Configuring Support for Multiple PIV Signers
In order to use multiple PIV Personal Identity Verification (technical standard of "HSPD-12") signers, you need to make changes to the PIVEnrollment.properties file, as well as the XML Schema Definition and CPR The Card Production Request (CPR) contains a list of user-specific attributes that will be stored, fully or partially, in the PIV Metadata database, and will be loaded on the PIV card during the issuance. XML files.
PIVEnrollment.properties
There are 4 indexable parameters which can be configured:
-
sign.p12_password: present if sign.hsm is set to false
-
sign.p12_filename: present if sign.hsm is set to false
-
sign.alias: present if sign.hsm is set to true.
-
hash.algo: always present
Other parameters, such as sign.hsm for instance, are not indexable, which means that the sign.hsm value will apply to all the key indexes. As a result, all the signatory keys are either all in an HSM A Hardware Security Module (HSM) securely stores secret key material. They are similar to large-storage, multisession smart cards. However, unlike smart cards, they are used mainly on the server side of a system. (sign.hsm set to true), or they are all in software (sign.hsm set to false); there cannot be a mix between HSM and non-HSM keys.
To add the new parameters to the PIVEnrollment.properties file:
-
Go to the ActivID CMS configuration directory (for example: %PROGRAMDATA%\HID Global\Credential Management System\Shared Files\).
-
Make a backup copy of the existing PIVEnrollment.properties file in a different folder and with a different extension.
-
Edit the PIVEnrollment.properties file.
Important: Do not overwrite your PIVEnrollment.properties file as it contains other configuration specific to your environment.
-
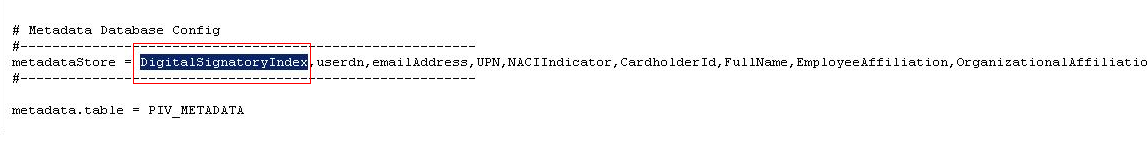
Add the new DigitalSignatoryIndex attribute to the metadataStore parameter as shown here:
-
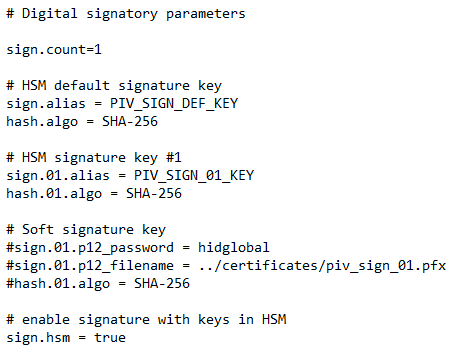
Add the new sign.count parameter.
Note: This is the number of digital signatory keys, in addition to the default signatory key. -
For each digital signatory key, add the parameters defining the key:
-
hash.xx.algo + sign.xx.alias (for HSM keys), OR
-
hash.xx.algo + sign.xx.p12_password + sign.xx.p12_filename (for non-HSM keys).
-
An example of the configuration is shown below:
-
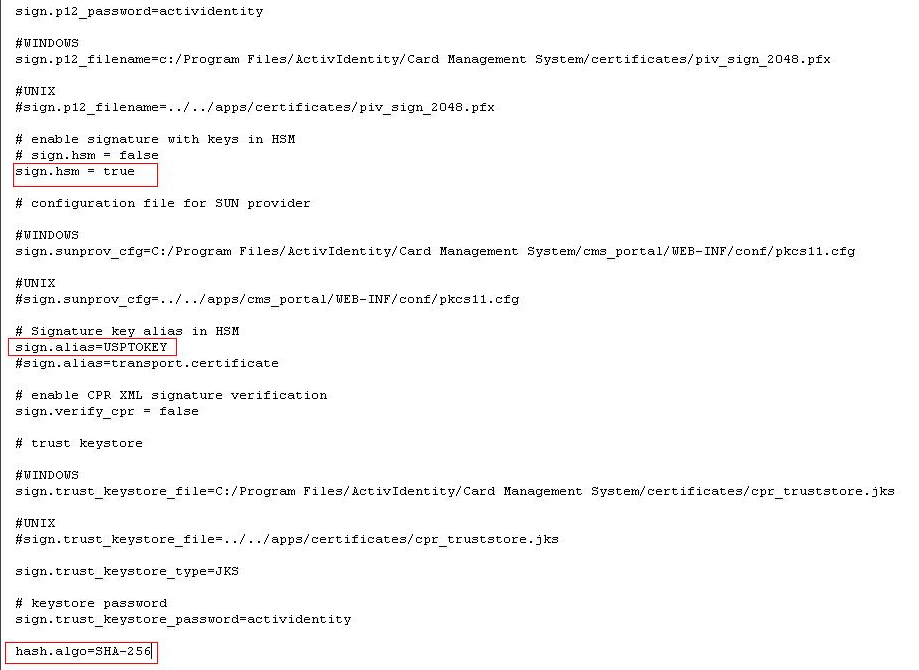
Make sure that the default PIV signer configuration remains present:
XML Schema Definition
-
Go to your existing PIV Toolkit delivery folder and back up the existing CPR with extension.xsd file typically located under …\Tools\PIV\SimuIDPRS\CPR with extensions.xsd.
-
Copy the following modification:
<xsd:element name="DigitalSignatoryIndex" minOccurs="0">
<xsd:simpleType>
<xsd:annotation>
<xsd:documentation> Digital Signatory Index Number</xsd:documentation>
</xsd:annotation>
<xsd:restriction base="xsd:int">
<xsd:minInclusive value="1"/>
<xsd:maxInclusive value="99"/>
</xsd:restriction>
</xsd:simpleType>
</xsd:element>… into the CPR with extensions.xsd file as shown below:

Sample CPR XML file
-
Go to your existing PIV Toolkit delivery folder and back up the existing sample CPR .xml file typically located under …\Tools\PIV\CPRSigning\CPR 2.1.8.sample.xml.
-
Make sure that the CPR 2.1.8.sample.xml file is pointing to the correct CPR with extension.xsd file.
-
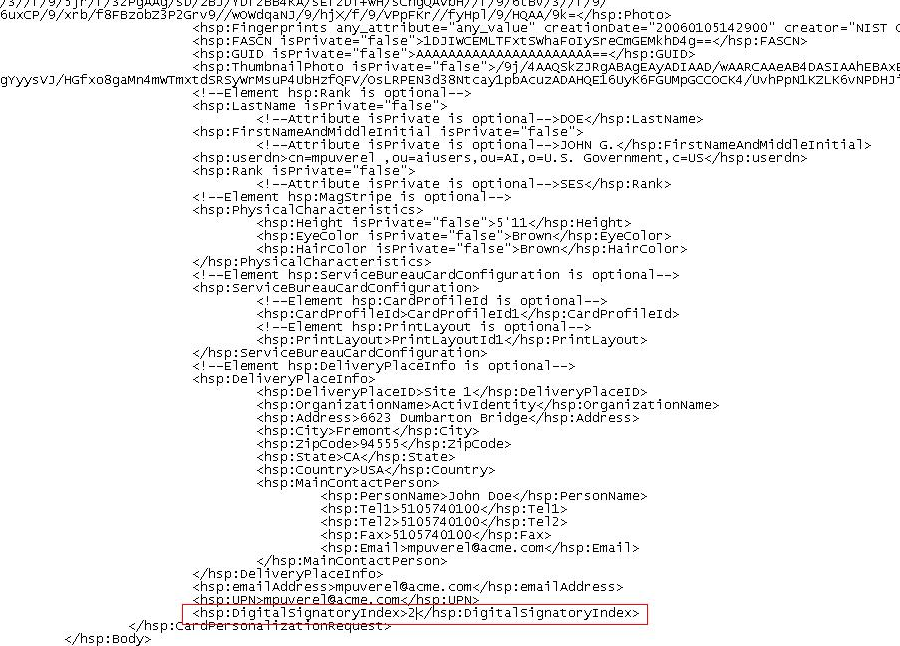
Add the new DigitalSignatoryIndex tag (with the correct value):
Copy<hsp:DigitalSignatoryIndex>2</hsp:DigitalSignatoryIndex>…into the CPR 2.1.8.sample.xml file as shown below: