Configure System Settings - Trust
This feature limits trust during PKI transactions to certain certificates. You can specify trust relationships between the Direct OCSP Interface and foreign certificates.
-
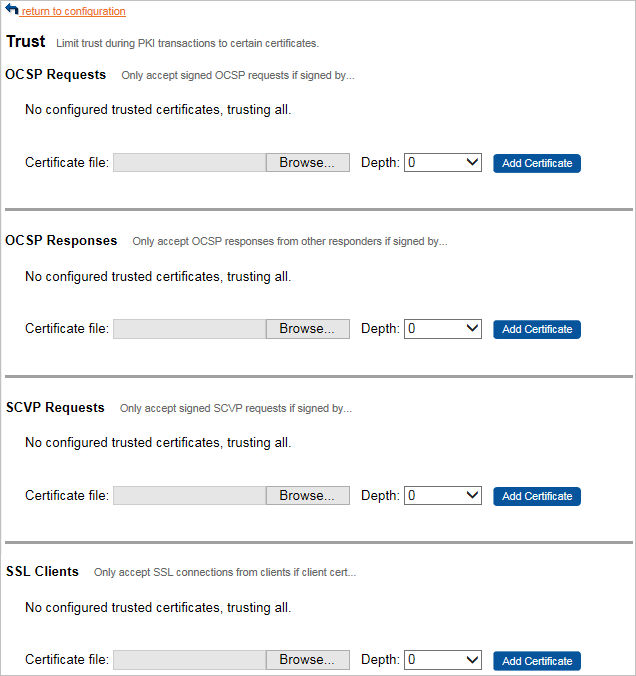
On the Configuration page, click trust.
-
To add a certificate used to sign for OCSP Requests, OCSP Responses, SCVP Requests, and SSL Clients, click Browse to locate the Certificate file.
-
First, configuring OCSP Request trust restricts the set of relying parties that will be trusted when the Validation Responder receives digitally signed OCSP requests. The request will only be serviced if it is digitally signed and the signer’s certificate is explicitly trusted or can be chained back to a trusted certificate with fewer than the set Depth certificates in the chain. If OCSP Request trust is configured, unsigned OCSP requests will be rejected.
-
Second, configuring OCSP Response trust restricts the set of Validation Authority certificates that will be trusted when the Validation Responder receives a response to a relayed OCSP request. The response will only be trusted if the Validation Responder certificate included in the response is explicitly trusted or can be chained back to a trusted certificate with fewer than the set Depth certificates in the chain. If OCSP Response trust is configured, responses to relayed OCSP requests will be re-signed by the Validation Responder if the responder is capable of signing and the response can be trusted. If the response cannot be trusted, it will be returned to the relying party without being re-signed.
-
Third, configuring SCVP Request trust restricts the set of client certificates that will be trusted when Validation Authority receives SCVP requests. The SCVP request will only be accepted if the certificate used to sign the request is explicitly trusted or can be chained back to a trusted certificate with fewer than the set Depth certificates in the chain.
-
Fourth, configuring SSL Client trust restricts the set of client certificates that will be trusted when the Validation Responder receives OCSP requests via HTTPS. The SSL session will only be accepted if the client certificate is explicitly trusted or can be chained back to a trusted certificate with fewer than the set Depth certificates in the chain. Even if SSL Client trust is configured, the Validation Responder will still respond to insecure (HTTP) requests.
-
-
From the Depth drop-down list, select your option.
The Depth parameter specifies the maximum length of the chain of certificates that can be used to link the certificate being tested to a trusted certificate.
-
Click Add Certificate.





