Network Security
In addition to providing physical security, you must ensure that the Validation Authority server is protected against unauthorized network access.
The following diagrams illustrate two possible configurations of a Validation Authority in a secure data center.
-
The first configuration illustrates a minimally secure configuration that provides good security, but permits some limited network requests from external network locations.
-
The second configuration illustrates a slightly more complex configuration that offers the highest level of security by eliminating all external network requests to the Validation Authority.
-
In summary, the below shown examples of configurations that provide some protection for Validation Authority, but cannot guarantee network security in your environment. You must review the security in your environment with your network administrator.
Medium Security Deployment:
In a medium security deployment, Validation Authority is shielded from most network attacks through a Firewall which strictly limits requests to Validation Authority server so that only the IP addresses of known Validation Responders, administrators, and system operators are allowed to communicate with the server from outside the protected environment.
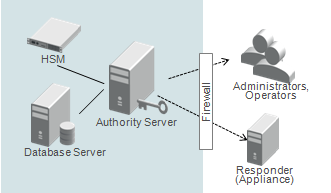
A proper firewall can also limit the communications types (protocols) and provide intrusion detection tools for responding to network attacks.
Such a firewall, along with the built-in security of the Validation Authority server, can prevent most access attempts from unauthorized sources and limit the impact of such access.
High-Security Deployment:
A high security deployment separates the external publishing functions of Validation Authority from the security-sensitive functions and divides these into separate network segments.
In this configuration, Validation Authority can be administered ONLY from within the protected subnet (shown as the Protected Zone).
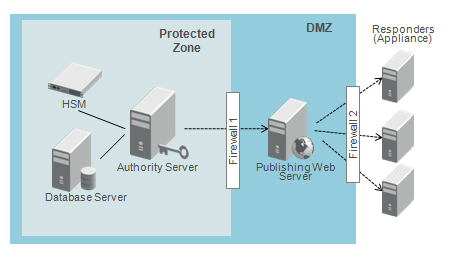
Communication with the outside world is mediated through a static publishing web server which receives the response list to redistribute to Validation Responders. The division between the protected subnet and the partially public DMZ is enforced through a second firewall (or router configuration) that only allows outbound network connections from Validation Authority to its publishing server. This enables Validation Authority to publish its OCSP response lists through a standard mechanism, such as NFS, while being protected from any requests from the external network.
Additional security could be achieved by removing all network connectivity between the subnet containing Validation Authority and other networks. In this case, OCSP response lists would be published using a physical medium such as a CD-ROM.
Security Considerations for Non-Distributed Operations
The Validation Authority’s direct OCSP interface and SCVP DPV interface require that relying parties have direct network access to Validation Authority. If your configuration uses the direct OCSP interface or the DPV interface, make sure that the firewall permits access to Validation Authority’s HTTP or HTTPS ports by Validation Responder or other relying party applications. For information about configuring the port numbers, refer to the description of the conf/server.xml file in the Advanced Configuration section.
You should also consider limiting access to Validation Authority only to trusted IP addresses and changing the URL used to service requests made to the direct OCSP interface and the DPV interface. For more information, refer to the description of the server/WEBINF/web.xml file in the Advanced Configuration section.





