Configure CIV-Compliant Face-to-Face Device Policies
This section describes how to configure an ActivID CMS Face-to-Face device policy to issue CIV-compliant smart cards for different certificate authorities.
This section summarizes the actions that must be taken to issue a test CIV-compliant smart card. To test CIV Commercial Identity Verification configuration, you must create a Face-to-Face CIV Device policy for one-step issuance. For details, review Face-to-Face (F2F) Device Policy Configuration. To summarize what you will do:
-
Add Device policy.
Configure each application in the device policy. The following section provides step-by-step instructions to complete the summarized previous summary of steps. For the application configuration that is CA-specific, please refer to subsequent sections that describe your CA.
Before you begin, make sure that:
-
A CA The Certificate Authority (CA) issues and manages security credentials and public keys for message encryption in a networks environment. account configured for CIV workflow is available.
-
Certificate templates are configured for the CIV PKI applications that will be defined in the device policy.
-
-
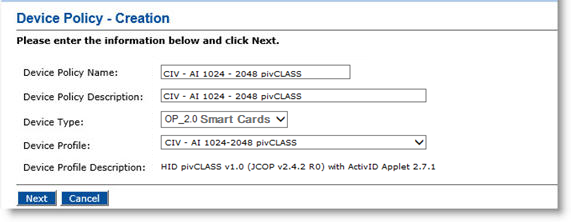
Log on to ActivID CMS, select the Configuration tab, click Policies, and then click Add Device Policy.
-
Populate the fields as displayed for CIV cards.
-
Device Policy Name—Enter a name for your device policy.
-
Device Policy Description—Enter a description of your device policy.
-
Device Type—From the drop-down list, select OP_2.0 Smart Cards.
-
Device Profile—From the drop-down list, select the device profile to use depending on the type of device you are using.
-
Click Next. The Device Policy Configuration page is displayed.
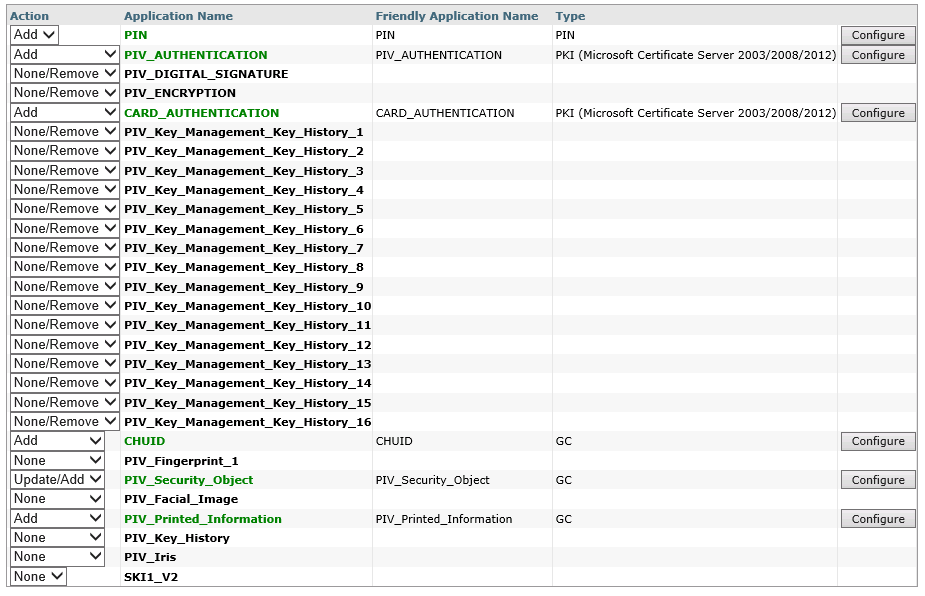
The following applications are mandatory on CIV cards to provide compatibility with a large number of PIV-compliant software and hardware applications:
-
PIN – The personal identification number (PIN) that is known only to the owner of the card
-
PIV_AUTHENTICATION – Contains a PKI certificate and key pair used to authenticate the user.
-
CHUID – Stores the Cardholder Unique Identifier. Generated automatically by ActivID CMS.
-
PIV_Security_Object – Generated automatically by ActivID CMS.
-
PIV_Printed_Information – Generated automatically by ActivID CMS.
The following applications are optional on CIV cards:
-
CARD_AUTHENTICATION – This key and certificate supports Card Authentication for device to device authentication purposes (physical access).
-
PIV_DIGITAL_SIGNATURE – This key and certificate supports the use of digital signatures for the purpose of document signing.
-
PIV_ENCRYPTION – This key and certificate supports the use of encryption for the purpose of confidentiality. This key pair is escrowed by the issuer for key recovery purposes.
-
PIV_Key_Management_History_1-20 – These containers store keys and certificates that have been retired. When at least one of these containers is configured, the PIV_Key_History container becomes mandatory.
-
PIV_Key_History – This container stores the number of retired keys that are stored on the card. This application is required when at least one of the PIV_Key_Management_History containers is configured.
-
PIV Fingerprint 1 – This container stores the biometric template of the user’s fingerprint.
-
PIV_Facial_Image – This container stores the biometric template of the user’s facial image.
-
PIV_Iris – This container stores the biometric template of the user’s iris image.
-
-
Perform the rest of the procedure as described in Configure PIV-Compliant Face-to-Face Device Policies.
-
Click Set to return to the main Device Policy Configuration page.
-
Continue the procedure in the corresponding CA section.
Using Microsoft Certificate Authority
-
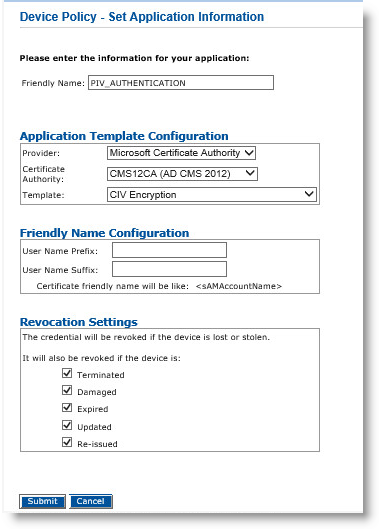
Next to the PIV_AUTHENTICATION object, click Configure.
-
On the Set Application Information page, make sure that the correct Certificate Authority and Template are displayed, and then click Submit.
-
Perform the rest of the procedure as described in Using Microsoft Certificate Authority.





