Network Configuration
To implement a secure ActivID CMS system, it is important that you understand the communication dependencies between ActivID CMS and other components within the overall network system. The following figure illustrates the recommended ActivID CMS network deployment and the typical communication flows.
Recommended ActivID CMS Network Deployment
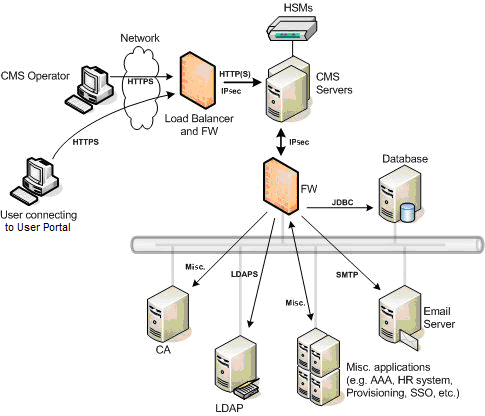
ActivID CMS network deployment can mean a configuration that requires connectivity with a variety of external components. The requirement for the ActivID CMS systems to be connected to and accessed by network devices and clients also potentially makes them vulnerable to various cyber-attacks to the hardware and software required to run the ActivID CMS server and services.
The best way to protect the ActivID CMS system(s) and the related dependent entities from network-based cyber-attacks requires a layered approach that is based upon the Open System Interconnection (OSI) model, which consists of 7 layers. The layers relevant to the network communication are Layer 2 to Layer 4, specifically the Data Link, Network, and Transport layers. The following figure illustrates the 7 layers of the OSI model.
OSI Model Layers

A detailed explanation of the OSI model is beyond the scope of this documentation and the illustration of the OSI model is included for reference purposes only. HID Global assumes that the reader possesses an in-depth knowledge of the 7 layers or has access to other reference sources for this material.
Recommendations
The following are network configuration-related recommendations:
-
To prevent Layer 2 attacks, devices that are located on the same IP network should be unable to communicate with each other using the Data Link Layer. A separate network should be used for the ActivID CMS server and this network should be separated both physically and logically from any other device.
-
In some network environments, the previously suggested level of separation is neither practical nor feasible. In such cases, the ActivID CMS server should be protected at the Data Link Layer by using private Virtual Local Area Networks (VLANs). By using private VLANs (PVLANs) or by using a separate physical network forces all communications to be routed, and thus pass through a Layer 3 device (such as a router, firewall, or a Layer 3 switch).
-
Every device on the network infrastructure should be configured with Access Control Lists (ACLs), including switches, firewalls, and routers. ACLs can be customized to adapt to the environment in which they are used, and should be implemented using the minimum privileges required to perform the desired tasks. The ports required for ActivID CMS communication are listed in the following table.
-
ActivID CMS servers should be deployed with two separate network interfaces—one interface which is made public for ActivID CMS operators and users—and another interface used for connections with back-end components and potential back-up systems.
-
IDS systems should be deployed on both network segments that are connected to the ActivID CMS servers and host-based Intrusion Protection Systems (IPS) should be installed on the ActivID CMS server.
To assist with the network configuration, the following table outlines the network communications that are required to and from the ActivID CMS systems for the following configurations.
|
Target |
Protocol |
Direction |
Type |
Port |
Encryption |
Authentication |
|---|---|---|---|---|---|---|
|
Operator-based Systems |
HTTPS |
Inbound |
TCP |
Configurable |
TLS |
Mutual PKI |
|
Client-based Systems |
HTTPS |
Inbound |
TCP |
Configurable |
TLS |
Server-based PKI and one additional form factor |
|
Client-based Smartphones |
HTTPS |
Inbound |
TCP |
Configurable |
TLS |
Server-based PKI and Unique server-provided token |
|
Microsoft CA |
RPC (remote procedure call) |
Outbound |
TCP |
135 (above 1024, ports are randomly-allocated) |
SMB signing and NTLM encryption |
Windows authentication |
|
Symantec® / VeriSign® CA |
HTTPS |
Outbound |
TCP |
Configurable |
TLS |
Mutual PKI |
|
Verizon® / UniCERT™ CA |
HTTPS |
Outbound |
TCP |
Configurable |
TLS |
Mutual PKI |
|
OpenTrust®/ Keynectis CA |
HTTPS |
Outbound |
TCP |
Configurable |
TLS |
Mutual PKI |
|
Entrust® CA EASM |
XAP |
Outbound |
TCP |
Configurable/443 |
TLS |
Mutual PKI |
|
Directory |
LDAPS |
Outbound |
TCP |
636 |
TLS |
Server-based PKI and LDAP Lightweight Directory Access Protocol PWD |
|
AAA Server |
HTTPS |
Outbound |
TCP |
Configurable |
TLS |
Server-based PKI and AAA PWD |
|
Microsoft SQL Database |
JDBC |
Outbound |
TCP |
1433 |
JDBC |
JDBC PWD |
|
Oracle® SQL Database |
SQLNET |
Outbound |
TCP |
1521 |
SQLNET |
SQLNET PWD |
|
Email Server |
SMTP |
Outbound |
TCP |
25 |
None |
None |
|
Peered ActivID CMS Servers |
HTTPS |
Bidirectional |
TCP |
Configurable |
TLS |
Mutual PKI |
|
CRL Location(s) |
HTTP |
Outbound |
TCP |
80 |
None |
None |
|
AIA Location(s) |
HTTP |
Outbound |
TCP |
80 |
None |
None |





