Configuring Application Recovery Mode
In addition to the usual application recovery mode, you can select the “CA Managed” recovery mode in the application configuration screen.
For the "CA Managed" mode, the credential provider generates a credential profile template with ExternalKeyRecovery usage information for each Entrust certificate definition having the "Key backup" property (for example, ct_piv_user:PivEnc). The "CA Managed” mode is available if there is at least one such profile template.
Depending on the provisioning method selected, see the following respective sections.
Provisioning Method Set to Create Credential
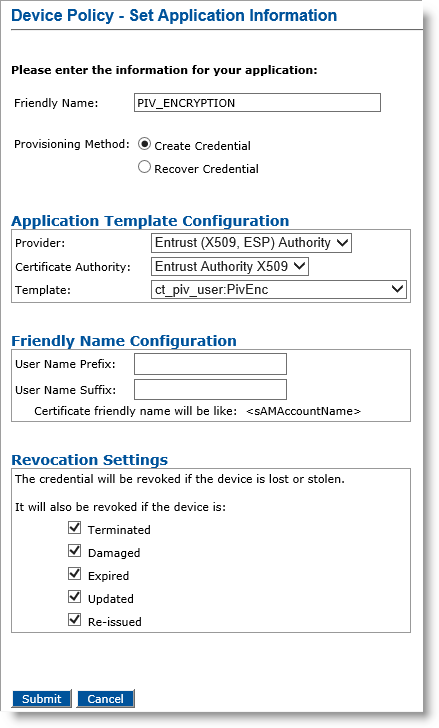
The list of templates does NOT contain the templates with the “usage” set to ExternalKeyRecovery.
For information on how to set the application information, refer to Configuring a PKI Application Using an Entrust Authority CA.
Provisioning Method Set to Recover Credential
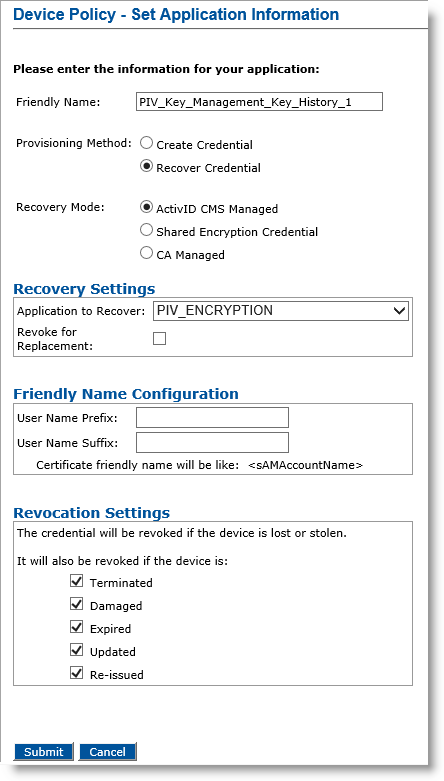
-
If you select Recover Credential for the Provisioning Method option, the Recovery Mode options become available.
Note: Selecting the Recover Credential option is the equivalent of setting the former Recover Application option (available in previous ActivID CMS versions) to Yes. -
Select and configure one of the following modes according to the location of the credential In the context of ActivID, a credential is a collection of one or more credential elements that together provide some form of digitally provable identity. In the context of PIV, a credential refers to the completed PIV card itself. to recover:
Note:-
To avoid any inconsistent behavior, do not mix “ActivID CMS Managed” and “CA Managed” applications from the same CA in the same device policy.
-
If you select Recover Credential, but the usage information is absent or set to a value other than ExternalKeyRecover in the templates, then the “CA Managed” recovery option is not displayed.
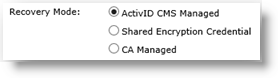
-
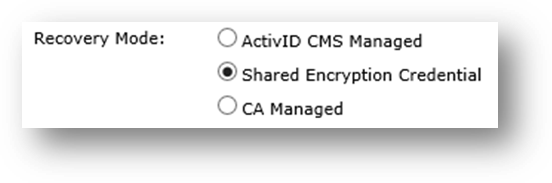
ActivID CMS Managed
This is the usual ActivID CMS recovery mode (for standard replacement, applications update and re-issuance operations) where the credential to recover is present in the ActivID CMS system.
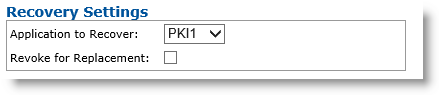
-
Application to Recover drop-down list—Select the application you want to recover from the original device (this means that credentials on this PKI slot contain a certificate template that escrows credentials).
-
Revoke for Replacement option—Select this option if you want to revoke credentials when a device replacement request is executed.
Note: The ActivID CMS Managed option is not available for mobile app certificate device policies. -
-
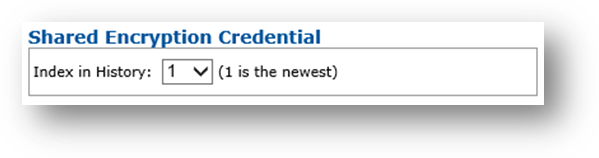
Shared Encryption Credential
This is the mode where the key of the credential to recover, already issued to the same user, has been archived by ActivID CMS on the Certificate Authority.
-
Index in History drop-down list—Select number indicating position of credential to recover in the list of shared encryption credentials available (newest item is at position 1).
Note:-
The Shared Encryption Credential option is the only recovery mode supported for mobile app certificate device policies.
-
Currently, when using mobile app certificates, you can only recover the latest shared encryption credential on mobile devices.
-
-
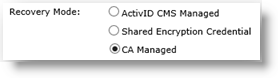
CA Managed
This is the mode where the credential to recover is NOT present in the ActivID CMS system but is on an external CA. The selected certificate authority must provide at least one credential profile template with the “usage” information set to “ExternalKeyRecovery”.
The list of templates contains the templates with the “usage” set to ExternalKeyRecovery.
-
-
Set the Revocation Settings — By default, the credentials are revoked for all the listed states of the device (terminated, damaged, expired, updated, re-issued). You can clear the check box(es) to indicate any state(s) for which you do not want to revoke the credentials. For example, if you clear the Damaged check box, the credentials in a device in the Damaged state will not be revoked.
-
Click Submit.





