Setting a Secure Connection with Oracle Server Database (Optional)
Enabling encrypted connection to the Oracle server increases the security of data transmitted across networks between the ActivID CMS Server and the Oracle Server instance.
Oracle supports:
-
two types of encryption: SSL Encryption and Advanced Security Option (ASO) network encryption.
-
a message integrity protocol.
Configuring Secure Socket Layer (SSL) Encryption
SSL communication is configured in Oracle by creating two wallets (client and server) that will store certificates, and by modifying the sqlnet.ora, tnsnames.ora and listener.ora configuration files.
The wallets can be created using the orapki utility, or using the Oracle Wallet Manager GUI tool (as indicated in this section).
-
Start the Oracle Wallet Manager.
-
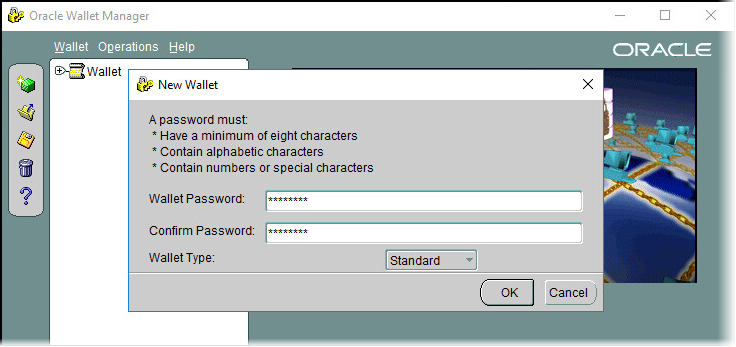
Create a new wallet with the Standard wallet type.
-
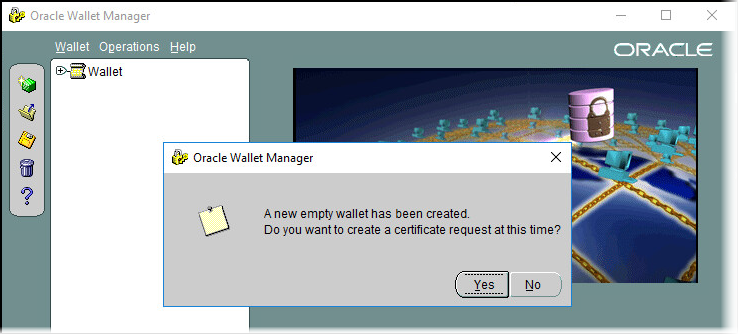
Click Yes to create a new certificate request.
-
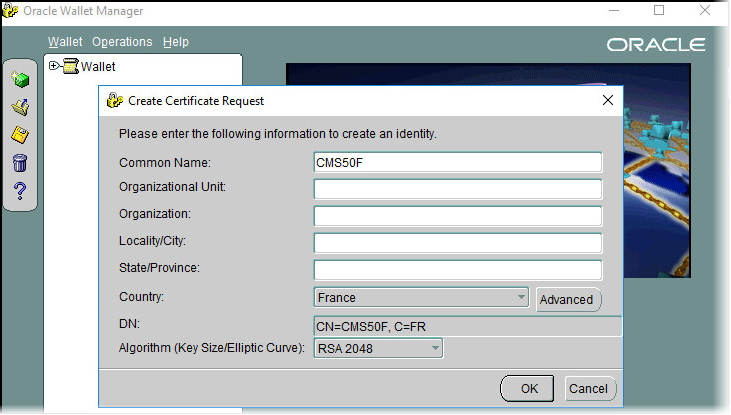
Set the Common Name to match the Fully Qualified Domain Name (FQDN).
-
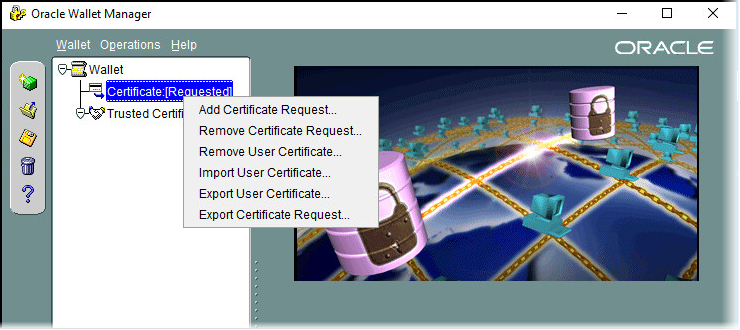
Right-click on the certificate and choose Export Certificate Request… then issue a Web Server certificate with this request.

-
Install the .p7b file generated, which contains the root certificate and the SQL server certificate. The certificate issued is:
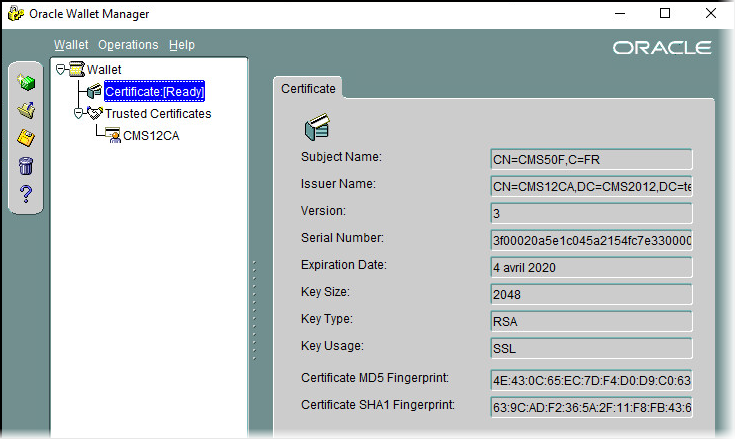
-
Select the Wallet.
-
Check the Auto Login option and save the wallet in the <Oracle Home>\ServerWallet folder.
-
Start the Net Manager.
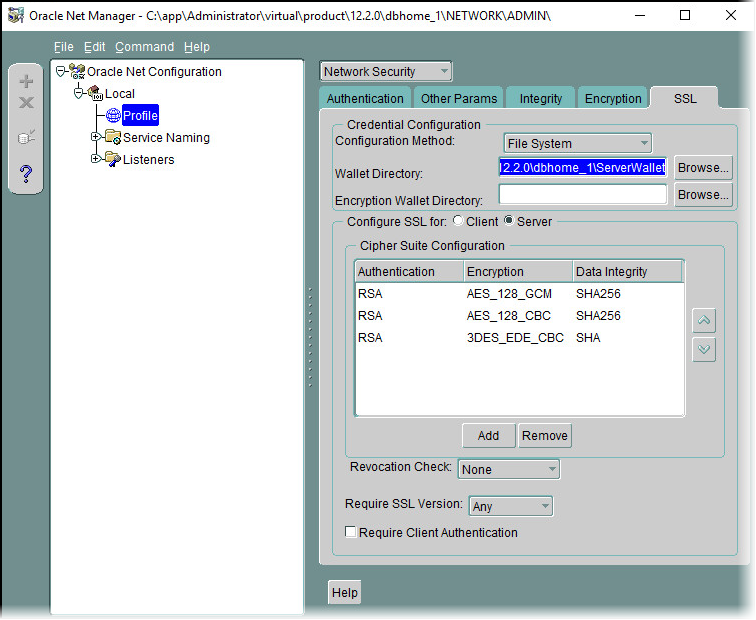
-
Configure the SSL Encryption to use the new wallet and save the network configuration.
The sqlnet.ora configuration is:
CopySQLNET.AUTHENTICATION_SERVICES= (BEQ, TCPS, NTS)
SSL_VERSION = 0
#TRACE_LEVEL_CLIENT = SUPPORT
SSL_CLIENT_AUTHENTICATION = FALSE
SQLNET.ENCRYPTION_TYPES_SERVER= (AES256, AES192, AES128, 3DES168)
WALLET_LOCATION =
(SOURCE =
(METHOD = FILE)
(METHOD_DATA =
(DIRECTORY = C:\app\Administrator\virtual\product\12.2.0\dbhome_1\ServerWallet)
)
)
SSL_CIPHER_SUITES= (SSL_RSA_WITH_AES_256_GCM_SHA384, SSL_RSA_WITH_AES_128_CBC_SHA256, SSL_RSA_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_AES_128_GCM_SHA256, SSL_RSA_WITH_3DES_EDE_CBC_SHA)
ADR_BASE = C:\app\Administrator\virtual\product\12.2.0\dbhome_1\log -
Update the tnsnames.ora file and add a new SID CMSDBSSL using TCPS protocol and the port 2484:
CopyCMSDB =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP)(HOST = CMS50F)(PORT = 1521))
)
(CONNECT_DATA =
(SERVICE_NAME = CMSDB)
)
)
CMSDBSSL =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCPS)(HOST = CMS50F)(PORT = 2484))
)
(CONNECT_DATA =
(SERVICE_NAME = CMSDB)
)
)
LISTENER_CMSDB =
(ADDRESS = (PROTOCOL = TCP)(HOST = CMS50F)(PORT = 1521))
(ADDRESS = (PROTOCOL = TCPS)(HOST = CMS50F)(PORT = 2484)) -
Update the listener.ora file and add the new wallet and the new listening port:
CopySID_LIST_LISTENER =
(SID_LIST =
(SID_DESC =
(GLOBAL_DBNAME = CMSDB)
(SID_NAME = CMSDB)
)
)
SSL_CLIENT_AUTHENTICATION = FALSE
WALLET_LOCATION =
(SOURCE =
(METHOD = FILE)
(METHOD_DATA =
(DIRECTORY = C:\app\Administrator\virtual\product\12.2.0\dbhome_1\ServerWallet)
)
)
LISTENER =
(DESCRIPTION_LIST =
(DESCRIPTION =
(ADDRESS = (PROTOCOL = TCP)(HOST = CMS50F)(PORT = 1521))
)
(DESCRIPTION =
(ADDRESS = (PROTOCOL = TCPS)(HOST = CMS50F)(PORT = 2484))
)
)
ADR_BASE_LISTENER = C:\app\Administrator\virtual\product\12.2.0\dbhome_1\log
#TRACE_LEVEL_LISTENER = ADMIN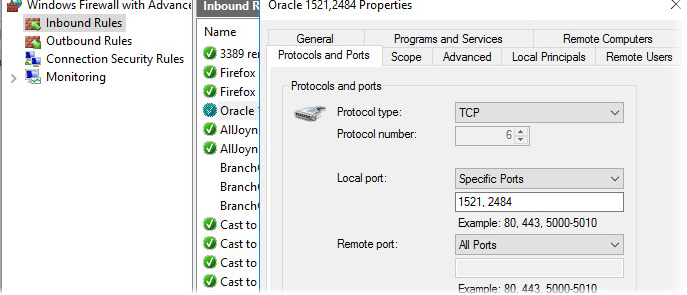
-
Update the Firewall and open the new port 2484.
-
Stop/Start the listener service.
On the ActivID CMS machine, execute the same steps performed for the database server but issue a SSL certificate for client authentication (use, for example, the "CMS Logon for Smartcard Admin" template on CMS CA).
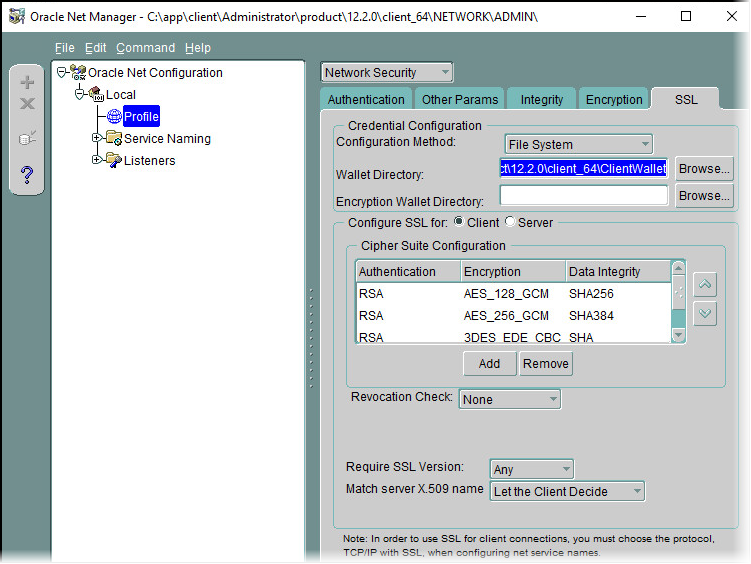
-
Save the Wallet in the <Oracle Home>\ClientWallet folder.
-
Start Net Manager and configure the SSL Configuration to use this wallet.
The sqlnet.ora on the client is:
CopySQLNET.AUTHENTICATION_SERVICES= (BEQ, TCPS, NTS)
SSL_VERSION = 0
#TRACE_LEVEL_CLIENT = ADMIN
#TRACE_LEVEL_SERVER = ADMIN
NAMES.DIRECTORY_PATH= (TNSNAMES, EZCONNECT)
SSL_CLIENT_AUTHENTICATION = FALSE
WALLET_LOCATION =
(SOURCE =
(METHOD = FILE)
(METHOD_DATA =
(DIRECTORY = C:\app\client\Administrator\product\12.2.0\client_64\ClientWallet)
)
)
SSL_CIPHER_SUITES= (SSL_RSA_WITH_AES_256_GCM_SHA384, SSL_RSA_WITH_AES_128_CBC_SHA256, SSL_RSA_WITH_AES_128_CBC_SHA, SSL_RSA_WITH_AES_128_GCM_SHA256, SSL_RSA_WITH_3DES_EDE_CBC_SHA)
ADR_BASE = C:\app\client\Administrator\product\12.2.0\client_64\log -
Update the tnsnames.ora file and add a new SID CMSDBSSL using TCPS protocol and the port 2484 (the host name is the database host name):
CMSDB =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCP)(HOST = cms50F)(PORT = 1521))
)
(CONNECT_DATA =
(SERVICE_NAME = cmsdb)
)
)
CMSDBSSL =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS = (PROTOCOL = TCPS)(HOST = cms50F)(PORT = 2484))
)
(CONNECT_DATA =
(SERVICE_NAME = cmsdb)
)
)Optional: Configuring Oracle Advanced Security Network Encryption (ASO Native Encryption)
Encryption and integrity parameters are defined by modifying an sqlnet.ora file on both the clients and the servers on the network.
The default value for each of the parameters is ACCEPTED.
-
To enable the encryption, start the Net Manager on the Client.
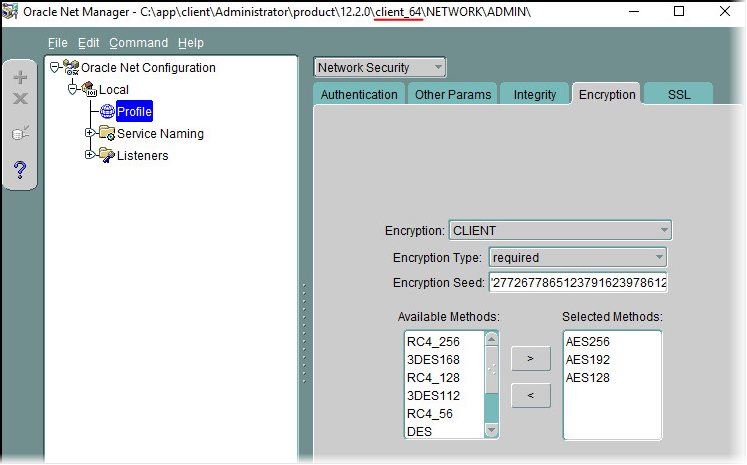
-
Select Profile -> Network Security -> Encryption.
-
Require encryption from the client; set the encryption methods; and, optionally, set a seed that is 10-70 characters in length.
Optional: Configuring Secure Data Integrity (Checksum)
The default value for each of the parameters is ACCEPTED.
-
To enable the encryption, start the Net Manager on the Client.
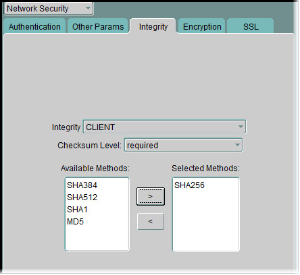
-
Select the Profile -> Network Security -> Integrity and set the configuration as shown above.
Checking the Database Configuration
-
From the client, check if the database connection is OK:
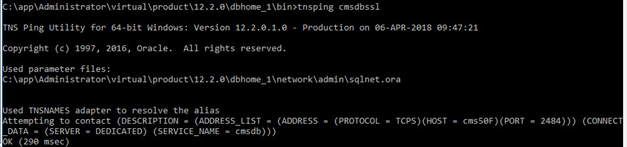
-
Check if the connection is TCPS:
-
Connect to the database using encrypted connection:
Copysqlplus system@cmsdbssl
-
Installing ActivID CMS Server Using a Secure Database Connection
-
During the ActivID CMS set-up, select the database service with a secure connection (in this example, cmsdbSSL):
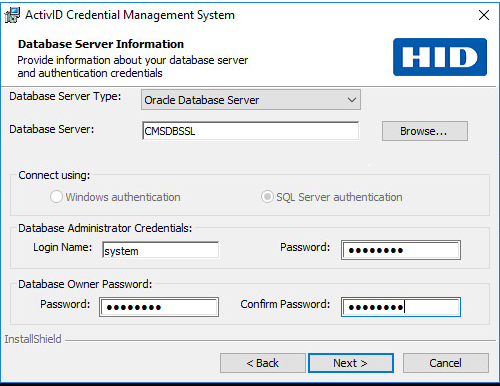
-
After ActivID CMS installation, check and update the Oracle URL in the %PROGRAMDATA%\HID Global\Credential Management System\Shared Files\database.properties.
-
Edit the file cms_installation_dir\wildfly\bin\standalone.conf.bat (for example, using Notepad).
-
Add the following lines at the very end of that file:
Copyset "JAVA_HOME=%JAVA_HOME% -Doracle.net.authentication_services=TCPS"
set "JAVA_HOME=%JAVA_HOME% -Doracle.net.ssl_version=1.2"
set "JAVA_HOME=%JAVA_HOME% -Djavax.net.ssl.trustStore=%PROGRAMDATA%\HID Global\Credential Management System\Shared Files\Certificates\CMSStore.jks"
set "JAVA_HOME=%JAVA_HOME% -Djavax.net.ssl.trustStoreType=JKS"
set "JAVA_HOME=%JAVA_HOME% -Djavax.net.ssl.trustStorePassword=<password>"
-
In this configuration:
-
The CMSStore.jks file is a Java keystore containing the Oracle database public certificate or the root of the CA that issued this certificate. It is advised to put that file in the %PROGRAMDATA%\HID Global\Credential Management System\Shared Files\Certificates directory.
-
<password> is the keystore password.
-
-
Start the ActivID CMS server.





