GPMC/GPOE Extensions
DigitalPersona AD Server and its associated clients use GPMC/GPOE extensions, installed under the Software Settings and Administrative Templates nodes, to link product policies and settings to Active Directory containers.
DigitalPersona creates a number of extensions that are visible in the Group Policy Management Console (read-only) and the Group Policy Management Editor.
The following sections describe these extensions from the viewpoint of the GPO Editor, since that is where they can be enabled and configured or disabled.
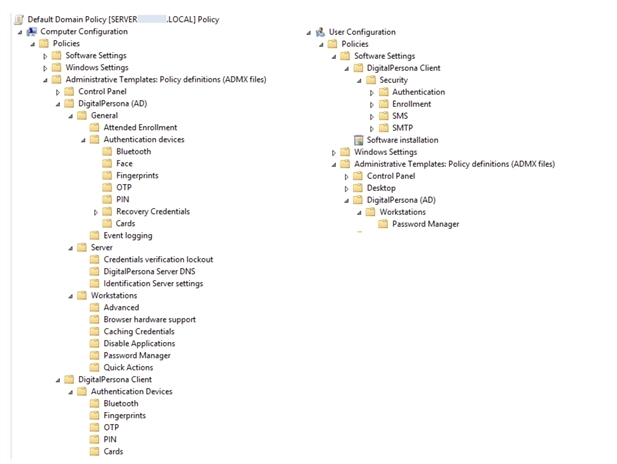
There are three child nodes under the Computer Configuration and User Configuration parent nodes in the Group Policy Object Editor namespace:
-
Software Settings
-
Windows Settings
-
Administrative Templates
DigitalPersona settings are located in the Software Settings and Administrative Templates nodes.
-
The Software Settings node contains extension snap-ins that extend the Computer Configuration node and the User Configuration node.
-
The Administrative Templates node contains registry-based policy settings, and are extended by using administrative template (.adm/.admx) files.
These DigitalPersona policies and settings are described in detail in Policies and Settings.
The Group Policy Object Extensions and the Administrative Templates are installed automatically as part of the DigitalPersona AD Administrative Tools.
By default, Administrative Templates are installed only into a local PolicyDefinitions store.
To install Administrative Template into a Central Store, see Installing Administrative Templates into a Central Store.
Adding an administrative template to a container applies the DigitalPersona policies and settings to the computers and users in that container. For instructions on installing the client Administrative Template locally, see Installing the Client Administrative Templates Locally.
Additional extensions or templates may be provided as new components are released, and will be specified in the Readme.txt file for each component.
Group Policy Object Extensions
DigitalPersona uses the following Group Policy Object Extensions under the Software Settings node. They are installed automatically as part of the DigitalPersona Administrative Tools.
DigitalPersona Client
| Node|Subnode | Setting | |
|---|---|---|
|
Security |
None (Used for license management) |
|
|
Authentication
|
Logon Authentication Policy |
|
|
Enhanced Logon Authentication Policy |
||
|
Session Authentication Policy |
||
|
Kiosk Session Authentication Policy |
||
|
Enrollment |
Enrollment Policy |
|
|
SMS |
SMS Configuration |
|
|
SMTP |
SMTP Configuration |
|
|
Kiosk Administration |
Allow automatic logon using Shared Kiosk Account |
|
|
Logon/Unlock with Shared Account Credentials |
||
|
Prevent users from logging on outside of a Kiosk session |
||
|
Kiosk Workstation Shared Account Settings |
||
|
Kiosk Unlock Script |
||
DigitalPersona Server
| Node | Setting | |
|---|---|---|
|
Licenses |
None (Used for license management) |
|
Administrative Templates
DigitalPersona uses the following Administrative Templates installed under the Computer Configuration/Policies/Administrative Templates node. They are installed automatically as part of the DigitalPersona AD Administrative Tools.
By default, Administrative Templates are installed only into a local PolicyDefinitions store. To install Administrative Template into a Central Store, see Installing Administrative Templates into a Central Store.
Creates a root-level folder and categories for all DigitalPersona products, and if not already present, is installed automatically with any DigitalPersona product.
Creates these settings under the following node:
Computer Configuration/Policies/Administrative Templates/DigitalPersona (AD)/General
| Subnode | Setting | ||
|---|---|---|---|
|
Attended Enrollment |
Security officer authentication |
||
|
Require enrolling or omitting each credential |
|||
|
Authentication devices |
Bluetooth |
||
|
Fingerprints |
|||
|
OTP |
|||
|
PIN |
|||
| Recovery Credentials |
Recovery Questions |
Enable Recovery Questions |
|
|
Allow Recovery Questions for Windows Logon |
|||
|
Self Password Reset |
Allow users to reset their Windows passwords |
||
|
Path to DigitalPersona Secure Token Server (STS) |
|||
|
Allow One-time access code for Windows Logon |
|||
|
Cards |
Contactless Card Usage |
||
| Allow enrolling only one contactless card per user | |||
|
Lock the computer upon card or device-bound passkey removal |
|||
| Allow the use of Contactless ID cards as a single (Primary) credential | |||
|
Contactless (RF) technologies |
|||
|
Event logging |
Level of detail in event logs |
||
Creates these settings under the following node:
Computer Configuration/Policies/Administrative Templates/DigitalPersona
| Subnode | Setting | ||
|---|---|---|---|
|
Workstations |
Advanced |
Always show the Windows password tile in sign-in options | |
|
Do not launch the Getting Started wizard upon logon |
|||
|
Add user-level credentials to Other User sign-in options |
|||
|
Identification Server domain |
|||
|
Compatibility with Microsoft Fingerprint support |
|||
|
Allow DigitalPersona client to use DigitalPersona Server |
|||
|
Show Taskbar icon |
|||
|
Allow VPN-less access |
|||
|
Browser hardware support |
Allow Localhost Loopback |
||
|
Localhost Loopback Origins |
|||
|
Caching Credentials |
Cache user data on local computer |
||
|
Maximum size of identification list |
|||
| Disable Applications |
Prevent Password Manager from running |
||
|
Quick Actions |
Credential |
||
|
Ctrl+Credential |
|||
|
Shift+Credential |
|||
Creates these settings under the following node:
Computer Configuration/Policies/Administrative Templates/DigitalPersona (AD)/Workstations/Password Manager
| Setting |
|---|
|
Authenticate other user for password manager operations |
|
Display password complexity popup |
Creates these settings under the following node:
User Configuration/Policies/Administrative Templates/DigitalPersona (AD)/Workstations/Password Manager
| Setting |
|---|
|
Allow creation of personal logons |
|
Managed logons |
Creates these settings under the following node:
Computer Configuration/Policies/Administrative Templates/DigitalPersona (AD)/Workstations
| Setting |
|---|
|
One Touch Lock |
Creates these settings under the following node:
User Configuration/Policies/Administrative Templates/DigitalPersona/Server
| Subnode | Setting |
|---|---|
|
Credentials verification lockout |
Allow users to unlock their Windows account using DigitalPersona Recovery Questions |
|
Account lockout duration |
|
|
Reset account lockout counter after |
|
|
Account lockout threshold |
|
|
DigitalPersona Server DNS |
Automated site coverage by DigitalPersona Server Locator DNS SRV records |
|
Refresh interval of DigitalPersona Server DNS records |
|
|
Sites covered by DigitalPersona Server Locator DNS SRV records |
|
|
Priority set in DigitalPersona Server Locator DNS SRV records |
|
|
Weight set in DigitalPersona Server Locator DNS SRV records |
|
|
Register DigitalPersona Server Locator DNS SRV records for domain |
|
|
Dynamic registration of DigitalPersona Server Locator DNS SRV records |
Creates these settings under the following node:
User Configuration/Policies/Administrative Templates/DigitalPersona/Server
| Subnode | Setting |
|---|---|
|
Identification Server settings
|
Perform fingerprint identification on server |
|
Restrict identification to a specific list of users |
Implementation Guidelines
Before you add any Administrative Templates to your GPOs, give some thought to your Active Directory structure, where GPOs are placed, and which GPOs the Administrative Templates should be added to.
Policy configuration needs will vary from network to network and specific policy recommendations are beyond the scope of this documentation. You may want to refer to Microsoft’s documentation on Group Policy Object configuration for more information.
Organizational Units and GPOs
Although the use and configuration of organizational units and GPOs varies widely among corporations, we have provided some general guidelines for structuring Active Directory organizational units.
There are two key factors in deciding how to structure your network:
-
How you group your users and computers, and
-
Where the DigitalPersona AD GPOs are set.
For example, if users and computers are to be grouped according to authentication policies, you should group them into separate OUs (Organizational Units) and then set specific GPOs for each OU.
However, when authentication policies within organizational units vary, as they often do among department heads and subordinates, then you should group your users and/or computers into child organization units reflecting the necessary authentication needs.
Structuring your organizational units based on authentication policies is the easiest way to administer DigitalPersona:
-
Plan your network structure by identifying the settings you intend to configure.
-
Determine whether to apply the settings to all users and computers in a site or domain, or just to the users and computers in an organizational unit.
-
Create the organizational units required to implement your design.
-
Add the respective users and computers to the organizational units.
GPO Behavior
Here are a few guidelines to keep in mind when configuring DigitalPersona GPOs.
-
If a GPO setting is not configured, the default value set in the software is used.
-
If a superior (higher-level) GPO has a value for a setting and a subordinate GPO has a conflicting value for that setting, the setting in the subordinate is used.
-
If a GPO has a value for a setting and a subordinate (lower-level) container has the GPO setting with no value, the setting in the superior (high-level) GPO is used.
-
GPOs can only be applied to the three Active Directory containers: sites, domains and organizational units; not to users or computers.
-
A single GPO can be applied to one or more containers.
-
A GPO affects all users and computers in the container, and subcontainers, it is applied to.
The DigitalPersona GPO settings apply only to computers with DigitalPersona software installed on them. In very basic Active Directory deployments, one can simply make a specific DigitalPersona GPO, linked at the domain, and set the DigitalPersona Server and DigitalPersona Workstation settings here for all users and computers alike.
Installing the Client Administrative Templates Locally
For local administration of a DigitalPersona AD Workstation or Kiosk, the following Administrative Templates can be added to the local policy object of any computer running the client by using the Microsoft Management Console (MMC) Group Policy Editor:
-
DPCA_AD_General.admx
-
DPCA_AD_DesktopApps.admx
-
DPCA_AD_PasswordManager.admx
-
DPCA_AD_OneTouchLock.admx
To add the Administrative Templates locally:
-
On the Start menu, click Run, type gpedit.msc and press Enter to launch the Group Policy Editor.
-
Right-click the Administrative Templates folder and select Add/Remove Templates on the Administrative Templates folder shortcut menu.
-
Click the Add button on the Add/Remove Templates dialog box and then locate and select the required Administrative Templates from the default administrative templates directory.
-
Click Close.
Installing Administrative Templates into a Central Store
Microsoft Windows allows storing Administrative Templates either in a:
-
Local store - (%SystemRoot%\PolicyDefinitions)
-
Central Store - (%SystemRoot%\SYSVOL\sysvol\%UserDomain%\Policies\PolicyDefinitions)
Administrative Templates installed in the Central Store are automatically replicated to all Domain Controllers in the domain. For more details, see the Microsoft article Create and manage central store.
If your company use a Central Store as a default place to store all Administrative Templates, then you may want to use it for DigitalPersona Administrative Templates as well.
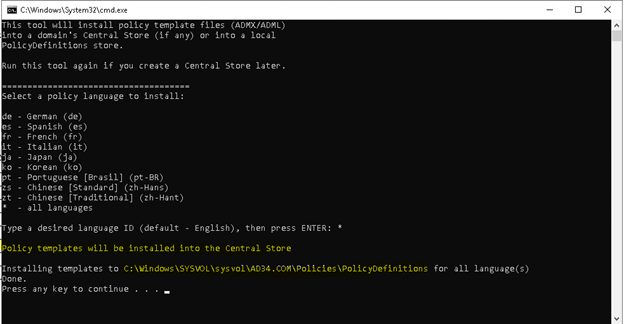
To install DigitalPersona Administrative Templates into the Central Store, you may either copy the ADMX/ADML files manually, like any other ADMX/ADML file, or you can use a DeployTemplates.bat script located within your DigitalPersona software package at the following location:
DigitalPersona ADServer\Server Tools\Policy Templates
When you run the script, it will attempt to detect whether you currently use the Central Store or a local store.
If the script discovers a "%SystemRoot%\SYSVOL\sysvol\%UserDomain%\Policies\PolicyDefinitions" folder, it will assume that you use Central Store, otherwise it will assume that you use a local store.
The script will also ask you to choose which language to install for DigitalPersona Administrative Templates.
Running the file will display the following interface:
-
Select a policy language to install by typing the two-letter abbreviation for a language, or type an asterisk (*) to install all languages.
-
Press Enter.
The script then installs administrative templates and selected language files into the detected policy definitions store.
Later, if you switch from local store to a Central Store, or vice versa, run the DeployTemplates.bat script again to install DigitalPersona Administrative Templates to the selected store.
-
Press Enter.
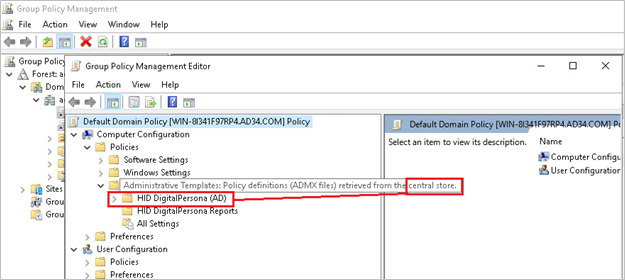
You can verify that the policies have been copied to the domain’s Central Store by ensuring that the GPME indicates that the Policy definitions have been ‘retrieved from the central store’.