Procedures for Configuring Connections to Certificate Authorities
In ActivID CMS, you can issue devices containing PKI applications. These applications, for example, enable users to access their computers and sign and encrypt/decrypt their email messages.
ActivID CMS communicates with one or several CA(s) to manage the PKI credentials (that is, the digital certificates and keys). This includes the managing of the issuance, revocation, suspension, and resumption of digital certificates. In addition, it also includes key escrow and recovery capabilities.
After you have installed the appropriate CA(s), you must configure ActivID CMS to create a connection to the CA(s).
The configuration procedure is outside the scope of this section. See the relevant Certificate Authorities section for specific details that explain the CA(s) you are using and any related connection procedures.
This section illustrates how to update a connection to an Entrust® CA.
-
Go to the Repositories Management page.
-
Locate the CA for which you want to update information. Look in the Certificate Authorities panel of the page in the Name column.
-
In the Action column, click Update. The Certificate Authority Update page appears:
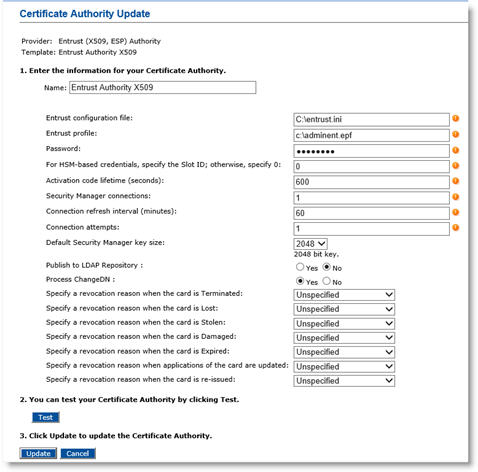
-
Review the data displayed on the page, and edit as required.
-
You can specify a revocation reason for each state of the device. The device can be in the following states: Terminated, Lost, Stolen, Damaged, Expired, and Re-issued.
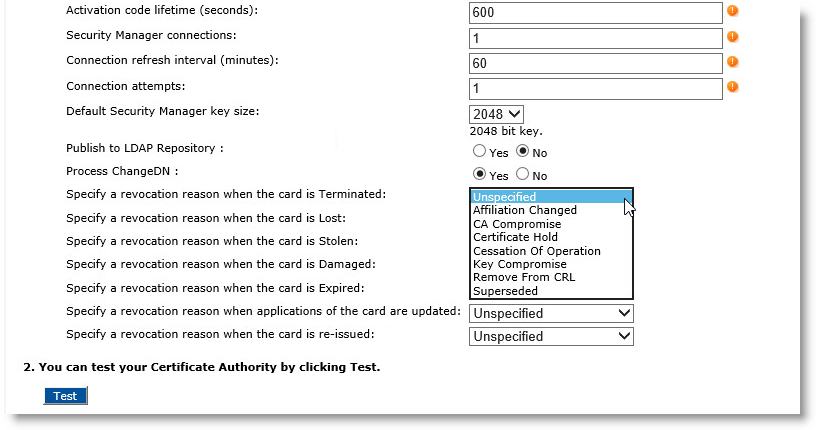
-
Locate the possible state of the device for which you want to update the revocation reason. For each possible state, you can select one of the following reason codes:
-
Unspecified – This option will not specify a reason for revocation.
-
Affiliation Changed – The user’s relationship with the organization has been terminated, indicated in the DN attribute of the certificate. This revocation code is most often used when an individual has been terminated or has resigned from an organization. You do not have to revoke a certificate when a user changes departments, unless your security policy requires a different certificate be issued by a departmental CA.
-
CA Compromise – The token or disk location where the CA’s private key is stored has been compromised and is in the possession of an unauthorized individual. When a CA’s private key is revoked, this results in all certificates issued by the CA that are signed using the private key associated with the revoked certificate being considered revoked as well.
-
Certificate Hold – A temporary revocation that indicates a CA will not vouch for a certificate at a specific point in time. Once a certificate has been revoked with a Certificate Hold reason code, the certificate can be revoked with another reason code, or unrevoked and returned to use.
-
Cessation Of Operation – If a CA is decommissioned (no longer to be used), then the CA’s certificate should be revoked with this reason code. Do not revoke the CA’s certificate if the CA no longer issues new certificates, yet still publishes certificate revocation lists (CRLs) for the currently-issued certificates.
-
Key Compromise – The token or disk location where the private key associated with the certificate is stored has been compromised and is in the possession of an unauthorized individual. This can include the case where a laptop is stolen or a device is lost.
-
Remove From CRL – This reason code indicates that a certificate is to be removed from a CRL because either the certificate expired or was removed from hold.
- Superseded – A replacement certificate has been issued to a user, and the reason does not fall under any of the previous reasons. This revocation reason is most often used when a device fails, the password for a token is forgotten by a user, or the user’s legal name has changed.
-
-
Review the data displayed on the page, and edit as required.
-
Click Test to verify that the connection is working.
-
Click Update.
-
When the connection to the CA is updated, a confirmation message appears. Click Done.
-
For security reasons, the password is not retrieved during an update.
-
It is not possible to change the type of the CA.
-
Go to the Repositories Management page.
-
Locate the CA in the Certificate Authorities section, in the Name column.
-
In the Action column, click View. The Certificate Authority Information page appears:
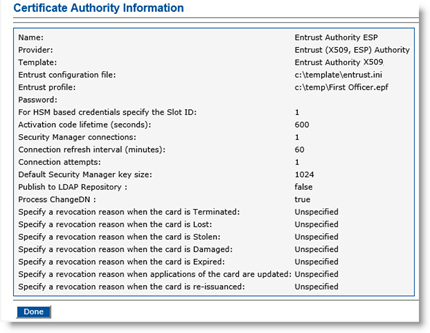
-
Click Done.
Removing a CA from the ActivID CMS database of supported CAs does not affect the CA itself. Removing a CA means that ActivID CMS will no longer manage the credentials issued by that CA. This section illustrates how to delete a connection to an Entrust CA.
-
Go to the Repositories Management page.
-
Locate the CA in the Certificate Authorities panel in the Name column.
-
In the Action column, click Delete. The Certificate Authority Deletion page appears:
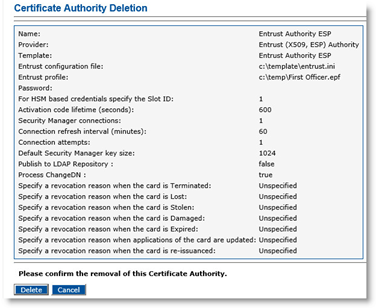
-
Click Delete.
-
When the confirmation message appears, click Done.





