Simple Distributed OCSP and SCVP (DPD) Deployment
The following figure illustrates how Validation Authority can be integrated into a simple deployment to offer Distributed OCSP and SCVP (DPD) services.
Functional Architecture for a Simple OCSP and SCVP (DPD) deployment
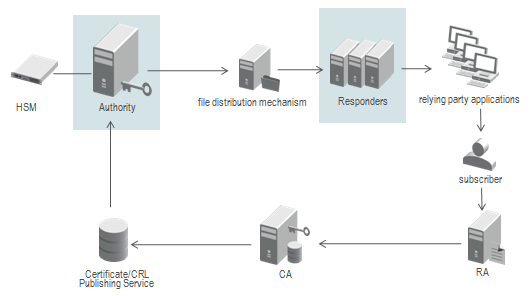
Prior to system operation, the Validation Authority must be configured with the certificate issuers that it will support. Issuers are registered with the Authority manually or using LDAP queries. New certificate issuers can be registered as required during operation. Authority dynamically discovers new certificate issuers from all configured LDAP and HTTP data sources.
-
Certificate issuers (CAs) publish Certificate Revocation Lists which Validation Authority uses to track certificates that are revoked or suspended. CRLs are digitally signed by the certificate issuer.
-
Certificate issuers publish end-entity certificates which Validation Authority retrieves. In most cases, Validation Authority does not require the end-entity certificates when generating OCSP responses. Certificates are digitally signed by the certificate issuer.
-
Validation Authority periodically creates and publishes lists containing current OCSP responses for an issuer’s certificates. Validation Authority also periodically precomputes and publishes lists containing current certification paths (PDP). Each response is digitally signed by Validation Authority.
-
Subscribers request services or access from a relying party application.
-
Relying party applications query Validation Responders for the status of a certificate. Validation Responder returns the appropriate OCSP response. Relying party applications also query Validation Responders for a certification path. Validation Responder returns one or more previously published certification paths to the relying party.
-
Relying party applications grant or deny a subscriber's service request based on the response received from Validation Responder.
-
The Validation Suite components (Validation Authority and Validation Responder) are deployed as standalone programs that can be integrated easily into existing infrastructures and business processes.
In this example, the subscriber represents an entity that requests access to a service, data, or physical location by presenting his or her certificate to a relying party (RP) application.
Certificates are generated by the CA upon receipt of an authorized request from a Registration Authority (RA). The relying party grants or denies access based on the integrity and validity of the presented certificate.





