Installing KMS
ActivID KMS is delivered as part of the ActivID CMS distribution.
System Requirements
-
Microsoft® Windows® 10 or higher, or Windows Server® 2016 or higher (64-bit)
-
2 GB RAM
-
80 GB hard drive
-
Available PCI slot or Ethernet port
-
Removable hard drive (optional)
Refer to ActivID CMS System Environment for the list of supported HSMs.
Installation Procedure
Install the client software for each type of HSM A Hardware Security Module (HSM) securely stores secret key material. They are similar to large-storage, multisession smart cards. However, unlike smart cards, they are used mainly on the server side of a system.. For details, refer to the ActivID CMS Technical Note applicable to your HSM configuration.
Make sure that the HSM is accessible and functional.
Install ActivID KMS in a folder without any space characters " ".
-
Create a new directory on your hard drive.
-
Copy the ActivID KMS directory from the ActivID CMS distribution into the directory you created in step 1. Then copy the principal.cfg and test.cfg files of the HSM directory from the ActivID CMS distribution into the local KMS directory.
Important: This version of ActivID CMS supports FIPS Federal Information Processing Standard 140-2 Level 3 Entrust Datacard® (formerly Thales®) HSMs, which no longer support 2TDEA key generation and thus cannot issue SCP01 profiles.As a result, the default configuration of the HSM directory delivered with this version was updated to be more secure. SCP01 keys were removed and a Legacy subdirectory was added, providing access to definitions of the SCP01 keys (including 2TDEA keys).
For new ActivID CMS installations or upgrades that still require support for SCP01 profiles:
use the LEGACY\Test.cfg and LEGACY\Principal.cfg files (provided in the .zip file) for HSM initialization on an HSM that is not FIPS 140-2 Level 3.
For new ActivID CMS installations or upgrades with only SCP03 profiles support:
use the main Test.cfg and Principal.cfg files for HSM initialization.
For more information about which devices support SCP01 and SCP03 profiles, refer to Device Profiles and Hardware Devices.
The directory contains the:
-
ActivID KMS executable file (ackms.exe)
-
principal.cfg sample (for use when you create your own custom principal.cfg file)
-
test.cfg file containing the keys that ActivID KMS injects into the HSM during the Init Test HSM operation
-
If using an Entrust Datacard (formerly Thales) nShield™ HSM, on the machine where ActivID KMS is installed, go to System Properties > Advanced and then click Environment Variables.
-
Under System variables, click Path, and then click Edit.
-
Append the path variable value with <nfast ROOT>\bin directory (for example, C:\Program Files (x86)\nCipher\nfast\bin).
-
-
Depending on which HSM you are using, now you must copy a specific DLL file to the local KMS directory. Select one of the following:
-
For SafeNet Luna, copy the cryptoki.dll file from the HSM Installed directory (for example, C:\Program Files\SafeNet\LunaClient\) to the local KMS directory.
Note: For SafeNet Luna SA HSM, you must have the 64-bit Luna SA HSM client software installed and correctly configured, so that the HSM partition that you are targeting is visible on your machine. For details about connecting a client machine to HSM, refer to the SafeNet Luna SA HSM documentation.
-
For Entrust Datacard (formerly Thales) nShield Connect:
-
Copy the PKCS #11 cknfast-64.dll file from the <nfast ROOT>\toolkits\pkcs11 directory of the HSM Installed directory to the local KMS directory.
-
Modify or create the cknfastrc file in the <nFast ROOT> directory of the HSM Installed directory (for example, C:\Program Files(x86)\nCipher\nfast) to turn off the view of the accelerator slot and disable the security assurance mechanisms.
To modify the file, add the following lines:CopyCKNFAST_OVERRIDE_SECURITY_ASSURANCES=tokenkeys;unwrap_mech;unwrap_kek;explicitness
CKNFAST_NO_ACCELERATOR_SLOTS=1
Note: Make sure that the cknfastrc configuration file (located in C:\Program Files (x86)\nCipher\nfast\cknfastrc) only contains the above lines. -
- For AEP Keyper, copy the ap220w64HSM.dll file from the HSM Installed directory (for example, C:\Program Files\AEP\) or C:\Windows\System32 to the local KMS directory.
When you finish step 4, ActivID KMS installation is complete.
Testing the Installation
Before you use ActivID KMS to manage HSMs in a production environment, you must test the installation. This section explains how to start ActivID KMS, initialize a test HSM, view the contents of the test HSM, and exit ActivID KMS.
-
To launch ActivID KMS double-click the ackms.exe file.
The command prompt welcome screen is displayed.
-
To continue, press any key.
-
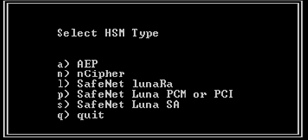
Select an HSM by entering the option that corresponds to your HSM type:
-
a) AEP
-
n) nCipher
-
l) SafeNet LunaRa
-
p) SafeNet Luna PCM or PCI
-
s) SafeNet Luna SA
-
-
Select one of the following sections to review sample command line illustrations, and then continue with step 5 below.
 Sample Flow 1: Select SafeNet Luna SA as the HSM
Sample Flow 1: Select SafeNet Luna SA as the HSM
When you select option “s” (SafeNet Luna SA) as the HSM type, one or more partitions are displayed (depending on the number of partitions set up when the SafeNet Luna SA HSM was prepared). A partition is a secure area in the HSM that contains keys. In order to access a partition, you must present the partition PIN.
In the following illustration, two HSM partitions are defined.
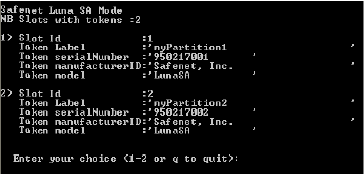
-
Select 1 or 2.
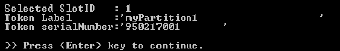
In this example, Partition 1 will receive the keys.
-
Press the Enter key. The command prompt main menu is displayed.
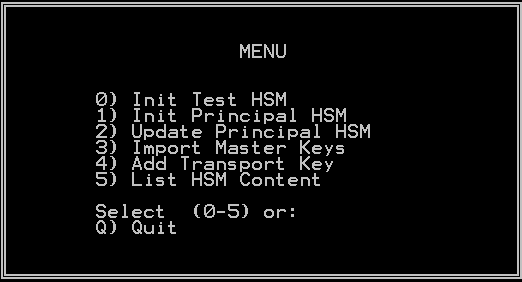
-
To continue the HSM initialization process, skip to step 5.
 Sample Flow 2: Select SafeNet Luna PCM or PCI as the HSM
Sample Flow 2: Select SafeNet Luna PCM or PCI as the HSM
When you select option “p” (SafeNet Luna PCM or PCI) as the HSM type, the following command lines are displayed (sample lines in the illustration). This also applies to Luna PCI-E models.
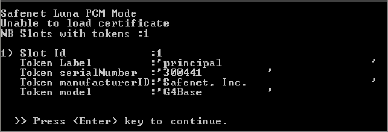
On SafeNet Luna PCM or PCI, there is only one partition available.
-
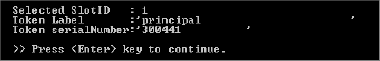
Press the Enter key.
-
Press the Enter key. The command prompt main menu is displayed.

-
To continue the HSM initialization process, skip to step 5.
 Sample Flow 3: Select nCipher as the HSM
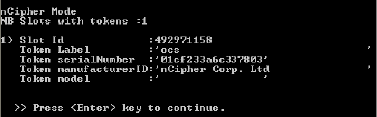
Sample Flow 3: Select nCipher as the HSM
When you select option “n” (nCipher) as the HSM type (which applies to Entrust Datacard (formerly Thales) nShield HSMs), the following command lines are displayed (sample lines in the illustration).
-
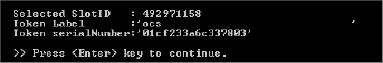
Press the Enter key.
-
Press the Enter key. The command prompt main menu is displayed.

-
-
From the command prompt menu, type 0 to start the Init Test HSM. The setup test HSM command prompt screen is displayed.
Important: Make sure that the HSM that you selected is connected or inserted properly. For SafeNet Luna PCM or PCI, make sure there is ONLY one SafeNet Luna PCM HSM connected to the SafeNet Luna Dock reader. You can use any HSM (new or already initialized).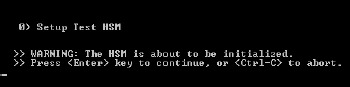
-
For SafeNet Luna PCM or PCI, the Init Test HSM operation requires that you enter the current Security Officer PIN in order to continue.
-
For SafeNet Luna PCM or PCI, the initial PIN for testing purposes is default (this is the HSM factory state).
-
-
To continue, press ENTER.
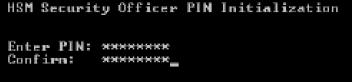
-
Enter and confirm the Security Officer PIN.
Note:About PINs and the rest of this test:
-
This is ONLY an initialization test of the HSM. What you see as you move through this test depends on the type of HSM you are using. Please review the tips here, but ignore any steps or directions that do not match what you see on your console. Follow the steps presented for your HSM type.
-
For SafeNet Luna PCM or PCI, the Init Test HSM operation requires that you enter the current Security Officer PIN in order to continue. For SafeNet Luna PCM or PCI, the initial PIN for testing purposes is default (this is the HSM factory state).
-
For SafeNet Luna SA, the Security Officer and Operator PIN are initialized through the SafeNet Luna SA tool when the HSM is set up (outside the scope of ActivID KMS). During ActivID KMS operations, the Operator is required to enter the Operator PIN, which protects access to the partition selected during the session. The 0) Init Test HSM and 1) Init Principal HSM The first or main HSM. If you require multiple HSMs with the same master keys, use HSM manufacturer tools to duplicate the keys in the other HSM. operations do not actually initialize the HSM, but just add the keys to the HSM. You must clean up the HSM using the SafeNet Tool, and call the partition clear: command to delete “old” keys when the test is completed.
-
For Entrust Datacard (formerly Thales) nShield, the Security Officer PIN and the Operator PIN are initialized using Entrust Datacard tools; the Security Officer and the Operator have these PINs on their smart cards, which they use to access the HSM. As a result, during ActivID KMS operations, there are prompts to enter the Operator PIN (which is the same as the PIN on the Operator card inserted into the nShield Module). For this model, the 0) Init test HSM and 1) Init Principal HSM operations do not actually initialize the HSM, but just add the keys to the HSM. As a result, if you are using Entrust Datacard nShield, you must clean up the HSM using an Entrust Datacard tool, such as KeySafe™ to delete “old” keys when the test is completed. END OF NOTE
-
-
Press ENTER.
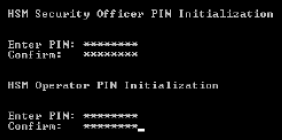
-
Enter and confirm a new HSM Operator PIN.
-
Press Enter.
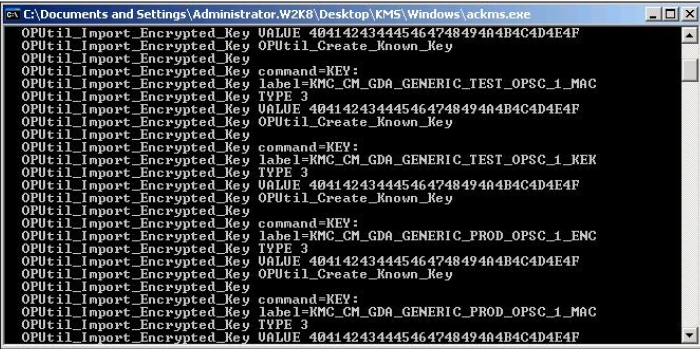
ActivID KMS reads the keys stored in the test.cfg file and injects them into the HSM.
-
When the operation is completed, press ENTER or any other key to return to the main menu.
-
From the ActivID KMS main menu, enter 5 (List HSM Content) and enter the correct Operator PIN (if prompted) in order to view the list of Keys.
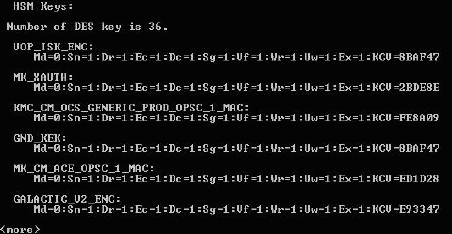
-
View the test HSM content to confirm that ActivID KMS successfully injected the test.cfg keys.
Note: The list of keys displayed will differ from what is displayed in the illustration on this page. Check the content of the test.cfg file to find out what keys are loaded into the test HSM -
Press ENTER to return to the main menu. To exit, type Q (Quit).





