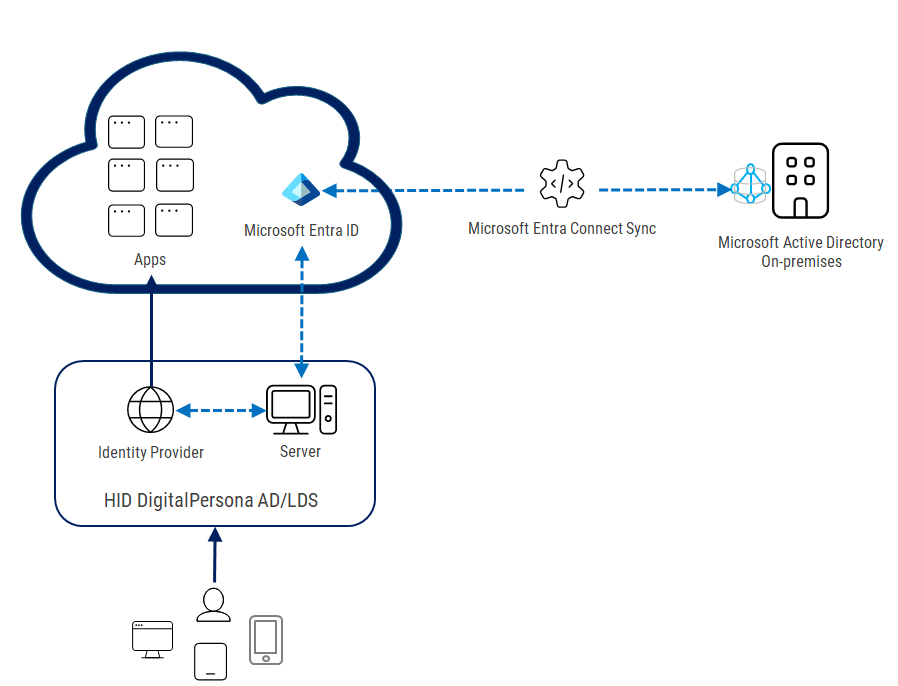
Configuring Microsoft Entra ID Federation with the DigitalPersona IdP
The following sections describe how to implement identity federation from the DigitalPersona Identity Provider (IdP) using Microsoft's hybrid identity solution to connect your on-premises Active Directory® (AD) identities with Microsoft® Entra® ID so users can access on-premise and cloud resources with a single identity.
This integration is an alternative to the cloud-native Microsoft Entra ID solution as it supports the continued use of your current on-premise infrastructure.
About Microsoft's Hybrid Identity Solution
At its core, hybrid identity synchronizes identities from on-premises local Active Directory (AD) to Microsoft Entra ID. This ensures users and groups in your local directory are represented in the cloud, enabling a seamless login experience for services such Microsoft 365, Azure, and third-party applications.
Microsoft Entra Connect Sync is Microsoft’s on-premises synchronization tool that connects your local Active Directory to Microsoft Entra ID. It runs as a Microsoft Windows service and continuously synchronizes identity data (such as users, groups, contacts, and in some cases passwords) between your on-premises AD and the cloud directory.
Federation is another identity integration method that allows authentication to be delegated to an external identity provider. For non-Microsoft identity providers, such as DigitalPersona, you can configure Entra ID to trust their assertions to allow users to access Entra-integrated apps.
For further information, go to:
-
What is hybrid identity with Microsoft Entra ID? | Microsoft Learn
-
What is Microsoft Entra Connect and Connect Health? | Microsoft Learn
-
What is federation with Microsoft Entra ID? | Microsoft Learn
Federation with DigitalPersona
In a federation with DigitalPersona, when a user attempts to sign in to a Microsoft cloud service, Entra ID recognizes the federated domain and redirects them to the DigitalPersona IdP for authentication.
After signing in via the DigitalPersona IdP’s login page, Entra ID grants access to the requested Microsoft service. This allows users to log in to Microsoft 365 applications using their DigitalPersona credentials, including one-time passwords, passkeys, cards, and fingerprints.
Prerequisites
The following requirements must be met before beginning the integration:
-
You must be an Administrator in the Microsoft Entra tenant
-
The domain you want to federate must already be added and verified in Microsoft Entra
-
On-premises users must have the same UPN suffix as the federating domain
-
Microsoft Entra Connect Sync must be deployed and running
-
DigitalPersona LDS Server must be deployed and running
-
DigitalPersona Web Management Components (WMC) must be deployed and running
Only the DigitalPersona Security Token Service (the Identity Provider (IdP)) component is required for federation. The other components are optional.
Set Up Federation
You can enable federation using the Microsoft Graph PowerShell.
It cannot be configured in the Microsoft Entra ID admin center.
-
Install the Microsoft Graph PowerShell module using the following command:
CopyInstall-Module Microsoft.Graph -Scope CurrentUser -
Authenticate and grant admin consent using the following command:
CopyConnect-MgGraph -Scopes "Domain.ReadWrite.All", "Directory.ReadWrite.All", "Directory.AccessAsUser.All" -
Set up federation with the following parameters:
Property Description DomainId
Name of the verified domain to federate
For example, contoso.com
DisplayName
The display name of the federated identity provider
For example, DigitalPersona
IssuerUri
Issuer URI of the federation server
For example, https://dpsts.contosofed.com/dppassivests
PassiveSignInUri
URI that clients are directed to when signing in to Microsoft Entra services
For example, https://dpsts.contosofed.com/dppassivests/wsfed
SignOutUri
URI that clients are redirected to when they sign out of Microsoft Entra services
For example, https://dpsts.contosofed.com/dppassivests/wsfed
PreferredAuthenticationProtocol
Must be wsFed
FederatedIdpMfaBehavior
Must be acceptIfMfaDoneByFederatedIdp
Microsoft Entra ID accepts MFA performed by the federated identity provider. If the federated identity provider did not perform MFA, Microsoft Entra ID performs the MFA.
SigningCertificate
Current certificate used to sign tokens passed to the Microsoft identity platform
The certificate in compatible format can be found in WS-FED metadata file that is available at https://dpsts.contosofed.com/dppassivests/wsfed/metadata
Important: All values are case-sensitive. Enter the domain names in lower case.For example (where you should replace the values of idpDomain and federatedDomain with your IdP domain name and the Entra ID verified domain that you want to federate):
Copy$idpDomain = "dpsts.contosofed.com"
$entraDomain = "contoso.com"
New-MgDomainFederationConfiguration `
-DomainId $entraDomain `
-DisplayName "DigitalPersona" `
-IssuerUri https://$idpDomain/dppassivests `
-PassiveSignInUri https://$idpDomain/dppassivests/wsfed `
-SignOutUri https://$idpDomain/dppassivests/wsfed `
-PreferredAuthenticationProtocol wsFed `
-FederatedIdpMfaBehavior acceptIfMfaDoneByFederatedIdp `
-SigningCertificate ((Invoke-RestMethod https://$idpDomain/dppassivests/wsfed/metadata).EntityDescriptor.RoleDescriptor.KeyDescriptor.KeyInfo.X509Data.X509Certificate) -
To verify that the domain is federated, log on to the Microsoft Entra admin center, go to Domain Names and make sure there is a check mark in the Federated column for your domain.
For further information, go to Create internalDomainFederation | Microsoft Learn
Update the Signing Certificate
If you need to update the DigitalPersona IdP signing certificate (for example, because the previous certificate has expired), manually upload the new certificate to Microsoft Entra ID. This can also be done with Microsoft Graph PowerShell.
-
Authenticate and grant admin consent using the following command:
CopyConnect-MgGraph -Scopes "Domain.ReadWrite.All", "Directory.ReadWrite.All", "Directory.AccessAsUser.All" -
Find the internal ID of the federated domain using the following command:
CopyGet-MgDomainFederationConfiguration -DomainId contoso.com -
Update the certificate with the following parameters:
Property Description DomainId Name of the federated domain InternalDomainFederationId Internal ID of the federation configuration SigningCertificate Current signing certificate For example (where you should replace the values of idpDomain and federatedDomain with your IdP domain name and the Entra ID verified domain that you want to federate):
Copy$idpDomain = "dpsts.contosofed.com"
$entraDomain = "contoso.com"
Update-MgDomainFederationConfiguration `
-DomainId $entraDomain `
-InternalDomainFederationId (Get-MgDomainFederationConfiguration -DomainId $entraDomain).Id `
-SigningCertificate ((Invoke-RestMethod https://$idpDomain/dppassivests/wsfed/metadata).EntityDescriptor.RoleDescriptor.KeyDescriptor.KeyInfo.X509Data.X509Certificate)
Disable Federation
To disable federation for a domain using Microsoft Graph PowerShell you convert it from federated to managed. This is done by removing the federation configuration for that domain.
-
Authenticate and grant admin consent using the following command:
CopyConnect-MgGraph -Scopes "Domain.ReadWrite.All", "Directory.ReadWrite.All", "Directory.AccessAsUser.All" -
Find the internal ID of the federated domain using the following command:
CopyGet-MgDomainFederationConfiguration -DomainId contoso.com -
Disable federation with the following parameters:
Property Description DomainId Name of the federated domain InternalDomainFederationId Internal ID of the federation configuration For example(where you should replace the values of idpDomain and federatedDomain with your IdP domain name and the Entra ID verified domain that you want to federate):
Copy$idpDomain = "dpsts.contosofed.com"
$entraDomain = "contoso.com"
Remove-MgDomainFederationConfiguration `
-DomainId $entraDomain `
-InternalDomainFederationId (Get-MgDomainFederationConfiguration -DomainId $entraDomain).Id