Dynamically Register an OpenID Client
OpenID provides a protected endpoint with which OpenID clients can be dynamically registered.
A predefined OpenID client with administrative permissions authenticates and then sends registration requests to this endpoint to register and administer other clients.
A user with administrative permissions must be defined as the OpenID Client (referred to as the ‘OpenID administrator’ in this section). This user must also have an associated OpenID client (organization) configuration adapter.
Subsequently, as this OpenID administrator, you can register new OpenID clients via the OpenID register endpoint.
Create the OpenID Administrator for Dynamic Registration
Create an OpenID administrator configured with a valid logon authenticator and the required permissions that you will use to register OpenID clients.
-
Log on to the ActivID Management Console as an ActivID Administrator and create an ActivID AS user with administrative privileges (for example, called OpenID_admin) in the System Users group.
-
Select the Wallet tab and create a password for the user with the System Static Login authentication policy.
-
Create the Permissions set to register/unregister a client:
-
Select the Access Administration tab and, under Access Control, select Permission Sets.
-
Click Add.
-
Enter a descriptive Name for the permission set (for example, OpenID Client Registration Permissions) and edit the Code if necessary.
-
From the Permission Type drop-down list, select Predefined.
-
From the Resource Type drop-down list, select Admin Group.
-
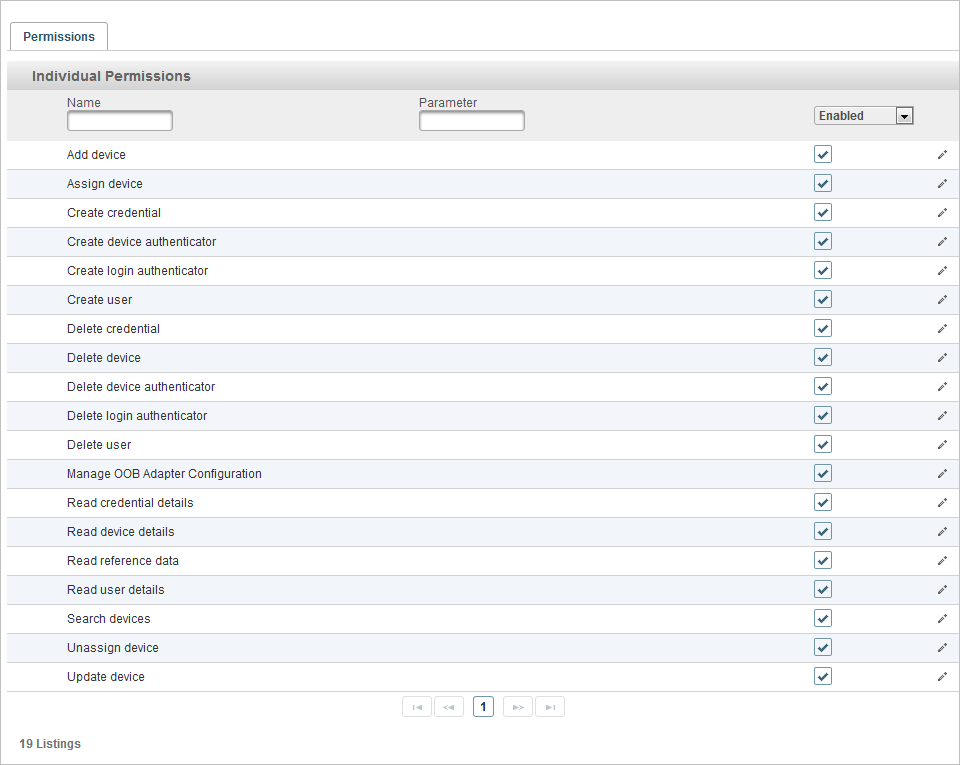
Select the required permission(s) from the Individual Permissions list as illustrated above and Click Save.
-
-
Assign the Permission Set to the System Users group:
-
Select the Access Administration tab and, under User Organization, select Administration Groups.
-
Click on the name of the System Users group.
-
Select the Permissions tab, and then scroll down to Available to view the available permissions for the group.
-
Click Assign for the OpenID permission set you created above to assign it to the group.
-
Keep the default values (Any …) for policy, channel and resource, click Next and then OK.
-
Click Ok to apply the settings.
-
-
Create an OpenID adapter – with same name as the "OpenID administrator":
-
Select the Configuration tab and, under Environment, select Adapters.
-
Click Add.
-
Enter the main information for the adapter:
- Name – mandatory (should use same name as the “OpenID administrator”)
- Description – a user-friendly description of the adapter (optional).
- Adapter Type – select Process to send notifications of operational events (such as user validations).
- Adapter Category – select OpenID client (organization) configuration as the definition of the adapter.
-
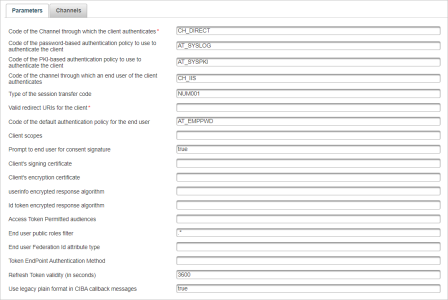
Enter the required parameter:
- Valid redirect URIs for the client - mandatory
- If necessary, enter the optional parameters:
For example, you can customize the expected channel and authentication policy for end users according to users group configuration used by your application.
-
Individual IP - supports the IPv4 or IPv6 protocols (for example, 10.16.125.223)
-
IP range - defined by CIDR block allocation (for example, 10.16.124.0/32)
The default values are defined in the /usr/local/activid/ActivID_AS/applications/resources/ap/samlidp.properties file:
Parameter Description Default value Property hid_client_channelChannel through which the client authenticates CH_DIRECT OpenId.DEFAULT_RP_CLIENTCHANNEL hid_client_pwd_policyPassword-based authentication policy to use to authenticate the client AT_SYSLOG OpenId.DEFAULT_RP_CLIENTCREDAUTHPOL hid_client_pki_policyPKI-based authentication policy to use to authenticate the client AT_SYSPKI OpenId.DEFAULT_RP_CLIENTPKIAUTHPOL hid_client_credential_typeCredential type for authentication type configured for OpenID client authentication if the authentication type is configured with several credential types Not applicable
Note: This parameter is not present by default, and does not have a default value or associated property.hid_user_channelChannel through which an end user of the client authenticates CH_TDSPROV OpenId.DEFAULT_RP_USERCHANNEL hid_user_authn_policyDefault authentication policy for the end user AT_TDSOOB OpenId.DEFAULT_RP_USERPWDAUTHPOL hid_sessiontransfer_typeType of the  transfer policy for the session's authorization code
transfer policy for the session's authorization codeNUM001 OpenId.DEFAULT_RP_USERSESSIONTRANSFTYPE hid_client_groupDefault user group for the client USG_SYS OpenId.DEFAULT_RP_USERPARENTGROUP hid_client_authentication_constraintsWhitelist of IP addresses allowed to authenticate the OpenID client
The supported value is a comma-separated list containing individual, or a range of, IP addresses as a string:
The value can contain both individual and ranges.
For example:
"10.16.125.223,10.16.124.0/32"
If the parameter is not present or undefined, no IP restriction will be applied for OpenID client authentication
Not applicable
Note: This parameter is not present by default, and does not have a default value or associated property. -
-
Click Save.
Dynamically Register a New OpenID Client
-
Call the OpenID token endpoint with the predefined OpenID administrator's credentials to obtain an access token.
-
(Optional) Call the OpenID configuration endpoint to get the register endpoint URL.
-
Send the OpenID client registration request to the OpenID register endpoint with the predefined OpenID administrator's access token to register an OpenID client with the required parameters (see Supported Parameters for OpenID Client Registration Requests).
A successful registration will:
-
Create a user in the specified (or configured) user group with a generated client id.
-
Create the corresponding credential based on the:
-
token_endpoint_auth_method – this parameter is optional.
- hid_client_xxx_policy
If not present, the default value is client_secret_post (the OpenID Connect Registration specification defines client_secret_basic as the default value but client_secret_post is used as it is more secure).
-
-
Create a password credential or a device (if required such as for PKI credentials) and assign it to the user.
-
Create the corresponding authentication record.
-
Create an OpenID adapter.