Procedures for Configuring the Mobile Portal
The Configure Mobile Portal link is only available when support for mobile app certificates has been enabled. For details on enabling support for mobile app certificates, see Setting Parameters for Devices.
When using an HSM A Hardware Security Module (HSM) securely stores secret key material. They are similar to large-storage, multisession smart cards. However, unlike smart cards, they are used mainly on the server side of a system. (recommended), the operator must first generate keys in the HSM for the required certificates, which can then be used to configure the mobile portal. For more details, see Procedure 1: Generating Keys and Details of Certificates Required for Mobile App Certificates Issuance.
When updating the mobile portal, it is recommended to use certificates stored in an HSM. If using software certificates, they must be of the PKCS#12 type (filename extension .pfx or .p12). These files can be uploaded from the workstation. It is not recommended to use the auto-generated certificates provided by default for deployment purposes.
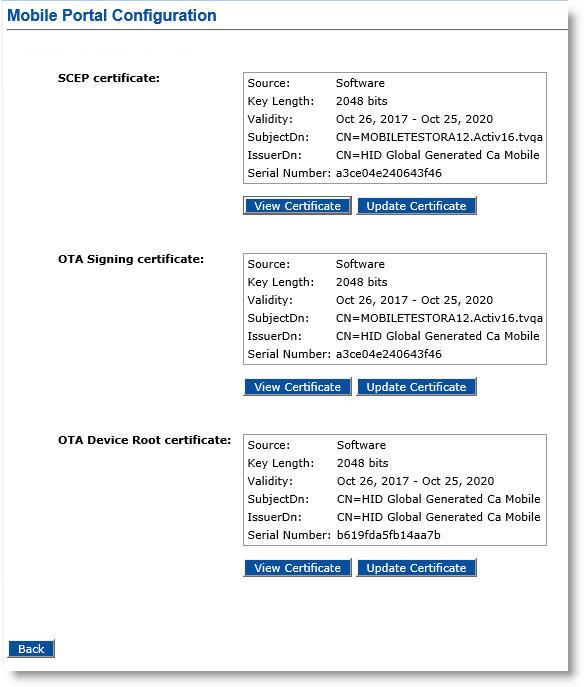
Note that the OTA Device Root certificate does not need to be installed on the user’s mobile device.
For details about mobile app certificates, see Managing Mobile App Certificates.
The following table includes a description of the certificates managed on the mobile portal as well as details such as their issuer, default location, and key usage.
When using an HSM, the operator must generate the corresponding keys for the SCEP, OTA Signing and OTA Device Root certificates in the HSM. These keys can then be used to update the mobile app certificates.
To generate a key for each certificate, the operator must:
-
Select the Configuration tab and then click HSM Credentials.
-
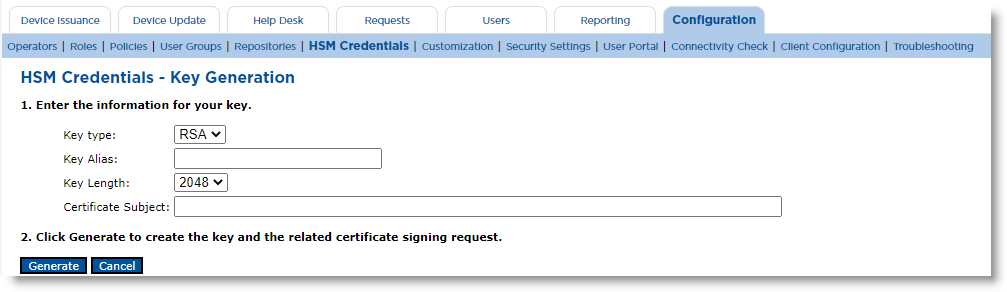
Click Generate Key.
-
Enter the Key Alias, select a Key Length and enter the Certificate Subject. Then click Generate.
In addition, for the SCEP and OTA Signing certificates, the operator must:
-
Use the corresponding Certificate Signing Request (CSR) to request a certificate from the CA. (Locate the desired key and click Get CSR in the associated Action column.)
-
Attach this certificate to the key. (Locate the desired key and click Attach Certificate in the associated Action column).
-
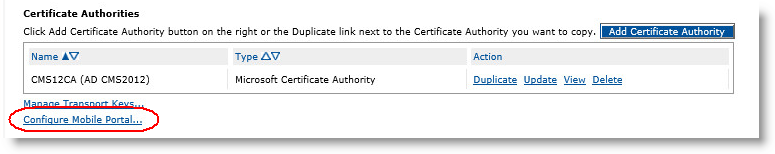
Go to the Repositories Management page.
In the Certificate Authorities panel of the page, click Configure Mobile Portal.
The Mobile Portal Configuration page appears:
-
Click the Update Certificate button next to the certificate you want to replace:
-
If you are using an HSM:
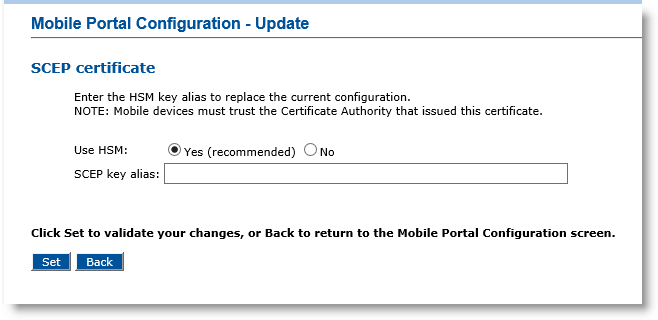
Enter the key alias for the certificate file in the associated field.
-
-
If there is no HSM available, or if you choose not to use it (Use HSM set to No):
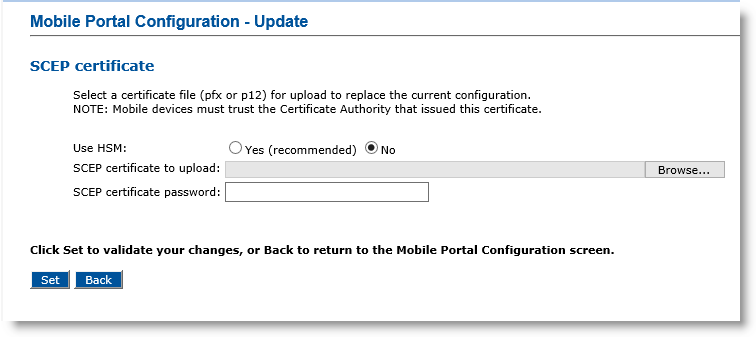
Use the Browse button to select the new certificate file to be uploaded and enter the password protecting this file in the associated password field.
-
Click Set.
-
Go to the Repositories Management page.
-
In the Certificate Authorities panel of the page, click Configure Mobile Portal.
The Mobile Portal Configuration page appears.
-
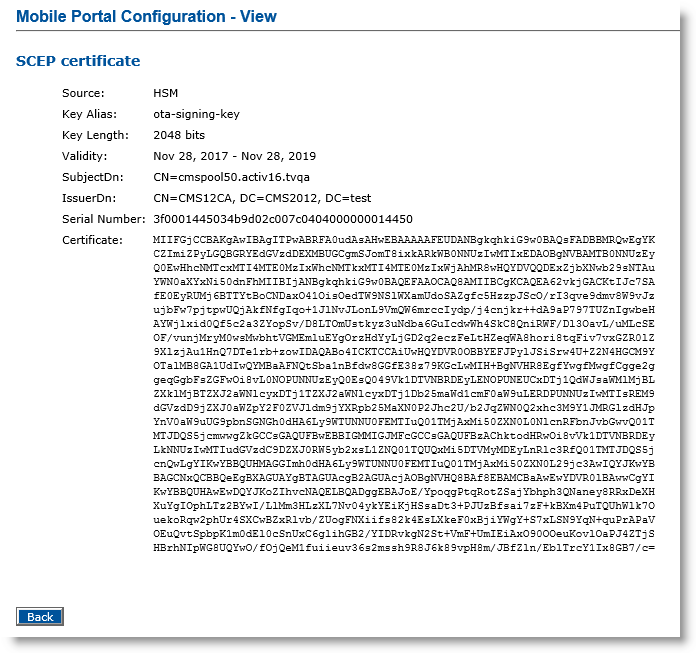
Click the View Certificate button next to the certificate whose details you want to see:
The Mobile Portal Configuration - View page appears:
-
Click Back.





