A Closer Look at Authentication Policies
Login Authentication Policies
Login authentication policies are specific to the static password authentication method. When you use the ActivID Management Console to create a Login Authentication Policy, you must specify the password policy. The policy defines aspects such as:
- The number of unsuccessful authentication attempts before the authentication record is locked
- The default validity period for password of this policy
- Whether or not the policy supports seeding (that is, user authentication using partial characters from the password)
- Password and username constraints
ActivID AS can be configured with multiple Login Authentication Policies. In other words, it can support multiple password policies. Each Login Authentication policy is assigned an encryption key. All passwords created for that authentication policy are encrypted using the assigned key.
If the encryption key for a Login Authentication policy is changed, all new user passwords set up under that type will be encrypted using the new key. Passwords for existing users with authentication records set up under that type will continue to be encrypted with the previous key until the password is changed or until you carry out a manual conversion.
Using the ActivID Management Console, you can set one or more of the following constraints for authentication policies belonging to the Login authentication type. These constraints are applied to the authentication records set up as instances of that authentication policy.
The following table describes the password constraints enforced by ActivID AS preventing weak password usage.
| Active Constraints | Description | Available for Username | Available for Password |
|---|---|---|---|
| Contain only numeric characters | Only numbers allowed, no punctuation, no characters, and no spaces. | X | X |
| Contain only alpha characters | Only letters allowed, no punctuation, no numbers, and no spaces. | X | X |
| Contain either numeric or alpha characters | Combination of letters and numbers allowed, no punctuation, and no spaces. | X | X |
| Contain both numeric and alpha characters | Must have a combination of letters and numbers, no punctuation, and no spaces. | X | X |
| Maximum length | Maximum number of characters for the user name or password (For a user name, the default is 100 characters and can be up to 250 characters; 100 characters for a password). | X | X |
| Minimum length | Minimum number of characters for the user name or password. | X | X |
| Case-sensitive |
The password will be case-sensitive. Note: Make sure you understand the relationship between the Case-sensitive and Different characters constraints. In a string of lowercase characters, uppercase characters are “different.” For example, if you specify Case-sensitive and also specify a value of 3 for Different characters, neither aa11 nor Aa11 will be valid passwords.
|
- | X |
| Must not be any previous password | Previous passwords are saved and compared against new password submissions. | - | X |
| Must not contain username and is not a user attribute |
New password submissions are compared against user attribute values specified for that user. Note: User attribute values, such as surname and date of birth, are specified in relation to attribute types assigned to the user type to which a user belongs.
|
- | X |
| Must not contain black-listed words | Must not contain black-listed words | X | X |
| Must not be a letters or numbers sequence | Password must not consist of a series of numbers or letters (for example, 5678, abc). | - | X |
| Contain at least one numeric character | Contain at least one numeric character | X | X |
| Contain at least one lowercase character | Contain at least one lowercase character | X | X |
| Contain at least one uppercase character | Contain at least one uppercase character | X | X |
| Contain at least one special character | Contain at least one special character | X | X |
| Minimum number of different characters |
User name or password must contain at least the same number of different characters as the number specified in this field. For example, if 3 is specified as the number in this field, aa11 is not valid, while Aa11 could be valid. Note: Make sure you understand the relationship between the Case-sensitive and Different characters constraints. In a string of lowercase characters, uppercase characters are “different.” For example, if you specify Case-sensitive and also specify a value of 3 for Different characters, neither aa11 nor Aa11 will be valid passwords.
|
X | X |
Security Questions Authentication Policies
ActivID AS can be configured with multiple policies for Security Questions. Authentication policies belonging to the Security Questions type support user authentication by validating responses to defined prompts, such as mother’s maiden name and a specific date. These prompts are defined using the ActivID Management Console.
When creating a Security Questions authentication policy, you must specify the policy. The policy defines aspects such as:
- The number of unsuccessful authentication attempts permitted before the authentication record is locked
- The default validity period for authentication records of this policy
- Whether or not the policy supports seeding (that is, user authentication using partial characters from the responses)
- The list of questions that will be asked
- The number of responses that a user must register
A security question prompt can be associated to more than one Authentication Policy. A user’s response to a specific security question prompt is valid across all their security questions authentication records using that prompt. Constraints (for example, being alphanumeric, or being of a maximum or minimum length) can be set for responses to security question prompts.
When a Security Questions authentication record is created for a user, the user must provide responses to the security questions, in line with a specific number of the default prompts from the group. When the user tries to authenticate using that authentication policy, only the prompts for which the user has provided security questions are presented.
There is no constraint on the number of prompts that can be assigned to a particular authentication policy of the Security Questions type.
You can set one or more of the following constraints in the ActivID Management Console for responses to security question prompts. When a prompt with one or more security question constraint(s) is/are included in an authentication policy, the constraint(s) is/are applied to the security questions for all authentication records set up as instances of that authentication policy.
Security question constraints are as follows:
- Numeric − numbers only: no punctuation, no characters, no spaces
- Alpha − letters only: no punctuation, no numbers, no spaces
- Alphanumeric − combination of letters and numbers: no punctuation, no spaces
- Forced alphanumeric − must have a combination of letters and numbers: no punctuation, no spaces
- Case-sensitive − applies the case-sensitive constraint so the response will be checked for case-sensitivity
- Max length − maximum number of characters for the prompt response (up to 50 characters)
- Min length − minimum number of characters for the prompt response
- Not a user attribute − responses are compared against user attribute values specified for that userNote: User attribute values (for example, surname, date–of-birth) are specified in relation to the attribute types assigned to the User Type to which a user belongs.
- Date format − specifies the format for a date in a response. For example, for a response to the prompt “What is your memorable date?” the format is specified using the letters: d, M, and y, as in: dd/MM/yyyy = 12/07/2003, dd/MMMM/yy = 12/July/03
Device Authentication Policies
Device authentication policies are used for all other authentication schemes, especially where a credential is stored on a device, such as a one-time password token or OTP/PKI smart card.
In addition, device authentication policies are used for OOB, LDAP, and custom authentication methods. The applicable authentication method is determined based on the type of credential contained on the device which is also associated to the Authentication Policy.
By default, ActivID AS includes a number of device- based authentication policies for the following Authentication methods:
- One-Time Password
- Push notification based authentication
- PKI Authentication with Certificate check and Challenge/Response
- Out of Band with SMS or SMTP (email)
- LDAP based authenticationNote: LDAP is categorized as a Device Authentication policy as, technically, it’s an extension authentication method.
Timeouts for Authentication Policies
An ActivID AS user session is protected by two timeout periods:
- Session inactivity timeout − applies when a user is authenticated at a particular level and does not use any ActivID AS functionality at that level for the period of the timeout.
- Session valid duration − maximum amount of time that the user can remain logged on to ActivID AS regardless of activity (that is, the maximum amount of time for which the session is valid).
Use the ActivID Management Console to specify these timeout periods for each authentication policy.
- With non-tiered authentication, if either period is exceeded, then ActivID AS automatically closes the user session.
- With tiered authentication, a user initially authenticates to the first level in the tier using an authentication record of the base authentication policy. ActivID AS applies the session inactivity timeout period and the session valid duration timeout period specified for this base authentication policy.
- Ascending the tier by authenticating to each successive level applies the session inactivity timeout specified for the corresponding authentication policy per level, but retains and continues to apply the session valid duration timeout specified for the base authentication policy.
- When closing the authentication to a successive level in the tier, ActivID AS:
- Applies the session inactivity timeout period of the authentication policy for the parent level to which the user returns in the tier, LESS any used session inactivity timeout for the authentication policy for the closed authentication.
- Retains and continues to apply the session valid duration timeout specified for the base authentication policy.
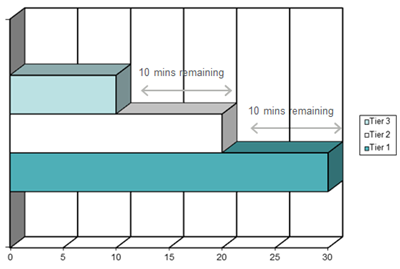
For example, in an authentication tier comprised of three levels, where a user authenticates to the first level in the tier, and the base authentication policy has a session inactivity timeout period of 30 minutes and a session valid duration timeout period of 40 minutes, the user can remain authenticated to ActivID AS at the first level of the tier for 30 minutes without using ActivID AS functionality. The ActivID AS session can last for 40 minutes in total, regardless of the level in the tier to which the user authenticates.
When the user authenticates to the second level in the tier, and the authentication policy for the second level in the tier has a session inactivity timeout period of 20 minutes, the user can remain authenticated to ActivID AS at the second level for 20 minutes without using ActivID AS functionality. The ActivID AS session can still last for 40 minutes in total.
When the user authenticates to the third level in the tier, and the authentication policy for the third level in the tier has a session inactivity timeout period of 10 minutes, the user can remain authenticated to ActivID AS at the third level for 10 minutes without using ActivID AS functionality. The ActivID AS session can still last for 40 minutes in total.
If the user is authenticated to the third level in the tier but does not use any ActivID AS functionality for 10 minutes, ActivID AS applies the session inactivity timeout period, closes the authentication at the third level, and returns the user to the second level in the tier.
ActivID AS then applies the session inactivity timeout period for the authentication policy for the second level, LESS the used session inactivity timeout for the authentication policy for the closed authentication. ActivID AS calculates, and applies a session inactivity timeout period. In this case, it is 20-10=10 minutes now remains for the second level.





