-
Create the Managed domain(s).
-
Create the dedicated user type, user group, authentication type and roles for external administration users.
The administrator is granted the privileges based this group, roles, authentication policy and the SCIM channel.
You can reuse any user group, authentication type. Any roles from the JWT token that are not defined in the Managed Domains will be ignored.
For example, create the following user group:
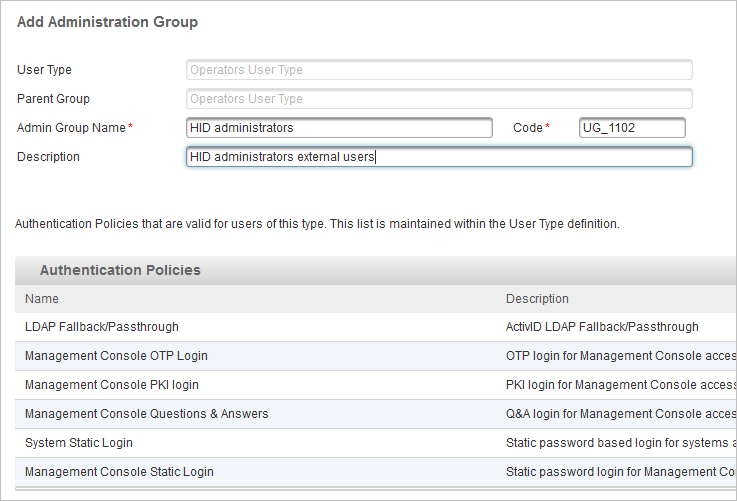
An administrator of this group will inherit the following permissions:
-
Device Administration Functions
-
Read User Details
-
User Administration Functions
-
-
Configure the JWT session validation adapter that will validate the JWT sessions generated by the Administration Domain.
You can configure multiple adapters on the same channel(s) as long as they have a distinct JSON Web Token Issuer.
Local session can also be used concurrently on these channels.
-
In the Configuration tab, under Environment, select Adapters and click Add.
-
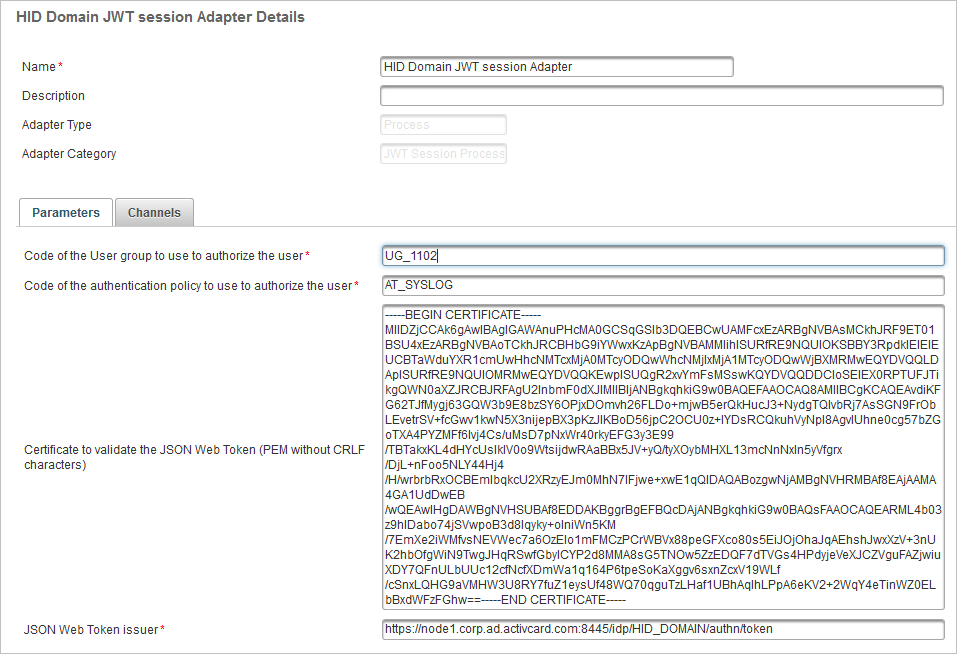
Enter the main information for the adapter:
-
Name – mandatory and should be unique for ease of administration.
-
Description – a user-friendly description of the adapter (optional).
-
Adapter Type – select Process.
- Adapter Category – select JWT Session Process Adapter.
-
-
Define the Parameters for the adapter:
-
Codes of the User Group and authentication policy to authorize the user – enter the codes for the group and policy defined for the administrator external users.
-
Certificate to validate the JSON Web Token – copy the contents of the IdP signing certificate (without the CRLF characters) that you downloaded in the previous section.
-
JSON Web Token issuer – enter the following value based on the IDP_HOSTNAME and IDP_HTTPS_PORT properties from <ACTIVID_HOME>/ActivID_AS/applications/resources/common/activid.properties file.
https://<IdP public FQN>:<IdP public port (if not SSL standard port)>/idp/<Issuer domain>/authn/token
-
-
- Click Save.





