Using the ADUC Snap-Ins
The ADUC snap-ins described below are part of the DigitalPersona AD Administration Tools component.DigitalPersona AD
For installation instructions, see DigitalPersona AD Administration Tools.
Users and Computers Snap-In
The DigitalPersona Users and Computers snap-in adds a new DigitalPersona tab to the User Properties page enabling additional administrative functions and adds a number of DigitalPersona commands to the user and computer object context menus.
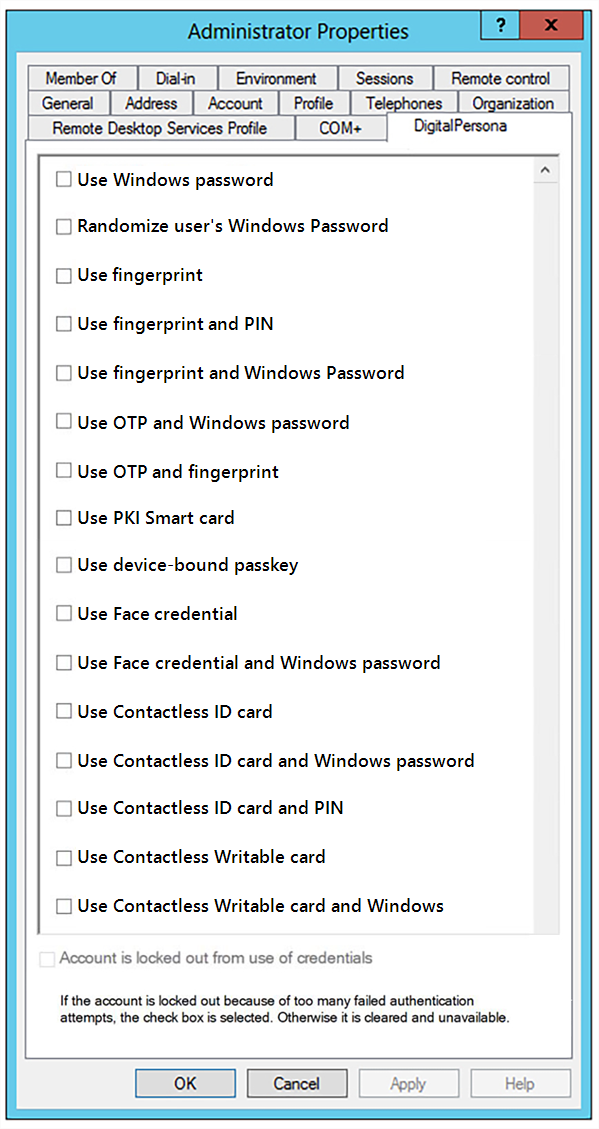
User Properties
he DigitalPersona Users and Computers snap-in provides the administrator with new DigitalPersona-specific user properties that define settings or behaviors that can be applied to a single user, multiple selected users and groups or OUs.
These properties are located on the Properties dialog for the selected Active Directory user(s), group(s) or OU(s).
To access the DigitalPersona Basic user properties:
-
In the Users and Computers console, open the Users folder.
-
Right-click on the desired user(s), group(s) or OU, select Properties and click the DigitalPersona tab.
-
Make any desired changes to the user properties, select Apply and then OK.
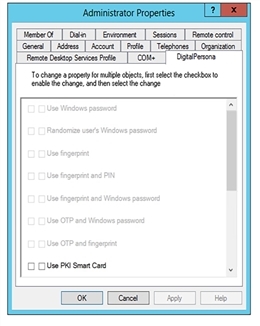
When making changes to multiple objects:
-
To disable a property setting for multiple users, select the leftmost checkbox for the setting and click Apply.
Do NOT select the second checkbox.
-
To enable a property setting for multiple users, select both checkboxes for the setting and click Apply.
Settings
Use Windows password
When this option is set, the user will not be subject to any logon policy from DigitalPersona AD.
Users will be able to logon with their password or PKI Smart Card as defined by the Windows logon settings.
By default this setting is turned off.
Randomize user's Windows Password
Enable this setting to randomize a user’s Windows Password. This will block them from using their Windows Password to verify their identity, and a fingerprint or other authorized and enrolled credential must be used instead.
When this option is set, DigitalPersona AD changes the user password to a random value when you click OK on this dialog box. This user will no longer be able to access any domain resources unless they have an alternative supported and enrolled credential - even computers where DigitalPersona AD software is not installed.
Use fingerprint
The user must verify their identity with a fingerprint credential in order to log on to Windows. No other credentials can be used, except for supported recovery options such as Self Password Recovery.
Use fingerprint and PIN
The user must provide a PIN whenever a fingerprint is used to log on, to unlock the computer or to change their Windows password. The fingerprint PIN option adds another level of security to logging on with a fingerprint.
Use fingerprint and Windows Password
The user must verify their identity with their fingerprint credential in addition to Windows authentication (a PKI Smart card or password according to the Windows policy setting).
Use OTP and Windows password
When this option is set, the user must provide a One-Time Password and their Windows password to log on.
Use OTP and fingerprint
The user must verify their identity with their fingerprint credential in addition to using the OTP credential.
Use PKI Smart card
When this option is set, the user must use a PKI Smart card to log on.
Use device-bound passkey
When this option is set, the user must use a passkey (device-bound or synced) to log on.
Use Face credential
When this option is set, the user must use a Face credential to log on.
Use Face credential and Windows password
The user must verify their identity with their Face credential in addition to Windows authentication (a PKI Smart card or password according to the Windows policy setting).
Use Contactless ID card
When this option is set, the user must use a Contactless ID card to log on.
Use Contactless ID card and Windows password
The user must verify their identity with a Contactless ID card in addition to Windows authentication (a PKI Smart card or password according to the Windows policy setting).
Use Contactless ID card and PIN
The user must verify their identity with a Contactless ID card and its associated PIN.
Use Contactless Writable card
When this option is set, the user must use a Contactless Writable card to log on.
Use Contactless Writable card and Windows password
The user must verify their identity with a Contactless Writable card in addition to Windows authentication (a PKI Smart card or password according to the Windows policy setting).
Account is locked out from use of fingerprint credentials
If the user account is locked out due to too many failed authentication attempts, this checkbox will be selected. Otherwise it will be unselected. Despite the mention of fingerprint credentials, other credentials may cause a lockout as well.
For instructions on unlocking an account, see Unlocking Accounts After Failed Logon Attempts.
Unlocking Accounts After Failed Logon Attempts
You can unlock an account that has been locked out of fingerprint authentication due to the user reaching the threshold number for failed authentication attempts. When an account is unlocked by an administrator, the account becomes immediately available for authentication from all computers, or after the next replication interval if there are multiple domain controllers.
The administrator can choose to set less strict lockout settings by reducing the lockout duration time or reducing the counter reset time.
-
In Active Directory for Users and Computers, right-click on the user name, and select Properties.
-
Click the DigitalPersona tab.
-
Clear the Account is locked out from use of credentials check box.
This check box is for unlocking accounts and cannot be checked by an administrator to lock an account. If the account is unlocked, the check box is disabled.
-
Click OK to close the dialog box and save the changes.
After the first 10 fingerprint authentication failures, each further attempt will be delayed by 20 seconds.
After a further 10 unsuccessful attempts, additional attempts will be delayed by 5 minutes.
A successful fingerprint authentication or a computer restart will reset the counter.
User Object Commands
Installation of DigitalPersona AD adds the following new commands to the context menu for a user in the Active Directory Users and Computers console.
Recover User
Enables recovery of the user's access to their Windows account through a one time access code available through a link on the Windows logon screen.
Delete License
Use this command to release the DigitalPersona license associated with this user back to the license pool.
This command will delete all of the selected user’s DigitalPersona credentials and other user data stored in Active Directory.
The license will be released within a few minutes after the user logs off from their computer.
The ability for a user to log on using their Windows password is not affected by deleting the license.
Due to cached credentials on the client computer, the user will still be able to use their enrolled credentials to log on to the computer after the license is deleted. But the cache will be cleared after the log on with any enrolled credential (except Windows password) and the user will need to re-enroll their credentials in order to continue to use them with the DigitalPersona software.
The first time a user tries to save a new Password Manager logon after their license has been deleted, they will receive an error, Data cannot be saved. If this persists, contact your administrator. The next time they attempt to do so, the message should not appear and the data should be saved successfully.
After a license has been deleted, a user’s first attempt to re-enroll their credentials through the user dashboard, or an administrator’s attempt to do so through the Attended Enrollment wizard, may fail. Closing and re-opening the user dashboard or Attended Enrollment wizard should resolve the issue.
Delete Credentials
Use this command to delete specific enrolled credentials for selected users. A dialog displays where you can select the credentials to be deleted. This does not release the associated DigitalPersona user license.
Group Properties
What is AD Group-based Logon Policy?
An AD group-based Logon Policy is a DigitalPersona Logon Policy which can be configured for any Active Directory Group and will apply on all users belonging to the AD Group.
This Logon Policy will apply only to AD Users which belongs to this AD Group but will not apply to AD computers which belong to the AD Group. In this respect, it will be acting as a User Level policy. The policy will apply to Windows Logon/Unlock only and will not apply to Session Policies (for example, for Password Manager), during credential enrollment or for the Web Authentication UI.
The following logic is used to resolve an AD group-based Logon Policy:
-
Based on a user name, we will resolve all AD Groups that the user belongs to.
-
For every AD group we will check if an AD group-based policy is set.
-
If an AD group-based policy is set, we will apply it to the user.
Ambiguity of AD Group-based Logon Policy
A user can belong to multiple AD Groups, so theoretically they can have multiple AD group-based Logon Policies applied—which could create a conflict. The following process is used to resolve this potential conflict, by combining all policies applied to the user.
-
Collect all Logon Policies assigned to the AD Groups that the user belongs to.
-
Combine those Logon Policies and to create the user's Logon Policy.
For example, if a user belongs to AD Groups A and B where group A has a Logon Policy of Fingerprint+Password assigned to it and group B has a Logon Policy of OTP+Password assigned to it, then the user's Logon Policy applied will be Fingerprint+Password OR OTP+Password.
Configuring AD Group-based Logon Policy
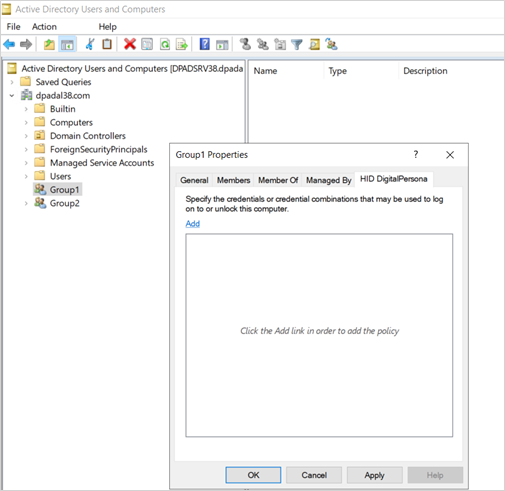
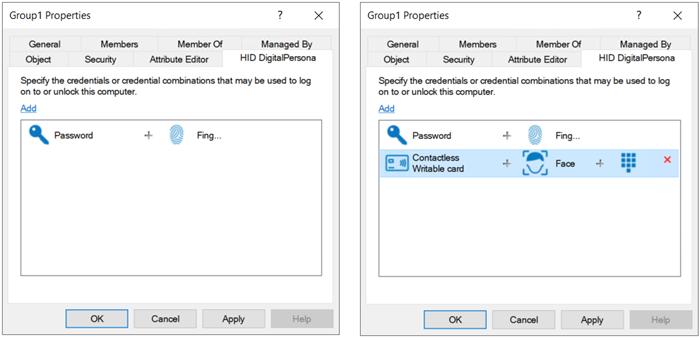
The DigitalPersona Users and Computers snap-in provides the administrator with DigitalPersona-specific AD group-based properties that define the Logon Policies that will be applied to a selected group.
To create a DigitalPersona AD group-based policy:
-
In the Users and Computers console, navigate to a folder where the desired group is located.
-
Right-click on the desired group, select Properties and click the DigitalPersona tab.
-
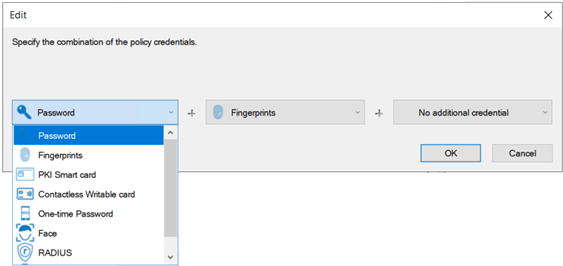
In the HID DigitalPersona [group] Properties dialog, click Add to display the Edit dialog.
-
In the Edit dialog, select the credentials and/or credential combinations from the drop-down list that will be allowed for authentication during Windows logon.
When selecting credentials to be used for the Logon Policy, the first credential must be a Primary credential. Additional (optional) credentials may be either Primary or Secondary credentials.
You can add multiple combinations to the list which will be treated as OR policies, i.e. in the image below on the right, allowed credential combinations would be Password + Fingerprint OR Contactless Writable Card + Face + PIN.
-
After adding all required credentials and/or credential combinations, click Apply. Then click OK.
To edit a credential or credential combination:
-
Click the credential or credential combination and edit it using the drop-down lists provided.
-
Click Apply.
To delete a credential or credential combination:
-
Click on the X that appears in the upper-right corner of the item.
-
Click Apply.
User Query Snap-In
The DigitalPersona User Query Snap-in is a component within the DigitalPersona AD Administration Tools.
These tools are a separate installation and are located in the DigitalPersona AD Administration Tools folder of your product package. This tool provides a means for the administrator to query the DigitalPersona AD user database for information about DigitalPersona AD users and to perform certain operations and to set values associated with a selected user.
It has three separate implementations, as described in the following topics:
The User Query Tool must be installed on a computer running a licensed copy of DigitalPersona AD Workstation, and the logged on user must have domain administrator privileges.
Once installed, the Interactive dialog-based application can be run from the Start menu by clicking DigitalPersona, User Query Tool.
ActiveX Control
The ActiveX control provides the most functionality, including performing operations against the user record and setting certain flags and values. The dialog-based and CLI applications are reporting tools only.
Examples of the types of query information that can be accessed by the ActiveX control are:
-
Number of installed licenses
-
Number of licenses used
-
Number of enrolled credentials for each user
-
Types of credentials enrolled for each user
-
Number of users accessing managed logons
-
Dates of first and last fingerprint enrollment
Additionally, certain operations may be performed against the DigitalPersona user database through the ActiveX control. For example:
-
Lock user account
-
Set user logon policy
-
Delete specific authentication credentials
-
Delete user Secrets
The DigitalPersona AD User Query Tool ActiveX control provides two interfaces that can be implemented through Visual Basic or Javascript.
IDPUserQueryControlInterface
This interface is used to return licensing information and create an instance of the DPUserControl object described in the next section.
[ object,
uuid(4AC9BCDA-7C6F-4919-A885-D533CBA447DF),
dual,
nonextensible,
helpstring("IDPUserQueryControl Interface: "),
pointer_default(unique)
]
valuesActiveX control
interface IDPUserQueryControl : IDispatch
{
[propget, id(1), helpstring("Returns number of licenses installed.")]
HRESULT NumberOfLicensesInstalled([out, retval] LONG* pVal);
[propget, id(2), helpstring("Returns number of licenses used.")]
HRESULT NumberOfLicensesUsed([out, retval] LONG* pVal);
[id(3), helpstring("Creates an instance of DPUserControl object based on user
DN.")]
HRESULT GetUser([in] BSTR UserDN, [out,retval] IDispatch** ppUser);
};IDPUserControl
The IDPUserControl is used to get or set a number of different user properties.
[
object,
uuid(C6AAB663-EA2A-4195-940F-1C56C5736924),
dual,
nonextensible,
helpstring("IDPUserControl Interface: "),
pointer_default(unique)
]
interface IDPUserControl : IDispatch{
[propget, id(1), helpstring("Returns a flag that indicates if the account
is locked because of intruder detection.")]
HRESULT IsAccountLocked([out, retval] VARIANT_BOOL* pfIsAccountLocked);
[propput, id(1), helpstring("Sets a flag that indicates if the account is
locked because of intruder detection.")]
HRESULT IsAccountLocked([in] VARIANT_BOOL fIsAccountLocked);
[propget, id(2), helpstring("Returns a user account control value.")]
HRESULT AccountControl([out, retval] LONG* pVal);
[propput, id(2), helpstring("Sets a user account control value.")]
HRESULT AccountControl([in] LONG newVal);
[propget, id(3), helpstring("Returns a user logon policy value.")]
HRESULT LogonPolicy([out, retval] LONG* pVal);
[propput, id(3), helpstring("Sets a user logon policy value.")]
HRESULT LogonPolicy([in] LONG newVal);
[propget, id(4), helpstring("Returns a flag that indicates if the specific
authentication token is enrolled.")]
HRESULT IsTokenEnrolled([in] BSTR TokenID, [out] VARIANT_BOOL*
pfIsTokenEnrolled);
[propget, id(5), helpstring("Returns a flag that indicates fingerprints
enrolled mask.")]
HRESULT FingerprintMask([out, retval] LONG* pVal);
[propget, id(6), helpstring("Returns user recovery password.")]
HRESULT RecoveryPassword([in] BSTR EncryptedPassword, [out, retval]
BSTR* pVal);
[id(7), helpstring("Deletes specific authentication token credentials.")]
HRESULT DeleteToken([in] BSTR TokenID);
[id(8), helpstring("Deletes enrolled fingerprints.")]
HRESULT DeleteFingerprints(void);
[id(9), helpstring("Deletes user Secrets.")]
HRESULT DeleteSecrets(void);
[id(10), helpstring("Returns date and time of first fingerprint
enrollment.")]
HRESULT FingerprintFirstEnrollmentTime([out, retval] DATE* pVal);
[id(11), helpstring("Returns date and time of last fingerprint
enrollment.")]
HRESULT FingerprintLastEnrollmentTime([out, retval] DATE* pVal);
[propget, id(12), helpstring("Returns a flag that indicates if the specific
authentication token is enrolled.")]
HRESULT IsTokenEnrolledEx([in] BSTR TokenID, [in] BSTR Prefix, [out]
VARIANT_BOOL* pfIsTokenEnrolled);
[propget, id(13), helpstring("Returns a flag that indicates if license
taken by this user.")]
HRESULT IsLicenseTaken([out, retval] VARIANT_BOOL* pfIsLicenseTaken);
[id(14), helpstring("Clear license by deleting all DigitalPersona data for
this user.")]
HRESULT ClearLicense(void);
};Sample VB Script
This is a sample of a VB script that returns the date and time of the first and last fingerprint enrollments for a user.
Dim objUser
Set objQueryControl = CreateObject("DPUserQuery.DPUserQueryControl")
Set objUser = objQueryControl.GetUser("cn=testuser,CN=Users,DC=testdomain,DC=COM")
wscript.echo objUser.FingerprintFirstEnrollmentTime
wscript.echo objUser.FingerprintLastEnrollmentTimeInteractive Dialog-based Application
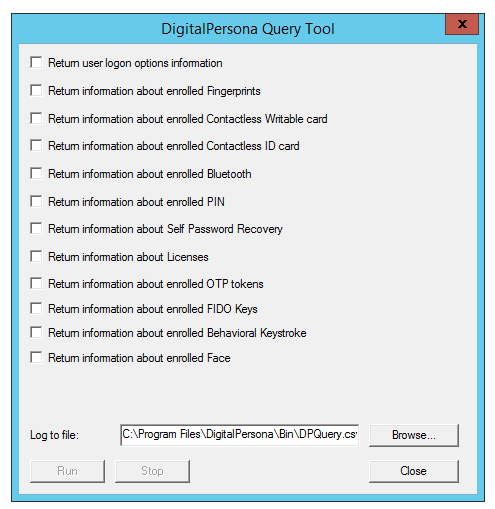
To run the interactive dialog-based application:
-
From the Start menu, select All Programs, DigitalPersona, and then User Query Tool.
-
In the application dialog that displays, select the type of information you would like to display.
-
Optionally, Browse to the location where you want to save the resulting log file.
-
Click Run .
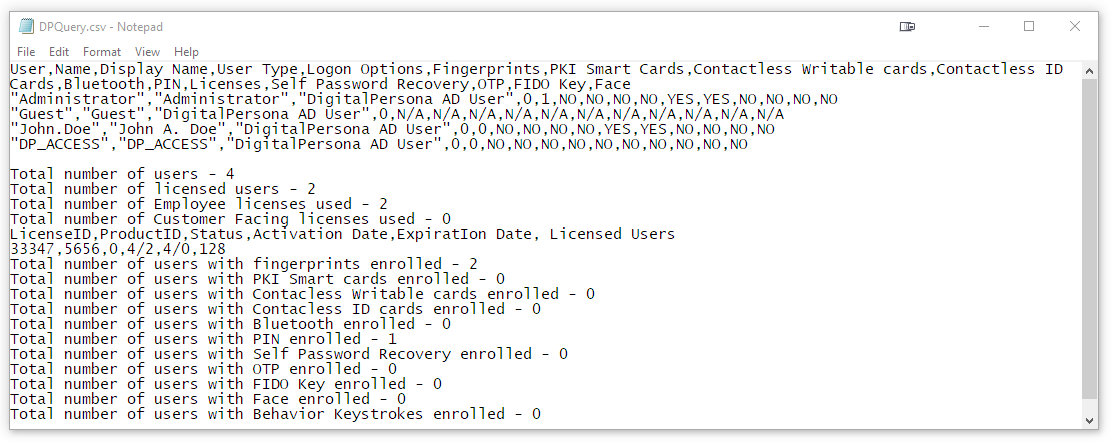
The file is saved as a .csv file with the default name of DPQuery.csv, which can be opened in Notepad or programs such as Microsoft Excel and other spreadsheet programs.
DPQuery.csv Format
The file resulting from the use of either the Interactive User Query Tool described above, or the command line interface User Query Tool, is illustrated below and described more fully in the table that follows.
| Column | Description |
|---|---|
|
User Name |
Name of the user being reported against. |
|
Display Name |
Display Name of the user being reported against. |
|
User Type |
Type of user - that is, Administrator or |
|
Logon Options |
0 - No logon option is set. 1 - User provides only Windows credentials to log on. 2 - Randomize user’s Windows Password. 4 - User must provide Fingerprint and PIN to log on. 8. - Account is locked out from use of fingerprints credentials. |
|
Fingerprints |
Number of fingerprints enrolled by the user. |
|
Contactless Writable Cards |
YES or NO. Indicates if this credential has been enrolled by the specified user. |
|
Contactless ID Cards |
YES or NO. Indicates if this credential has been enrolled by the specified user. |
|
Bluetooth |
YES or NO. Indicates if this credential has been enrolled by the specified user. |
|
PIN |
YES or NO. Indicates if this credential has been enrolled by the specified user. |
|
Licenses |
YES or NO. Indicates if a DigitalPersona User license is being utilized by the specified user. |
|
Self Password Recovery |
YES or NO. Indicates if the Self Password Recovery questions have been answered by the specified user. |
|
OTP |
YES or NO. Indicates if this credential has been enrolled by the specified user. |
|
Device-bound passkey |
YES or NO. Indicates if this credential has been enrolled by the specified user. |
|
Face |
YES or NO. Indicates if this credential has been enrolled by the specified user. |
Additionally, the following totals are provided at the end of the file:
-
Total number of users
-
Total number of Employee licenses used
-
Total number of Customer Facing licenses used
-
License ID, Product ID, Status, Activation Date, Expiration Date, Licensed Users
-
Total number of users with fingerprints enrolled
-
Total number of users with Contactless Writable cards enrolled
-
Total number of users with Contactless ID cards enrolled
-
Total number of users with Bluetooth enrolled
-
Total number of users with PIN enrolled
-
Total number of users with Self Password Recovery enrolled
-
Total number of users with OTP enrolled
-
Total number of users with device-bound passkeys enrolled
-
Total number of users with Face enrolled
Command Line Utility
The User Query Tool command line utility must be run from an elevated command prompt.
To run the User Query Tool command line utility:
-
Open an elevated command prompt by right-clicking any Command Prompt shortcut on the Windows Start menu (located by default in the Accessories folder) and selecting Run as administrator.
-
In the Command Prompt window, enter DPQuery.exe using the following syntax and parameters.
Syntax
DPQuery.exe [-noui] [-dn=”BaseDN”] [-out=”FileName”] [-ac] [-fp] [-cw] [-ci]
[-bt] [-pin] [-lic] [-rec]| Parameter | Description |
|---|---|
|
-noui |
Run utility silently with no graphical interface, writing results to the DPQuery.csv file in the [Installation path]\Bin folder (where the default location would be C:\Program Files\DigitalPersona\Bin). If -noui is not used, the Interactive Dialog-based Application displays. |
|
-dn= “BaseDN” |
Sets the Distinguished Name of the search base for the query. If missing, the DN of the domain name that the computer belongs to will be used as the search base. |
|
-out=”FileName” |
Identifies the path and file name for the output log file. If missing, the file DPQuery.csv will be created in the directory containing the utility. |
|
-fp |
Add information about the number of fingerprints enrolled for each user in a query. |
|
-ac |
Add information about user account control flags like password randomization. |
|
-cw |
Add information about Contactless Writable cards enrolled for each user in a query. |
|
-ci |
Add information about Contactless ID cards enrolled for each user in a query. |
|
-bt |
Add information about Bluetooth credentials enrolled for each user in a query. |
|
-pin |
Add information about PINs enrolled for each user in a query. |
|
-lic |
Add information about licenses utilized for each user in a query. |
|
-rec |
Add information about Self Recovery Password enrolled for each user in a query. |
|
-otp |
Add information about OTP credentials enrolled for each user in a query. |
|
-utf |
Add information about device-bound passkey credentials enrolled for each user in a query. |
|
-face |
Add information about Face credentials enrolled for each user in a query. |
Examples
Return license information on all users.
DPQuery.exe –noui –dn=”CN=Users,DN=DigitalPersona,DN=com” –licReturn information about users in the Users OU of the DigitalPersona domain, and includes account control flags (defined above) and information about enrolled fingerprints
DPQuery.exe –noui –dn=”CN=Users,DN=DigitalPersona,DN=com” –ac –fpReturn information about users in the Users OU of the DigitalPersona domain, and includes information about enrolled Contactless Writable and Contactless ID cards, and One-Time Password credentials
DPQuery.exe –noui –dn=”CN=Users,DN=DigitalPersona,DN=com” –cw -ci -otp