Managing Keys
Key management encompasses the generation, storage, distribution, and use procedures for card keys. Key management procedures must not compromise the security of other systems; and the key management procedures must be specific to the system hosting the key management application.
Two main players are involved during actual deployment:
-
Prepares card security domains.
-
Installs the GlobalPlatform (GP) keys to protect access to each security domain. A GlobalPlatform (GP) security domain is a secure area on the card that stores the cryptographic key values.
-
Injects applications into the cards. Optionally, the card issuer can perform this task.
-
Replaces the card manufacturer’s GP keys with card issuer GP keys. This ensures that the card manufacturer can no longer access the security domains.
-
Injects applications into cards (if not done by the card manufacturer).
-
Personalizes the applications.
-
Issues the cards to end users.
Both entities must securely exchange cryptographic keys to protect the card content and prevent attacks. The card manufacturer makes the cards and sends them to the card issuer. The card issuer processes the cards and must protect them with appropriate security measures. Specifically, each entity performs the following procedures.
Key Management Steps
This section describes the basic steps to key management. It is an overview of best practices and does not provide step-by-step instructions.
For step-by-step directions on how to perform ActivID KMS key ceremonies, how to initialize HSMs A Hardware Security Module (HSM) securely stores secret key material. They are similar to large-storage, multisession smart cards. However, unlike smart cards, they are used mainly on the server side of a system., and other operations, see Using ActivID KMS.
The card manufacturer injects a card with three GP keys for each of its security domains. These three GP keys protect the access to each security domain. The card manufacturer diversifies each GP key by using a specific GP master key and additional data unique to each card (for example, card serial number). Consequently, GP keys are different for each manufactured card.
The card manufacturer uses a key management system (for example, ActivID KMS) to generate these three master keys.
To prepare a new HSM for use, the manufacturer uses the ActivID KMS operation, Initialize the Principal HSM The first or main HSM. If you require multiple HSMs with the same master keys, use HSM manufacturer tools to duplicate the keys in the other HSM.. To add the master keys to an initialized HSM, the manufacturer uses the ActivID KMS operation, Update the Principal HSM.
To securely exchange the master keys with the card issuer, the card manufacturer now generates a transport key. In order to access the security domain, the card issuer uses the transport key (AES128/AES256 or 2TDEA/3TDEA key) to decrypt the master key generated by the card manufacturer’s HSM.
The card manufacturer performs the Add Transport Key operation to add a transport key to the Principal HSM. The transport key protects the GP master keys during an exchange between any two entities (card manufacturer and card issuer).
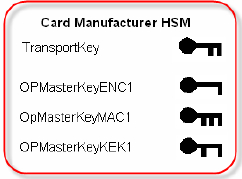
The Add Transport Key operation also generates three transport key sub- components and their corresponding key check values. There are three pairs of security officers at the card manufacturer’s location; each pair of security officers knows one of the three components. The following diagram illustrates the content of the card manufacturer’s Principal HSM after the generation of the three master keys and the transport key.
Card Manufacturer's HSM (Content of Principal HSM After Key Generation)
The card issuer replaces the card manufacturer’s GP keys in the smart cards with new card issuer GP keys. The card issuer uses the same method to generate the new GP keys as the card manufacturer used to create the original GP keys.
The Overall Process for Exchanging GP Master Keys figure below shows the content of the HSM after the card issuer generates three new GP master keys. The keys in the diagram have fictitious key labels.
As shown in previous figure, the card issuer generated three keys in the HSM:
-
OPMasterKeyENC2
-
OPMasterKeyMAC2
-
OPMasterKeyKEK2
Later, each GP key is diversified using the card issuer GP master key and card-specific data.
Now, the card manufacturer and the card issuer exchange the master keys generated by the card manufacturer.
The card manufacturer encrypts the three GP master keys with the transport key. This is the Export Master Key operation.
Three transport key sub-components are generated during the creation of the transport key. Each transport key component is owned by a pair of card manufacturer security officers. Each pair of officers sends their sub- components to their counterparts at the card issuer site. The card manufacturer Security Officer also sends the three encrypted GP master keys to the counterpart (another Security Officer) at the card issuer site. In this way, neither the Security Officer in charge of the GP master keys, nor any one of the six team members holding the three transport key components, know the values of the master keys or the transport key.
The officers at the card issuer site perform a Key Ceremony to inject the transport key sub-components that they have received. This operation reconstructs the transport key originally created at the card manufacturer’s site. This is the Add Transport Key operation.
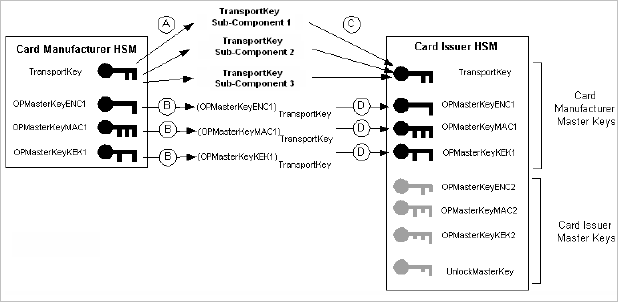
The card issuer Security Officer then enters the encrypted master keys into the Principal HSM. This is the Import Master Key operation. Recall that the Security Officer received these encrypted master keys from the card manufacturer’s Security Officer. Since the HSM already “knows” the transport key, the HSM can now decrypt the encrypted master keys that the Security Officer enters during this step. At the end of the exchange process, the content of the two HSMs (the card manufacturer HSM containing master and transport keys, and the card issuer HSM containing the newly injected keys) can be different; but the four keys that have been exchanged (one transport key and three master keys) are identical. The following diagram illustrates the overall process (the HSMs happen to be identical, but this is not always the case).
Overall Process for Exchanging GP Master Keys
|
Owner |
Activity |
|---|---|
|
Card Manufacturer |
A. Creates transport key (three components are computed). B. Encrypts the master keys with the transport key. |
|
Card Issuer |
C. Performs Key Ceremony to reconstruct the manufacturer’s transport key using the three key components. D. Injects the encrypted master keys. The HSM decrypts them, using the original transport key. |





