Setting Up Symantec PKI Repository in ActivID CMS
You can add the Symantec MPIK 8.0 Credential Provider CA, and then create and configure the device profile.
Configuring the Certificate Authority
This section describes how to configure the ActivID CMS Operator Portal for Symantec PKI.
For detailed instructions on creating directories and CAs in the ActivID CMS, refer to Procedures for Managing Directories and Procedures for Configuring Connections to Certificate Authorities.
-
Log on to the ActivID CMS Operator Portal with an ActivID CMS Administrator certificate.
-
Go to the Configuration tab, and then click Repositories.
-
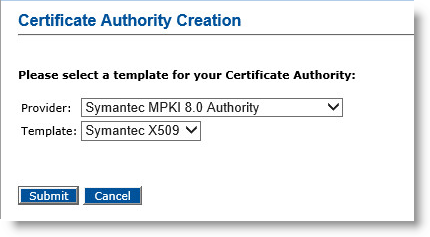
Click Add Certificate Authority.
-
From the drop-down list, select Symantec MPKI 8.0 Authority.
-
For Template, keep the default value (Symantec X509).
-
Click Submit.
-
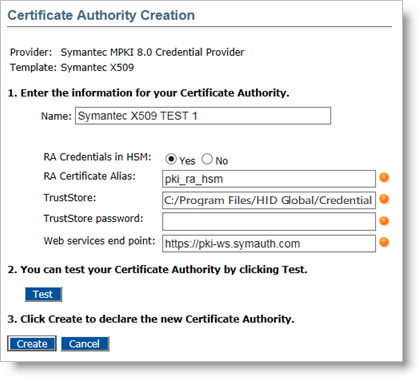
Enter a Name for the Certificate Authority.
-
Specify if the RA A Registration Authority (RA) is an authority in a network that verifies user requests for a digital certificate and instructs the CA to issue it. An RA is part of a PKI, a networked system that enables companies and users to exchange information safely and securely. Credentials are stored in an HSM (instead of in a Keystore file).
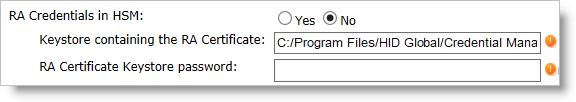
If you select No, the additional Keystore fields appear:
-
Depending on your deployment (HSM or Keystore), enter the required values:
Field
Description
Keystore containing the RA Certificate
Path of the KeyStore containing the RA certificates.
For example, C:/Program Files/HID Global/Credential Management System/certificates/racert.jks (only for software Keystore).
RA Certificate Keystore password
Password for RA certificate KeyStore (only for software Keystore).
RA Certificate Alias
-
With a software KeyStore, this field is optional – if you have only one key in your KeyStore, you can leave this field blank.
-
With an HSM: this field is mandatory – it must equal the RA Key Alias that was configured when setting the RA certificate in the HSM.
TrustStore
Path of the TrustStore containing the trusted root CA.
The TrustStore contains 5 certificates.
For example, C:/Program Files/HID Global/Credential Management System/certificates/cacerts.jks.
TrustStore password
Password for TrustStore.
Web services end point
Web services end point URL.
For example, https://ptnr-pki-ws.bbtest.net.
-
-
Click Test to verify the CA configuration.
-
Click Create to apply your changes.
Creating the Device Policy
This section explains how to create a device policy that loads Symantec certificates on to the user’s smart card.
For more information about creating a device policy, refer to Creating a Device Policy.
To create a device policy:
-
Log on to the ActivID CMS Operator Portal with an ActivID CMS Administrator certificate.
-
Click the Configuration tab, and then click Policies.
-
Depending upon the PKI applications to be used, add a new device policy.
-
Click Next, and then add the corresponding PKI applications.
-
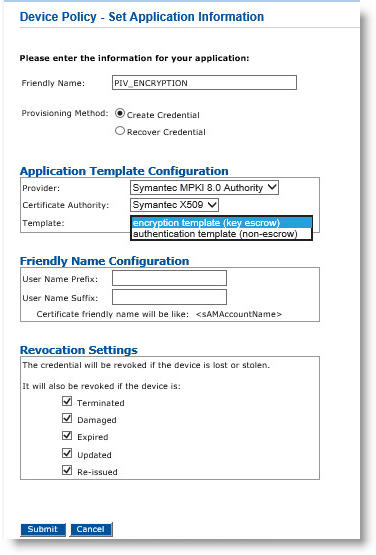
Click the Configure button corresponding to the PKI to display the Device Policy – Set Application Information page.
-
In the Friendly Name field, enter a valid, descriptive name for the certificate used for the device policy.
-
In the Provider drop-down menu, select Symantec Credential Provider.
-
Depending on the selected Provisioning Method setting, the fields vary.
-
If you select Create Credential for Provisioning Method:
Note: Selecting the Create Credential option is the equivalent of setting the former Recover Application option (available in previous ActivID CMS versions) to No.-
For Template, select either encryption template (key escrow) or authentication template (non-escrow) per your requirements. The encryption template allows key escrow.
-
Click Submit.
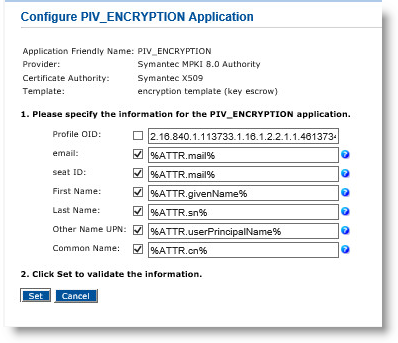
-
In the Profile OID field, make sure the profile OID matches the certificate profile template that you want to associate with this device policy.
You can find the certificate profile OID by logging on to the Symantec PKI Manager portal. For details, refer to Obtaining an RA Certificate to Store in a Java KeyStore File.
-
Click Submit.
-
Click Set.
-
-
If you select Recover Credential for the Provisioning Method, the Recovery Mode options become available:
Note: Selecting the Recover Credential option is the equivalent of setting the former Recover Application option (available in previous ActivID CMS versions) to Yes.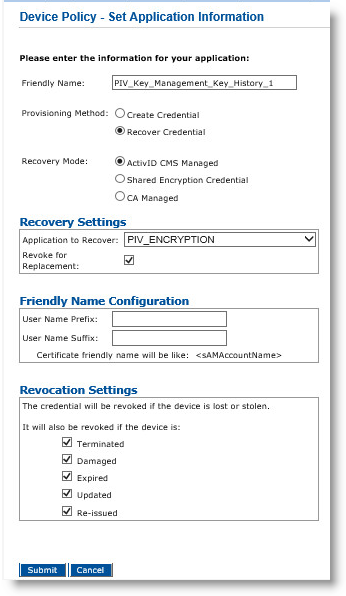
-
Select ActivID CMS Managed.
-
Under Recovery Settings, select the application to recover and select Revoke for Replacement.
This is a Symantec constraint as multiple valid encryption certificates per user are not allowed. The recovered encryption certificate must be revoked.
-
Click Submit.
-
-
-
Click Save.





