An OpenID Client can be registered and configured manually using the ActivID Management Console.
-
Register a user and define a valid credential except if it represents a “Public Client” (in which case it does not need credentials):
-
Log on to the ActivID Management Console as an ActivID Administrator and go to the Help Desk tab.
-
Under Users, click Register User and follow the wizard’s instructions to register a user with a valid credential.
-
-
Create an OpenID Client Configuration adapter for this user:
-
In the Configuration tab, under Environment, click Adapters.
- Click Add and create an OpenID client (organization) configuration adapter with the same name as the user (in this example, spl-api):
-
-
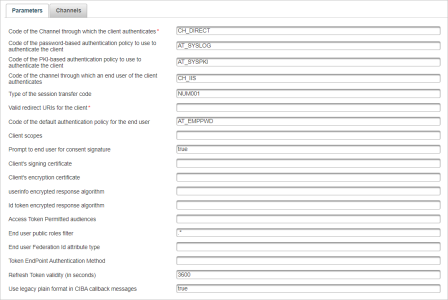
Configure the adapter’s Parameters according to the OpenID client’s configuration:
Code of the Channel through which the client authenticates
Code of the password-based authentication policy to use to authenticate the client
Code of the PKI-based authentication policy to use to authenticate the client
Code of the channel through which an end-user of the client authenticates
Type of the session transfer code
Valid redirect URIs for the client (comma delimited)
- Code of the default authentication policy for the end user
In this example, the user spl-api is registered in the System Users Admin Group with a static password credential (using the System Static Login authentication policy).
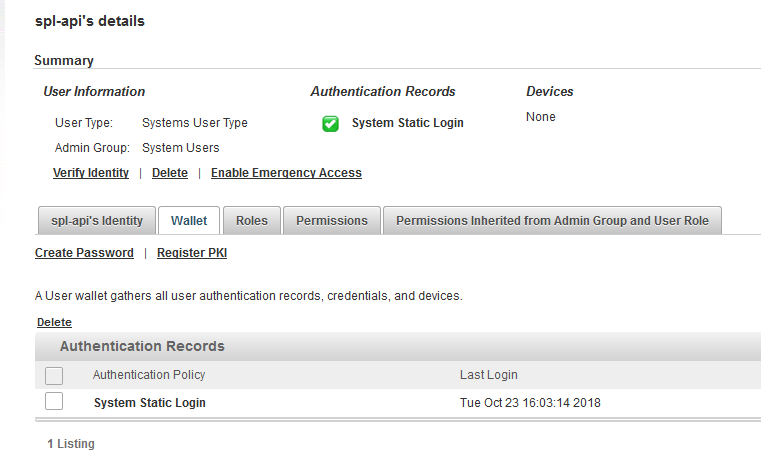
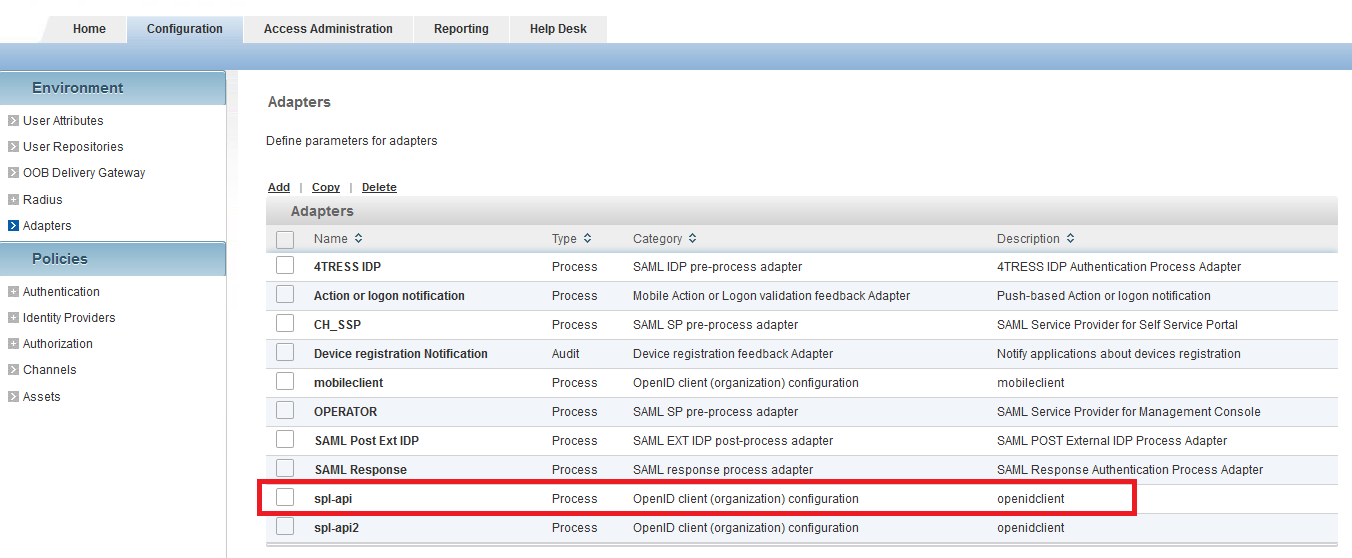
The important parameters are:
For additional parameters, see OpenID client (organization) configuration.
You can also configure the OpenID Client Configuration adapter for the following:
| Configuration option | Parameters |
|---|---|
|
OpenID end-user claims and consent capture |
For further information, see Enabling OpenID Connect Claims and Prompting User for Consent. |
|
OpenID request object support |
For further information, see Configuring Support for OpenID Connect Request Objects. |
|
Domain Federation |
For further information, see Configuring Security Domain Federation. |
|
OpenID client’s type – public client or confidential client |
For further information, see section Configuring OpenID Connect Support of Public Clients. |
|
Refresh Token support |
For further information, see Configuring Support for Refresh Tokens. |
|
Format and signature of the ID Token in the CIBA response |
Use legacy plain format in CIBA messages Possible values:
To keep the previous behavior, set the parameter to true. Note: If you dynamically register the client, the corresponding parameter is
hid_ciba_callback_format_plain. For further information, see Supported Parameters for OpenID Client Registration Requests.Optionally, you can also configure the OpenID client for ID Token encryption using the following parameters:
|