Distributed Certificate Validation Technology
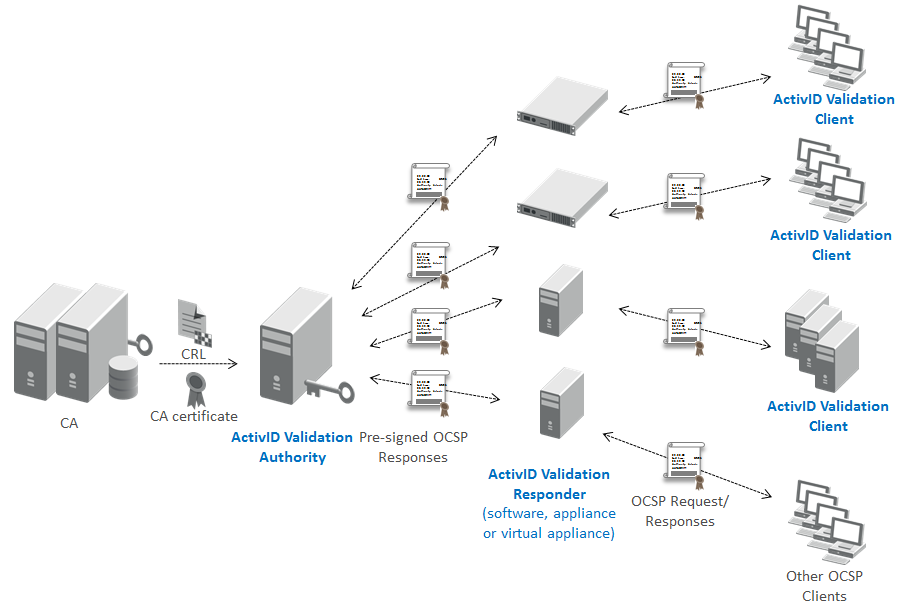
The HID Global distributed certificate validation approach is based on the design principle of separating security sensitive data and trusted operations from the delivery process of providing certificate status to relying party applications. This approach eliminates the scalability and availability problems associated with the alternative validation approaches of CRLs and Online Validation.
A single, centralized ActivID Validation Authority (VA) manages validation information for a set of certificate issuers (Certificate Authorities, or CA). Validation Authority periodically creates and publishes OCSP response lists for these issuers.
The distributed ActivID Validation Responders (VRs) periodically retrieve the new OCSP response lists when they become available. Validation Responders are available as software, as an appliance, or as a virtual appliance.
The relying parties are OCSP Clients. They can be using ActivID Validation Client or other third-party OCSP clients. ActivID Validation Client may be installed on either workstations or servers. Note that some ActivID Validation Client versions are named Desktop Validation Client (when installed on workstations) and SerVE – for Server Validation Extension (when installed on servers; different models exist for different server types: Windows Domain Controller, IIS web server, Exchange server with OWA).
The relying party application validates a user’s certificate through the following steps:
-
Receives the user’s certificate.
-
Verifies the integrity of the certificate (by checking its digital signature, expiration date, and so on).
-
Checks associated authentication factors (PIN, public key challenge, biometrics, and so on).
-
Requests an OCSP response from a Validation Responder.
-
Receives the OCSP response for the user’s credential.
-
Verifies the integrity of the OCSP response.
-
Processes or denies the requested transaction based on the information received from the Responder.
This process performs authentication and validation of the user’s credentials. As long as the relying party can receive a current OCSP response, it can perform all of these operations without making a real-time connection to a central, trusted authority.
OCSP responses are public, verifiable, and tamper-evident, so they can be published widely. Since the Validation Responders only return responses that were pre-generated by a Validation Authority, Validation Responders do not have to be individually trusted or tightly secured. A relying party can accept an OCSP response coming from any Validation Responder, regardless of the location of that specific Responder or who is administering it.





