Certificates
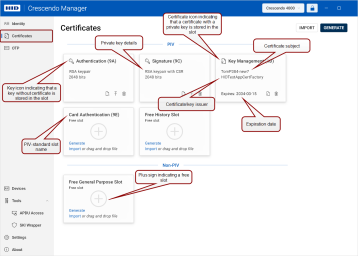
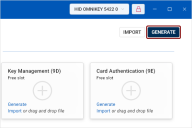
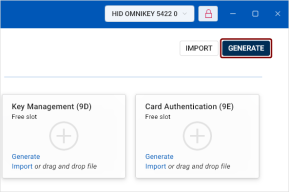
The Certificates view accessible from the left navigation pane enables you to access and manage the certificates and keys stored on a selected token.
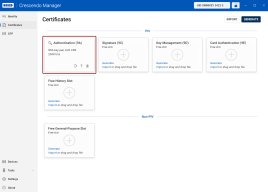
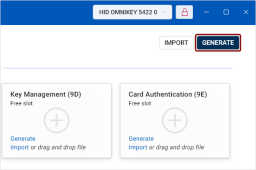
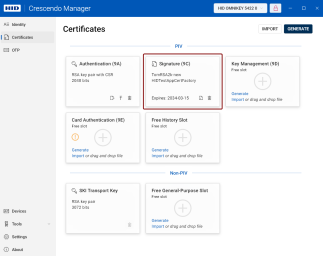
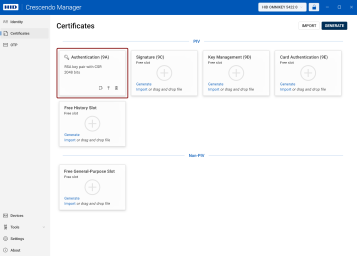
Here, you can view both the free slots and the keys and certificates currently stored in them. The slots are displayed as individual tiles.
Available Slots
-
PIV (Personal Identity Verification) Slots:
-
Authentication (Slot 9A): This slot is used for keys that authenticate the holder's identity, usually for system login.
-
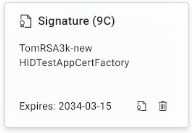
Signature (Slot 9C): This slot holds keys used to digitally sign documents, files and communications.
-
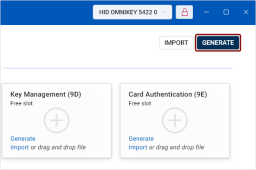
Key Management (Slot 9D): This slot is for keys that provide encryption for confidentiality, such as decrypting emails.
-
Card Authentication (Slot 9E): This slot is used for keys that authenticate the device (not the user) to systems, typically via the contactless interface. By default, this slot does not protect keys with a PIN.
-
Free History Slot: In addition to the designated PIV slots, the device can hold additional keys in generic slots, which are mostly used for archiving key management (that is encryption) certificates.
-
-
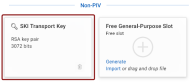
Non-PIV Slots:
-
Free General-Purpose Slot: Crescendo 4000 Cards provide the capability to add new general-purpose slots, with the only limitation being the memory available on the card. These slots provide flexibility for additional security functions that may not fall under standard PIV categories.
-
Validity
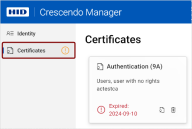
If a certificate has been generated or imported to your device, the tile displays the expiration date.
-
Yellow text "Expires soon" indicates that the certificate will expire within a month.
-
Red text "Expired" indicates that the key or certificate has already expired.
If one or more certificates expire within a month or have already expired, a yellow warning icon  is displayed on the Certificates navigation pane tab.
is displayed on the Certificates navigation pane tab.
More details about a certificate's validity can be viewed by clicking on the respective tile.
Actions Available From the Certificates View
Generating Keys, Certificate Signing Requests, and Certificates
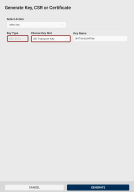
Crescendo Manager allows you to generate new public-private key pairs with your tokens.
To generate a new key pair with the selected token:
-
Go to the Certificates view in the left navigation pane.
-
Click the Generate link on the desired slot.
-
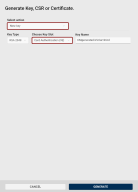
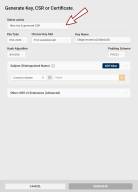
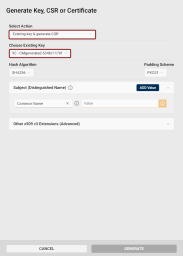
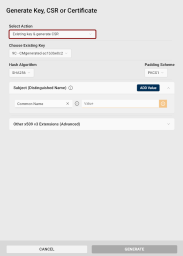
The Generate Key, CSR or Certificate dialog opens, with the New key generation action and the specific slot already pre-selected.
(An alternative to the Generate link is to click the Generate button in the top-right corner of the Certificates view and select New key from the Select action drop-down.)
-
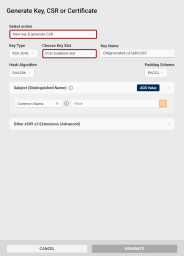
Key Type: Select the key pair type to generate. The key pair type determines the cryptographic algorithm and key length.
 Available options:
Available options:
-
RSA 2048 (default): 2048-bit Rivest-Shamir-Adleman key
-
RSA 3072: 3072-bit Rivest-Shamir-Adleman key
-
RSA 4096: 4096-bit Rivest-Shamir-Adleman key
-
ECC P-256: Elliptic curve-based 256-bit key.
-
ECC P-384: Elliptic curve-based 384-bit key.
-
-
Choose Key Slot: If necessary, you can select a different slot for generating the new key pair.
 Available options:
Available options:
-
First available slot: The key will be generated in the first free slot. You can select this option if the key usage is not important.
-
Authentication (9A)
-
Signature (9C)
-
Key Management (9D)
-
Card Authentication (9E)
-
First available History Slot
-
SKI Transport Key RSA-3072 key uniquely bound to a specific token, used to securely transfer data to that token in compliance with the Secure Key Injection protocol.: Select this option to generate an RSA-3072 key for encrypting keys for Secure Key Injection. The Key Type field will be set to RSA 3072 automatically.
-
First General-Purpose Slot
-
-
Key Name: The key name is a human-readable string used to identify the key. Use the randomly generated value or overwrite it.
Note:Knowing the key name is useful when you need to use the key directly, such as with the Cryptography Next Generation (CNG Cryptography Next Generation. A modern cryptographic API (Application Programming Interface) introduced by Microsoft as part of Windows to replace the older CryptoAPI. It provides a flexible and extensible framework for implementing cryptographic algorithms, key storage, and secure key management and supports a wide range of cryptographic operations, including encryption, decryption, hashing, and digital signatures.) application programming interface. See the simple PowerShell example below, which opens the key for further actions.
Copy[System.Security.Cryptography.CngKey]::Open($keyname, [System.Security.Cryptography.CngProvider]::MicrosoftSmartCardKeyStorageProvider) -
Click the Generate button. The new key is now displayed in the respective slot tile.
-
To copy the public key, click the tile. The private key cannot be accessed or retrieved.
Actions Available With an Existing Key
Once you have a key stored on your token, you can:
Crescendo Manager allows you to generate cryptographic keys and corresponding certificate signing requests (CSR) with your tokens.
To generate a new key and CSR with the selected token:
-
Go to the Certificates view in the left navigation pane.
-
Click the Generate button in the top-right corner of the Certificates view.
-
The Generate Key, CSR or Certificate dialog opens, with the New Key & generate CSR generation action and the First available slot pre-selected.
-
Key Type: Select the key pair type to generate. The key pair type determines the cryptographic algorithm and key length.
 Available options:
Available options:
-
RSA 2048 (default): 2048-bit Rivest-Shamir-Adleman key
-
RSA 3072: 3072-bit Rivest-Shamir-Adleman key
-
RSA 4096: 4096-bit Rivest-Shamir-Adleman key
-
ECC P-256: Elliptic curve-based 256-bit key.
-
ECC P-384: Elliptic curve-based 384-bit key.
-
-
Choose Key Slot: The First available slot option is pre-selected. You can choose a different slot for generating the new key pair and CSR.
 Available options:
Available options:
-
First available slot: The key and the CSR will be generated in the first free slot. Select this option if the key usage is not important.
-
Authentication (9A)
-
Signature (9C)
-
Key Management (9D)
-
Card Authentication (9E)
-
First available History Slot
-
First General-Purpose Slot
-
-
Key Name: The key name is a human-readable string used to identify the key. Use the randomly generated value or overwrite it.
Note:Knowing the key name is useful when you need to use the key directly, such as with the Cryptography Next Generation (CNG Cryptography Next Generation. A modern cryptographic API (Application Programming Interface) introduced by Microsoft as part of Windows to replace the older CryptoAPI. It provides a flexible and extensible framework for implementing cryptographic algorithms, key storage, and secure key management and supports a wide range of cryptographic operations, including encryption, decryption, hashing, and digital signatures.) application programming interface. See the simple PowerShell example below, which opens the key for further actions.
Copy[System.Security.Cryptography.CngKey]::Open($keyname, [System.Security.Cryptography.CngProvider]::MicrosoftSmartCardKeyStorageProvider) -
Hash Algorithm: Select the hash algorithm used to create a digital representation (hash) of the data within the CSR. This hash is used to create a digital signature that proves the integrity and authenticity of the CSR.
 Available options:
Available options:
-
SHA1
-
SHA256 (default)
-
SHA384
-
SHA512
We recommend using SHA-256 (default) or higher.
-
-
Padding Scheme: If a RSA key type is selected, you can choose the padding A method used to add extra data to a hash before creating a digital signature with an RSA key to ensure that the resulting signature is unique and resistant to certain types of cryptographic attacks. scheme.
-
PKCS1 (Public Key Cryptography Standards #1)
-
PSS (Probabilistic Signature Scheme): PSS adds randomness to the padding process, making the signature more secure against certain types of cryptographic attacks.
Important: PSS is considered more secure, but PSS-signed certificates may not be supported by older systems.
-
-
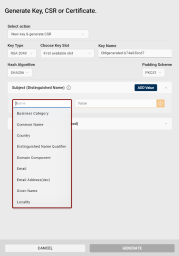
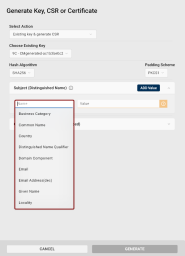
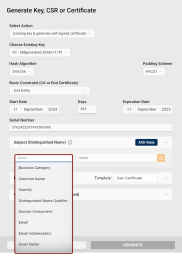
Subject (Distinguished Name): Add at least one Subject Distinguished Name component for your CSR.
-
Common Name is selected as default, but you can delete the value by clicking the Clear icon
 and select another option from the drop-down list.
and select another option from the drop-down list. -
Alternatively, you can type the attribute's long or short name or OID directly into the field.
-
Click the Add Value button to include additional attributes of your Subject Distinguished Name in the CSR.
-
-
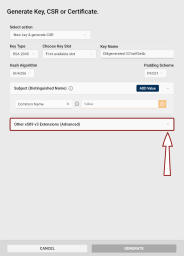
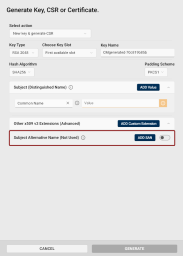
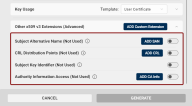
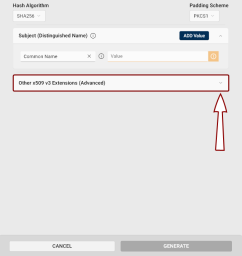
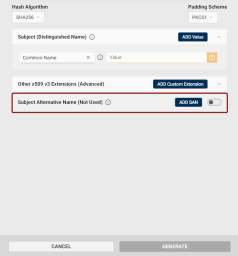
Other x509 v3 Extensions (Advanced): If you need x509 v3 extensions to be added to your CSR:
-
Click the Other x509 v3 Extensions (Advanced) drop-down button.
-
The Subject Alternative Name (SAN) extension section will be displayed.
(If you want to add a custom extension to your CSR, see point 11.)
-
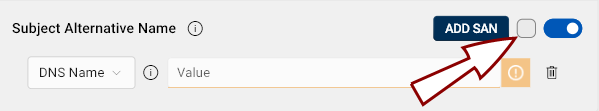
Click the toggle button
 to enable SAN in your CSR.
to enable SAN in your CSR. -
A checkbox will appear to the left of the toggle button. If checked, the extension will be marked as critical.
-
Click the Add SAN button for additional SAN entries. The number of SANs is not limited.
The available types of SANs are:
-
IP Address
-
DNS Name
-
Email
-
URI (Unique Resource Identifier)
-
UPN (User Principal Name)
Hover over the information icon to view example entries for each type.
-
-
-
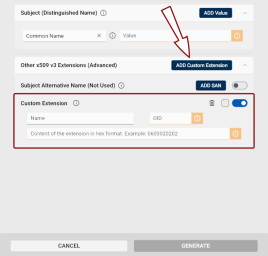
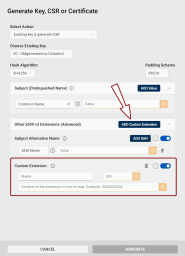
To add custom extensions to your certificate, click the Add Custom Extension button in the Other x509 v3 Extensions (Advanced) field.
-
The Name field for the custom extension is for informational purposes only.
-
Enter the custom extension object identifier (OID Object identifier. Globally unique identifiers standardized by the International Telecommunication Union. OIDs are represented as a series of numbers separated by dots (e.g., 2.5.29.37).) (e.g., 2.5.29.19).
-
Add the extension content in hexadecimal format.
-
To mark an extension as critical, check the checkbox to the left of the toggle button.
-
To remove an extension, click the trash bin icon
 .
.
-
-
Click the Generate button.
The new key with the generated CSR is now displayed in the respective slot tile.
Crescendo Manager allows you to generate cryptographic keys and corresponding self-signed certificates with your tokens.
To generate a new key and self-signed certificate with the selected token:
-
Go to the Certificates view in the left navigation pane.
-
Click the Generate button in the top-right corner of the Certificates view.
-
The Generate Key, CSR or Certificate dialog opens, with the New Key & generate CSR action and the First available slot pre-selected.
-
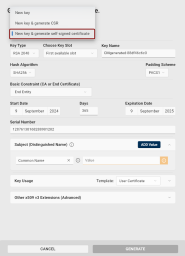
Click the Select Action drop-down and select New key & generate self-signed certificate.
-
Key Type: Select the key pair type to generate. The key pair type determines the cryptographic algorithm and key length.
 Available options:
Available options:
-
RSA 2048 (default): 2048-bit Rivest-Shamir-Adleman key
-
RSA 3072: 3072-bit Rivest-Shamir-Adleman key
-
RSA 4096: 4096-bit Rivest-Shamir-Adleman key
-
ECC P-256: Elliptic curve-based 256-bit key.
-
ECC P-384: Elliptic curve-based 384-bit key.
-
-
Choose Key Slot: The First available slot option is pre-selected. You can choose a different slot for generating the new key pair and self-signed certificate.
 Available options:
Available options:
-
First available slot: The key and the self-signed certificate will be generated in the first free slot. Select this option if the specific type of key usage is not important.
-
Authentication (9A)
-
Signature (9C)
-
Key Management (9D)
-
Card Authentication (9E)
-
First available History Slot
-
First General-Purpose Slot
-
-
Key Name: The key name is a human-readable string used to identify the key. Use the randomly generated value or overwrite it.
Note:Knowing the key name is useful when you need to use the key directly, such as with the Cryptography Next Generation (CNG Cryptography Next Generation. A modern cryptographic API (Application Programming Interface) introduced by Microsoft as part of Windows to replace the older CryptoAPI. It provides a flexible and extensible framework for implementing cryptographic algorithms, key storage, and secure key management and supports a wide range of cryptographic operations, including encryption, decryption, hashing, and digital signatures.) application programming interface. See the simple PowerShell example below, which opens the key for further actions.
Copy[System.Security.Cryptography.CngKey]::Open($keyname, [System.Security.Cryptography.CngProvider]::MicrosoftSmartCardKeyStorageProvider) -
Hash Algorithm: Select the hash algorithm used to create a digital representation (hash) of the data within the certificate. This hash is used to create a digital signature that proves the integrity and authenticity of the certificate.
 Available options:
Available options:
-
SHA1
-
SHA256 (default)
-
SHA384
-
SHA512
We recommend using SHA-256 (default) or higher.
-
-
Padding Scheme: If a RSA key type is selected, you can choose the padding A method used to add extra data to a hash before creating a digital signature with an RSA key to ensure that the resulting signature is unique and resistant to certain types of cryptographic attacks. scheme.
-
PKCS1 (Public Key Cryptography Standards #1)
-
PSS (Probabilistic Signature Scheme): PSS adds randomness to the padding process, making the signature more secure against certain types of cryptographic attacks.
Important: PSS is considered more secure, but PSS-signed certificates may not be supported by older systems.
-
-
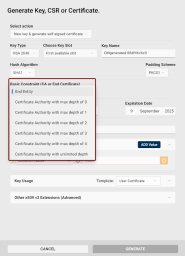
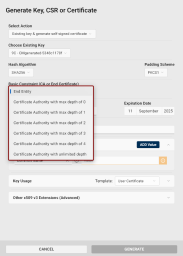
Basic Constraint (CA or End Certificate): Use this field to specify whether the certificate should be an end-entity certificate (default) or a Certificate Authority (CA) certificate.
 Available options:
Available options:
-
End Entity: Issues a leaf certificate for an end user, server, or device.
-
Certificate Authority with max depth of 0: Issues a CA certificate that can only issue end-entity certificates (no CA certificates).
-
Certificate Authority with max depth of 1-4: Issues a CA certificate that can issue one to four levels of subordinate CA certificates, in addition to end-entity certificates.
-
Certificate Authority with unlimited depth: Issues a CA certificate that can issue an unlimited number of subordinate CA certificates. This setting is typically used for root CAs or higher-level CAs that need the capability to create multiple levels of CA certificates below them.
Note: If you selected a CA certificate as the basic constraint, don't forget to specify appropriate key usage (see point 14). -
-
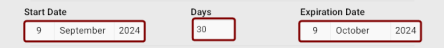
Set the self-signed certificate validity: Use the Start Date field along with the validity period defined in days, or set the Expiration Date directly.
-
Serial Number: Enter a decimal or hexadecimal number for the certificate's serial number, or use the automatically generated value.
-
Subject (Distinguished Name): Specify at least one Subject Distinguished Name component for your self-signed certificate.
-
Common Name is selected as default, but you can delete the value by clicking the Clear icon
 and select another option from the drop-down list.
and select another option from the drop-down list. -
Alternatively, you can type the attribute's long or short name or OID directly into the field.
-
Click the Add Value button to include additional attributes of your Subject Distinguished Name in the self-signed certificate.
-
-
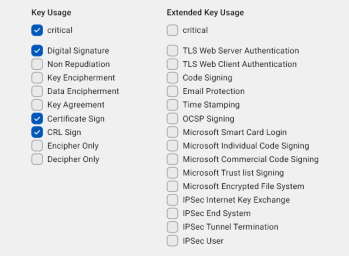
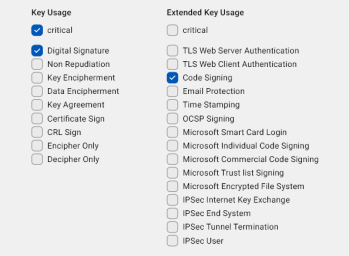
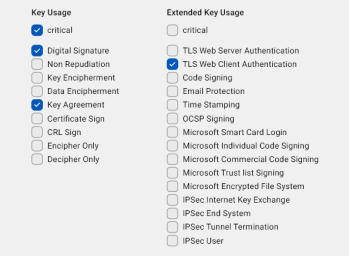
Key Usage: Use this section to specify the intended purpose of the certificate. The User Certificate template is pre-selected.
You can select a template with pre-selected options, which you can edit, or choose the empty template to define the key usage from scratch.
Click the drop-down button
 on the right to display key usage and extended key usage options.
on the right to display key usage and extended key usage options.The available templates are:
-
 Certificate Authority: You can use this template as a starting point if you selected a CA certificate as the basic constraint (see point 10.)
Certificate Authority: You can use this template as a starting point if you selected a CA certificate as the basic constraint (see point 10.) -
 User Certificate(default)
User Certificate(default)
-
Empty
-
-
Other x509 v3 Extensions (Advanced): If you need x509 v3 extensions to be added to your certificate:
-
Click the Other x509 v3 Extensions (Advanced) drop-down button.
-
A list of most commonly used extensions will be displayed.
If you want to add a custom extension to your certificate, see point 16.
-
Click the toggle button
 to enable an extension in your certificate.
to enable an extension in your certificate. -
A checkbox will appear to the left of the toggle button. If checked, the extension will be marked as critical.
-
 Subject Alternative Name:
Subject Alternative Name:
-
IP Address
-
DNS Name
-
Email
-
URI (Unique Resource Identifier)
-
UPN (User Principal Name)
Hover over the information icon to view example entries for each type.
Click the Add SAN button for additional SAN entries. The number of SANs is not limited.
-
-
CRL Distribution Points:
Specify the HTTPS or LDAP endpoints' URLs where the Certificate Revocation List (CRL) can be accessed.
Click the Add CRL button for additional CRL distribution point entries. The number of entries is not limited.
-
Subject Key Identifier
This field is used to uniquely identify the certificate. Its value is typically the SHA-1 hash of the subject's public key.
If not enabled, the correct value will be automatically filled in during generation. You may enter your own value for testing purposes.
-
Authority Information Access:
This extension specifies the locations where information about the issuing Certificate Authority (CA) certificate can be found, typically HTTP or LDAP URIs.
Select the access method to retrieve information about the CA certificate and enter the corresponding value:
-
OCSP: Specify the URI for the Online Certificate Status Protocol (OCSP) responder, which checks the revocation status of the certificate.
-
CA Issuer: Specify the URI for the issuing CA’s certificate.
-
-
-
To remove an extension, click the trash bin icon
 .
.
-
-
To add custom extensions to your certificate, click the Add Custom Extension button in the Other x509 v3 Extensions (Advanced) field.
-
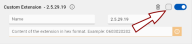
The Custom Extension form will appear in the dialog:
-
Enter a Name for the custom extension. This value is for informational purposes only.
-
Enter the custom extension's object identifier (OID Object identifier. Globally unique identifiers standardized by the International Telecommunication Union. OIDs are represented as a series of numbers separated by dots (e.g., 2.5.29.37).) (e.g., 2.5.29.19).
-
Add the extension's content in hexadecimal format.
-
To mark an extension as critical, check the checkbox to the left of the toggle button.
-
To remove an extension, click the trash bin icon
 .
.
-
-
Click the Generate button.
The new key with the generated certificate is now displayed in the respective slot tile:
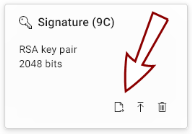
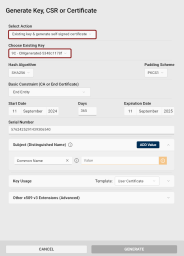
If you have a key stored on your token, you can generate corresponding certificate signing requests (CSRs) with it.
To generate a CSR using an existing key:
-
Go to the Certificates view in the left navigation pane.
-
Click the Generate CSR icon
 on the slot holding the existing key.
on the slot holding the existing key. -
The Generate Key, CSR or Certificate dialog opens, with the Existing key & generate CSR generation action and the key stored in the respective slot pre-selected.
Alternatively, you can click the Generate button in the top-right corner of the Certificates view.
In the Generate dialog, select Existing Key & generate CSR from the Select action drop-down.
-
Choose Existing Key: Use this drop-down to select other than the pre-selected key to generate the CSR for.
-
Hash Algorithm: Select the hash algorithm used to create a digital representation (hash) of the data within the CSR. This hash is used to create a digital signature that proves the integrity and authenticity of the CSR.
The available options are:
-
SHA1
-
SHA256 (default)
-
SHA384
-
SHA512
We recommend using SHA-256 (default) or higher.
-
-
Padding Scheme: If a RSA key type is selected, you can choose the padding A method used to add extra data to a hash before creating a digital signature with an RSA key to ensure that the resulting signature is unique and resistant to certain types of cryptographic attacks. scheme.
-
PKCS1 (Public Key Cryptography Standards #1)
-
PSS (Probabilistic Signature Scheme): PSS adds randomness to the padding process, making the signature more secure against certain types of cryptographic attacks.
Important: PSS is considered more secure, but PSS-signed certificates may not be supported by older systems.
-
-
Subject (Distinguished Name): Add at least one Subject Distinguished Name component for your CSR.
-
Common Name is selected as default, but you can delete the value by clicking the Clear icon
 and select another option from the drop-down list.
and select another option from the drop-down list. -
Alternatively, you can type the attribute's long or short name or OID directly into the field.
-
Click the Add Value button to include additional attributes of your Subject Distinguished Name in the CSR.
-
-
Other x509 v3 Extensions (Advanced): If you need x509 v3 extensions to be added to your CSR:
-
Click the Other x509 v3 Extensions (Advanced) drop-down button.
-
The Subject Alternative Name (SAN) extension section will be displayed.
(If you want to add a custom extension to your CSR, see point 9.)
-
Click the toggle button
 to enable SAN in your CSR.
to enable SAN in your CSR. -
A checkbox will appear to the left of the toggle button. If checked, the extension will be marked as critical.
-
Click the Add SAN button for additional SAN entries. The number of SANs is not limited.
The available types of SANs are:
-
IP Address
-
DNS Name
-
Email
-
URI (Unique Resource Identifier)
-
UPN (User Principal Name)
Hover over the information icon to view example entries for each type.
-
-
-
To add custom extensions to your certificate, click the Add Custom Extension button in the Other x509 v3 Extensions (Advanced) field.
-
The Name field for the custom extension is for informational purposes only.
-
Enter the custom extension object identifier (OID Object identifier. Globally unique identifiers standardized by the International Telecommunication Union. OIDs are represented as a series of numbers separated by dots (e.g., 2.5.29.37).) (e.g., 2.5.29.19).
-
Add the extension content in hexadecimal format.
-
To mark an extension as critical, check the checkbox to the left of the toggle button.
-
To remove an extension, click the trash bin icon
 .
.
-
-
Click the Generate button.
The generated CSR has been added to the key in the respective slot.
If you have a key stored on your token, you can generate corresponding self-signed certificates with it.
To generate a self-signed certificate using an existing key:
-
Go to the Certificates view in the left navigation pane.
-
Click the Generate button in the top-right corner of the Certificates view.
-
The Generate Key, CSR or Certificate dialog opens, with the New Key & generate CSR action and the First available slot pre-selected.
-
Click the Select Action drop-down and select Existing key & generate self-signed certificate and select an existing key.
-
Hash Algorithm: Select the hash algorithm used to create a digital representation (hash) of the data within the self-signed certificate. This hash is used to create a digital signature that proves the integrity and authenticity of the certificate.
 Available options:
Available options:
-
SHA1
-
SHA256 (default)
-
SHA384
-
SHA512
We recommend using SHA-256 (default) or higher.
-
-
Padding Scheme: If a RSA key type is selected, you can choose the padding A method used to add extra data to a hash before creating a digital signature with an RSA key to ensure that the resulting signature is unique and resistant to certain types of cryptographic attacks. scheme.
-
PKCS1 (Public Key Cryptography Standards #1)
-
PSS (Probabilistic Signature Scheme): PSS adds randomness to the padding process, making the signature more secure against certain types of cryptographic attacks.
Important: PSS is considered more secure, but PSS-signed certificates may not be supported by older systems.
-
-
Basic Constraint (CA or End Certificate): Use this field to specify whether the certificate should be an end-entity certificate (default) or a Certificate Authority (CA) certificate.
 Available options:
Available options:
-
End Entity: Issues a leaf certificate for an end user, server, or device.
-
Certificate Authority with max depth of 0: Issues a CA certificate that can only issue end-entity certificates (no CA certificates).
-
Certificate Authority with max depth of 1-4: Issues a CA certificate that can issue one to four levels of subordinate CA certificates, in addition to end-entity certificates.
-
Certificate Authority with unlimited depth: Issues a CA certificate that can issue an unlimited number of subordinate CA certificates. This setting is typically used for root CAs or higher-level CAs that need the capability to create multiple levels of CA certificates below them.
Note: If you selected a CA certificate as the basic constraint, don't forget to specify appropriate key usage (see point 11). -
-
Set the self-signed certificate validity: Use the Start Date field along with the validity period defined in days, or set the Expiration Date directly.
-
Serial Number: Enter a decimal or hexadecimal number for the certificate's serial number, or use the automatically generated value.
-
Subject (Distinguished Name): Specify at least one Subject Distinguished Name component for your self-signed certificate.
-
Common Name is selected as default, but you can delete the value by clicking the Clear icon
 and select another option from the drop-down list.
and select another option from the drop-down list. -
Alternatively, you can type the attribute's long or short name or OID directly into the field.
-
Click the Add Value button to include additional attributes of your Subject Distinguished Name in the self-signed certificate.
-
-
Key Usage: Use this section to specify the intended purpose of the certificate. The User Certificate template is pre-selected.
You can select a template with pre-selected options, which you can edit, or choose the empty template to define the key usage from scratch.
Click the drop-down button
 on the right do display key usage and extended key usage options.
on the right do display key usage and extended key usage options.The available templates are:
-
 Certificate Authority: You can use this template as a starting point if you selected a CA certificate as the basic constraint (see point 10.)
Certificate Authority: You can use this template as a starting point if you selected a CA certificate as the basic constraint (see point 10.) -
 User Certificate (default)
User Certificate (default)
-
Empty
-
-
Other x509 v3 Extensions (Advanced): If you need x509 v3 extensions to be added to your certificate:
-
Click the Other x509 v3 Extensions (Advanced) drop-down button.
-
A list of most commonly used extensions will be displayed.
If you want to add a custom extension to your certificate, see point 16.
-
Click the toggle button
 to enable an extension in your certificate.
to enable an extension in your certificate. -
A checkbox will appear to the left of the toggle button. If checked, the extension will be marked as critical.
-
 Subject Alternative Name:
Subject Alternative Name:
-
IP Address
-
DNS Name
-
Email
-
URI (Unique Resource Identifier)
-
UPN (User Principal Name)
Hover over the information icon to view example entries for each type.
Click the Add SAN button for additional SAN entries. The number of SANs is not limited.
-
-
CRL Distribution Points:
Specify the HTTPS or LDAP endpoints' URLs where the Certificate Revocation List (CRL) can be accessed.
Click the Add CRL button for additional CRL distribution point entries. The number of entries is not limited.
-
Subject Key Identifier
This field is used to uniquely identify the certificate. Its value is typically the SHA-1 hash of the subject's public key.
If not enabled, the correct value will be automatically filled in during generation. You may enter your own value for testing purposes.
-
Authority Information Access:
This extension specifies the locations where information about the issuing Certificate Authority (CA) certificate can be found, typically HTTP or LDAP URIs.
Select the access method to retrieve information about the CA certificate and enter the corresponding value:
-
OCSP: Specify the URI for the Online Certificate Status Protocol (OCSP) responder, which checks the revocation status of the certificate.
-
CA Issuer: Specify the URI for the issuing CA’s certificate.
-
-
-
To remove an extension, click the trash bin icon
 .
.
-
-
To add custom extensions to your certificate, click the Add Custom Extension button in the Other x509 v3 Extensions (Advanced) field.
-
The Custom Extension form will appear in the dialog:
-
Enter a Name for the custom extension. This value is for informational purposes only.
-
Enter the custom extension's object identifier (OID Object identifier. Globally unique identifiers standardized by the International Telecommunication Union. OIDs are represented as a series of numbers separated by dots (e.g., 2.5.29.37).) (e.g., 2.5.29.19).
-
Add the extension's content in hexadecimal format.
-
To mark an extension as critical, check the checkbox to the left of the toggle button.
-
To remove an extension, click the trash bin icon
 .
.
-
-
Click the Generate button.
The key with the generated certificate is now displayed in the respective slot tile.
Crescendo Manager allows you to generate Secure Key Injection Secure Key Injection is a FIPS certification-compliant protocol that ensures data protection when importing private keys, OTP secrets, and management keys. (SKI) Transport key pairs for your tokens. These key pairs can then be used for secure transfer of secrets to your tokens in compliance with the Secure Key Injection protocol.
To generate a new SKI Transport Key for the selected token:
-
Go to the Certificates view in the left navigation pane.
-
Click the Generate button in the top-right corner of the Certificates view
-
From the Select action drop-down, select New key.
-
Choose Key Slot: In the drop-down menu, select SKI Transport Key. The Key Type field will be set to RSA 3072 automatically.
-
Key Name: The key name is a human-readable string used to identify the key. Use the randomly generated value or overwrite it.
Note:Knowing the key name is useful when you need to use the key directly, such as with the Cryptography Next Generation (CNG Cryptography Next Generation. A modern cryptographic API (Application Programming Interface) introduced by Microsoft as part of Windows to replace the older CryptoAPI. It provides a flexible and extensible framework for implementing cryptographic algorithms, key storage, and secure key management and supports a wide range of cryptographic operations, including encryption, decryption, hashing, and digital signatures.) application programming interface. See the simple PowerShell example below, which opens the key for further actions.
Copy[System.Security.Cryptography.CngKey]::Open($keyname, [System.Security.Cryptography.CngProvider]::MicrosoftSmartCardKeyStorageProvider) -
Click the Generate button. The new SKI Transport Key is now displayed as a new tile.
Exporting an SKI Transport Key
To copy the public part of an SKI Transport Key:
-
Click the SKI Transport Key tile.
-
Click Copy to Clipboard to copy and paste the public part of the SKI Transport Key into the desired application in PEM format.
-
Click Save to File to save the public part of the SKI Transport Key in PEM format to the selected destination.
What's Next
A generated SKI Transport Key can be used for encrypting secrets for Secure Key Injection with the SKI Wrapper tool.
Viewing, Copying and Exporting Certificate/CSR/Key Details
To view more details about a key or certificate stored in a slot, click on the slot tile.
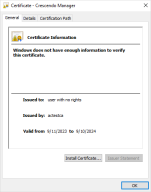
If you click a slot that contains a certificate, the native Windows Certificates dialog will open:
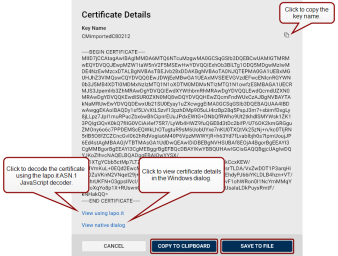
You can also click the certificate icon ![]() in the bottom-right corner of a tile to display certificate details in PEM format:
in the bottom-right corner of a tile to display certificate details in PEM format:
-
Click the View using lapo.it link to decode the key using the lapo.it ASN.1 JavaScript decoder online.
-
Click the copy button
 in the top-right corner to copy the key name.
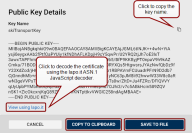
in the top-right corner to copy the key name. -
Click View native dialog to open the native Windows Certificates dialog.
-
Click Copy to Clipboard to copy the content of the certificate in PEM format to your clipboard.
-
Click Save to File to save the content of the certificate in PEM format to the selected destination.
If you click a slot tile that contains a key or a key and a CSR, the Public Key Details dialog will open.
-
Click the View using lapo.it link to decode the key using the lapo.it ASN.1 JavaScript decoder online.
-
Click the copy button
 in the top-right corner to copy the key name.
in the top-right corner to copy the key name. -
Click Copy to Clipboard to copy the content of the key in PEM format to your clipboard.
-
Click Save to File to save the public key in PEM format to the selected destination.
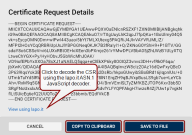
If a slot tile contains a key pair with a CSR, you can click the CSR icon ![]() in the bottom-right corner of the slot tile to view the CSR details in PEM format.
in the bottom-right corner of the slot tile to view the CSR details in PEM format.
-
Click the View using lapo.it link to decode the CSR using the lapo.it ASN.1 JavaScript decoder online.
-
Click Copy to Clipboard to copy the content of the CSR in PEM format to your clipboard.
-
Click Save to File to save the CSR in PEM format to the selected destination.
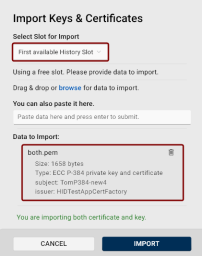
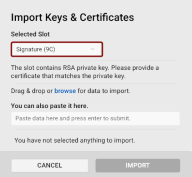
Importing Keys and Certificates
To import keys and certificates to your devices, you have several options to choose from:
The Import Keys & Certificates dialog will open with the chosen slot pre-selected:
Upload a key and/or certificate:
-
Use the drag & drop function or browse for the key/certificate file to import one or more files. Supported file formats include p12 and private key files (*.pem, *.der, *.key, etc.).
-
You can also simply paste the data in PEM format in the provided field.
-
Once you have provided the necessary data, click Import.
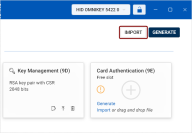
The Import Keys & Certificates will open with the selected slot filled in.
-
Use the drag & drop function or browse for the certificate file to import a matching certificate.
-
You can also simply paste the data in PEM format in the provided field.
-
Once you have provided the necessary data, click Import.
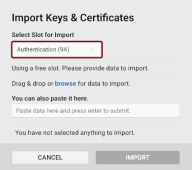
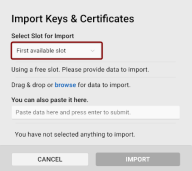
The Import Keys & Certificates dialog will open with the First available slot option pre-selected.
-
If necessary, select another slot to import a key and/or certificate to.
-
Use the drag & drop function or browse for the key/certificate file to import one or more files.
Supported file formats include p12 and private key files (*.pem, *.der, *.key, etc.).
-
You can also simply paste the data in PEM format in the provided field.
-
Once you have provided the necessary data, click Import.
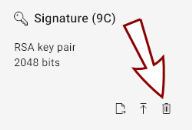
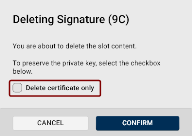
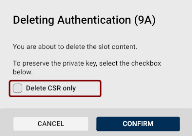
Deleting Keys, Certificates, and Certificate Signing Requests
To delete a key, certificate, or a CSR, click the trash-bin icon  in the bottom-right corner of the slot tile in the Certificates view.
in the bottom-right corner of the slot tile in the Certificates view.
A dialog will open, prompting you to confirm the deletion.
If the slot contains a certificate or a CSR, you can choose to keep the key and delete only the certificate/CSR by checking the checkbox: