Onboarding Users
| Mandatory Server Settings |
HOST |
<HID Authentication Service Host> (e.g., test123.aaas.hidcloud.com) |
|---|---|---|
|
TENANT |
<HID Authentication Service Tenant Id> (e.g., tf98f45g90843781907) |
|
|
ORG_ADMIN_USERNAME |
<Org admin user of HID Authentication Service Tenant> (e.g., john.doe@abcorg.com) |
|
|
ORG_ADMIN_PASSWORD |
<Password for the Org admin user> (e.g., Password01) |
|
|
KONY_APP_KEY |
<App key of the fabric application> (e.g., h728h89031832jdy9292) |
|
|
KONY_APP_SECRET |
<App secret of the fabric application> (e.g., 89bv2894673792003jy2) |
|
|
SERVICES_URL |
https://<kony-account-host>/services
|
|
| Optional Server Settings |
ACTIVATION_CODE_AUTHTYPE |
<Activation Code Authenticator if other than AT_ACTPWD> |
|
PASSWORD_AUTHTYPE |
<Static Password Authenticator if other than AT_STDPWD> | |
|
OOB_SMS_OTP_AUTHTYPE |
<OOB SMS Authenticator if other than AT_OOBSMS> |
|
|
OOB_EMAIL_OTP_AUTHTYPE |
<OOB Email Authenticator if other than AT_OOBEML> |
|
|
DEVICE_TYPE |
<Device type to be used for HID Approve if other than DT_TDSV4> | |
| HID_IS_APPLIANCE | <Identifies whether device is HID Appliance or not> |
Onboarding Component Properties
| S.No. | Property Name | Allowed Values | Purpose |
|---|---|---|---|
| 1 | FirstFactor | "STATIC_PWD","SECURE_CODE", "OTP_SMS_PIN" |
This property determines the first authentication factor to be added to the user. Currently the first authentication factors supported are:
|
|
2 |
MFA |
"OTP_SMS","OTP_EML","APPROVE" |
This property determines the second authentication factor to be added to the user after the first authentication factor is created. Currently, the component supports the following factors:
|
-
When we select FirstFactor as OTP_SMS_PIN, then it is mandatory to select MFA as NO_MFA.
-
When we select FirstFactor as SECURE_CODE, then it is mandatory to select MFA as APPROVE.
Onboarding Component Functions
No public function is exposed. All the functions are called from the UI provided with the component.
Onboarding Component Flow
STATIC_PWD
- In the first screen, the user provides their Username and Activation Code, then clicks Register.

- After successfully validating the Activation Code, the component displays the screen to add a password for the user.
- In the second screen, user enters and confirms a Password and clicks Submit.Note: The Password must comply with the Password policy.
- After the Static password authenticator is successfully created, based on the defined value of the MFA property, the components adds the second authenticator for the user:
 HID Approve
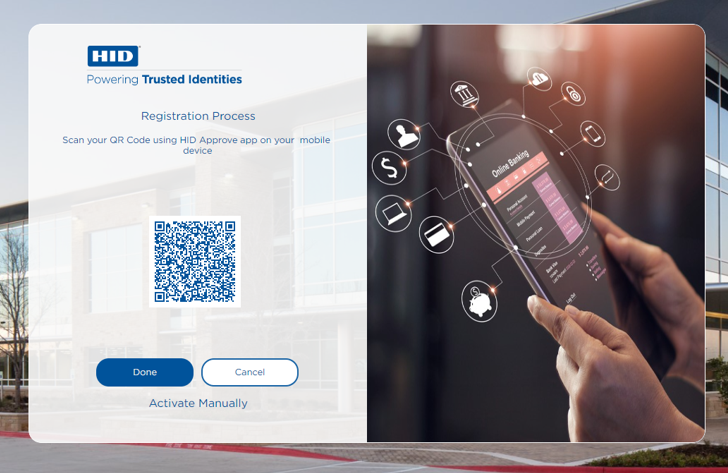
HID ApproveThe third screen displays the options to register an HID Approve device using either the QR code or manual registration.
Registration via QR Code
After the device is registered successfully, the user is directed to next screen with a notification that the Push notification has been sent to the registered device to confirm the onboarding process.
After approving the push notification, the user is directed to next screen confirming the successful onboarding.
 OTP via SMS or Email
OTP via SMS or EmailAfter adding the Out-of-Band (OOB) for SMS/Email authenticator to the user, the user receives an OTP either by SMS or by email based on the selected MFA option.
In the third screen, the user enters the received OTP to complete the onboarding process.
After validating the OTP successfully, the user is directed to next screen confirming the successful onboarding.
SECURE_CODE
-
On the first screen, user need to provide Username and activation code, then click Register Button.
-
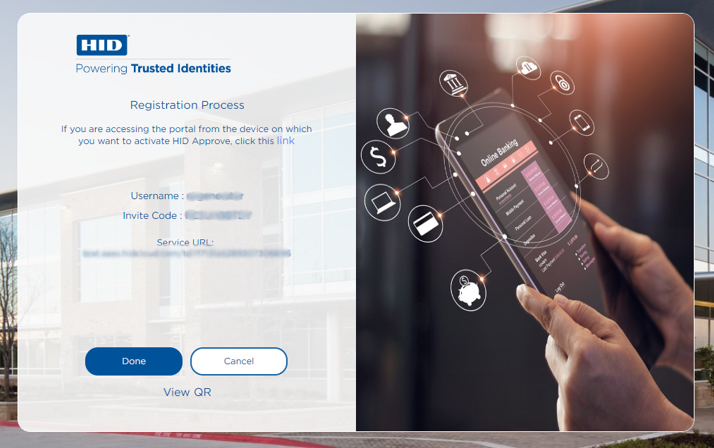
After successfully validating the activation code, it will show the next screen to with QR code to register user on mobile app.
or
User can select the "Activate Manually" option to display the details to register device manually.
-
After the device is registered successfully, user will be directed to next screen to show that the onboarding process is completed successfully.
-
OTP_SMS_PIN
-
On the first screen, user need to provide Username and activation code, then click Register Button.
-
After successfully validating the activation code, it will show the next screen to add PIN to the user.
-
On the second screen, user need to enter the Password and Confirm Password and click Submit Button (the PIN provided here should comply to the Password policy).
-
On the third screen, user will be directed to next screen to show that the onboarding process is completed successfully.
-
Onboarding Component Services
Object Services
| ServiceName | DataModel | Mapping | Purpose | Input Parameters | Invoking |
|---|---|---|---|---|---|
|
HIDObjects |
ActivationCodeValidation |
validateActivationCode |
Validate the user's activation code. |
filter (username), username, activationCode, authType |
OnboardingValidation > ValidateUser |
|
HIDObjects |
AddOOBAuthenticator |
addOOBAuthenticator |
Add an OOB (SMS/Email) authenticator to the user. |
userId, AuthenticatorType (AT_OOBSMS/ AT_OOBEML), AuthenticatorValue (OOB Device Type code : DT_OOBSMS/DT_OOBEML) |
ScimAPIsOrg > addOOBAuthenticator |
|
HIDObjects |
AddPasswordAuthenticator |
addPasswordAuthenticator |
Add a static password authenticator to the user. |
username, userId, password, authType |
ScimAPIsOrg > addPasswordAuthenticatorInt |
|
HIDObjects |
ApproveDeviceRegistration |
getInviteCode |
Provision the HID Approve device to the user and get the invite code to add the HID Approve device. |
UserId, username, usernameWithRandomNo |
PushDeviceRegistrationOrch > getInviteCode |
|
HIDObjects |
HIDApproveInitiation |
initiateApprove |
Initiate the Push notification on the HID Approve device. |
username |
HIDApproveInitiation > initiate |
|
HIDObjects |
ApproveStatusPolling |
approveStatusPolling |
Poll to the ApproveCallback service to fetch the status of user's response to the HID Approve Push notification. |
mfa_key (authRequest Id from the initiateApprove service response) |
HIDPollConsensus > getHIDApprovalStatus |
|
HIDObjects |
DeviceRegistrationPolling |
deviceRegistrationPolling |
Poll to the DeviceRegistration Callback service to fetch the status of the HID Approve device registration. |
deviceId (device Id from the getInviteCode service response) |
HIDPollConsensus > getHIDDeviceRegistrationStatus |
|
HIDObjects |
SendOOB |
sendOOB |
Send the OOB (SMS/Email) OTP to the user. |
username, AuthenticatorType (AT_OOBSMS/AT_OOBEML) |
OTPServices > sendOOB |
|
HIDObjects |
ValidateOOB |
validateOOB |
Validate the OOB (SMS/Email) OTP. |
username, AuthenticatorType (AT_OOBSMS/ AT_OOBEML), OTP |
OTPService > validateOOB |
| HIDObjects | PasswordPolicy | getPasswordPolicy | Gets the policy for Static Password Authenticator | none | ScimAPIs>getPasswordPolicy |
Fabric Services
| Names | Operation Name | Service Type | Description |
|---|---|---|---|
|
ClientIdentity |
- |
Identity |
Fetches Client Bearer Token |
|
OrgAdminScim |
- |
Identity |
Fetches OrgAdmin Bearer Token |
|
ActivationCodeService |
Login |
Integration |
Authenticates the Activation Code |
|
ClientAuthIdentityWrapper |
getClientBearerToken |
Integration |
IntegrationWrapper of ClientIdentity |
|
ClientAuthIdentityWrapper |
getOrgBearerToken |
Integration |
Integration Wrapper for OrgAdminScim |
|
DependencyManager |
|
Integration |
Resolves the dependencies for HIDProcessor.jar. |
|
DeviceProvisionJava |
GetProvisonMsg |
Integration |
Fetches the Invite Code |
|
HIDApproveInitiation |
Initiate |
Integration |
Sends an HID Approve Push notification to the user's registered device. |
|
HIDPollConsensus |
getHIDApprovalStatus |
Integration |
Java service to fetch callback response of the HID Approve Push notification. |
|
HIDPollConsensus |
getHIDDeviceRegistrationStatus |
Integration |
Java service to fetch the callback response of the HID Approve device registration status. |
|
OTPServices |
SendOOB |
Integration |
Sends an OOB OTP to the user. |
|
OTPServices |
validateOOB |
Integration |
Validates an OOB OTP. |
|
OTPServices |
validateOTP |
Integration |
Validates a Hardware OTP. |
|
ScimAPIs |
SearchUser |
Integration |
Searches for the user. |
|
ScimAPIs |
createNewDevice |
Integration |
Creates a new Device ID for the user. |
|
ScimAPIs |
getActivationCodeAuthenticator |
Integration |
An exclusive getAuthenticator service for the ValidateUser Orchestration service. This service does not work alone so use the getAuthenticator instead. |
| ScimAPIs | getPasswordPolicy | Integration | Provides the Password policy. |
|
ScimAPIs |
updateDevice |
Integration |
Binds the new Device ID to the user. |
|
ScimAPIsOrg |
addOOBAuthenticator |
Integration |
Adds an OOB Authenticator to the user. |
|
ScimAPIsOrg |
addPasswordAuthenticatorInt |
Integration |
Adds a Password Authenticator. |
|
OnbaordingValidation |
ValidateUser |
Orchestration |
|
|
PushDeviceRegistrationOrch |
getInviteCode |
Orchestration |
Provisioning Push Device |
Java Services
| Service Name | Purpose | Dependencies | Called by (Service Name-Operation) |
|---|---|---|---|
|
DeviceProvision |
Java service to send the Device Provisioning request for HID Approve device registration and process the response to send the provisioning message. |
You need to configure following Server Properties:
|
DeviceProvisionJava-getProvisonMsg |
|
HIDPollForConsensus |
Java service which keeps polling for 45 seconds to get the status of the HID Approve Push notification sent to the user. |
|
HIDPollConsensus-getHIDApprovalStatus |
|
PollForDeviceRegistrationStatus |
Java service which keeps polling for 45 seconds to get the status of the HID Approve device registration. |
|
HIDPollConsensus-getHIDDeviceRegistrationStatus |
Listener Endpoints (HTTP Servlets)
| Name | URL | Purpose | Dependencies |
|---|---|---|---|
|
ApproveCallBackEndpoint |
https://hidglobal-dev.konycloud.com/services/ApproveCallBackEndpoint |
Listen to the callback response sent by the HID Authentication Service for the user's response to the HID Approve Push notification. |
|
|
DeviceRegistrationCallBackEndpoint |
https://hidglobal-dev.konycloud.com/services/DeviceRegistrationCallBackEndpoint |
Listen to the callback response sent by the HID Authentication Service for the user's response to the HID Approve Device registration request (either by scanning QR code or manually registration) |
None (Listener endpoint URL is already being sent in Device Provisioning request as cb_url). |
Onboarding Pre/Post Processors
| Names | Description | Used by (ServiceName-Operation) |
|---|---|---|
|
ActivationCodeAuthenticatorPostProcessor |
Processes the output of Get Activation code authenticator for user and adds an error message to the response if activation code is already consumed, expired or reached wrong attempts threshold. |
ScimAPIs-getActivationCodeAuthenticator |
|
ActivationCodeLoginPostProcessor |
Adds an error message to the output if the validation of the Activation Code API sends an error. |
ActivationCodeService-login |
|
AddPasswordPostProcessor |
Processes the output of the Add Static password authenticator to user API, adds an error code to the output if the API fails and adds an error message if the API specifically fails because an authenticator already exists for the user. |
ScimAPIsOrg-addPasswordAuthenticatorInt |
|
CreateDevicePostprocessor |
Processes the output of Create Device API for HID Approve device registration, adds an error message to the output if the device creation fails. |
ScimAPIs-createNewDevice |
|
GetInviteCodePostProcessor |
Processes the output of the Create Device Provision API for the HID Approve device registration, adds an error message to the result if the device id or provisioning message is null in the response. |
PushDeviceRegistrationOrch-getInviteCode |
|
SearchUserPostProcessor |
Processes the output of the Search User API based on the total results and if user is active or not. Also verifies if the Activation Code authenticator is added to the user. |
ScimAPIs-SearchUser |
|
UpdateDevicePostProcessor |
Processes the output of the Update Device API which is used during the HID Approve device registration, adds an error message to the output if the API fails. |
ScimAPIs-updateDevice |
|
ValidateUserPostProcessor |
Processes the output of validating the user's Activation Code orchestration service, adds an error message to the result if any error occurs during the operation. |
OnbaordingValidation-ValidateUser |
|
ActivationCodeAuthenticatorPreProcessor |
Pre-processes the output of search user for GetActivationCode Authenticator for user to verify if the user exists and if the Activation Code authenticator exists for user. |
ScimAPIs-getActivationCodeAuthenticator |
|
ActivationCodeLoginPreProcessor |
Verifies if an error has occurred in the previous service during the orchestration. Also sets the value of AuthenticationType in the input for the request from the configured server setting ACTIVATION_CODE_AUTHTYPE. If not configured, takes the default value (AT_ACTPWD). |
ActivationCodeService-login |
|
AddOOBAuthenticatorPreProcessor |
Sets the value of AuthenticationType in the input for the request if configured in the server settings OOB_SMS_OTP_AUTHTYPE or OOB_EMAIL_OTP_AUTHTYPE. If not configured, takes the default value (AT_OOBSMS/AT_OOBEML). |
ScimAPIsOrg-addOOBAuthenticator |
|
AddPasswordPreProcessor |
Sets the startDate, expDate in the input for the request and AuthenticationType if configured in the server setting PASSWORD_AUTHTYPE. If not configured, takes the default value (AT_STDPWD). |
ScimAPIsOrg-addPasswordAuthenticatorInt |
|
CreateDevicePreProcessor |
Sets the startDate, expiryDate in the input for the request and deviceType if configured in the server setting DEVICE_TYPE. If not configured, takes the default value (DT_TDSV4). |
ScimAPIs-createNewDevice |
|
DeviceProvisionPreProcessor |
Verifies if an error has occurred in previous service during the orchestration. Also sets the value of deviceType in the input for the request from the configured server setting DEVICE_TYPE. If not configured, takes the default value (DT_TDSV4). |
ScimAPIs-updateDevice DeviceProvisionJava-getProvisonMsg |
|
OOBAuthenticatorPreprocessor |
Sets the value of AuthenticationType in the input for the request if configured in the server settings OOB_SMS_OTP_AUTHTYPE or OOB_EMAIL_OTP_AUTHTYPE. If not configured, takes the default value (AT_OOBSMS/AT_OOBEML). |
OTPServices-sendOOB |