Configure Data Input - MiniCRL Generation
This applies to Validation Authority deployments with miniCRL (uncommon). For more information, refer to Using MiniCRLs.
This configures how MiniCRLs will be generated.
-
On the Configuration page, click configure MiniCRL Generation.
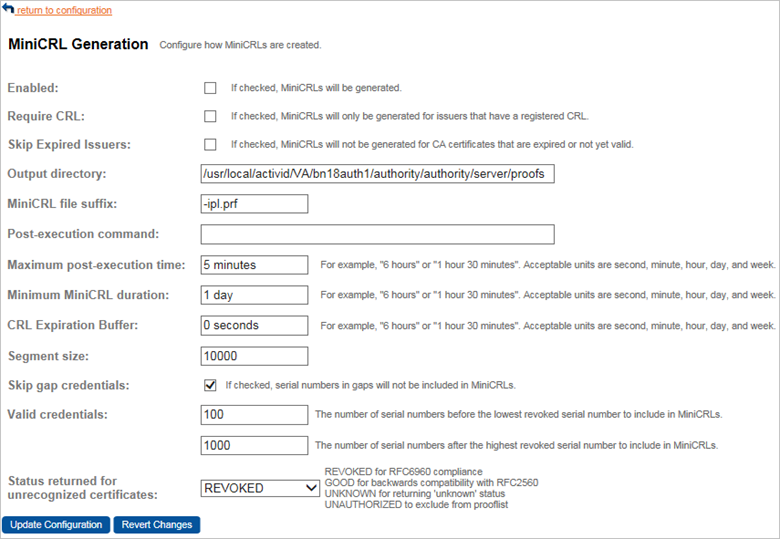
-
To enable MiniCRL generation, select the Enabled option.
-
To require that MiniCRLs are generated only for certificate issuers that have a registered CRL, select the Require CRL option.
-
You can specify whether a CRL should be registered for a certificate issuer before Validation Authority will generate MiniCRLs for that issuer.
-
Leave this option deselected if you want MiniCRLs to be generated regardless of whether or not the certificate issuer has a registered CRL.
-
-
To avoid generating response lists when CA certificates are expired or not yet valid, select the Skip Expired Issuers option.
-
To configure the location of the output directory where MiniCRLs are stored, enter the location in the Output Directory field.
-
When a MiniCRL is generated by Validation Authority, it is placed in this directory with a file name based on the nickname of the issuer. If this directory path is not absolute, it will be determined relative to the Validation Authority home directory. The default location, relative to the Validation Authority home directory, is authority/server/proofs/.
-
This default location is part of the Tomcat web server web path, which means that lists that are placed in this directory will be available over HTTP from Validation Authority.
For example, if Validation Authority were running on HTTP port 3501 on a machine named MY-MiniCRL, you could get the MiniCRL for an issuer named issuer1 from this URL:
http://MY-MiniCRL:3501/proofs/issuer1-ipl.prf
If the proof directory path is absolute, it can be used to write to any location, including mounted file servers.
-
-
To change the default MiniCRL file suffix, enter the new suffix in the MiniCRL file suffix field.
When a MiniCRL is generated and placed into the Output Directory, it will have a name that is constructed based on the nickname of the issuer with this suffix concatenated. For example, if the issuer's nickname is aaa-security-ca, and the MiniCRL file suffix is changed from the default -minicrl.prf to .prf, the file will be named as aaa-security-ca.prf.
-
Depending on your OS, enter your Post-execution command. This is a command that executes each time a MiniCRL is generated. Typically, copy the newly generated list to a new location for retrieval by a Validation Responder.
For example, on a Validation Authority running on a Linux OS, you can enter something like the following:
Copy/usr/local/scripts/securecopy {} /mnt/server/proofs/listnameWhere {} will be automatically replaced by the newly generated response list’s path.
On a Validation Authority running on a Windows OS, you can enter something like the following:
Copyxcopy.exe /Y {} f:\PATHWhere {} will be automatically replaced by the newly generated response list’s path, and /Y indicates that the script should overwrite older files without prompting.
-
Enter the Maximum post-execution time that specifies (in seconds) how long a post-execution command is allowed to execute before being forced to terminate by Validation Authority.
-
This is a value (in seconds) that limits how long a post-execution command will be allowed to execute before being forced to terminate by Validation Authority. The default value is 300.
-
-
Enter the Minimum response duration that specifies the minimum amount of time for which OCSP responses created by Validation Authority are valid.
-
If the CRL that the Validation Authority creates responses from expires, this value will enable the Validation Authority to continue creating non-expired responses. Setting this value to 0 means that the Validation Authority cannot create non-expired responses after the expiration of the CRL used to create responses.
-
-
Enter the CRL Expiration Buffer that defines the length of time, in seconds, that a response is accepted as valid beyond the CRL’s nextUpdate time.
-
OCSP responses are valid until a nextUpdate time that indicates when that response should be rejected in favor of a newer response.
-
When set to a value greater than 0, the CRL Expiration Buffer property defines the length of time, in seconds, that a response is accepted as valid beyond the CRL’s nextUpdate time.
-
This can be useful in preventing problems when Validation Authority is unable to obtain an updated CRL (for example, due to a network problem).
-
A value of 0 means that the CRL’s validity period is used.
-
-
To change the maximum number of certificates represented by each MiniCRL segment, enter the new number in the Segment size field.
-
MiniCRLs are generated in segments. Each segment represents a number of certificates which are either valid or revoked.
-
This property determines the expected number of certificates for which status information is included in each generated MiniCRL segment. When the CRL used to generate a MiniCRL segment contains a gap, the MiniCRL generator ends the segment with the last credential before the gap and begins a new segment starting with the first credential after the gap. The default value is 10000.
-
If this value is set higher, the server CPU time and bandwidth required to transmit the MiniCRL segments to relying parties are reduced (since fewer signatures are generated), but more server memory is used during MiniCRL generation.
-
-
Select the Skip gap credentials option.
-
If selected, Validation Authority will not include some of the unrecognized serial number which is in a big gap between 2 adjacent recognized serial numbers.
-
Any OCSP requests for unrecognized certificates will receive a UNAUTHORIZED response code.
-
-
To change the number of Valid credentials before the lowest revoked credential from a CRL that will be included in a MiniCRL, enter the new number in the serial numbers before the lowest revoked serial number field.
-
When Validation Authority generates a MiniCRL using CRLs, this value determines the number of valid certificate statuses that are generated for credentials that immediately precede the credential with the lowest serial number contained in the CRL.
-
This buffer is attached to the beginning of the CRL and to the beginning of every cluster of entries in the CRL. Typically, you set the values of this property based on the size of the batches of certificates that the CA tends to issue in a given serial number range.
-
-
To change the number of Valid credentials after the highest revoked credential from a CRL that will be included in a MiniCRL, enter the new number in the serial numbers after the highest revoked serial number field.
-
When Validation Authority is generating a MiniCRL using CRLs, this value determines the number of valid certificate statuses that will be generated for credentials that immediately follow the credential with the highest serial number contained in the CRL.
-
This buffer is attached to the end of the CRL and to the end of every cluster of entries in the CRL. Typically, you set the value of this property based on the size of the batches of certificates that the CA tends to issue in a given serial number range. This property is set larger than the number of serial number before the lowest revoked serial number to include in MiniCRLs to account for growth.
-
-
From the Status returned for unrecognized certificates drop-down list, select one of the following:
-
REVOKED - As defined in RFC 6960.
-
GOOD - For backward compatibility with RFC 2560.
-
UNKNOWN - Validation Authority can return UNKNOWN, if desired.
-
UNAUTHORIZED - To be excluded from the proof list.
A proof list contains revocation status data for all the serial numbers that are recognized and those for some of the serial numbers that are unrecognized.
If you selected UNAUTHORIZED, then unrecognized serial numbers are excluded from the proof list. Any OCSP requests for unrecognized certificates will receive an UNAUTHORIZED response code.
If you have selected UNAUTHORIZED, then perform the following steps to configure Validation Authority to control which unrecognized serial numbers are to be included from the proof list. This configuration prevents the size of the proof list from getting too large. For example, if CA issues certificates of random serial numbers, then a proof list gets very large if all the unrecognized serial numbers are included.
-
-
Click Update Configuration to save your changes.
Alternatively, click Revert Changes to cancel your changes.





