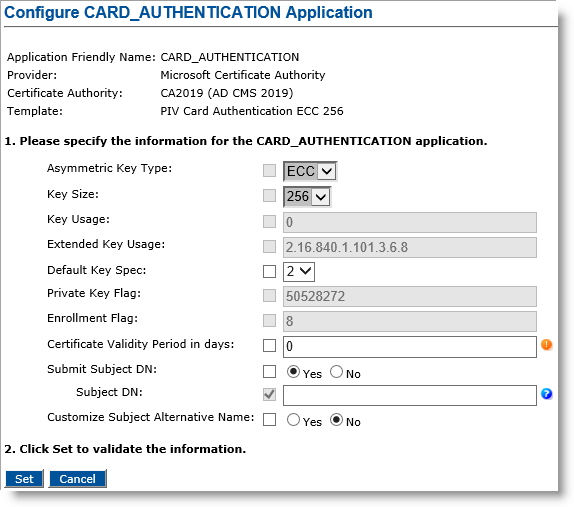
Configuring a PKI Application Using a Microsoft CA
For detailed instructions on how to configure a PKI application using a Microsoft CA, see the example in Creating a Device Policy completed by the section below.
Customizing the Subject Alternative Name for Microsoft PKI Applications
Microsoft CA The Certificate Authority (CA) issues and manages security credentials and public keys for message encryption in a networks environment. is the credential provider.
A template has been chosen that has the "Source of subject name" parameter set to "Supplied in the request".
To customize the Subject Alternative Name (SAN) for a Microsoft PKI application, perform the following steps:
-
Go to the PKI Application Configuration page. For detailed instructions how to get to this page, see Creating a Device Policy.
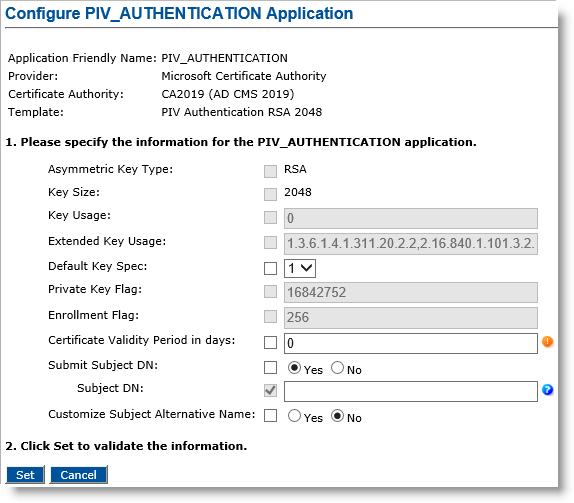
-
Customize Subject Alternative Name option—Select Yes.
Additional fields will appear as shown below.
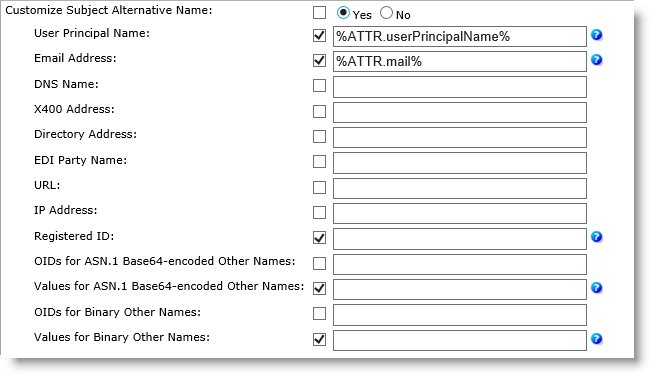
-
User Principal Name option—Corresponds to the single-valued GeneralName “otherName”. Default value is %ATTR.userPrincipalName% (dynamic).
With the User Principal Name set in the syntax “%ATTR.userPrincipalName%”, ActivID CMS will compute the attribute using the LDAP Lightweight Directory Access Protocol attribute “userPrincipalName”. The attribute will be added as GeneralName “otherName” with the OID = "1.3.6.1.4.1.311.20.2.3" (OID for UPN).
-
Email Address option—Corresponds to the GeneralName “rfc822Name”. Default value is %ATTR.mail% (dynamic).
With the default set in the syntax “%ATTR.mail%”, ActivID CMS will generate the attribute using the LDAP attribute “mail”.
-
DNS Name option—Corresponds to the GeneralName “dNSName”. The attribute can be multi-valued (use “&” as separator). The value is static by default.
-
X400 Address option—Corresponds to the GeneralName “x400Address”. The attribute must be in “ASN.1 base64-encoded” format. The value is static by default.
-
Directory Address option—Corresponds to the GeneralName “directoryName”. The attribute can be multi-valued (use “&” as separator). The attribute is static by default.
-
EDI Party Name option—Corresponds to the GeneralName “ediPartyName”. The attribute must be in “ASN.1 base64-encoded” format. The attribute is static by default.
-
URL option—Corresponds to the GeneralName “uniformResourceIdentifier”. The attribute can be multi-valued (use “,” as separator). The attribute is static by default.
-
IP Address option—Corresponds to the GeneralName “iPAddress”. The attribute can be multi-valued (use “&” as separator). The attribute is static by default.
-
Registered ID option—Corresponds to the GeneralName “registeredID”. The attribute can be multi-valued (use “&” as separator). The attribute is static by default.
-
OIDs for ASN.1 Base64-encoded Other Names option—A list of comma-separated OIDs for ASN.1 Other Names are in Base64 format. No default attribute. The attribute is static by default.
The number of OIDs must match the number of values in the “Values for ASN.1 Base64-encoded Other Names” parameter.
The following screenshot illustrates the setting of two elements: 1.3.5.7=%ATTR.asn1Attr1% and 2.4.6.8=%ATTR.asn1Attr2%:
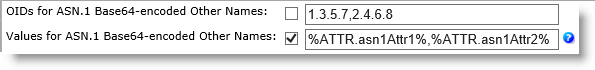
-
Values for ASN.1 Base64-encoded Other Names option—A list of comma-separated values for ASN.1 Other Names are in Base64 format. No default value. The attribute is dynamic by default.
The number of values must match the number of OIDs in the “OIDs for ASN.1 Base64-encoded Other Names” parameter.
-
OIDs for Binary Other Names option—A list of comma-separated OIDs for Other Names with a binary value. No default attribute. The attribute is static by default.
The number of OIDs must match the number of values in the “Values for Binary Other Names” parameter.
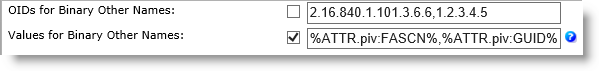
The example above illustrates the setting of two elements: 2.16.840.1.101.3.6.6 =%ATTR.piv:FASCN% and 1.2.3.4.5=%ATTR.piv:GUID%.
-
Values for Binary Other Names option—A list of comma-separated values for Other Names with a binary value. No default value. The value is dynamic by default.
The number of values must match the number of OIDs in the “OIDs for Binary Other Names” parameter.
Using ECC Keys with Microsoft Card Authentication Applications
The procedure for configuring a Card Authentication application is the same as described more generally in Creating a Device Policy. Note that on the Configure Card Authentication Application page, the Asymmetric Key Type and Key Size corresponding to the selected template are automatically displayed: