New Credential Profile Templates
You must configure a new credential profile template per encryption template for the Entrust credential provider.
The new templates have the “usage” set to ExternalKeyRecovery. Thus, the new templates are available only when you select the option CA Managed.
Each new template has the same name as the related encryption template, but each has specific parameters for external key recovery, as illustrated below:
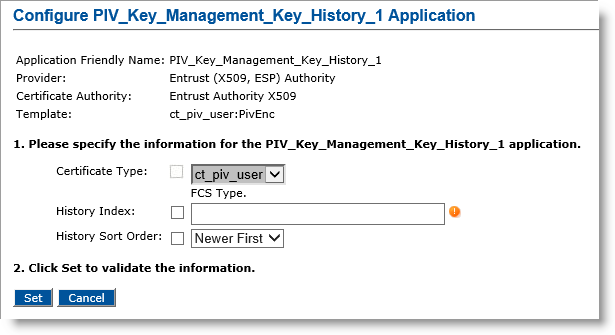
-
Certificate Type: the type of certificate to recover, given by the template.
-
History Index: an integer representing the position (starting at 1) of the certificate to recover in the list of all certificates present in the user key history having the same type as specified above. The list is ordered by certificate serial number. Sort order is defined with the parameter below.
-
History Sort Order: the sort order for the list of certificates. You can select either Newer First (the most recent certificate appears at the beginning of the list) or Older First (the oldest certificate appears at the beginning of the list).
As an example, a new ct_piv_user:PivEnc credential profile template with “usage” information set to “ExternalKeyRecovery“ is available that is intended to recover a PivEnc certificate managed on the CA.
Any certificate recovered with such a credential profile is automatically revoked when necessary. This ensures that only one PIV Personal Identity Verification (technical standard of "HSPD-12") credential of this type is active at any time, as required by PIV specifications.
One Device Policy For All Use Cases
For key history recovery, the purpose is to extract all certificates of a given type from the list for the user being issued the device. The certificates are sorted according to their serial number (ascending or descending, depending on a configuration parameter), and the one at a given index (numbering starts at 1) is selected.
To retrieve the entire history of encryption keys in the same card, you can define one single device policy with a maximum number of PKI encryption applications configured for key history recovery.
-
Thus, the key history can be retrieved for a user disregarding the number of encryption certificates the user actually has, as well as their current status (Active, Revoked, or Expired).
You can define the PKI encryption applications of this device policy as follows:
-
PIV_ENCRYPTION: new certificate using ct_piv_user:PivEnc credential profile template (as usual).
-
PIV_Key_Management_Key_History_1: “Recover / CA managed” using ct_piv_user:PivEnc CA Managed credential profile:
-
Certificate Type: ct_piv_user
-
Index in History: 1
-
History Sort Order: Newer First
-
-
PIV_Key_Management_Key_History_2: “Recover / CA managed” using ct_piv_user:PivEnc CA Managed credential profile:
-
Certificate Type: ct_piv_user
-
Index in History: 2
-
History Sort Order: Newer First
-
You must define each of the PIV key history PKI applications with the same values and in the same way, but with different index positions.
If the index in history is out of bounds, the credential provider ignores the credential creation request. The related application is not personalized.
You must configure these PKI applications with the CA Managed option only. Once a card is issued with this device policy, all the user encryption certificates are stored in the ActivID CMS database, and you can recover them in the “standard” way, if necessary.





