Setting up the DigitalPersona Event Collector
The DigitalPersona Event Collector gathers events generated by DigitalPersona software and brings them into a single event archive suitable for further analysis with a business intelligence (BI) tools.
Requirements
The DigitalPersona Event Collector requires the following components:
-
Windows Event Collector (WEC) service – to collect events from multiple computers in a domain.
This service is a Microsoft Windows built-in feature.
-
Microsoft SQL Server - to store the collected event data.
Installation and Configuration
-
Install and configure a new Microsoft SQL Server instance as described Installing Microsoft SQL Server for Event Collector.
-
Configure WEC, create a DigitalPersona Event Collector database and start to collect events by running the Import-Events cmdlet.
Querying and Analyzing Event Data
After the DigitalPersona Event Collector is configured, it creates a number of useful queries that allow you to immediately start analyzing the most important events. Many of these queries are used in the Microsoft Power BI reporting templates provided with the DigitalPersona Reports package. You can also add your own custom queries and reporting templates.
Installing Microsoft SQL Server for Event Collector
DigitalPersona Reports uses a Microsoft SQL Server database to store collected DigitalPersona events and Microsoft SQL Native Client to connect to the server.
Install Microsoft SQL Server
-
Download Microsoft SQL Server. You can download it from https://www.microsoft.com/en-us/sql-server/sql-server-downloads.
-
Run the Microsoft SQL Server installer and create a new SQL Server instance. Choose the default instance name ("mssqlserver" for a full Microsoft SQL Server or "sqlexpress" for Microsoft SQL Express), or create your own.
If you create your own, take note of the name as you will need to use it in later steps.
Enable Remote Access to Microsoft SQL Server
-
Create firewall rules for Microsoft SQL Server, opening the following ports:
-
TCP port 1433 for the SQL Server default instance
-
UDP port 1434 for the SQL Server Browser Service
CopyIn Powershell
New-NetFirewallRule -DisplayName "SQLServer default instance" -Direction Inbound -LocalPort 1433 -Protocol TCP -Action Allow
New-NetFirewallRule -DisplayName "SQLServer Browser service" -Direction Inbound -LocalPort 1434 -Protocol UDP -Action AllowCopyFrom the command line
netsh advfirewall firewall add rule name = SQLServerInstance dir = in protocol = tcp action = allow localport = 1433 remoteip = localsubnet profile = DOMAIN
netsh advfirewall firewall add rule name = SQLServerBrowser dir = in protocol = udp action = allow localport = 1434 remoteip = localsubnet profile = DOMAINFor further details, see https://docs.icrosoft.com/en-us/sql/sql-server/install/configure-the-windows-firewall-to-allow-sql-server-access
-
-
Open SQL Server Configuration Manager.
-
In the SQL Server services section, configure the SQL Server Browser service to run automatically, and then start it.
-
In SQL Server Network Configuration/Protocols for [instance name], enable the TCP/IP protocol.
Installing the Microsoft SQL Server Native Client
-
If the Event Collector computer hosts an Microsoft SQL Server, it already has an Microsoft SQL Server Native Client installed and you can skip this section.
-
If the Event Collector machine does not host an SQL Server but connects to a remote one, an Microsoft SQL Server Native Client must be installed.
-
Open a Microsoft SQL Server 2012 SP4 Feature Pack from https://www.microsoft.com/en-us/download/details.aspx?id=56041.
-
Click Download to reveal a list of components.
-
Select sqlncli.msi and click Next to start the download.
Note: There are two sqlncli.msi files listed - the smaller one is 32-bit, the larger one is 64-bit. Choose the one matching your platform (in most cases the larger 64-bit one). -
Run the file sqlncli.msi to install the SQL Native Client.
Creating a DigitalPersona Event Collector Database
The `Import-Events` PowerShell cmdlet is a central component of the DigitalPersona event collection. To create a DigitalPersona Event Collector database, run the Import-Events cmdlet using an account with dbadmin privileges.
The cmdlet will attempt to locate and upgrade any existing DigitalPersona Events database. It is recommended that you back up your existing events database before running the cmdlet.
The current version of the SQL database is 2.0. It is NOT backward compatible with older DigitalPersona Reports schemas. DO NOT ATTEMPT to install them both on the same machine.
Prerequisites and System Requirements
-
A dedicated event collector computer joined to the domain
-
The Windows logon used to setup the event collector should have permission to create GPOs on the domain controller.
-
A Microsoft SQL Server instance, installed either on the collector computer, or on a separate database server.
-
Ensure that you can login with the database administrator role in order to create the required database. Windows Integrated Authentication is the recommended logon protocol.
Installation
The Import-Events cmdlet and its supporting files are supplied with the DigitalPersona Reports package. It can be copied to any directory and does not require special installation.
-
Copy the $\Collector\Import-Events directory to the computer used as an event collector.
-
Open the PowerShell administrative console.
The Windows user should have enough privileges to create GPO on a Domain Controller.
-
If using Windows Integrated Authentication (WIA) for Microsoft SQL Server, then the same Windows account should also have an Microsoft SQL logon with the dbadmin role.
-
If using SQL authentication (not recommended), ensure that you have the proper dbadmin credentials.
-
-
Navigate to the installation directory.
-
Make sure your PowerShell execution policy allows you to run scripts. To set the proper execution policy, run: PS> Set-ExecutionPolicy -ExecutionPolicy RemoteSigned
See the following article for details: https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.security/set-executionpolicy.
-
You can also run Get-Help $pwd\Import-Events.ps1 to view available cmdlet parameters. Further information is also contained in the Cmdlet Parameters.
Configuration
-
In the same PowerShell administrative console, run the Import-Events.ps1 cmdlet for the first time with initial parameters including the database connection string to initialize all event collection services and tasks.
CopyIf using WIA on Microsoft SQL, run:
PS> .\Import-Events.ps1 -Destination "server=(local);Database=DpEvents" -SaveConfigCopyIf using SQL Auth, run:
PS> . \ImportEvents.ps1 -Destination "server=(local);Database=DpEvents" -Credentials (Get-Credentials) -SaveConfigThe latter command will prompt you for SQL server `dbadmin` credentials. In the above command, “server=(local);Database=DpEvents” is an example of the required connection string. The administrator must provide the actual server name.
Note: The -SaveConfig switch will save the database connection string provided with the -Destination parameter in a default configuration file default.json, so that the next time you run the cmdlet you can omit the parameters.If you need to modify the configuration file, you can use any text editor, or you can run the cmdlet with different parameter values and use the -SaveConfig switch to persist them.
After the `Import-Events` cmdlet finishes its first run, it should have made the following changes in your system:
-
Enabled and tested the Windows Event Collector (WEC) service
-
Created and tested Windows Event Forwarding (WEF) subscriptions for DigitalPersona events
These subscriptions contain queries that allow forwarding DigitalPersona events to the ForwardedEvents event log.
-
Created and tested a periodic event import task in the Windows Task Scheduler
This task runs the Import-Events cmdlet without parameters every 15 minutes.
-
Imported and tested Group Policy Objects (GPOs) for configuring event collection on domain workstations
-
Connected to the Microsoft SQL Server using the connection string defined in the -Destination parameter and created a DigitalPersona Events database using a set of SQL scripts.
-
The database name should be provided in the database connection string. By default it is named DpEvents.
-
-
In the Group Policy Management Console:
-
Locate a new GPO named Enable WinRM Service.
-
Link the GPO to the AD domain, or to the domain object containing both the Event Collector and all computers that the events should be collected from.
-
Locate a new GPO named Enable Event Forwarding.
-
Open the GPO in a policy editor using the "Edit" command from the context menu.
-
In the GPO editor, navigate to the following node:
Local Computer Policy\Computer Configuration\Administrative Templates\Windows Components\Event Forwarding
-
Open and enable the following policy:
Configure the server address, refresh interval, and issuer certificate authority of a target Subscription Manager
-
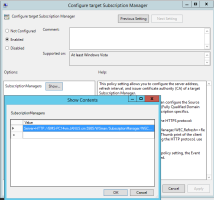
Click SubscriptionManager’s Show....
-
In the SubscriptionManager’s Configuration dialog enter the following string, using the FQDN (Fully Qualified Domain Name) of your Event Collector:
Server=http://<FQDN of the Event Collector server>:5985/wsman/SubscriptionManager/WEC,Refresh=<Refresh interval in seconds>
For example:
Server=http://reports.mydomain.com:5985/wsman/SubscriptionManager/WEC,Refresh=30
Important: Make sure to follow the above format strictly. Omitting the Server= part is the most frequent cause of issues with event forwarding.
-
Link the GPO to an AD object containing computers that the events should be collected from.
This may be either one or more OUs (Organizational Units), or a whole domain.
WMI filtering can be used to limit the GPO scope to specific computers. Collecting events from DigitalPersona clients should be sufficient; avoid additionally collecting events from DigitalPersona servers, as this will cause duplication of some events, throwing off reports.
-
After all GPOs are linked, the selected workstations should receive GPO updates shortly and start forwarding events.
Import-Events cmdlet
The Import-Events cmdlet allows passing configuration parameters via the command line and storing the parameters in a configuration file.
Cmdlet Parameters
The most important parameters and switches are the following:
| Parameter | Description |
|---|---|
| -SaveConfig |
This switch instructs the cmdlet to persist input parameters in the currently loaded config file. Use this switch to save script parameters so that the next time the script is run without parameters it will use these values as defaults. |
| -Log |
This switch instructs the cmdlet to create an execution transcript log. The log file’s name is Import-Events.log and it will be located in the cmdlet installation directory. The previous log file will automatically be backed up as Import-Events.log.bak. |
|
-Destination <database connection string> |
This switch defines the connection string to the Microsoft SQL database. The default value is: server=(local), database=DpEvents Use a value of $null to explicitly reset to default. |
|
-Credential <PSCredential> |
Credentials for the destination database (e.g. for SQL authentication). The user should have admin privileges for creating/upgrading the destination database and must have writer privileges in order to write events. By default Windows Integrated Authentication used with the current user. To ask for credentials interactively, use -Credential=(Get-Credential) |
To get a full list of parameters and examples of usage, run:
PS> Get-Help $pwd\Import-Events.ps1 -fullEvent Import Schedule
The Import-Events cmdlet creates a recurring task in the Windows Task Scheduler on its first run if it has not already been created.
By default, the task runs the cmdlet every 15 minutes, using a default configuration saved in the default.json file.
You can modify the task by changing the execution interval, or by using a different configuration file. You can also query to run the task manually out of schedule.
If you need to log the execution, modify the task and add a -Log parameter to the command. A text log file will be created in the cmdlet installation folder when the task runs.
SQL Database
The Import-Events cmdlet creates a new DigitalPersona Reports database on its first run with SQL admin privileges, using Microsoft SQL scripts that can be found and inspected in the .\Modules\MSSQL\schemas\ directory.
If the database already exists, the cmdlet will check its version and may try to upgrade from older versions to the latest one.
Before installing a newer version of the cmdlet, you should backup your events database.
Troubleshooting
For Windows Server 2016 and higher, you may find the following information helpful:
-
If events are not being forwarded from workstations to the Event Collector, first check for error messages in the following event logs, both on the workstation and on the Collector computer:
-
Microsoft/Windows/EventCollector/EventCollector/Operational
-
Microsoft/Windows/EventCollector/Eventlog-ForwardingPlugin/Operational
The majority of issues with event collection are caused by one of the following issues.
-
An invalid SubscriptionManager value
-
Connectivity issues between the workstation and the reporter, for example:
-
Port 5985 has been disabled by the firewall.
-
IPv6 is enabled but the IPv6 filter rule is missing.
-
Another application or service is listening on port 5985 (e.g. IIS).
-
-
-
To verify that the WinRM service is the service listening on port 5985, run the following command on the Event Collector computer:
Copywinrm e winrm/config/listenerThe expected output should include:
CopyListener [Source="GPO"]
Address = *
Transport = HTTP
Port = 5985
Hostname
Enabled = true
URLPrefix = wsman
CertificateThumbprint
ListeningOn = <your IPv4/IPv6 addresses> -
To confirm that WinRM is actively listening, run one of the following commands and observe the expected result:
CopyFrom the Command Line:
> netstat -aon | find "5985"
The expected output should be:
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4CopyFrom Powershell:
PS> Get-NetTCPConnection -LocalPort 5985
The expected output should be:
LocalAddress LocalPort RemoteAddress RemotePort State AppliedSetting
----------------- ----------- ------------------- -------------- ------ -------------------
:: 5985 :: 0 Listen -
Make sure the collector computer is accessible from the workstation, running ping <collector's IP> on the workstation.