Configuring for Thales SafeNet Luna HSM
To configure Microsoft CA key recovery agent for a Thales® (formerly Gemalto®) SafeNet® Luna HSM, perform the following procedures.
-
Go to C:\Program Files\SafeNet\LunaClient\KSP, and launch KspConfig.exe.
Note: In order to work properly, KspConfig.exe must be run as administrator. -
In the left pane, double-click Register Or View Security Library.
-
In the right-hand pane, go to the library C:\Program Files\SafeNet\LunaClient\cryptoki.dll, and click Register.
-
When the success message appears, click OK.
-
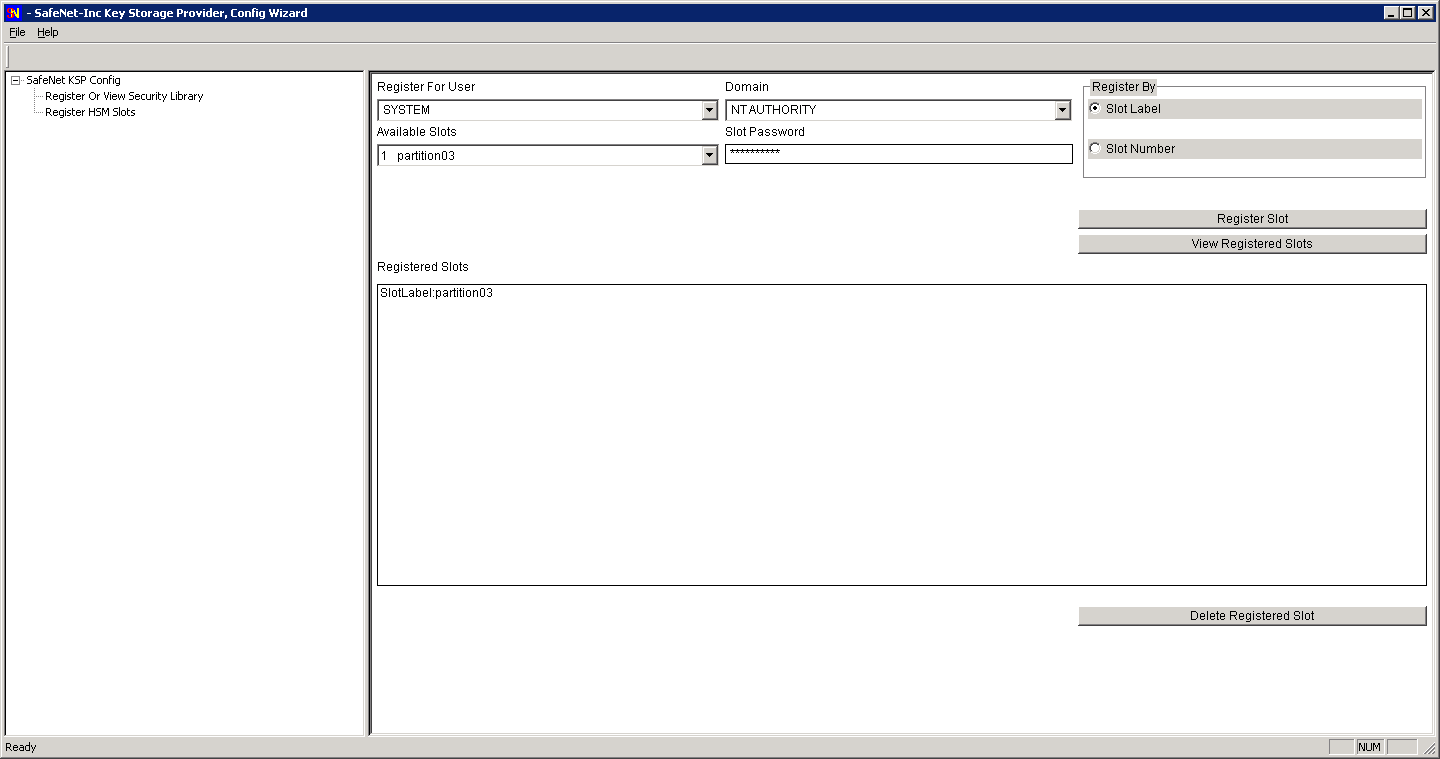
Return to the left-hand pane, and double-click Register HSM Slots.
-
In the Slot Password field, type in the password for the indicated slot.
-
To the right of the window, click the [Register Slot] button to register the slot for ActivID CMS User.
-
In the Register for User field, enter Administrator (or the admin equivalent account that is managing this setup, for example, SYSTEM), and in the Domain field, match the domain or local computer with which you are logged in, for example, NT AUTHORITY. Enter the password for the slot being registered, and again click Register Slot to complete the KSP (Key Storage Provider) configuration.
You should generate the key as follows:
-
Create a text file with the following content:
Copy[NewRequest]
KeyUsageProperty="NCRYPT_ALLOW_ALL_USAGES"
ProviderType=1
RequesterName=CMS\Administrator <Change to the correct user name>
RequestType=PKCS10
ProviderName="SafeNet Key Storage Provider"
Subject="CN=MSCAKRA SafeNet" <Change as appropriate>
KeyContainer="Administrator» <Change as appropriate This will be the label of the key generated in the HSM>
MachineKeySet=false
HashAlgorithm=sha1
KeyAlgorithm=RSA
KeyLength=2048 -
Save the file as policy.inf.
Note: The policy.inf file must be saved in ANSI format. -
Run the following command:
Copycertreq -new policy.inf policy.req -
Submit the certificate signing request (CSR) in the policy.req to the CA. From the HSM client machine, use a command specifying the KRA Key Recovery Agent template name as follows:
Copycertreq -attrib "CertificateTemplate:KRAinHSM" -submit policy.reqNote: The KRA certificate issued by the CA must first be configured as a recovery agent for the CA in order for ActivID CMS to be able to recover certificates using the KRA key stored in the HSM.
Import the certificate from the CA to the personal certificate store of the ActivID CMS user.
-
Import the certificate from the CA into the personal certificate store of the ActivID CMS user.
-
Copy the thumbprint of the certificate.
-
Open the command prompt, and enter the following command:
CopyCd \Program Files\SafeNet\LunaClient\KSP -
Run the following command:
Copycertutil -f -user -v -repairstore -csp "SafeNet Key Storage Provider" "My" "<Thumbprint of Certificate>" -
Make sure the certificate in the certificate store has a corresponding private key.





