6. Temenos Digital Web Banking with PIN (or Password) & SMS Secure Code & RMS
6.1 Registration (SMS Authentication)
-
Customer has received the customer ID and Activation Code using the Temenos components.
-
Customer is prompted to enter the customer ID and Activation Code.
-
Customer enters the customer ID and Activation Code.
-
Activation code is successfully validated on the HID Authentication Service.
-
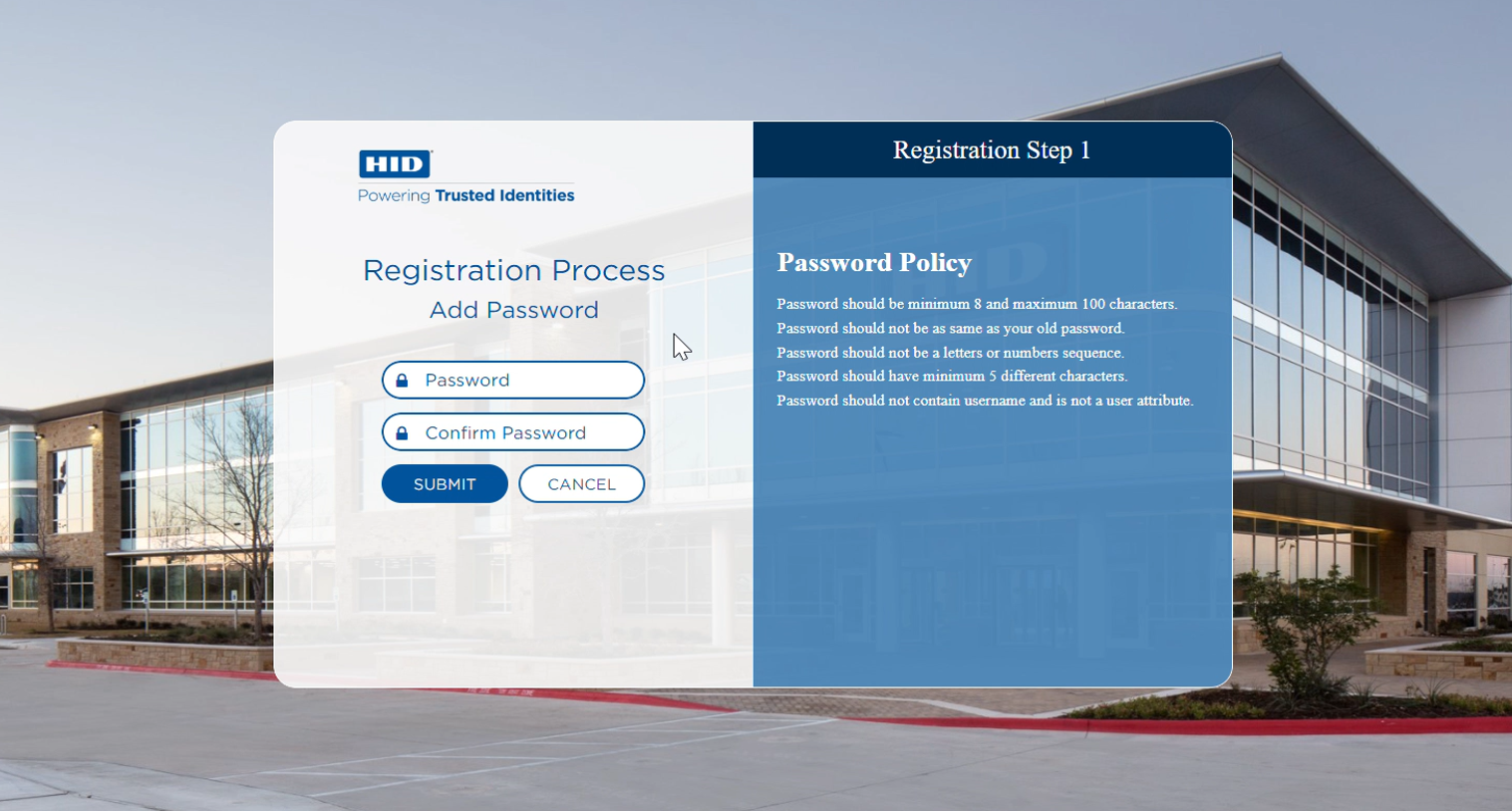
Customer is prompted to add password.
-
Customer's password is submitted.
-
Password is stored securely on HID Authentication Service.
-
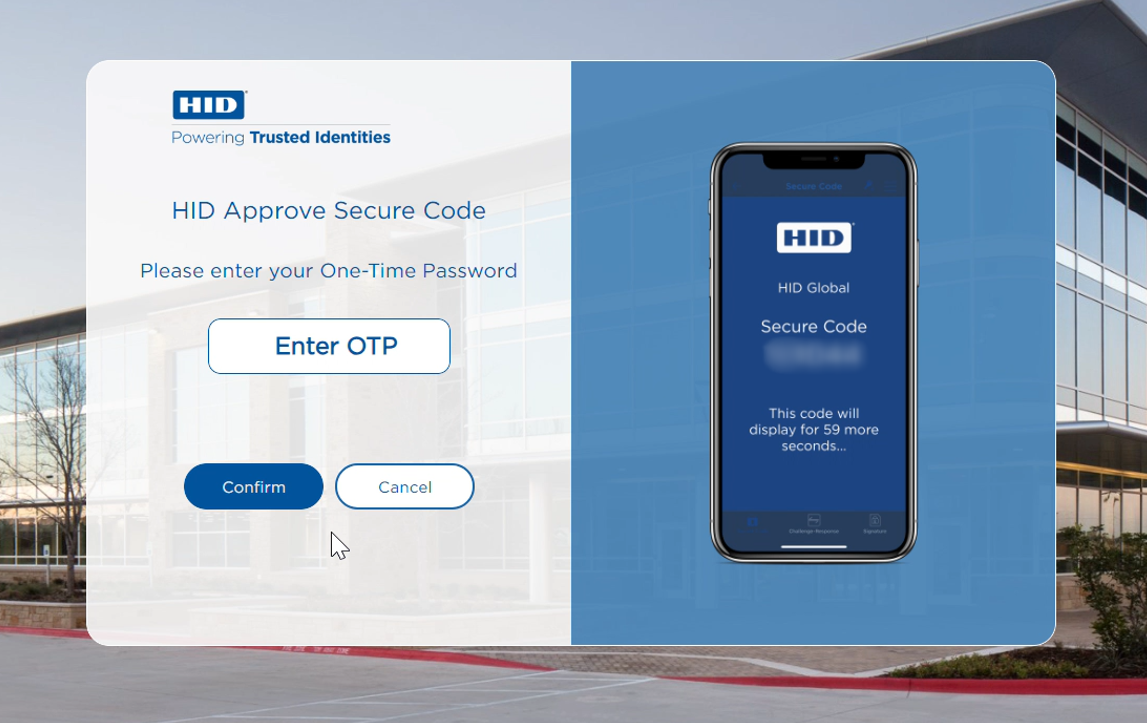
Customer is sent the SMS Secure Code to the registered mobile number.
-
Customer enters the Secure Code in the online banking application.
-
Secure Code authenticated successfully.
-
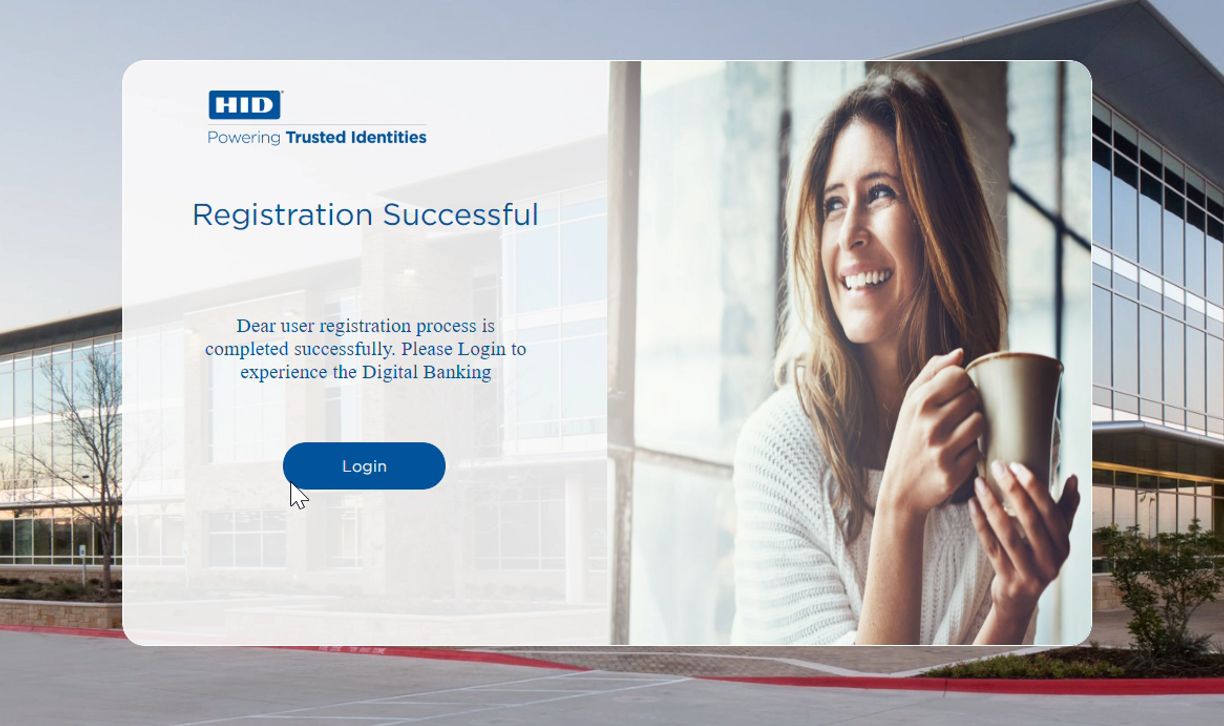
Customer has successfully registered for SMS-based authentication.
6.2 Login Web Channel (SMS)
-
Customer accesses the online banking application.
-
Online banking application requests JS probe and session data from RMS.
-
RMS generates session data and returns it to Online banking application.
-
Online banking application caches session data and sends data gathered by probe to RMS.
-
-
Customer chooses the option to log in with SMS Secure Code.
-
Customer is prompted to enter the customer ID and Password.
-
Customer enters the customer ID and Password.
-
Customer ID and Password are sent to HID Authentication Service for validation.
-
If successful, the customer is sent an SMS Secure Code to their registered mobile number.
-
Web online banking application prompts the customer to enter SMS Secure Code.
-
Customer enters the received SMS Secure Code in the online banking application.

-
SMS Secure Code is sent to the HID Authentication Service for validation.
-
Online banking application calls RMS to create session and get risk data (allow, step-up, block).
-
 If ALLOW
If ALLOW
-
Online banking application calls RMS to login.
-
-
Customer is logged in successfully.
6.3 Transaction Web Channel (SMS Signature)
-
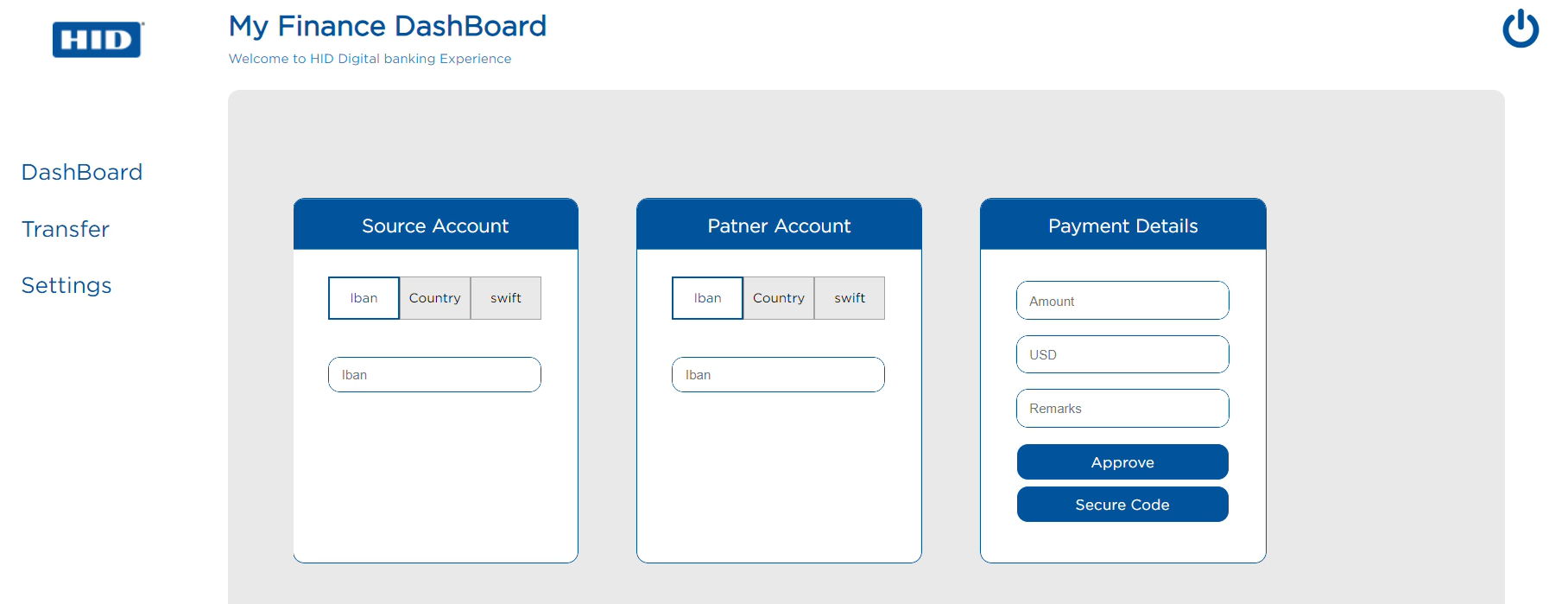
Customer initiates transaction in the online banking application.
-
Online banking application calls RMS to create payment and get risk data (allow, step-up, block).
-
 If BLOCK
If BLOCK
-
Online banking application calls RMS to reject payment.
-
Online banking application denies transaction.
-
-
 If STEP-UP
If STEP-UP
-
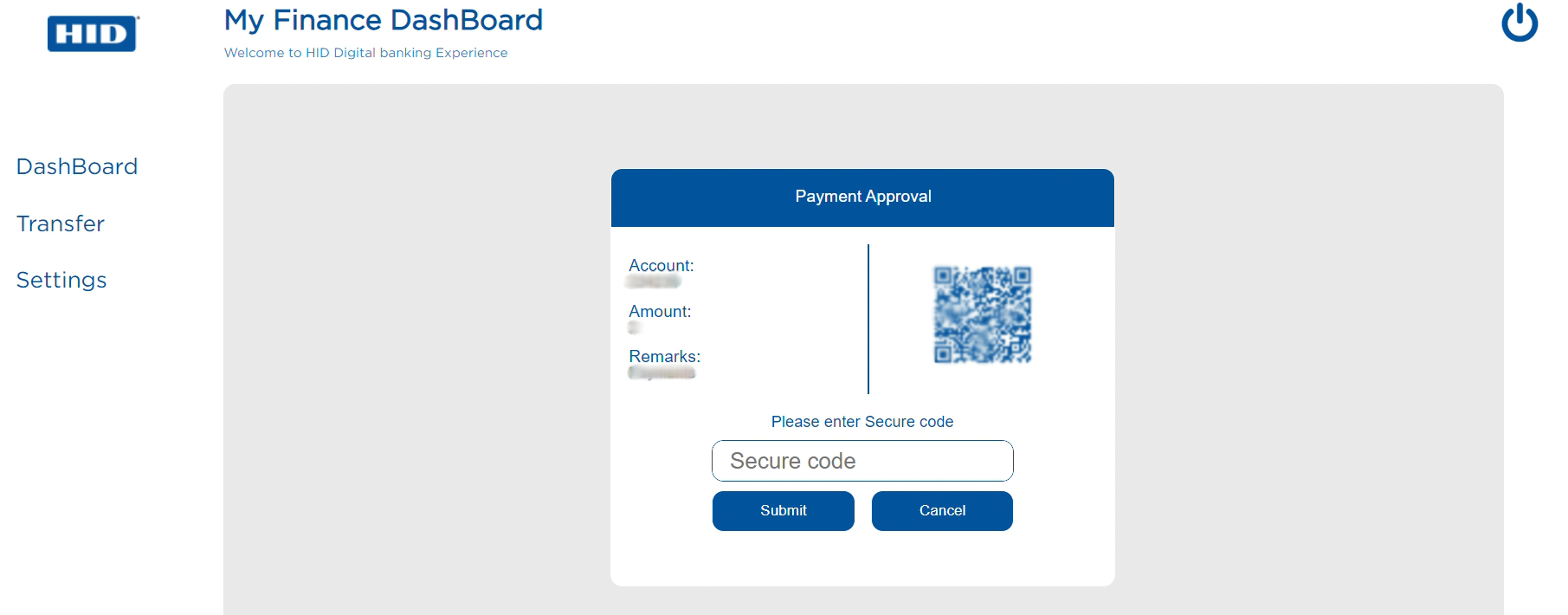
Customer is prompted to enter the PIN.
-
Customer ID and PIN are sent to HID Authentication Service for validation.
-
If the Customer ID and PIN authentication is successful, the customer is sent an SMS Secure Code along with transaction details to their registered mobile number.
-
Web online banking application prompts the customer to enter SMS Secure Code.
-
Customer enters the received SMS Secure Code in the online banking application.
-
SMS Secure Code is sent to the HID Authentication Service for validation.
-
Online banking application calls RMS to sign and accept the transaction.
-
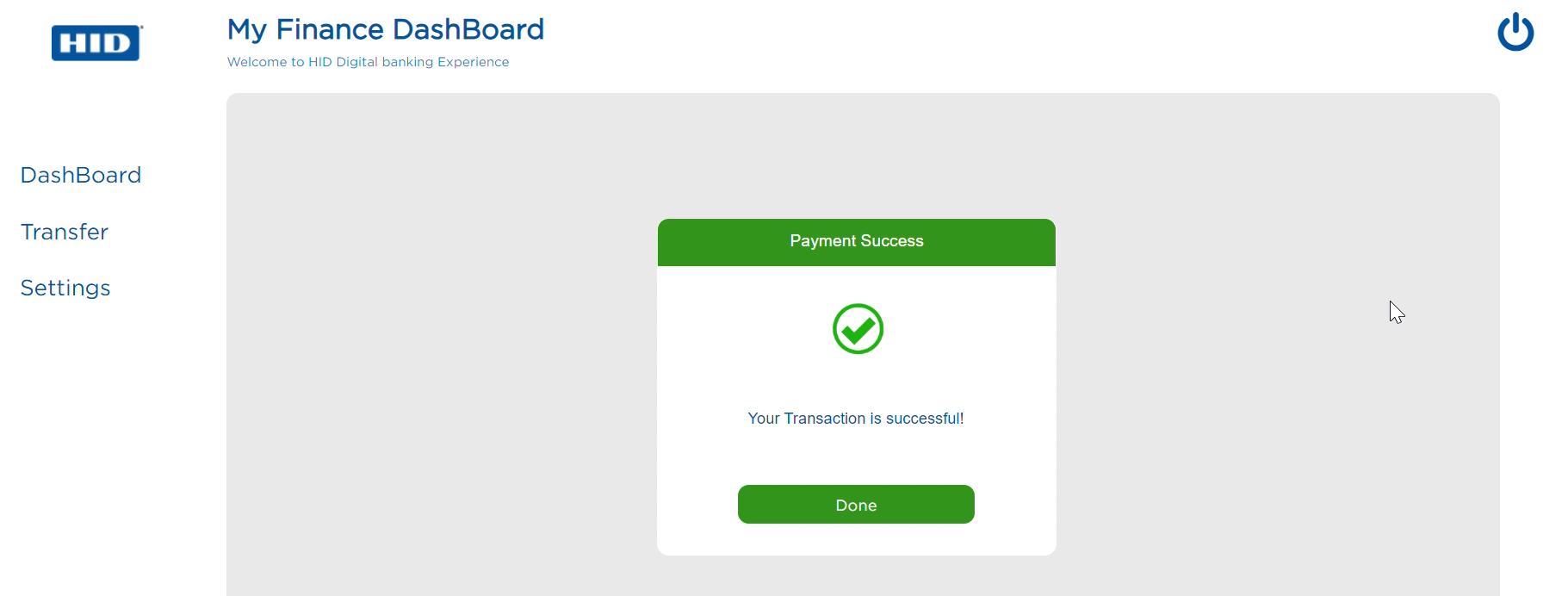
Transaction completed successfully.
-
-
 If ALLOW
If ALLOW
-
Online banking application calls RMS to sign and accept the transaction.
-
Transaction completed successfully.
Note: This workflow can also be used for any non-financial transactions such as updating a mobile number or email address, etc. -
6.4 Change PIN or Password
-
Customer initiates SMS PIN or Password change in the online banking application.
-
Online banking application calls RMS to create action and get risk data (allow, step-up, block).

-
 If BLOCK
If BLOCK
-
Online banking application calls RMS to reject action.
-
Online banking application denies Change PIN request.
-
-
 If STEP-UP
If STEP-UP
-
Customer is prompted to enter the PIN.

-
Customer ID and PIN are sent to HID Authentication Service for validation.
-
If the Customer ID and PIN authentication is successful, the customer is sent an SMS Secure Code along with transaction details to their registered mobile number.
-
Web online banking application prompts the customer to enter SMS Secure Code.

-
Customer enters the received SMS Secure Code in the online banking application.
-
SMS Secure Code is sent to the HID Authentication Service for validation.
-
Online banking application calls RMS to sign and complete the action.
-
Customer is prompted to enter new SMS PIN or Password.
-
New PIN or Password is sent to HID Authentication Service and stored securely.
-
-
 If ALLOW
If ALLOW
-
Online banking application calls RMS to sign and complete the action.
-
Customer is prompted to enter new SMS PIN or Password.
-
New PIN or Password is sent to HID Authentication Service and stored securely.
-
6.5 Forgotten PIN or Password
The customer can't recover their forgotten or lost SMS PIN. Customer must contact the bank and request for their account to be reset. Upon reset customer will be sent a new Activation Code so they can re-register for SMS-based authentication to online banking.
6.6 Expired PIN or Password
-
Customer accesses the online banking application.
-
Online banking application requests JS probe and session data from RMS.
-
RMS generates session data and returns it to Online banking application.
-
Online banking application caches session data and sends data gathered by probe to RMS.
-
-
Customer chooses the option to log in with SMS Secure Code.
-
Customer is prompted to enter the customer ID and PIN.
-
Customer enters the customer ID and PIN.

-
Customer ID and PIN are sent to HID Authentication Service for validation.
-
HID Authentication Service returns a response that the PIN or Password has expired.
-
Infinity prompts the customer to enter a new PIN or Password..
-
Infinity sends the new password to the HID Authentication Service to store it securely.
-
Customer is prompted to enter the new PIN or Password.
-
The new PIN or Password is sent to the HID Authentication Service for validation.
-
If successful, the customer is sent an SMS Secure Code to their registered mobile number.
-
Web online banking application prompts the customer to enter SMS Secure Code.

-
Customer enters the received SMS Secure Code in the online banking application.
-
SMS Secure Code is sent to the HID Authentication Service for validation.
-
Online banking application calls RMS to create session and get risk data (allow, step-up, block).
-
 If BLOCK or STEP-UP
If BLOCK or STEP-UP
-
Online banking application calls RMS to reject login.
-
Online banking application denies access to account.
-
-
 If ALLOW
If ALLOW
-
Online banking application calls RMS to login.
-
Customer is logged in successfully.

-
6.7 SMS Authentication Policy Reset Failure Counter
An SMS Secure Code authentication policy on the HID Authentication Service can be blocked due to customers entering incorrect SMS Secure Codes for authentication in the web channel. The customer must contact the bank help desk so the bank can reset the failure counter of the authentication policy from Spotlight. It is recommended that the bank staff perform Identity and Verification before resetting the failure counter. Please note that Spotlight integration is out of scope for HID Global.
6.8 SMS Authentication Policy Reset Number of times the customer can request for Secure Code
It is possible to configure the number of times a customer can request for SMS Secure Code on the HID Authentication Service without validating it. This configuration prevents the bank customers from being exposed to DDOS attacks. If this is configured to a limited number of requests and the customer has exceeded the threshold then they will not be able to request for SMS Secure Code anymore. Customers must contact the bank help desk so the bank can unregister and register the SMS authentication policy so customers can continue to login. It is recommended that the bank staff perform Identity and Verification before they re-register the SMS authentication policy for the customer.