About High Availability Mode
The Thales SafeNet Network HSM / Thales TCT Luna SA HSM implements a High Availability (HA) mode that connects one or more HSMs together to form a virtual device. The client application accesses only the virtual partition exposed by the HA group. It does not access each HSM individually. All HSMs involved in the HA belong to that group. A virtual partition consists of a phantom partition that identifies physical partitions existing in one or more HSMs.
HA provides load balancing across all the HSMs from this virtual group. HA load balancing provides improved performance and reduces the overall response time during HSM access. In case of failure in any HSM part of the group, the HA mode automatically redirects the requests to the other remaining operational HSMs. From the client perspective, there is no interruption of services.
Using HA is an option that requires the physical presence of several HSMs during deployment. These HSMs must be of the same type: either Trusted Path Authentication or Password Authentication.
Adding an HA Group
Before you create an HA group, verify the following list of prerequisites.
-
The Allow Cloning and Enable Network Replication parameters are enabled.
-
Allow Cloning is already enabled according to parameters listed in Using the ‘showPolicies’ Command. For details, see Creating Partitions. Make sure that Enable Network Replication is enabled by running the following command:
Copy[adr_luna_sa] lunash;>hsm –changePolicy –policy 16 -value 1
-
All HSM group members that belong to the same cloning domain must use the same red PED key.
-
Each HSM must have at least one partition created. There is no requirement to use the same partition name. However, each partition must be set using the same password. This is the password that authenticates the client.
-
Record the serial number of each partition that is created on each HSM. These partition numbers are required during the creation of the HA group.
-
Each partition can be configured to be Auto-Activated (if this is not already the case).
-
Assign the client to each partition (found on each HSM). For details, see Procedure 6: Assign a Client to an HSM Partition.
-
On the client system, open a DOS window from the following location (C:\Program Files\SafeNet\LunaClient), and then call the vtl software using the haAdmin option. For example:
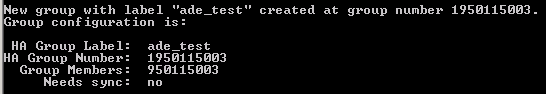
CopyVtl haAdmin –newGroup –serialNum 902514001 –label ade_test –password 12345678 -
To access other partitions that are on other existing HSMs in the HA group, run the following commands:
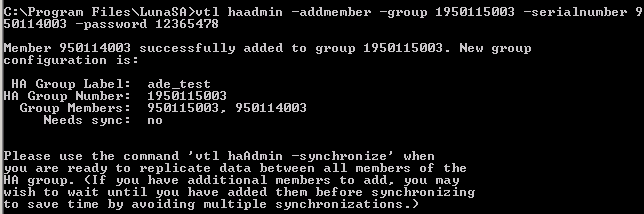
CopyVtl haAdmin –addmemember –group [groupname] –serialNum {serial number for the other partition] –password [Partition password]
Deleting an HA Group
This section describes how to delete an HA group. Use the commands in the following example as a guide: