Configure Data Input - Direct OCSP Interface
The Direct OCSP Interface is the Validation Authority built-in OCSP responder, which allows Validation Authority to directly service OCSP requests, rather than using a Validation Responder to service OCSP requests using pre-generated OCSP responses.
-
On the Configuration page, click configure Direct OCSP Interface.
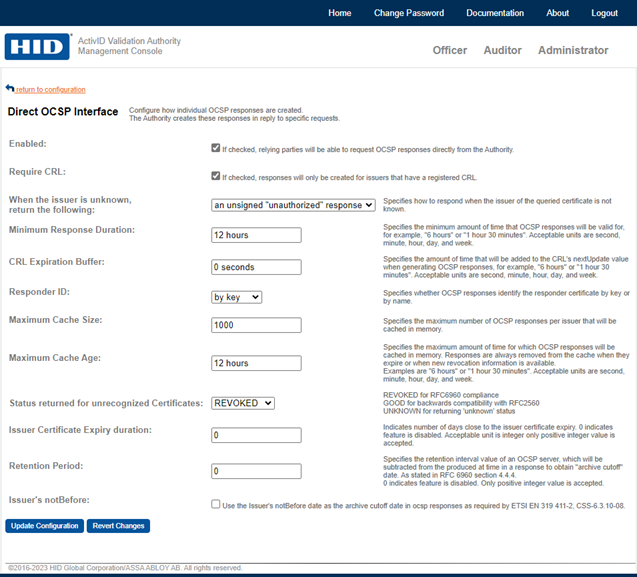
-
Select the Enabled option to enable generation of OCSP responses by the Direct OCSP Interface. By default, this option is not selected.
-
If a CRL should be registered for a certificate issuer before Validation Authority will return a definitive response of GOOD or REVOKED to an OCSP response, select the Require CRL option. This prevents Validation Authority from responding to OCSP requests when there is no CRL registered for the issuer of the certificate being queried. By default, this option is not selected
-
To specify how to respond when the issuer of the queried certificate is not known, select from the When the issuer is unknown, return the following drop-down list.
You can specify whether Validation Authority returns a signed unknown response or an unsigned unauthorized response when responding to an OCSP request that contains a certificate that was issued by a certificate issuer that is unknown to Validation Authority. Validation Authority can be configured to return either a signed Unknown response or an unsigned Unauthorized response when responding to an OCSP request that contains a certificate issued by a certificate issuer that is unknown to Validation Authority. By default, Validation Authority returns a signed Unknown response.
Based on the response received, relying parties can take additional actions required by their organization’s security policy.
-
Enter the Minimum Response Duration that specifies the minimum amount of time for which OCSP responses created by the Direct OCSP Interface are valid.
If the CRL that the Validation Authority creates responses from expires, this value will enable the Validation Authority to continue creating non-expired responses. Setting this value to 0 means that the Validation Authority cannot create non-expired responses after the expiration of the CRL used to create responses.
The default value is set to 12 hours which indicates that OCSP responses are generated with a minimum of a 12-hour validity period.
-
Enter the CRL Expiration Buffer that defines the length of time, in seconds, that a response is accepted as valid beyond the CRL’s nextUpdate time. OCSP responses are valid until a nextUpdate time that indicates when that response should be rejected in favor of a newer response. When set to a value greater than 0, the CRL Expiration Buffer property defines the length of time, in seconds, that a response is accepted as valid beyond the CRL’s nextUpdate time. This can be useful in preventing problems when Validation Authority is unable to obtain an updated CRL (for example, due to a network problem). A value of 0 means that the CRL’s validity period is used. The default value is 0.
-
From the Responder ID drop-down list, select the option to specify whether OCSP responses identify the responder certificate by key or by name.
You can specify the format of the responder ID that is contained in OCSP responses. The responder ID enables relying parties locate the responder certificate in the OCSP response. If you select by key, the responder ID will be represented by the hash of the public signature key of Validation Authority. If you select by name, the responder ID will be the distinguished name in the signing certificate of Validation Authority. HID Global recommends against selecting the by name option, unless your relying party software is unable to process responder IDs that use the key hash.
-
Enter the Maximum Cache Size that specifies the maximum number of responses per issuer that can be cached in memory.
This parameter specifies the maximum number of OCSP responses per issuer that will be cached in memory. A larger number can decrease response times, but will increase the amount of memory required by Validation Authority. The default setting is 1000. To disable response caching, set this value to 0. By default, Validation Authority will cache previously generated OCSP responses in memory to improve OCSP response performance. For more information, refer to Settings for Generating OCSP Responses.
-
Enter the Maximum Cache Age that specifies the maximum amount of time, in seconds, that a response will be cached in memory. The default setting is 43200 seconds, or 12 hours.
-
From the Status returned for unrecognized certificates drop-down list, select one of the following:
-
REVOKED - As defined in RFC 6960.
-
GOOD - For backward compatibility with RFC 2560.
-
UNKNOWN - Validation Authority can return UNKNOWN, if desired.
Recognized serial numbers can be one of the following:
-
Serial numbers that appears in the CRL
-
Serial numbers of the certificates known to be issued by the issuer.
Unrecognized serial numbers can be one of the following:
-
CA has not issued a certificate of the serial number
-
CA has issued a certificate of the serial number, but Validation Authority does not recognize it.
-
-
Enter a positive integer value in the Issuer Certificate Expiry duration field to enable this feature, the entered value specifies the number of days prior to the certificate expiry, from which the nextUpdate field’s format will change in the OCSP response. The default value is 0 which indicates the feature is disabled. Based on the entered expiry duration, if the issuer certificate is close to the expiry date then the nextUpdate field in the OCSP response will change to this format 9999<Month><Day><Hours><Minutes><Seconds>.
For Example, if the entered value is 20, and the expiry date is 30th December 2020, the value in the nextUpdate field of OCSP response will be 99991230235959Z (Time will change according to the zone) from 11th December 2020 onwards.
Where:
9999 – Year
12 – Month
30 – Date of Expiry
23 – Hours
59 – Minutes
59 – Seconds
-
Enter a positive integer value (1 to 99) in the Retention Period field to enable the Archive Cutoff feature. By default, the value is 0 and the feature is disabled. If this feature is enabled, archive cutoff date will be included in the OCSP response. The certificate's "archive cutoff" date will be derived by subtracting this retention interval value from the producedAt time in the OCSP response.
For Example, if the entered value is 7, and the producedAt time is 2013-11-13, then the archive cutoff value is 2006-11-13, which means that certificate expired before 2006-11-13 is not reliable.
-
Select the Issuer’s notBefore to enable the archive cutoff feature. If this feature is enabled, Retention Period field will become null and the issuer's valid from date will be used as archive cutoff date in the OCSP response.
-
When you have made the desired changes, click Update Configuration to save your changes.
Alternatively, click Revert Changes to discard your changes and revert to the previously saved settings.





