Configure the Push-Based Validation Authentication Policies
For easy configuration/usage purposes, you can use the pre-configured Authentication Policies:
-
Mobile Registration authentication (AT_TDSOOB)
-
Mobile push-based Logon Validation (AT_PASA)
-
Mobile push-based Action Validation (AT_TDS)
-
Mobile application update (AT_SMK)
-
Customer One Time Password (AT_CUSTOTP)
In this case, you only need to:
-
Verify that these policies are enabled for the end user’s User Type (they are enabled by default).
-
Add the Azure Delivery adapters to the push-based authentication policies.
-
Log on to the ActivID Management Console and select the Access Administration tab.
-
Select the Configuration tab.
-
Under User Organization, select User Types.
-
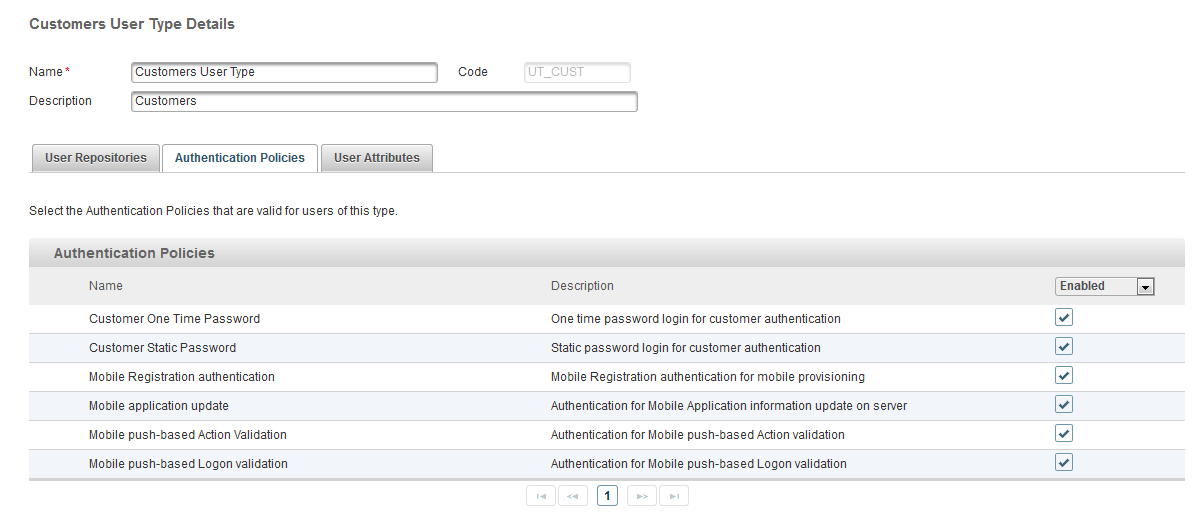
Select the User Type that corresponds to your push-based users’ administration group.
For example, if the users belong to the Consumer Online Banking (USG_CUST1) administration group, then the policies must be enabled for the corresponding Customer User Type (UT_CUST) (as illustrated below).
-
Select the Authentication Policies tab and verify that the required policies (listed below) are enabled:
- Mobile Registration authentication (AT_TDSOOB)
- Mobile push-based Logon Validation (AT_PASA)
- Mobile push-based Action Validation (AT_TDS)
- Mobile application update (AT_SMK)
- Customer One Time Password (AT_CUSTOTP)
By default, the predefined Customers User Type and Employees User Type are configured with the push-based validation policies.
-
Select the Configuration tab.
-
Under Policies, select Authentication, and then select Authentication Policies.
-
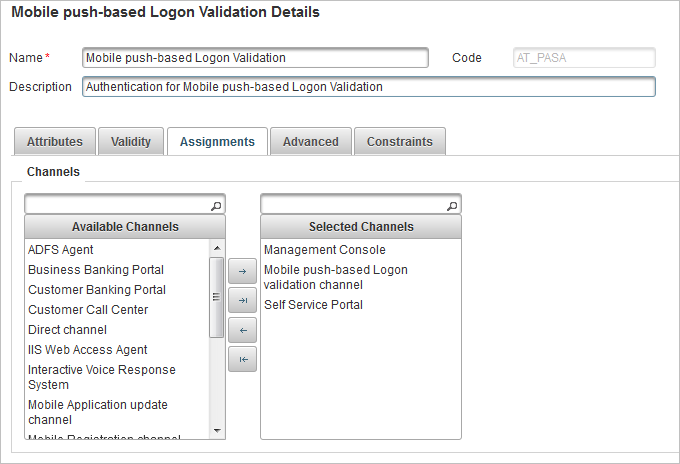
In the list of policies, select Mobile push-based Logon Validation (AT_PASA).
-
Select the Assignments tab.
-
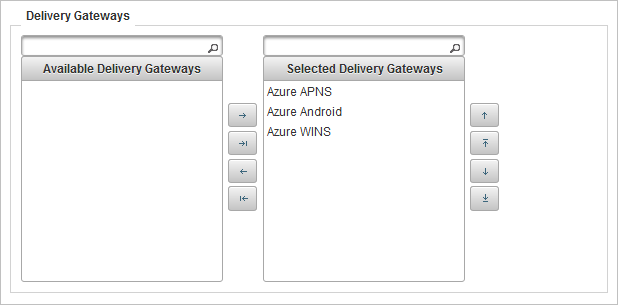
Add the Azure APNS and Azure Android and Azure WINS Delivery adapters (that you created previously) to the list of selected gateways for the policy.
-
Click Save.
-
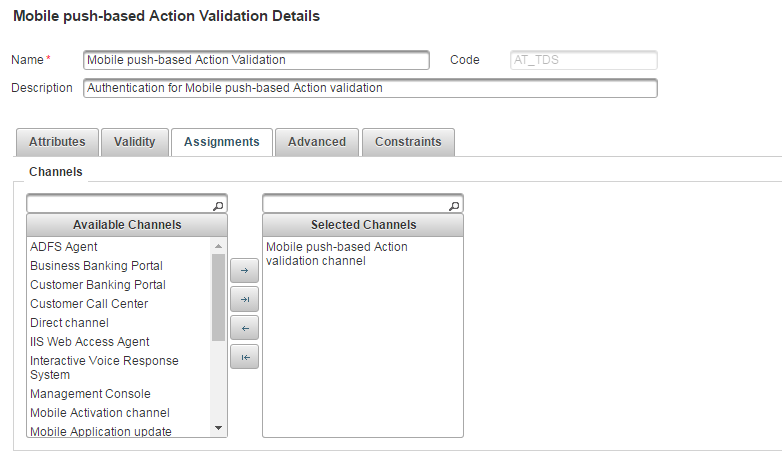
Optionally, if you also want users to validate actions (such as adding a beneficiary) using push-based notifications, return to the list of Authentication Policies under Authentication, and then select Mobile push-based Action Validation (AT_TDS).
-
Select the Assignments tab.

-
Add the Azure APNS and Azure Android and Azure Windows Delivery adapters (that you created previously) to the list of selected gateways for the policy.
-
Click Save.





