Issue PIV-I Compliant Cards
To support PIV Personal Identity Verification (technical standard of "HSPD-12") for Non-Federal Issuers (also known as PIV-Interoperable or PIV-I standard), ActivID CMS enables the issuance of cards in either a PIV-compliant mode or a PIV-I-compliant mode.
The following steps are a summary of the actions you must perform when issuing PIV-I cards.
-
Configure the PIV certificate templates in your CA The Certificate Authority (CA) issues and manages security credentials and public keys for message encryption in a networks environment. with the proper Subject and Policy OIDs for PKI certificates.
-
Make sure the mandatory applications have been added and configured in the device policy you are using, in accordance with the PIV-I standard
-
Set CPR The Card Production Request (CPR) contains a list of user-specific attributes that will be stored, fully or partially, in the PIV Metadata database, and will be loaded on the PIV card during the issuance. attributes to be PIV-compliant
Configuring PIV-I Certificate Templates
You must configure the CA The Certificate Authority (CA) issues and manages security credentials and public keys for message encryption in a networks environment. you are using to use the right certificate extensions for your certificate templates. This includes setting the PIV-I policy OIDs. You can configure the certificate templates as you would for a PIV Personal Identity Verification (technical standard of "HSPD-12") card, with the exception to the attributes provided in the following table. The attributes must be modified as described in the table.
For further information on configuring the PIV and PIV-I certificate templates, refer to Configuring Microsoft Certificate Authority for PIV and CIV Deployments.
Never set NACI on any PIV certificate in PIV-I mode, in particular on PIV_AUTHENTICATION & CARD_AUTHENTICATION (contrary to what is done in PIV mode).
Enforcing this rule is done either by the CA itself (in its configuration) or by ActivID CMS (which does not pass NACI information to the credential provider when issuing in PIV-I mode, that is, it ignores the NACIIndicator attribute retrieved from the CPR).
|
PKI Slot |
Card_Authentication |
Authentication |
Digital_Signature |
Encryption |
|---|---|---|---|---|
|
SubjectName |
serialNumber=UUID, ou=Affiliated Organization Name,{Base DN} serialNumber=UUID, ou=Unaffiliated, ou=Entity CA’s Name,{Base DN} |
cn=Subscriber's full name, ou=Affiliated Organization Name,{Base DN} cn=Subscriber's full name, ou=Unaffiliated, ou=Entity CA’s Name,{Base DN} |
cn=Subscriber's full name, ou=Affiliated Organization Name,{Base DN} cn=Subscriber's full name, ou=Unaffiliated, ou=Entity CA’s Name,{Base DN} |
cn=Subscriber's full name, ou=Affiliated Organization Name,{Base DN} cn=Subscriber's full name, ou=Unaffiliated, ou=Entity CA’s Name,{Base DN} |
|
SubjectAltName |
URI = UUID
|
URI = UUID OtherName = UPN |
Rfc822Name = user email |
Rfc822Name = user email |
|
keyUsage |
Signature Critical |
Signature Critical |
Signature and non-repudiation Critical |
Key encipherment Critical |
|
Enhanced Key Usage |
2.16.840.1.101.3.6.8 id-PIV-cardAuth Critical |
1.3.6.1.4.1.311.20.2.2 1.3.6.1.5.5.7.3.2 TLS Client authentication 1.3.6.1.5.2.3.4 id-pkinit-KPClientAuth |
1.3.6.1.5.5.7.3.4 1.3.6.1.4.1.311.10.3.12 MSFT Document Signing 1.2.840.113583.1.1.5 Adobe Certified Document Signing |
|
|
Certificate Policy |
2.16.840.1.101.3.2.1.3.19 id-fpki-certpcy-pivi-cardAuth |
2.16.840.1.101.3.2.1.3.18 id-fpki-certpcy-pivi-hardware |
2.16.840.1.101.3.2.1.3.18 id-fpki-certpcy-pivi-hardware |
2.16.840.1.101.3.2.1.3.18 id-fpki-certpcy-pivi-hardware |
|
Authority Info access |
1.3.6.1.5.5.7.48.1 1.3.6.1.5.5.7.48.2 |
1.3.6.1.5.5.7.48.1 1.3.6.1.5.5.7.48.2 |
1.3.6.1.5.5.7.48.1 1.3.6.1.5.5.7.48.2 |
1.3.6.1.5.5.7.48.1 1.3.6.1.5.5.7.48.2 |
|
CRL distribution point |
LDAP and HTTP URLs |
LDAP and HTTP URLs |
LDAP and HTTP URLs |
LDAP and HTTP URLs |
Issuer should NOT use the PIV-I policy OIDs above directly, but use its own OIDs that can be mapped later to the PIV-I OIDs via cross certification.
Configuring Device Policies in ActivID CMS
To enforce the PIV-I mode in the device policies, you must add and configure the following applications:
-
PIV_AUTHENTICATION – Mandatory application. Contains a PKI certificate and key pair used to authenticate the user.
-
CARD_AUTHENTICATION – Mandatory application. This key and certificate (if the key is an asymmetric key) supports PIV Personal Identity Verification (technical standard of "HSPD-12") Card Authentication for device-to-device authentication purposes (physical access). When the Card Authentication Key is a symmetric key, the CHUID Card Holder Unique Identifier authentication key map must be present and must specify the cryptographic algorithm and key storage location.
-
PIV_DIGITAL_SIGNATURE – Optional application. This key and certificate support the use of digital signatures for the purpose of document signing.
-
PIV_ENCRYPTION – Optional application. This key and certificate support the use of encryption for the purpose of confidentiality. This key pair is escrowed by the issuer for key recovery purposes.
-
CHUID – Mandatory application. This container stores the Cardholder Unique Identifier.
-
PIN – Mandatory application. The personal identification number (PIN) that is known only to the owner of the card.
-
PIV Security Object – Mandatory application. This container stores data compliant with the matching readable travel document from the International Civil Aviation Organization (ICAO). An update of this application is required if at least one PIV_Key_Management_History application is added and configured.
-
PIV_Facial_Image – Mandatory application. This container stores the biometric template of the user’s facial image.
Subject DN Processing
When using Microsoft credential provider, subject DN processing is conditioned by the Subject Name setting of the CA certificate template being used by the credential profile.
-
Certificate Subject Names
The four PIV-I certificates are configured to supply the Subject Name in the request – that is, subject DN is built from the credential profile.
The format of the Subject Name must be set in the ActivID CMS PKI application parameters within the device policy.
The table below lists the expected subject name format for each PIV-I certificate:
PIV-I Certificate Subject Name Format Certificate Type
PIV-I Subject Name
Authentication
cn={Subscriber's full name},ou={Affiliated Organization Name},{Base DN}
Card Authentication
serialNumber={UUID},ou={Affiliated Organization Name},{Base DN}
Digital signature
{User DN}
Encryption (KMK)
{User DN}
The following mapping is proposed between subject name components and PIV-I attributes:
-
Subscriber's full name = piv:FullName
-
UUID = piv:GUIDUUID
-
Affiliated Organization Name = piv:EmployeeAffiliation
-
The Base DN should be hard coded to the base DN of the directory.
For example, the Subject DN parameter of the PIV_AUTHENTICATION application could be:
Copycn=%ATTR.piv:FullName%,ou=%ATTR.piv:EmployeeAffiliation%, dc=mydomain, dc=com -
-
Certificate Subject Alternative Names
When the related Microsoft CA certificate template enables you to supply the subject in the request, the Subject Alternative Name (SAN) components are configurable in the ActivID CMS PKI application configuration.
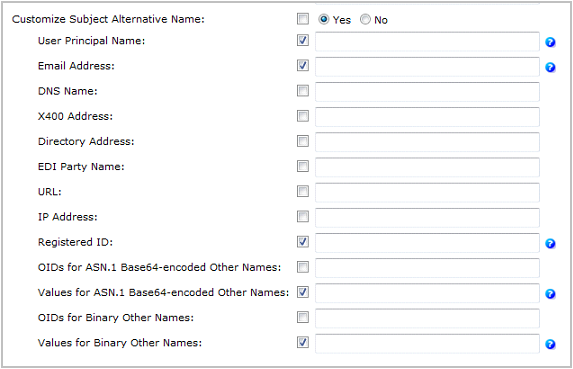
The table below lists the expected subject alternative name format for each PIV-I certificate:
PIV-I Certificate Subject Alternative Name Format Certificate Type
PIV-I Subject Alternative Name Components
Authentication
User Principal Name = %ATTR.piv:UPN%
URL = urn:uuid:%ATTR.piv:GUIDUUID%
Card Authentication
URL = urn:uuid:%ATTR.piv:GUIDUUID%
Digital signature
Email Address = %ATTR.piv:emailAddress%
Encryption (KMK)
Email Address = %ATTR.piv:emailAddress%
The following mapping is proposed between subject alternative name components and PIV-I attributes:
-
Email = piv:emailAddress
-
UPN = piv:UPN
-
UUID = piv:GUIDUUID
Note: All listed components must be set as dynamic. Non-listed components must have an empty value to enforce PIV-I compliance. -
Before you begin, make sure that:
-
A CA account configured for PIV-I workflow is available.
-
Four certificate templates are configured for the four PIV-I PKI applications that will be defined in the device policy (refer to Configuring Microsoft Certificate Authority for PIV and CIV Deployments).
-
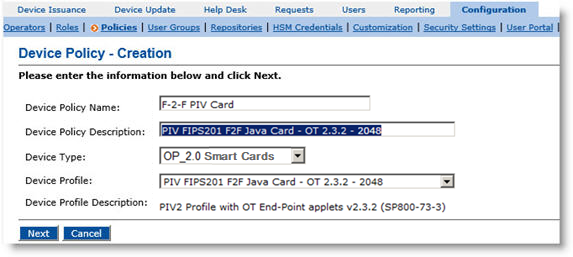
Log on to ActivID CMS, select the Configuration tab, click Policies, and then click Add Device Policy.
-
Populate the fields as displayed for OCS PIV Endpoint cards.
-
Device Policy Name—Enter a name for your device policy.
-
Device Policy Description—Enter a description of your device policy.
-
Device Type—From the drop-down list, select OP_2.0 Smart Cards.
-
Device Profile—From the drop-down list, select the device profile to use depending on the type of device you are using.
Note: You must select a device profile that starts with PIV FIPS201 F2F for one-step issuance.
-
Click Next. The Device Policy Configuration page is displayed.
-
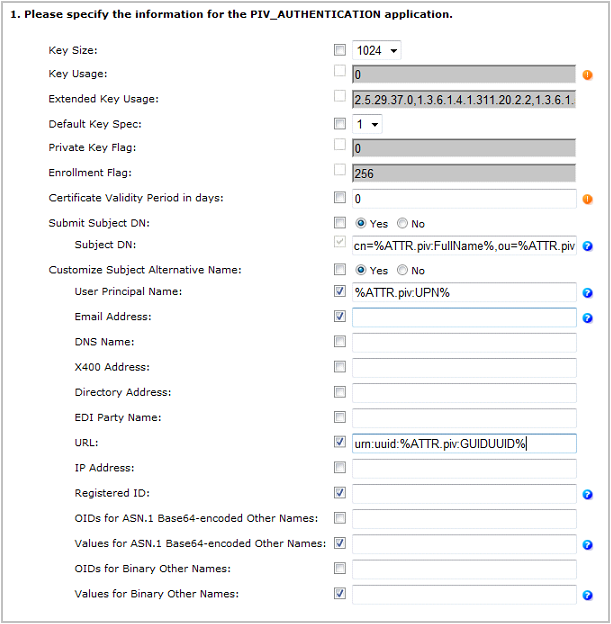
Next to the PIV_AUTHENTICATION application, click Configure.
-
On the Set Application Information page, make sure that the correct Certificate Authority and Template are displayed, and then click Submit.
-
Set the application information as follows:
-
Key Size—Select the key size according to the device profile you use.
-
Default Key Spec—Select 1.
-
Certificate Validity Period in days—Define the certificate validity period according to your organization’s security policy.
-
Set Submit Subject DN to Yes.
-
For the Subject DN, enter:
Copycn=%ATTR.piv:FullName%,ou=%ATTR.piv:EmployeeAffiliation%, {Base DN}Where:
-
Subscriber's full name = piv:FullName
-
Affiliated Organization Name = piv:EmployeeAffiliation
-
The Base DN should be hard coded to the base DN of the directory.
-
-
Set Customize Subject Name Alternative to Yes.
-
Select the User Principal Name component, and enter the value %ATTR.piv:UPN%.
-
Select the URL component, and enter the value urn:uuid:%ATTR.piv:GUIDUUID%.
-
Click Set to return to the main Device Policy Configuration page.
-
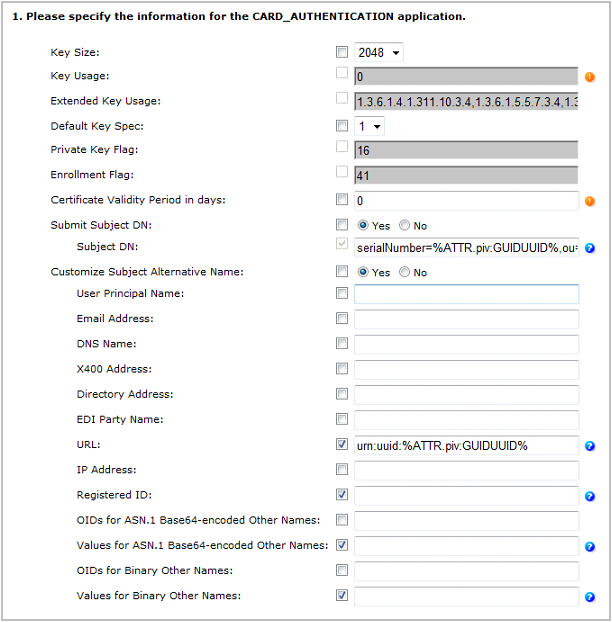
Next to CARD_AUTHENTICATION, select Add, and then click Configure.
-
On the Set Application Information page, make sure that the correct Certificate Authority and Template are displayed, and then click Submit.
-
Set the application information as follows:
-
Key Size—Select the key size according to the device profile you use.
-
Default Key Spec—Select 1.
-
Certificate Validity Period in days—Define the certificate validity period according to your organization’s security policy.
-
Set Submit Subject DN to Yes.
-
For the Subject DN, enter:
CopyserialNumber=%ATTR.piv:GUIDUUID%, ou=%ATTR.piv:EmployeeAffiliation%, {Base DN}Where:
-
UUID = piv:GUIDUUID
-
Affiliated Organization Name = piv:EmployeeAffiliation
-
The Base DN should be hard coded to the base DN of the directory.
-
-
Set Customize Subject Name Alternative to Yes.
-
Select the URL component and enter the value urn:uuid:%ATTR.piv:GUIDUUID%.
-
Click Set to return to the main Device Policy Configuration page.
-
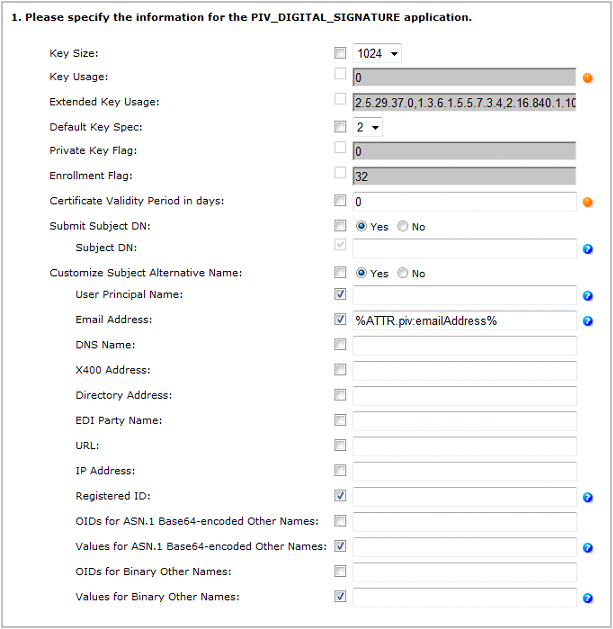
Next to PIV_DIGITAL_SIGNATURE, select Add, and then click Configure.
-
On the Set Application Information page, make sure that the correct Certificate Authority and Template are displayed, and then click Submit.
-
Set the application information as follows:
-
Key Size—Select the key size according to the device profile you use.
-
Default Key Spec—Select 1.
-
Certificate Validity Period in days—Define the certificate validity period according to your organization’s security policy.
-
Set Submit Subject DN to Yes, and leave the Subject DN field empty as the User DN will be used.
-
Set Customize Subject Name Alternative to Yes.
-
Select the Email Address component and enter the value %ATTR.piv:emailAddress%.
-
Click Set to return to the main Device Policy Configuration page.
-
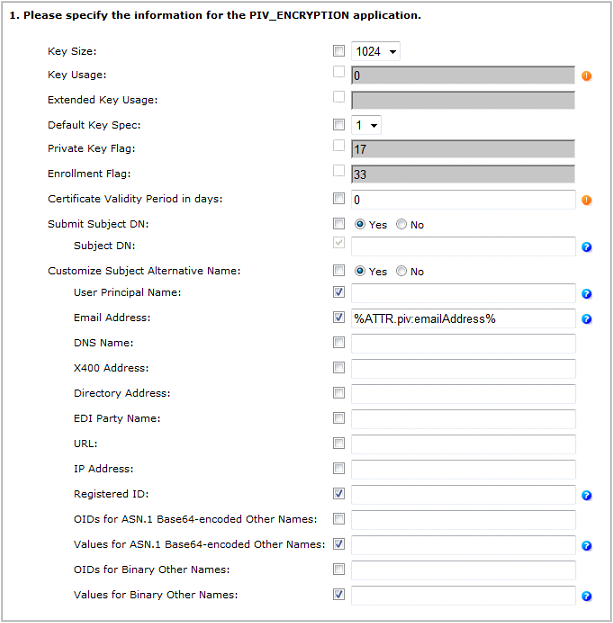
Next to PIV_ENCRYPTION, select Add, and then click Configure.
-
On the Set Application Information page, make sure that the correct Certificate Authority and Template are displayed, and then click Submit.
-
Set the application information as follows:
-
Key Size—Select the key size according to the device profile you use.
-
Default Key Spec—Select 1.
-
Certificate Validity Period in days—Define the certificate validity period according to your organization’s security policy.
-
Set Submit Subject DN to Yes, and leave the Subject DN field empty as the User DN will be used.
-
Set Customize Subject Name Alternative to Yes.
-
Select the Email Address component, and enter the value %ATTR.piv:emailAddress%.
-
Click Set to return to the main Device Policy Configuration page.
Configuring the CPR
In compliance with SP 800-73-3, it is strongly recommended that you use the CPR The Card Production Request (CPR) contains a list of user-specific attributes that will be stored, fully or partially, in the PIV Metadata database, and will be loaded on the PIV card during the issuance. 2.1.8 schema to issue PIV Personal Identity Verification (technical standard of "HSPD-12") cards. ActivID CMS is configured by default using this standard. This guide assumes that your system will be configured to comply with this new revision. However, ActivID CMS will continue to issue cards with a system configured using previous CPRs (for example, those that are compliant with SP 800-73-1) until the CPR schema has been upgraded.
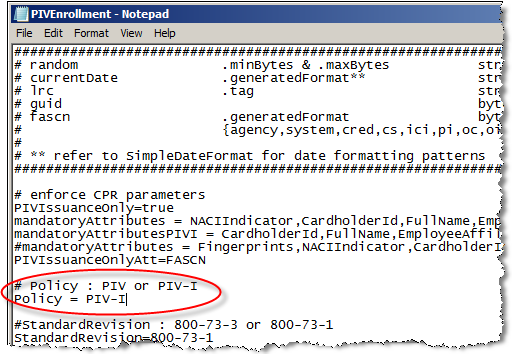
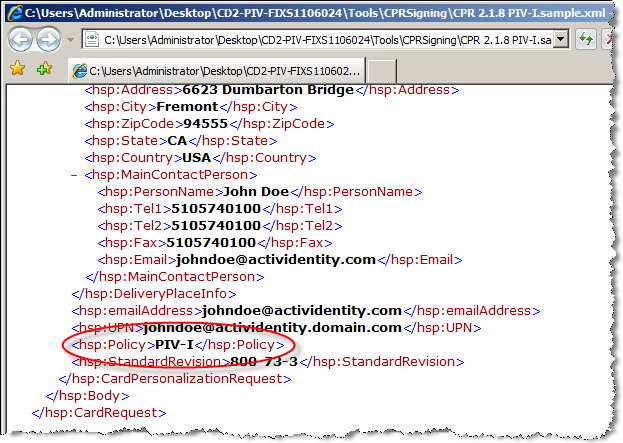
To issue PIV-Compliant cards, you must set the attribute PIV Policy to PIV-I.
-
This can be configured in the CPR, with the attribute <hsp:policy> (see the corresponding figure below).
OR
-
When the CPR Policy entry does not exist, it can be configured in the ActivID CMS PIVEnrollment.properties configuration file with the attribute policy = (see the corresponding figure below).
The attribute in the CPR takes priority over the PIVEnrollment.properties. The following table lists the resulting PIV compliance mode with difference policies defined in the CPR and PIV Plug-in.
|
PIV Policy in CPR |
PIV Policy in PIVEnrollment.properties |
Resulting PIV Policy |
|---|---|---|
|
<absent> |
<absent> |
PIV |
|
PIV |
<any> |
PIV |
|
PIV-I |
<any> |
PIV-I |
|
<absent> |
PIV |
PIV |
|
<absent> |
PIV-I |
PIV-I |
When in a PIV-I-compliant mode:
-
GUID is used in place of FASC-N for subject alternative names and biometric objects signature.
-
FASC-N will start with 9999 9999 999999 (Agency Code + System Code + Credential number).
PIV Policy Attribute in the CPR
PIV Policy Attribute in PIVEnrollment.properties