Configure the ActivID AAA Server
After the installation of AAA Server 7.0 completes successfully, you must run the Server Configurator and SKI Connector Configurator (see Configure the SKI Connector) to ensure all AAA Services are properly configured before proceeding.
This section describes how to configure the AAA Server so that it can communicate with the AAA Administration Console.
- From the Windows Start menu, point to Programs, ActivID, AAA, and then click Server Configurator.
Keep the password in a safe place.
Use a different password when you log on to the Administration Console.
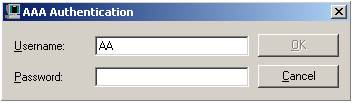
- Do one of the following, then click OK.
| If... | Then... |
|---|---|
| This is the first installation of the AAA Server and you chose not to create the Service credential during installation. | Enter the new credentials and enter the password again when prompted to confirm. |
| There is an existing installation. | You are prompted for your username and password. |
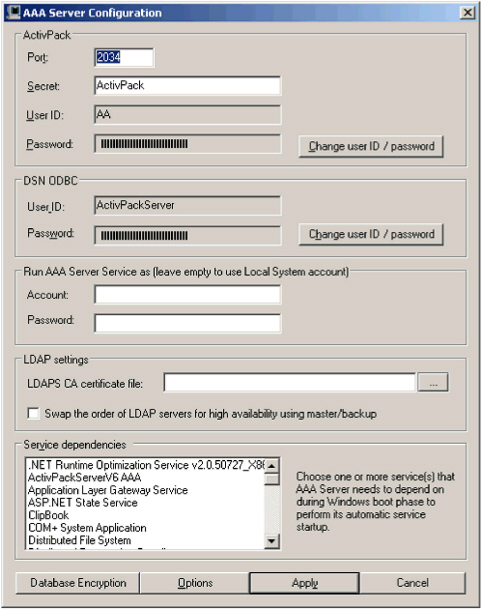
The AAA Server Configuration window is displayed:
-
In the ActivPack section, define the following settings:
- Port - TCP/IP listening port for exchanges between the AAA Server and the Administration Console (for example, transfer credentials and settings between the Administration Console and the Authentication Server).
The AAA Server uses the port in the authentication server to synchronize the Administration Console database and the authentication database and to log data for audit purposes.
You can accept the default port, 2034 , or change it as needed.
You must then set the same Port when configuring the AAA Authentication Server(s) in the Administration Console.
- Secret - The AAA Server uses this secret to encrypt exchanges between the AAA Authentication Server(s) and the Administration Console.Important: You MUST change the default server shared secret to maintain maximum security.
The maximum length of the secret is 24 characters and special characters are allowed.
You must then set the same Secret when configuring the AAA Authentication Server(s) in the Administration Console.
The default value is ActivPack.
- User ID and Password - AAA Server uses the fields to encrypt the database encryption key. Note: The AAA Server uses the User ID and Password fields to start the ODBC connection with the database used by the server. It is strongly recommended that you protect this database access from unauthorized third parties.
To change one or both of these values, click Change user ID / password.
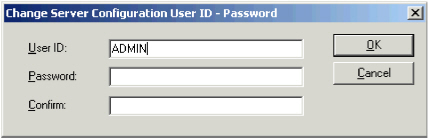
Enter the new credentials, and click OK.
Important: Completion of this step changes the username and password required to access the AAA Server Configuration program. Keep the first Administrator’s User ID and Password in a safe place. This is the permanent User ID and Password used to access the server. - Port - TCP/IP listening port for exchanges between the AAA Server and the Administration Console (for example, transfer credentials and settings between the Administration Console and the Authentication Server).
- In the DSN ODBC section, to change the user ID or password, click Change user ID / password, and click OK.
The Change ODBC User ID - Password window is displayed.
The AAA Server uses the User ID and Password fields to start the ODBC connection with the database used by the server. It is strongly recommended that you protect this database access from unauthorized third parties.
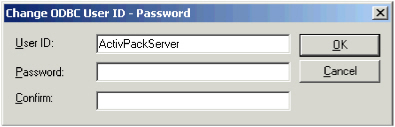 Note: If you change the database user ID or password, remember to update the value in this screen, and in your database management system.
Note: If you change the database user ID or password, remember to update the value in this screen, and in your database management system. - If you want the AAA Server service to use the Windows account, instead of the Local System administrator, enter the credentials for the alternative account in the Run AAA Server Service as section.
This account must have sufficient rights to write to the disk, access the databases and run the Services.
Important: If you experience errors when starting the AAA Service via the Server Configurator or AAA Administration Console (such as “Unable to retrieve database version,” or other errors), AAA may not have the permissions needed to run properly. In this case, it is recommended to input a Local or Domain Administrator account in the Run AAA Server Service as and verify that the issue is resolved.Leave these fields empty to use the Local System administrator account.
-
If you intend to use a secure connection to the LDAP, under LDAPS settings:
- Browse to the exported root certificate (a .cer file in base64 format) of the certificate authority that issued the server certificate installed in your directory and used to access your LDAP.Important:
- This certificate must be imported into the AAA Server's Trusted Root Certification Authorities store, as well as any server which will initiate LDAPS communication with the directory server on behalf of AAA Server (for example, if the SKI Connector is running on a separate server, the certificate should also be chainable to root on that server).
- You must also configure the same certificate in the Administration Console (see Configure the Connection to LDAP) and SKI Connector (see Configure the SKI Connector).
Note: LDAPS with Multiple Domains
LDAPS will not work for multiple peer domains in the same forest, nor will it work for multiple domains in different forests. -
Select Swap the order of LDAP servers... if you are using two LDAP repositories and want to ensure high availability.
Note: In a master/backup or server pool configuration, you must swap the LDAP order on only one of the AAA Servers. - Browse to the exported root certificate (a .cer file in base64 format) of the certificate authority that issued the server certificate installed in your directory and used to access your LDAP.
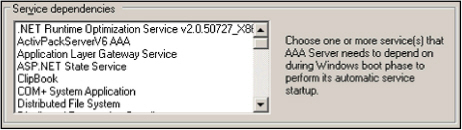
- In the Service dependencies section of the AAA Server Configuration dialog (shown below), select any services the AAA Server requires to perform an automatic startup during a Windows boot. This step is required only if the AAA Server and the database engine hosting the server’s database are on the same machine.
- Click Database Encryption to view the current encryption status.
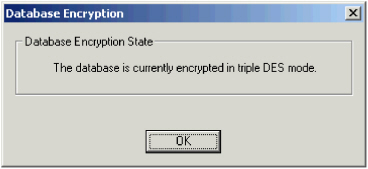 Note: It is recommended that you always work in encrypted mode. Use database decryption is deactivated by default and should only be used for debugging. For more information, contact HID Global technical support.
Note: It is recommended that you always work in encrypted mode. Use database decryption is deactivated by default and should only be used for debugging. For more information, contact HID Global technical support.The encryption status display applies ONLY if the AAA Server and the database engine hosting the server’s database are on the same machine. Make sure that the database engine has started before the AAA authentication service starts. Skip this step if your AAA Server and database are on different machines.
- Click OK to return to the Service Dependencies section of the configuration dialog.
Set the Log and Trace Information, and Configure EAP
-
Click Options to set log and trace information and configure EAP.
-
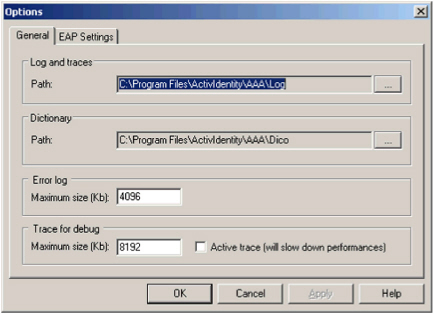
Click General.
- Log and traces Path: specify the directory location for the error log file (ActivPackAdminErr.txt) and the debug trace file (ActivPackAdminTra.txt).
- Dictionary Path: specify the directory location for the various RADIUS and TACACS+ dictionaries. (The default directory was set during installation.)
-
Error log Maximum size: set the file size for the error log.
- Trace for debug Maximum size: set the maximum size for the debug trace log file.
- Select Active trace to activate Error log and Trace for debug.
You must select this option; otherwise, the system does not write to the error log. - Click OK.
Note: The Error and Trace log file sizes affect the amount of information captured. Set the file sizes large enough to be useful to capture the information for review. Do NOT set them too large to compromise the AAA Server system performance. Based on your company organization, the number of people using devices, your security policies and procedures etc., you can either estimate the log file size or accept the default value temporarily. You can change the size when you are more familiar with the system. - Select the EAP Settings tab.
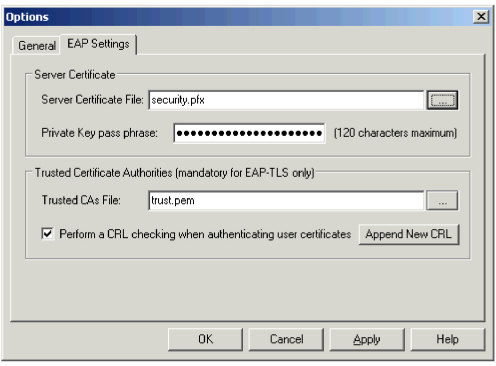
- In the Server Certificate File field, enter the name (including location) of the AAA Server certificate (*.pem, *.pfx or *.p12), or browse to the certificate file.
Any certificate authority can generate the AAA Server certificate. However, to generate the required *.pem, *.pfx or *.p12 files, you must select the Mark keys as exportable option during the certificate generation process. For more information, see your certificate authority documentation. The following table lists the options for the type of certificate you are using:
If... Then... You are using a .pfx certificate. The Please Enter Certificate Pass Phrase dialog box is displayed. Enter the pass phrase, and click OK. The pass phrase is entered in the Private Key pass phrase field. You are using a .pem or .p12 certificate. Manually enter the certificate’s pass phrase in the Private Key pass phrase field. In the Trusted CAs file field in the Trusted Certificates Authorities section, enter the name (including location) of the trusted certificate authorities file, or browse to the file.
- (Optional) To remove the user’s wireless authentication rights at the certificate level, select Perform a CRL checking, and click Append New CRL to locate the list of revoked certificates.
- In the EAP Settings dialog, click Apply.
Note: Configuring the Trusted CAs File is mandatory for EAP TLS (client certificate authentication).
You can append a Certificate Revocation List (CRL) by updating it manually from the certificate authority. - In the Server Certificate File field, enter the name (including location) of the AAA Server certificate (*.pem, *.pfx or *.p12), or browse to the certificate file.
- At the bottom of the Server Configuration window, click Apply.





