Troubleshooting
The process for initializing a Thales (formerly Gemalto) SafeNet / Thales TCT (formerly SafeNet AT) HSM requires a number of operations. Even when following the steps presented in this documentation, you may still encounter issues with the initialization process that cause the HSM to work improperly with ActivID KMS or ActivID CMS.
This section describes how you can determine your HSM configuration, and how you can generate a log file that provides support information about your HSM configuration. If you want to communicate with HID Global or Thales SafeNet / Thales TCT Support services to resolve an issue, then current configuration and log file information is essential. Contact the support service for the company from whom you acquired your HSM.
Troubleshooting PCIe models
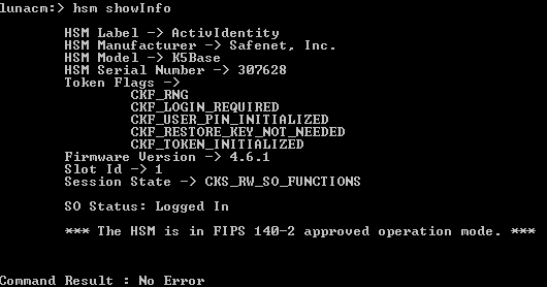
To display specific configuration information you may need, use the hsm showinfo command. This command displays the following types of information:
-
HSM label, manufacturer, model, and serial number
-
Token flags in use
-
Firmware version
-
Slot ID
-
Session state
-
SO status
To display a screen that displays such HSM-specific information, complete the following steps:
-
Go to the lunacm command prompt.
-
Enter the following command (which displays the following screen):
Copyhsm showinfo
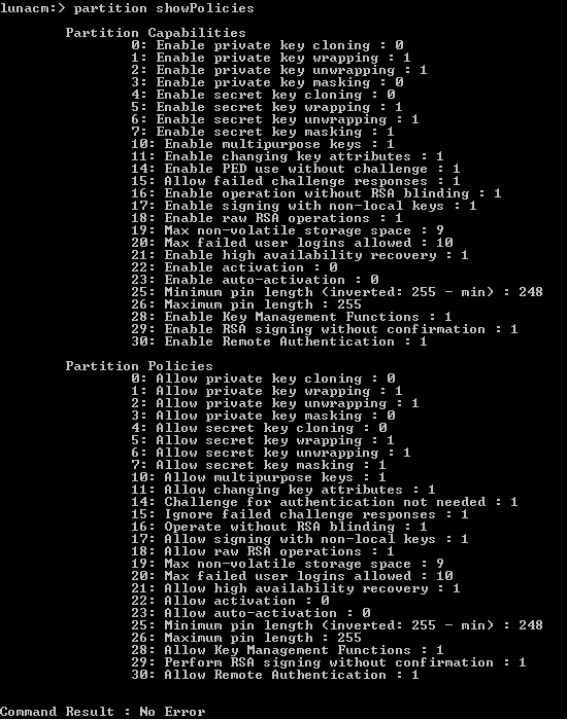
To display specific partition capability and policy information you may need, use the partition showpolicies command. For example, this command displays the following types of partition capability or policy information (refer to the screen example for a complete listing):
-
State of the following partition capabilities:
-
Private key cloning
-
Private key wrapping/unwrapping
-
Private key masking
-
Secret key cloning
-
Secret key wrapping/unwrapping
-
Secret key masking
-
Max non-volatile storage space
-
Max failed user logins allowed
-
-
State of the following partition policies:
-
Private key cloning
-
Private key wrapping/unwrapping
-
Private key masking
-
Secret key cloning
-
Secret key wrapping/unwrapping
-
Secret key masking
-
Multipurpose keys
-
Changing key attributes
-
To display a screen that displays such HSM-specific information, complete the following steps:
-
Go to the lunacm command prompt.
-
Enter the following command (which displays the following screen):
Copypartition showpolicies
To reset the HSM content in an HSM to its original manufacturing state, use the hsm factoryreset command and restart the HSM. However, you must be aware that resetting the HSM content to its original manufacturing state erases all of the existing content and it will be unrecoverable once reset.
To perform a reset of HSM content and display a screen with the corresponding prompts, complete the following steps:
-
Go to the lunacm command prompt.
-
Enter the following command (which displays the following screen):
Copyhsm factoryreset
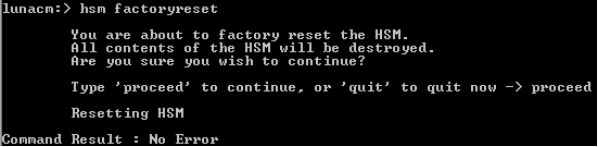
After completing the reset operation, the HSM is fully re-initialized (with its content having been cleared including its partitions). The HSM has been reset back to its original manufacturing state (for example, the SO PIN is again set to default). In addition, all of the previous keys have been irreversibly destroyed during this operation.
Troubleshooting Network HSMs
To gather the most current configuration information (appliance details, HSM details, partition details, and FIPS Federal Information Processing Standard 140-2 status), run the following command:
[ade_luna_sa] lunash:>hsm show
Appliance Details:
==================
Software Version: 4.3.2-21
HSM Details:
============
HSM Label: ade_luna_sa
Serial #: 950217
Firmware: 4.6.1
Hardware Model: Luna K5
Authentication Method: PED keys
HSM Admin login status: Logged In
HSM Admin login attempts left: 3 before HSM zeroization!
MofN activation status: M of N not used
Partitions created on HSM:
==========================
Partition: 902514001, Name: ade_partition
FIPS 140-2 Operation:
=====================
The HSM is NOT in FIPS 140-2 approved operation mode.
Command Result: 0 (Success)You can generate an HSM log file that contains the current support information using the ctp utility. The file can be shared with either the HID Global or Thales / Thales TCT Support staff. Use the following sample as a guide:
[cmslunasa] lunash:>hsm -su
'hsm supportInfo' successful.
Use 'ctp' from a client machine to get file named:
supportInfo.txt
Command Result: 0 (Success)





