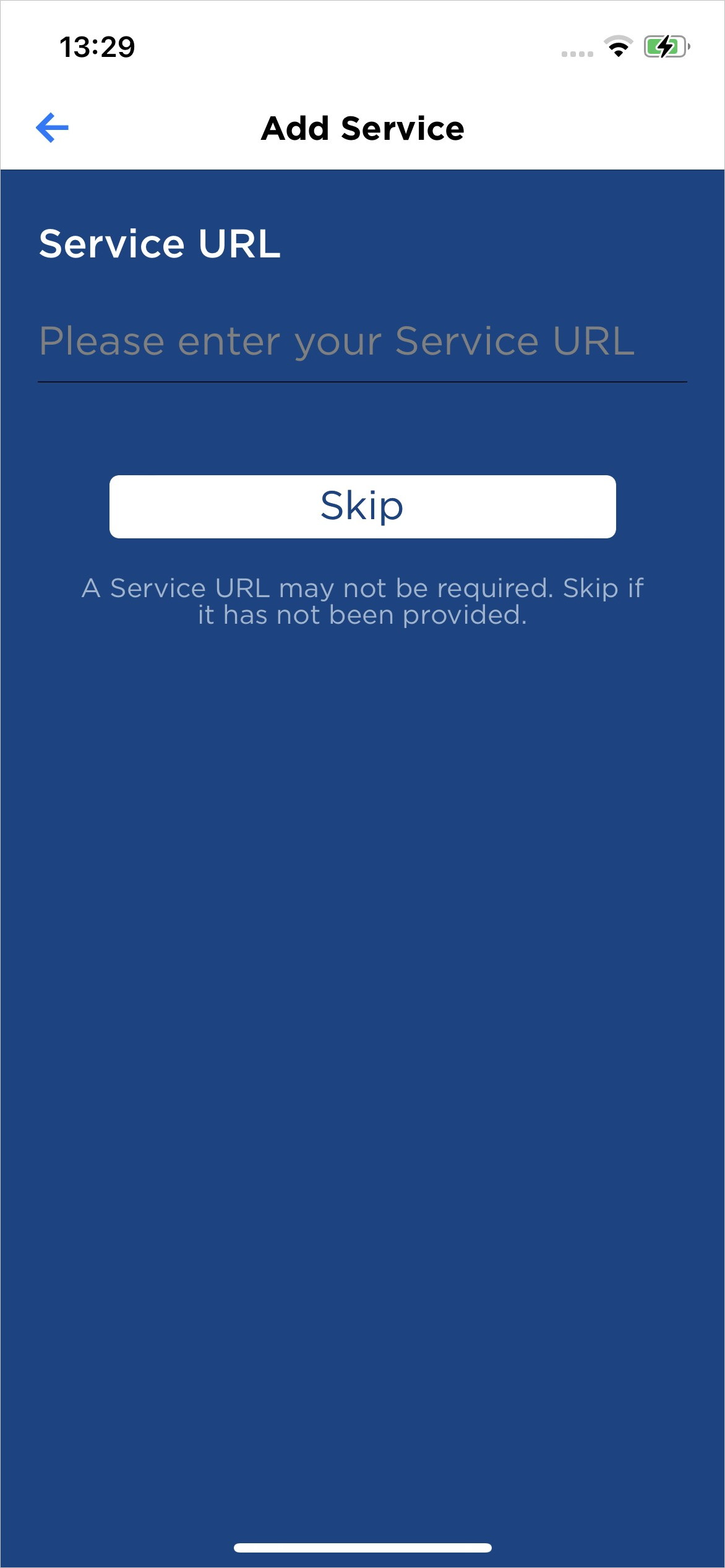
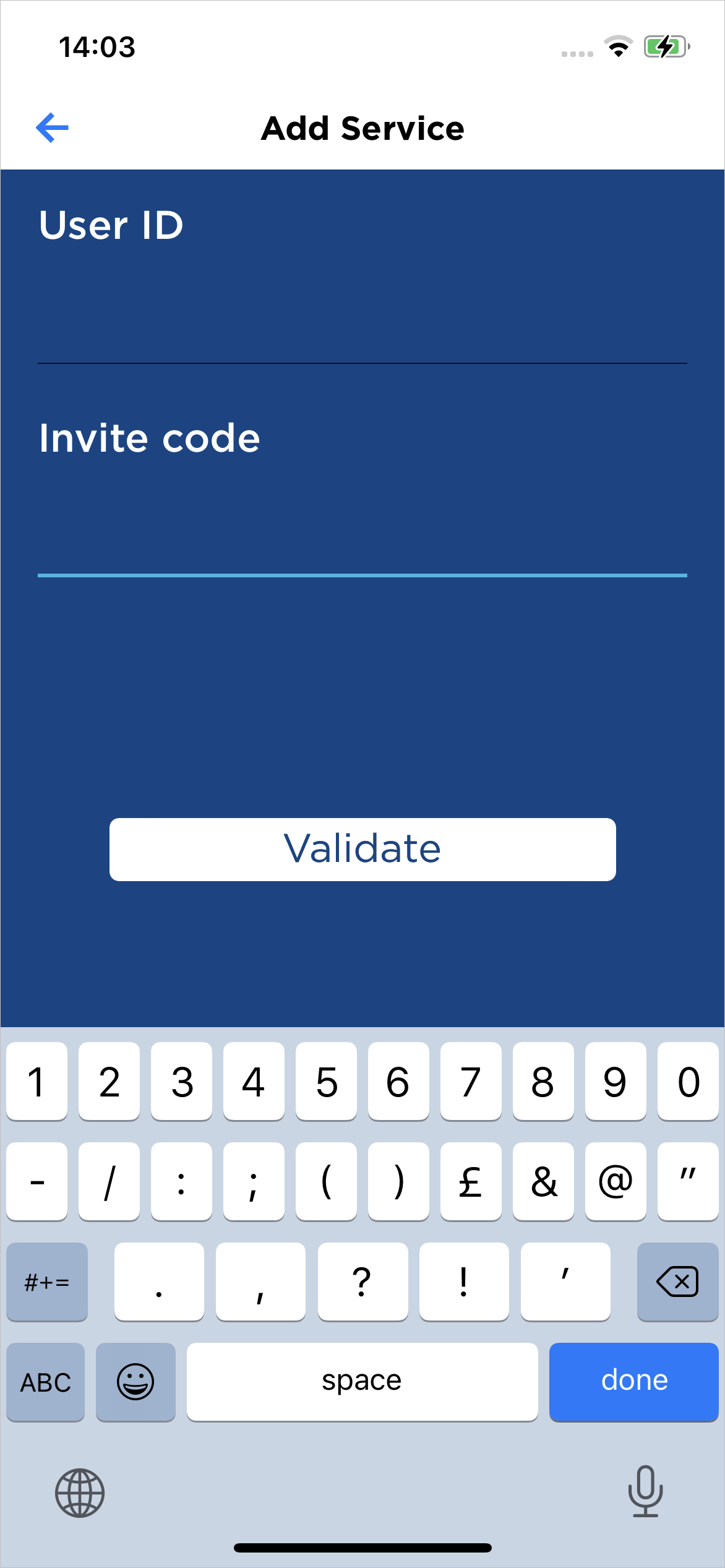
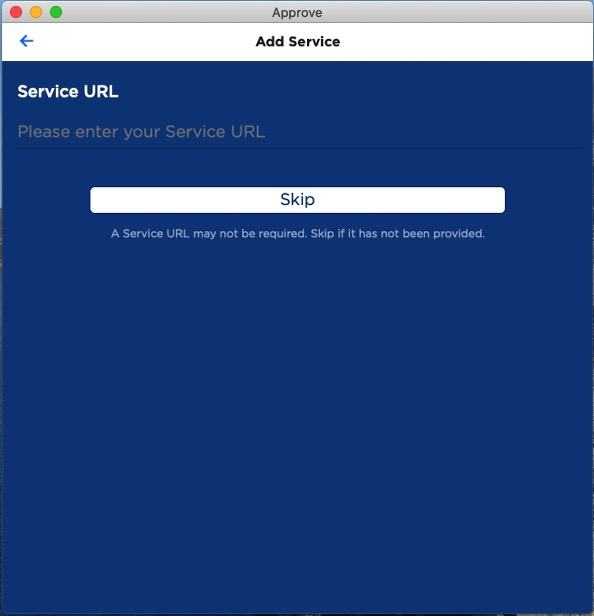
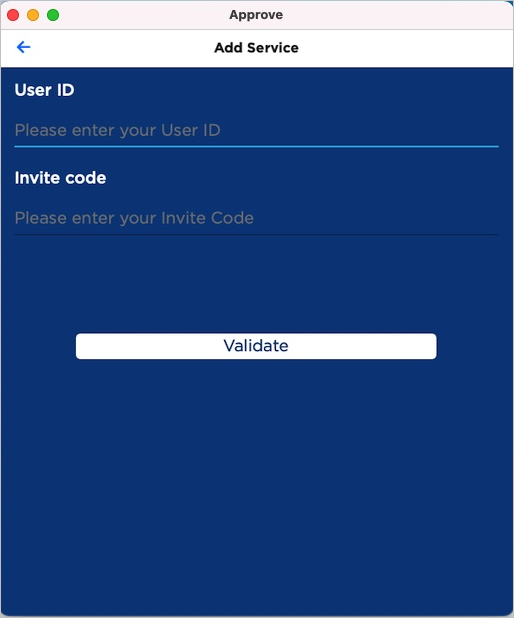
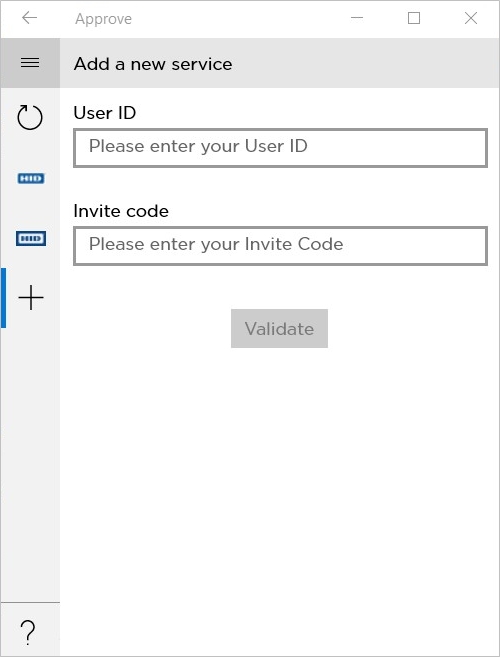
- The user taps enter invite manually.
iOS/Android macOS
Windows 10

-
In the Add Service fields, the user enters the corresponding information as displayed by the portal.
- Service URL
- User ID
- Invite code
-
The user taps Validate to initiate the Service registration.
-
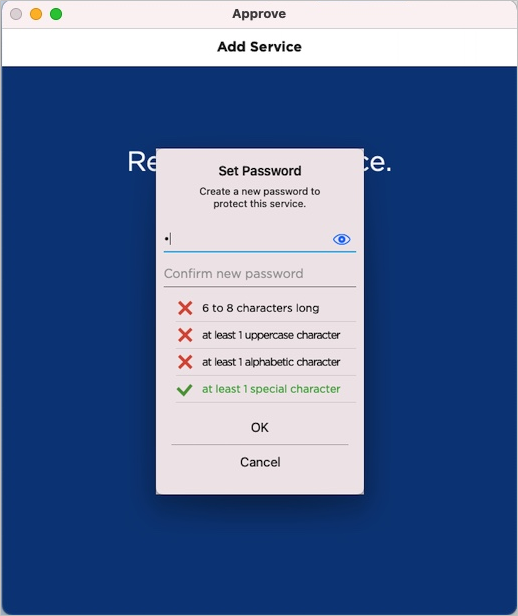
The user enters and confirms a Password and then taps OK.
If the security policy requires that the service be protected by a password or biometric, the user is prompted to set a password.
The password protection conditions depend on the key protection policy configured for the Device type (or individual Credential Type). For further information, see Customize the Key Protection Methods.
|
iOS/Android |
macOS |
Windows 10 |
|
|
|
|
As the user types, the app displays the password rules (such as the number of upper or lower case characters).
The success message is displayed.
|
iOS/Android |
macOS |
Windows 10 |
|
|

|
|
Add a Service using a Activation URL
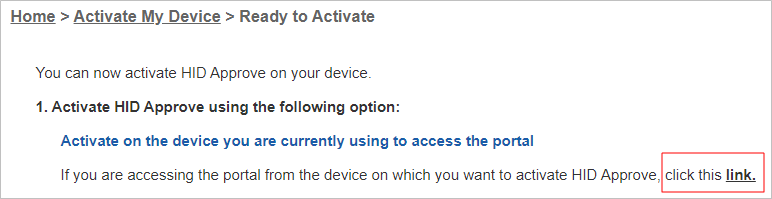
If the user needs to register a service on the Microsoft Windows 10 PC or tablet that they are using for activation, an easy activation process is available, requiring minimal user input:
-
The user clicks the activation link on the web page.
The link automatically triggers the service registration on the HID Approve Microsoft Windows 10 Universal App.
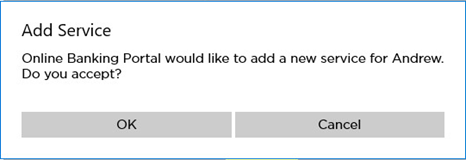
-
The user clicks OK to add the new service.
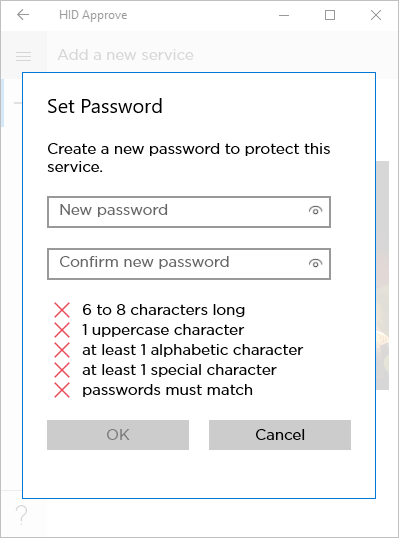
If the security policy requires that the service be protected by a password or biometric, the user is prompted to set a password.
The password protection conditions depend on the key protection policy configured for the Device type (or individual Credential Type). For further information, see Customize the Key Protection Methods.
-
The user enters and confirms a Password and then taps OK.
As the user types, the app displays the password rules (such as the number of upper or lower case characters).
The success message is displayed.
See Also: